Free Dumps, Free Microsoft Dump
Free MS-900 Dump
Question #240
A company uses Azure Active Directory.
The company requires that authentication requests from client applications that do not support modern authentication are blocked.
You need to identify the policy that meets the requirement.
Which policy should you select?
- A. Conditional Access
- B. Multi-factor authentication registration
- C. Sign-in risk
- D. User risk
Correct Answer: A
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
Community vote distribution
A (100%)
Question #241
You are a Microsoft 365 administrator for a company.
You need to identify security vulnerabilities by using the Office 365 Attack Simulator.
Which three attack simulations are available? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Brute-force password
- B. Cross-site scripting
- C. Password-spray
- D. Denial-of-service
- E. Display name spear-phishing
Correct Answer: ACE
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/attack-simulator
Question #242
DRAG DROP –
A company plans to use Microsoft 365 Defender.
Which services should you use? To answer, drag the appropriate services to the correct requirements. Each service may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/microsoft-365-defender?view=o365-worldwide
Question #243
HOTSPOT –
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct match is worth one point.
Hot Area:

Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/microsoft-365/enterprise/about-microsoft-365-identity?view=o365-worldwide
Question #244
HOTSPOT –
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct match is worth one point.
Hot Area:

Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
Question #245
HOTSPOT –
A company plans to implement Microsoft Defender for Office 365.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct match is worth one point.
Hot Area:
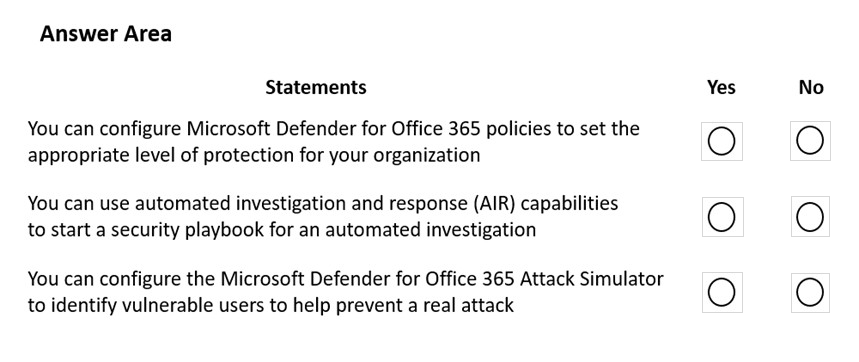
Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/overview?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/tenant-wide-setup-for-increased-security?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/attack-simulator?view=o365-worldwide
Question #246
A company plans to implement an insider risk solution in Microsoft 365.
The company needs to implement a solution that meets the following requirements:
✑ Uses machine learning to identify email risks.
✑ Provides workflows to remediate email risks.
✑ Provides a dashboard to display email risks, actions, and trends.
You need to identify a solution that meets the requirements.
Which solution should you select?
- A. Communication compliance policies
- B. Core eDiscovery cases
- C. Advanced eDiscovery cases
- D. Sensitivity labels
Correct Answer: A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/communication-compliance?view=o365-worldwide
Question #247
Your organization plans to deploy Microsoft 365 in a hybrid scenario.
You need to ensure that employees can use a smart card for authentication.
Which hybrid identity solution should you implement?
- A. password hash synchronization with single sign-on
- B. Active Directory Federation Services (AD FS)
- C. PingFederate and federation integration
- D. pass-through authentication and single sign-on
Correct Answer: B
Reference:
https://docs.microsoft.com/en-us/azure/security/azure-ad-choose-authn
Question #248
HOTSPOT –
You implement Microsoft Azure Information Protection.
For each of the following statements, select Yes if the statement is true. otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/azure/information-protection/what-is-information-protection https://docs.microsoft.com/en-us/azure/information-protection/rms-client/client-classify-protect
Question #249
You need to ensure that the process by which users sign in to Microsoft 365 confirms the identity of the user.
Which feature should you use?
