Free Dumps, Free ISACA Dump
Free CISSP Dump
Question #300
Which of the following is the MOST important rule for digital investigations?
- A. Ensure original data is never modified.
- B. Ensure systems are powered on.
- C. Ensure event logs are rotated.
- D. Ensure individual privacy is protected.
Correct Answer: A
Community vote distribution
A (100%)
Question #301
An information security professional is reviewing user access controls on a customer-facing application. The application must have multi-factor authentication
(MFA) in place. The application currently requires a username and password to login. Which of the following options would BEST implement MFA?
- A. Geolocate the user and compare to previous logins
- B. Require a pre-selected number as part of the login
- C. Have the user answer a secret question that is known to them
- D. Enter an automatically generated number from a hardware token
Correct Answer: C
Community vote distribution
D (96%)
4%
Question #302
Which of the following is a MAJOR consideration in implementing a Voice over Internet Protocol (VoIP) network?
- A. Use of Request for Comments (RFC) 1918 addressing.
- B. Use of Network Access Control (NAC) on switches.
- C. Use of separation for the voice network.
- D. Use of a unified messaging.
Correct Answer: D
Community vote distribution
C (100%)
Question #303
During testing, where are the requirements to inform parent organizations, law enforcement, and a computer incident response team documented?
- A. Security Assessment Report (SAR)
- B. Security assessment plan
- C. Unit test results
- D. System integration plan
Correct Answer: A
Community vote distribution
B (100%)
Question #304
The security architect has been mandated to assess the security of various brands of mobile devices. At what phase of the product lifecycle would this be MOST likely to occur?
- A. Implementation
- B. Operations and maintenance
- C. Disposal
- D. Development
Correct Answer: D
Community vote distribution
D (100%)
Question #305
Which of the following statements is MOST accurate regarding information assets?
- A. International Organization for Standardization (ISO) 27001 compliance specifies which information assets must be included in asset inventory.
- B. Information assets include any information that is valuable to the organization.
- C. Building an information assets register is a resource-intensive job.
- D. Information assets inventory is not required for risk assessment.
Correct Answer: B
Community vote distribution
B (83%)
A (17%)
Question #306
Which of the following attack types can be used to compromise the integrity of data during transmission?
- A. Synchronization flooding
- B. Session hijacking
- C. Keylogging
- D. Packet sniffing
Correct Answer: D
Community vote distribution
B (90%)
10%
Question #307
A malicious user gains access to unprotected directories on a web server. Which of the following is MOST likely the cause for this information disclosure?
- A. Broken authentication management
- B. Security misconfiguration
- C. Cross-site request forgery (CSRF)
- D. Structured Query Language injection (SQLi)
Correct Answer: B
Community vote distribution
B (100%)
Question #308
When reviewing the security logs, the password shown for an administrative login event was ‘ OR ‘ ‘1’=’1′ –. This is an example of which of the following kinds of attack?
- A. Structured Query Language (SQL) Injection
- B. Brute Force Attack
- C. Rainbow Table Attack
- D. Cross-Site Scripting (XSS)
Correct Answer: A
Community vote distribution
A (100%)
Question #309
Which is the BEST control to meet the Statement on Standards for Attestation Engagements 18 (SSAE-18) confidentiality category?
- A. File hashing
- B. Storage encryption
- C. Data retention policy
- D. Data processing
Correct Answer: B
Community vote distribution
B (100%)
Question #310
Which of the following BEST describes why software assurance is critical in helping prevent an increase in business and mission risk for an organization?
- A. Request for proposals (RFP) avoid purchasing software that does not meet business needs.
- B. Contracting processes eliminate liability for security vulnerabilities for the purchaser.
- C. Decommissioning of old software reduces long-term costs related to technical debt.
- D. Software that does not perform as intended may be exploitable which makes it vulnerable to attack.
Correct Answer: A
Community vote distribution
D (100%)
Question #311
An employee’s home address should be categorized according to which of the following references?
- A. The consent form terms and conditions signed by employees
- B. An organization security plan for human resources
- C. Existing employee data classifications
- D. The organization’s data classification model
Correct Answer: D
Community vote distribution
D (100%)
Question #312
Which of the following activities should a forensic examiner perform FIRST when determining the priority of digital evidence collection at a crime scene?
- A. Gather physical evidence.
- B. Assign responsibilities to personnel on the scene.
- C. Establish a list of files to examine.
- D. Establish order of volatility.
Correct Answer: B
Community vote distribution
D (100%)
Question #313
Which software defined networking (SDN) architectural component is responsible for translating network requirements?
- A. SDN Controller
- B. SDN Datapath
- C. SDN Northbound Interfaces
- D. SDN Application
Correct Answer: C
Community vote distribution
A (78%)
C (22%)
Question #314
An internal audit for an organization recently identified malicious actions by a user account. Upon further investigation, it was determined the offending user account was used by multiple people at multiple locations simultaneously for various services and applications. What is the BEST method to prevent this problem in the future?
