Free Dumps, Free Fortinet Dump
Free NSE4_FGT-7.0 Dump
60.Refer to the exhibit to view the application control profile.
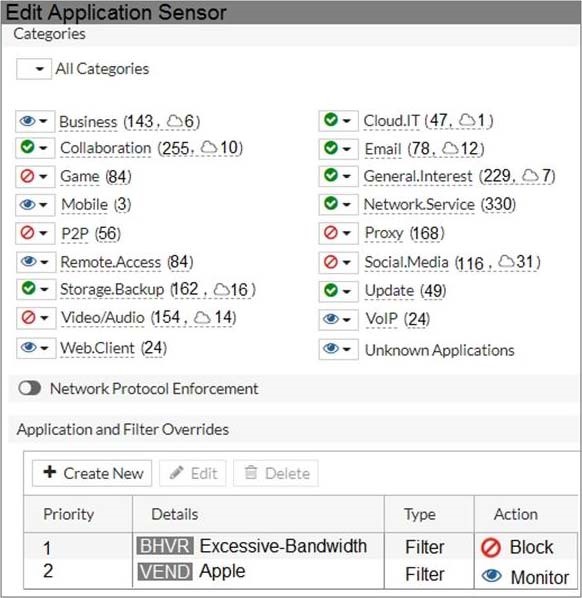
Users who use Apple FaceTime video conferences are unable to set up meetings.
In this scenario, which statement is true?
A. Apple FaceTime belongs to the custom monitored filter.
B. The category of Apple FaceTime is being monitored.
C. Apple FaceTime belongs to the custom blocked filter.
D. The category of Apple FaceTime is being blocked.
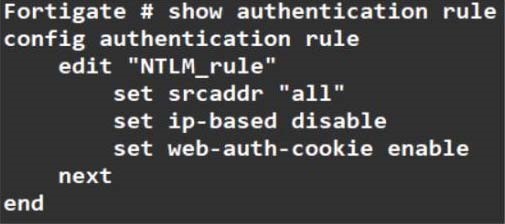
61.Exhibit: Refer to the exhibit to view the authentication rule configuration In this scenario, which statement is true? A. IP-based authentication is enabled B. Route-based authentication is enabled C. Session-based authentication is enabled. D. Policy-based authentication is enabled 62.Which of the following statements correctly describes FortiGates route lookup behavior when searching for a suitable gateway? (Choose two) A. Lookup is done on the first packet from the session originator B. Lookup is done on the last packet sent from the responder C. Lookup is done on every packet, regardless of direction D. Lookup is done on the trust reply packet from the responder 63.Which two policies must be configured to allow traffic on a policy-based next-generation firewall (NGFW) FortiGate? (Choose two.) A. Firewall policy B. Policy rule C. Security policy D. SSL inspection and authentication policy
64.Which three CLI commands can you use to troubleshoot Layer 3 issues if the issue is in neither the physical layer nor the link layer? (Choose three.) A. diagnose sys top B. execute ping C. execute traceroute D. diagnose sniffer packet any E. get system arp
65.Which two statements about IPsec authentication on FortiGate are correct? (Choose two.) A. For a stronger authentication, you can also enable extended authentication (XAuth) to request the remote peer to provide a username and password B. FortiGate supports pre-shared key and signature as authentication methods. C. Enabling XAuth results in a faster authentication because fewer packets are exchanged. D. A certificate is not required on the remote peer when you set the signature as the authentication method.
66.Which of the following are valid actions for FortiGuard category based filter in a web filter profile ui proxy-based inspection mode? (Choose two.) A. Warning B. Exempt C. Allow D. Learn
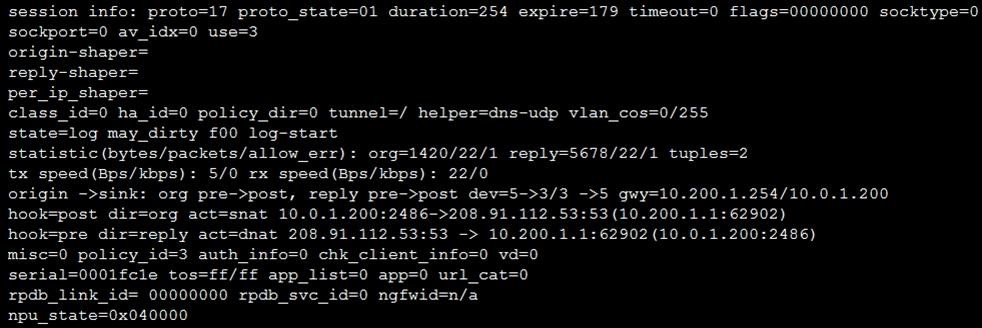
67.Refer to the exhibit, which contains a session diagnostic output. Which statement is true about the session diagnostic output? A. The session is a UDP unidirectional state. B. The session is in TCP ESTABLISHED state. C. The session is a bidirectional UDP connection. D. The session is a bidirectional TCP connection.
68.Which two statements are true about collector agent standard access mode? (Choose two.) A. Standard mode uses Windows convention-NetBios: Domain\Username. B. Standard mode security profiles apply to organizational units (OU). C. Standard mode security profiles apply to user groups. D. Standard access mode supports nested groups.
69.Which two VDOMs are the default VDOMs created when FortiGate is set up in split VDOM mode? (Choose two.) A. FG-traffic B. Mgmt C. FG-Mgmt D. Root
70.An administrator needs to increase network bandwidth and provide redundancy. What interface type must the administrator select to bind multiple FortiGate interfaces? A. VLAN interface B. Software Switch interface C. Aggregate interface D. Redundant interface
71.Which CLI command will display sessions both from client to the proxy and from the proxy to the servers? A. diagnose wad session list B. diagnose wad session list | grep hook-pre&&hook-out C. diagnose wad session list | grep hook=pre&&hook=out D. diagnose wad session list | grep “hook=pre”&”hook=out”
72.Which three criteria can a FortiGate use to look for a matching firewall policy to process traffic? (Choose three.) A. Source defined as Internet Services in the firewall policy. B. Destination defined as Internet Services in the firewall policy. C. Highest to lowest priority defined in the firewall policy. D. Services defined in the firewall policy. E. Lowest to highest policy ID number.
73.Which statements best describe auto discovery VPN (ADVPN). (Choose two.) A. It requires the use of dynamic routing protocols so that spokes can learn the routes to other spokes. B. ADVPN is only supported with IKEv2. C. Tunnels are negotiated dynamically between spokes. D. Every spoke requires a static tunnel to be configured to other spokes so that phase 1 and phase 2 proposals are defined in advance.
74.An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.) A. The interface has been configured for one-arm sniffer. B. The interface is a member of a virtual wire pair. C. The operation mode is transparent. D. The interface is a member of a zone. E. Captive portal is enabled in the interface.
75.NGFW mode allows policy-based configuration for most inspection rules. Which security profile’s configuration does not change when you enable policy-based inspection? A. Web filtering B. Antivirus C. Web proxy D. Application control
76.Refer to the exhibit, which contains a static route configuration. An administrator created a static route for Amazon Web Services. What CLI command must the administrator use to view the route? A. get router info routing-table all B. get internet service route list C. get router info routing-table database D. diagnose firewall proute list