- A. mobile application management (MAM)
- B. Microsoft Defender for Office 365
- C. Multi-Factor Authentication (MFA)
- D. data loss prevention (DLP) policies
Correct Answer: C
Multi-Factor Authentication (MFA) is a two-step identity verification system that can be used to authenticate users.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-howitworks
Question #250
You are a Microsoft 365 administrator for a company.
You need to ensure that company documents are marked as confidential. You must prevent employees from sharing documents with people outside the company.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Validate outbound emails by using DomainKeys Identified Mail (DKIM)
- B. Create sensitive information types
- C. Configure Secure/Multipurpose Internet Mail Extensions (S/MIME) settings for Outlook
- D. Create a data-loss prevention policy
- E. Apply sensitivity labels to documents
Correct Answer: BE
B: Sensitive information types can also be used with the Azure Information Protection scanner to classify and protect files on premises. Sensitive information types define how the automated process recognizes specific information types such as health service numbers and credit card numbers.
E: With sensitivity labels you can classify and help protect your sensitive content. Protection options include labels, watermarks, and encryption.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/protect-information
Community vote distribution
DE (100%)
Question #251
HOTSPOT –
A company uses Microsoft 365 services that include Microsoft eDiscovery.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 
Question #252
HOTSPOT –
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
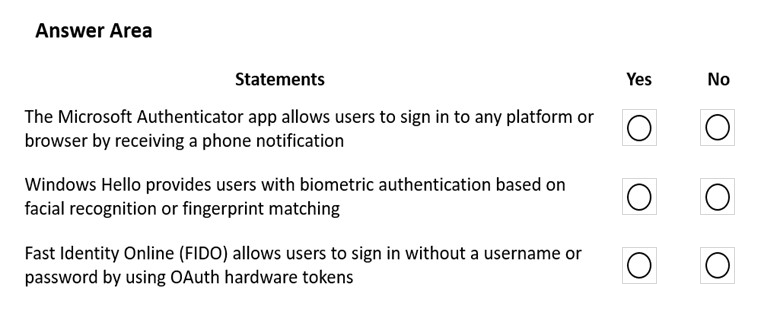
Correct Answer: 
Question #253
A company plans to deploy a solution to manage its Windows 10 computers. Some computers are connected to the corporate network and some computers are connected to the internet,
The solution must meet the following requirements:
✑ Deploy an operating system to the computers.
✑ Join the computer to an on-premises Active Directory domain.
✑ Install Windows updates to the computers.
You need to identify a solution that meets the requirements.
Which solution should you choose?
- A. Microsoft Endpoint Manager
- B. Microsoft Intune
- C. Windows Autopilot
- D. Configuration Manager
Correct Answer: A
Endpoint Manager includes the services and tools you use to manage and monitor mobile devices, desktop computers, virtual machines, embedded devices, and servers. Endpoint Manager combines services, including Microsoft Intune, Configuration Manager, Desktop Analytics, co-management, and Windows Autopilot.
Reference:
https://docs.microsoft.com/en-us/mem/endpoint-manager-overview
Community vote distribution
A (57%)
D (43%)
Question #254
A company deploys Microsoft 365.
The company plans to use sensitivity labels.
You need to identify the capabilities of sensitivity labels.
What are three capabilities of sensitivity labels? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Sensitivity labels can be customized.
- B. Sensitivity labels can ensure that a document is retained indefinitely.
- C. Sensitivity labels can trigger disposition reviews.
- D. Sensitivity labels can be used to encrypt documents.
- E. Sensitivity labels can automatically be applied to documents.
Correct Answer: ADE
With sensitivity labels you can classify and help protect your sensitive content. Protection options include labels, watermarks, and encryption.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
Community vote distribution
ADE (100%)
Question #255
What are three capabilities of Security and Compliance Center? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Management of e-discovery cases, holds, and exports
- B. Assessment and auditing of Active Directory event logs
- C. Prevention of data loss for Exchange Online and SharePoint Online
- D. Assessment and auditing of on-premises firewall logs
- E. Threat management by using email filtering and anti-malware software
Correct Answer: ACE
Reference:
https://docs.microsoft.com/en-us/office365/servicedescriptions/office-365-platform-service-description/office-365-securitycompliance-center
Question #256
HOTSPOT –
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/defender-cloud-apps/what-is-defender-for-cloud-apps https://docs.microsoft.com/en-us/defender-cloud-apps/
Question #257
HOTSPOT –
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/sensitivity-labels
Question #258
HOTSPOT –
A company plans to implement Microsoft Information Protection (MIP).