- A. Ensure each user has their own unique account.
- B. Allow several users to share a generic account.
- C. Ensure the security information and event management (SIEM) is set to alert.
- D. Inform users only one user should be using the account at a time.
Correct Answer: C
Community vote distribution
A (75%)
C (25%)
Question #315
Who should perform the design review to uncover security design flaws as part of the Software Development Life Cycle (SDLC)?
- A. A security subject matter expert (SME)
- B. A developer subject matter expert (SME)
- C. The business owner
- D. The application owner
Correct Answer: A
Community vote distribution
A (100%)
Question #316
The initial security categorization should be done early in the system life cycle and should be reviewed periodically. Why is it important for this to be done correctly?
- A. It determines the functional and operational requirements.
- B. It determines the security requirements.
- C. It affects other steps in the certification and accreditation process.
- D. The system engineering process works with selected security controls.
Correct Answer: C
Community vote distribution
B (93%)
7%
Question #317
When designing a Cyber-Physical System (CPS), which of the following should be a security practitioner’s first consideration?
- A. Detection of sophisticated attackers
- B. Topology of the network used for the system
- C. Risk assessment of the system
- D. Resiliency of the system
Correct Answer: D
Community vote distribution
D (63%)
C (38%)
Question #318
Which of the following events prompts a review of the disaster recovery plan (DRP)?
- A. Change in senior management
- B. Completion of the security policy review
- C. Organizational merger
- D. New members added to the steering committee
Correct Answer: C
Community vote distribution
C (100%)
Question #319
A user is allowed to access the file labeled “Financial Forecast,” but only between 9:00 a.m. and 5:00 p.m., Monday through Friday. Which type of access mechanism should be used to accomplish this?
- A. Minimum access control
- B. Limited role-based access control (RBAC)
- C. Access control list (ACL)
- D. Rule-based access control
Correct Answer: B
Community vote distribution
D (86%)
14%
Question #320
What is the benefit of using Network Admission Control (NAC)?
- A. NAC only supports Windows operating systems (OS).
- B. NAC supports validation of the endpoint’s security posture prior to allowing the session to go into an authorized state.
- C. NAC can require the use of certificates, passwords, or a combination of both before allowing network admission.
- D. Operating system (OS) versions can be validated prior to allowing network access.
Correct Answer: C
Community vote distribution
B (95%)
5%
Question #321
When MUST an organization’s information security strategic plan be reviewed?
- A. Whenever there are major changes to the business
- B. Quarterly, when the organization’s strategic plan is updated
- C. Every three years, when the organization’s strategic plan is updated
- D. Whenever there are significant changes to a major application
Correct Answer: A
Community vote distribution
A (86%)
14%
Question #322
An established information technology (IT) consulting firm is considering acquiring a successful local startup. To gain a comprehensive understanding of the startup’s security posture, which type of assessment provides the BEST information?
- A. A security audit
- B. A tabletop exercise
- C. A penetration test
- D. A security threat model
Correct Answer: A
Community vote distribution
A (100%)
Question #323
An organization plans to acquire a commercial off-the-shelf (COTS) system to replace their aging home-built reporting system. When should the organization’s security team FIRST get involved in this acquisition’s life cycle?
- A. When the system is verified and validated
- B. When the need for a system is expressed and the purpose of the system is documented
- C. When the system is deployed into production
- D. When the system is being designed, purchased, programmed, developed, or otherwise constructed
Correct Answer: B
Community vote distribution
B (100%)
Question #324
Which of the following is a PRIMARY security weakness in the design of Domain Name System (DNS)?
- A. Each DNS server must hold the address of the root servers.
- B. A DNS server can be disabled in a denial-of-service (DoS) attack.
- C. A DNS server does not authenticate source of information.
- D. A DNS server database can be injected with falsified checksums.
Correct Answer: B
Community vote distribution
C (90%)
10%
Question #325
To minimize the vulnerabilities of a web-based application, which of the following FIRST actions will lock down the system and minimize the risk of an attack?
- A. Apply the latest vendor patches and updates
- B. Run a vulnerability scanner
- C. Review access controls
- D. Install an antivirus on the server
Correct Answer: A
Community vote distribution
A (64%)
C (36%)
Question #326
An organization has implemented a password complexity and an account lockout policy enforcing five incorrect logins tries within ten minutes. Network users have reported significantly increased account lockouts. Which of the following security principles is this company affecting?
- A. Confidentiality
- B. Integrity
- C. Availability
- D. Authentication
Correct Answer: C
Community vote distribution
C (60%)
B (20%)
A (20%)
Question #327
In the last 15 years a company has experienced three electrical failures. The cost associated with each failure is listed below. Which of the following would be a reasonable annual loss expectation?