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
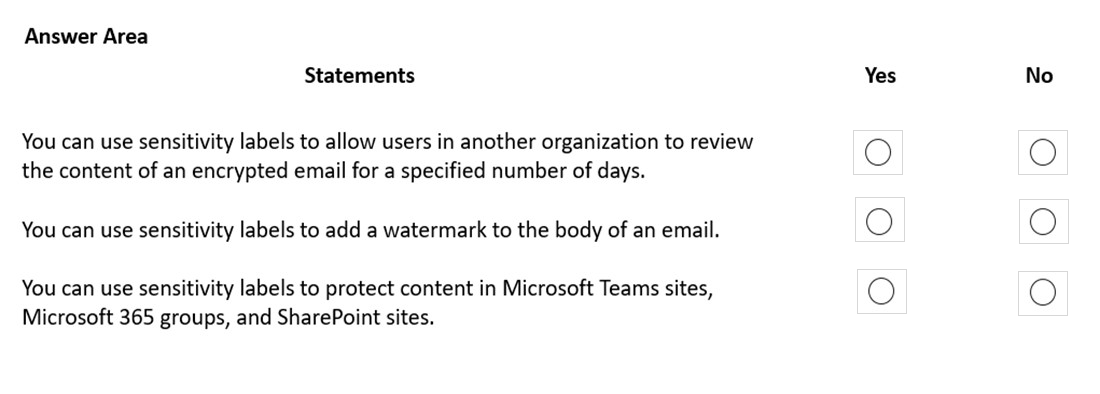
Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/encryption-sensitivity-labels?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/compliance/apply-sensitivity-label-automatically?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-teams-groups-sites?view=o365-worldwide
Question #259
HOTSPOT –
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/mem/endpoint-manager-overview
Question #260
You are a company’s Microsoft 365 administrator.
You need to retrieve the following information:
✑ an assessment of your tenant’s security status for a given regulation
✑ a list of audit and assessment reports on Microsoft’s cloud services
Which two portals have this information? Each correct answer presents a partial solution.
NOTE: Each correct selection is worth one point.
- A. Service Trust Portal
- B. Azure portal
- C. Compliance Center
- D. SharePoint admin center
Correct Answer: AC
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-service-trust-portal?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/compliance/microsoft-365-compliance-center?view=o365-worldwide
Community vote distribution
AC (100%)
Question #261
HOTSPOT –
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-service-trust-portal?view=o365-worldwide
Question #262
A company is evaluating Microsoft Azure Conditional Access policies.
You reed to determine which scenarios Conditional Access policies support.
Which three scenarios should you select? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Multi-factor authentication
- B. Self-service password reset capabilities
- C. Hybrid Azure Active Directory joined device
- D. Blocked access to Microsoft 365 services for unverified users
- E. BitLocker deployment
Correct Answer: ACD
AC: Common Azure Conditional Access policies decisions
* Block access
Most restrictive decision –
* Grant access
Least restrictive decision, can still require one or more of the following options:
Require multi-factor authentication
Require device to be marked as compliant
Require Hybrid Azure AD joined device
Require approved client app –
Require app protection policy (preview)
D: For customers with access to Identity Protection, user risk can be evaluated as part of a Conditional Access policy. User risk represents the probability that a given identity or account is compromised.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-conditions
Question #263
DRAG DROP –
An organization plans to deploy Microsoft 365 in a hybrid scenario.
You need to provide a recommendation based on some common identity and access management scenarios. The solution must minimize costs.
Match each solution to its appropriate scenario. To answer, drag the appropriate solutions from the column on the left to the scenarios on the right. Each solution may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.
Select and Place:

Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/azure/security/azure-ad-choose-authn https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-password-hash-synchronization https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-pta
Question #264
You are the Microsoft 365 administrator for a company.
An employee requests personal data under General Data Protection Regulation (GDPR) guidelines.
You need to retrieve data for the employee.
What should you do?
- A. Create a data subject request case.
- B. Create a retention policy.
- C. Create a data-loss prevention policy.
- D. Create a GDPR assessment.
Correct Answer: A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/gdpr-dsr-office365
Question #265
HOTSPOT –
A company plans to deploy Microsoft Intune.
Which scenarios can you implement by using Intune? To answer, select the appropriate answer for the given scenarios.
NOTE: Each correct selection is worth one point.
Hot Area:
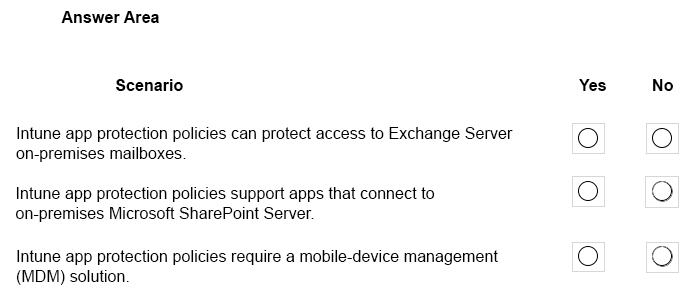
Correct Answer: 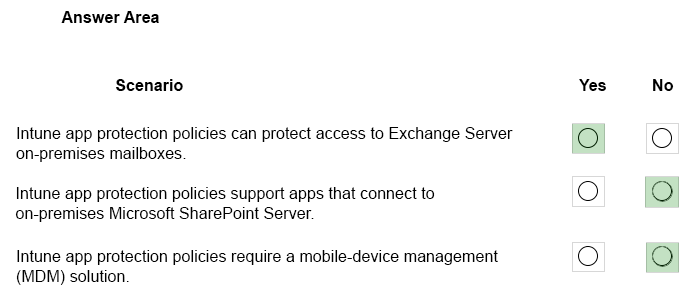
Box 1: Yes –
You can protect access to Exchange on-premises mailboxes by creating Intune app protection policies for Outlook for iOS/iPadOS and Android enabled with hybrid Modern Authentication.
Box 2: No –
App protection policies are not supported for other apps that connect to on-premises Exchange or SharePoint services.
Box 3: No –
App protection policies can be configured for apps that run on devices that are not enrolled in any mobile device management solution: These devices are typically employee owned devices that aren’t managed or enrolled in Intune or other MDM solutions.
Reference:
https://docs.microsoft.com/en-us/intune/app-protection-policy
Question #266
DRAG DROP –
You have a hybrid environment that includes Microsoft Azure AD. On-premises applications use Active Directory Domain Services (AD DS) for authentication.
You need to determine which authentication methods to use.
Match each feature to its authentication source. To answer, drag the appropriate authentication sources from the column on the left to the features on the right.
Each authentication source may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.
Select and Place:
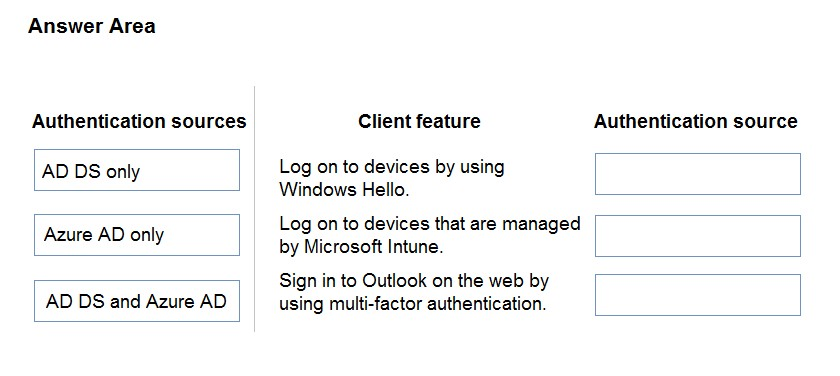
Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-identity-verification
Question #267
A company has a Microsoft 365 subscription. Employees are permitted to use devices that the company does not own to access company data in the cloud.
You need to restrict employees from copying data to personal OneDrive folders.
What should you use?
- A. Information Rights Management
- B. Microsoft Azure Security Center
- C. Microsoft Defender for Office 365
- D. Microsoft Endpoint Manager
Correct Answer: D
Reference:
https://docs.microsoft.com/en-us/intune/app-protection-policy
Question #268
You are the network administrator of a company.
The Microsoft 365 tenant contains sensitive information. Employees must verify their identities when they sign into Microsoft 365 by providing information in addition to their Azure AD password.
You need to select the tools that employees can use to verify their identities.
Which two tools should you select? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Customer Lockbox for Office 365
- B. Azure Security Center
- C. Windows Hello for Business
- D. Microsoft Authenticator
Correct Answer: CD
Two-step authentication can be implemented by using Windows Hello for Business or Microsoft Authenticator.
Reference:
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-manage-in-organization https://support.microsoft.com/en-us/help/4026727/microsoft-account-how-to-use-the-microsoft-authenticator-app
Community vote distribution
CD (100%)
Question #269
You need to move videos to a Microsoft 365 tenant and ensure that the contents are automatically transcribed.
Which Microsoft 365 service should you use?
- A. Yammer
- B. Stream
- C. Flow
Correct Answer: B
Microsoft Stream is used for video services, and includes deep search within automatic audio transcription.
Reference:
https://docs.microsoft.com/en-us/stream/office-365-video-feature-breakdown
Question #270
An organization uses Microsoft 365 Business to secure their data.
Many users install the organization’s data on their personal tablets and phones.
You need to protect the organization’s data stored on users’ devices.
Which three features support device security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Remotely wiping company data
- B. Enabling Advanced Threat Protection for users
- C. Disabling the device remotely
- D. Automatically deleting files after 90 days of inactivity
- E. Requiring users to have a PIN on their device
Correct Answer: ADE
You can manage many of the Microsoft 365 Business security features in the admin center, which gives you a simplified way to turn these features on or off. In the admin center, you can do the following:
✑ Set application management settings for Android or iOS devices.
These settings include deleting files from an inactive device after a set period, encrypting work files, requiring that users set a PIN, and so on.
✑ Set application protection settings for Windows 10 devices.
These settings can be applied to company data on both company-owned, or personally owned devices.
✑ Set device protection settings for Windows 10 devices.
You can enable BitLocker encryption to help protect data in case a device is lost or stolen, and enable Windows Exploit Guard to provide advanced protection against ransomware.
✑ Remove company data from devices.
You can remotely wipe company data if a device is lost, stolen, or an employee leaves your company.
✑ Reset Windows 10 devices to their factory settings.
You can reset any Windows 10 devices that have device protection settings applied to them.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/business/security-features
Community vote distribution
ABE (67%)
ADE (33%)
Question #271
This question requires that you evaluate the underlined text to determine if it is correct.
You use Microsoft Intune for device management. You must determine how many devices run each operating system.
You must launch Intune and navigate to the Mobile Apps blade.
Select the correct answer if the underlined text does not make the statement correct. Select `No change is needed` if the underlined text makes the statement correct.
- A. Device configuration
- B. Device compliance
- C. No change is needed
- D. Devices
Correct Answer: D
Reference:
https://docs.microsoft.com/en-us/intune/device-inventory
Question #272
HOTSPOT –
A company has a Microsoft 365 E5 subscription. The company plans to use eDiscovery to meet legal discovery requirements.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
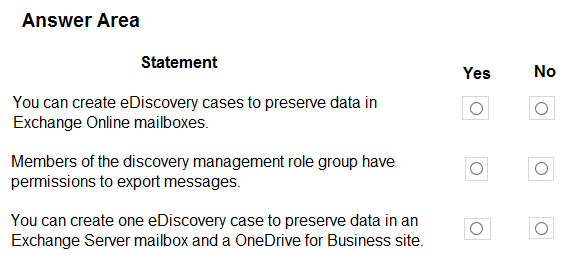
Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/ediscovery#ediscoverycases https://docs.microsoft.com/en-us/office365/securitycompliance/manage-ediscovery-cases https://docs.microsoft.com/en-us/office365/securitycompliance/assign-ediscovery-permissions
Question #273
You are the Microsoft 365 administrator for a company.
You need to ensure that users receive a warning message if they select links in emails that might be unsafe.
What should you do?
- A. Use Windows PowerShell to install the latest antimalware engine updates
- B. Enable Microsoft Office 365 Advanced Threat Protection
- C. Use the Microsoft Exchange Admin Center to configure a new spam-filter policy
- D. Use the Microsoft Exchange Admin Center to create a new antimalware policy
Correct Answer: B
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/atp-safe-links
Question #274
A business acquaintance from another company sends you a document that is encrypted by Azure Information Protection (AIP).
You are unable to open the document because the user account cannot be authenticated by the company’s Azure Active Directory.
You need to access the document.
What should you do?
- A. Implement Azure Rights Management (RMS) for individuals for the user account.
- B. Implement Information Rights Management (IRM) for the Office application.
- C. Upgrade your account to include AIP for Office 365.
Correct Answer: A
Reference:
https://docs.microsoft.com/en-us/azure/information-protection/rms-for-individuals
Question #275
HOTSPOT –
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 
Box 1: Yes –
The Defender for Cloud Apps framework includes
* Discover and control the use of Shadow IT: Identify the cloud apps, IaaS, and PaaS services used by your organization. Investigate usage patterns, assess the risk levels and business readiness of more than 25,000 SaaS apps against more than 80 risks. Start managing them to ensure security and compliance.
Note: Microsoft renamed Microsoft Cloud App Security. It’s now called Microsoft Defender for Cloud Apps.
Box 2: Yes –
The Defender for Cloud Apps framework includes:
* Protect against cyberthreats and anomalies: Detect unusual behavior across cloud apps to identify ransomware, compromised users or rogue applications, analyze high-risk usage and remediate automatically to limit the risk to your organization.
Box 3: Yes –
The Defender for Cloud Apps framework includes:
* Assess the compliance of your cloud apps: Assess if your cloud apps meet relevant compliance requirements including regulatory compliance and industry standards. Prevent data leaks to non-compliant apps, and limit access to regulated data.
Reference:
https://docs.microsoft.com/en-us/defender-cloud-apps/what-is-defender-for-cloud-apps
Question #276
A company uses Microsoft 365.
The company requires that you implement least privileged access.
You need to recommend solutions that meet the requirements.
Which two solutions should you recommend? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Device compliance
- B. IP address range restrictions
- C. Privileged Access Workstations (PAW) devices
- D. Just-in-time (JIT) access
Correct Answer: CD
C: Privileged Access Workstation (PAW) ג€” This is the highest security configuration designed for extremely sensitive roles that would have a significant or material impact on the organization if their account was compromised. The PAW configuration includes security controls and policies that restrict local administrative access and productivity tools to minimize the attack surface to only what is absolutely required for performing sensitive job tasks. This makes the PAW device difficult for attackers to compromise because it blocks the most common vector for phishing attacks: email and web browsing.
D: As shown in the diagram, privileged access management builds on the protection provided with native encryption of Microsoft 365 data and the role-based access control security model of Microsoft 365 services. When used with Azure AD Privileged Identity Management, these two features provide access control with just-in-time access at different scopes.

Reference:
https://docs.microsoft.com/en-us/security/compass/privileged-access-devices https://docs.microsoft.com/en-us/microsoft-365/compliance/privileged-access-management-overview?view=o365-worldwide
Question #277
A company uses Microsoft 365 for email. The company plans to implement a solution for employees who leave the company.
Currently, user accounts of terminated employees are deleted immediately. Mailbox content for terminated employees must be retained for 90 days and then deleted.
You need to identify solutions that meet the requirements.
What are two possible ways to achieve this goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Apply a Litigation Hold to the mailbox.
- B. Recover the inactive mailbox.
- C. Restore the inactive mailbox.
- D. Apply a retention policy to the mailbox.
Correct Answer: AD
A: You can place a mailbox on Litigation hold to retain all mailbox content, including deleted items and the original versions of modified items. When you place a user mailbox on Litigation hold, content in the user’s archive mailbox (if it’s enabled) is also retained. When you create a hold, you can specify a hold duration (also called a time-based hold) so that deleted and modified items are retained for a specified period and then permanently deleted from the mailbox. Or you can just retain content indefinitely (called an infinite hold) or until the Litigation hold is removed.
D: In Exchange Online, you can use archive policies to automatically move mailbox items to personal (on-premises) or cloud-based archives. Archive policies are retention tags that use the Move to Archive retention action.
You can modify retention tags included in the default policy to meet your business requirements. For example, you can modify the archive DPT to move items to the archive after three years instead of two.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/create-a-litigation-hold?view=o365-worldwide https://docs.microsoft.com/en-us/exchange/security-and-compliance/modify-archive-policies
Question #278
HOTSPOT –
A company uses Microsoft Viva Insights.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 
Box 1: No –
The insights for individuals that this app presents are completely personal and private. Personal insights in the app are for your eyes only; neither your manager nor the system administration can see your insights.
Box 2: No –
Box 3: Yes –
The personal insights and actions in the Viva Insights app are based on your Exchange Online mailbox data, such as email and calendar data. The insights are derived from data that isג€‰already availableג€‰to you in your Exchange Online mailbox. For example, if you want to determine what commitments you made to others, you could manually review each email in your mailbox. The Insights app simply saves you from this tedious process.
Reference:
https://docs.microsoft.com/en-us/viva/insights/personal/teams/viva-teams-app
Question #279
HOTSPOT –
A company uses the Microsoft Intune Connector for Active Directory in Microsoft Endpoint Manager.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 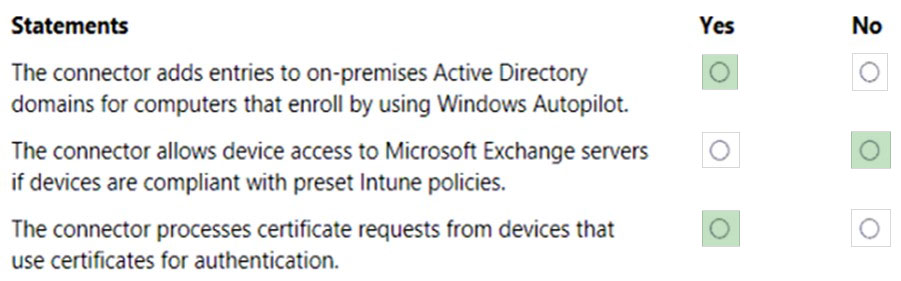
Box 1: Yes –
You can use Intune and Windows Autopilot to set up hybrid Azure Active Directory (Azure AD)-joined devices.
The Intune Connector for your Active Directory creates autopilot-enrolled computers in the on-premises Active Directory domain.
Box 2: No –
Need the Intune Exchange connector as well.
Box 3: Yes –
Use certificates with Intune to authenticate your users to applications and corporate resources through VPN, Wi-Fi, or email profiles. When you use certificates to authenticate these connections, your end users won’t need to enter usernames and passwords, which can make their access seamless. Certificates are also used for signing and encryption of email using S/MIME.
Reference:
https://docs.microsoft.com/en-us/mem/autopilot/windows-autopilot-hybrid https://docs.microsoft.com/en-us/mem/intune/protect/exchange-connector-install https://docs.microsoft.com/en-us/mem/intune/protect/certificates-configure