- A. 3,500
- B. 140,000
- C. 14,000
- D. 350,000
Correct Answer: A
Community vote distribution
C (100%)
Question #328
A security practitioner has been asked to model best practices for disaster recovery (DR) and business continuity. The practitioner has decided that a formal committee is needed to establish a business continuity policy. Which of the following BEST describes this stage of business continuity development?
- A. Developing and Implementing business continuity plans (BCP)
- B. Project Initiation and Management
- C. Risk Evaluation and Control
- D. Business impact analysis (BIA)
Correct Answer: D
Community vote distribution
B (94%)
6%
Question #329
What physical characteristic does a retinal scan biometric device measure?
- A. The amount of light reflected by the retina
- B. The pattern of blood vessels at the back of the eye
- C. The size, curvature, and shape of the retina
- D. The pattern of light receptors It the back of the eye
Correct Answer: B
Community vote distribution
B (100%)
Question #330
Which of the following BEST represents a defense in depth concept?
- A. Network-based data loss prevention (DLP), Network Access Control (NAC), network-based Intrusion prevention system (NIPS), Port security on core switches
- B. Host-based data loss prevention (DLP), Endpoint anti-malware solution, Host-based integrity checker, Laptop locks, hard disk drive (HDD) encryption
- C. Endpoint security management, network intrusion detection system (NIDS), Network Access Control (NAC), Privileged Access Management (PAM), security information and event management (SIEM)
- D. Web application firewall (WAF), Gateway network device tuning, Database firewall, Next-Generation Firewall (NGFW), Tier-2 demilitarized zone (DMZ) tuning
Correct Answer: C
Community vote distribution
B (60%)
C (40%)
Question #331
Which of the following is required to verify the authenticity of a digitally signed document?
- A. Agreed upon shared secret
- B. Digital hash of the signed document
- C. Recipient’s public key
- D. Sender’s private key
Correct Answer: B
Community vote distribution
B (62%)
C (23%)
D (15%)
Question #332
Which of the following contributes MOST to the effectiveness of a security officer?
- A. Developing precise and practical security plans
- B. Integrating security into the business strategies
- C. Understanding the regulatory environment
- D. Analyzing the strengths and weakness of the organization
Correct Answer: C
Community vote distribution
B (100%)
Question #333
Where can the Open Web Application Security Project (OWASP) list of associated vulnerabilities be found?
- A. OWASP Mobile Project
- B. OWASP Software Assurance Maturity Model (SAMM) Project
- C. OWASP Guide Project
- D. OWASP Top 10 Project
Correct Answer: D
Community vote distribution
D (100%)
Question #334
Employee training, risk management, and data handling procedures and policies could be characterized as which type of security measure?
- A. Preventative
- B. Management
- C. Non-essential
- D. Administrative
Correct Answer: D
Community vote distribution
D (72%)
A (28%)
Question #335
A hospital’s building controls system monitors and operates the environmental equipment to maintain a safe and comfortable environment. Which of the following could be used to minimize the risk of utility supply interruption?
- A. Digital protection and control devices capable of minimizing the adverse impact to critical utility
- B. Standardized building controls system software with high connectivity to hospital networks
- C. Lock out maintenance personnel from the building controls system access that can impact critical utility supplies
- D. Digital devices that can turn equipment off and continuously cycle rapidly in order to increase supplies and conceal activity on the hospital network
Correct Answer: A
Community vote distribution
A (100%)
Question #336
Which of the following statements BEST distinguishes a stateful packet inspection firewall from a stateless packet filter firewall?
- A. The SPI inspects traffic on a packet-by-packet basis.
- B. The SPI inspects the flags on Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) packets.
- C. The SPI is capable of dropping packets based on a pre-defined rule set.
- D. The SPI inspects the traffic in the context of a session.
Correct Answer: C
Community vote distribution
D (100%)
Question #337
What is the MAIN purpose of conducting a business impact analysis (BIA)?
- A. To determine the cost for restoration of damaged information system
- B. To determine the controls required to return to business critical operations
- C. To determine the critical resources required to recover from an incident within a specified time period
- D. To determine the effect of mission-critical information system failures on core business processes
Correct Answer: D
Community vote distribution
D (100%)
Question #338
Which algorithm gets its security from the difficulty of calculating discrete logarithms in a finite field and is used to distribute keys, but cannot be used to encrypt or decrypt messages?
- A. Kerberos
- B. Digital Signature Algorithm (DSA)
- C. Diffie-Hellman
- D. Rivest-Shamir-Adleman (RSA)
Correct Answer: A
Community vote distribution
C (92%)
4%
Question #339
Which of the following is established to collect information in accordance with pre-established metrics, utilizing information readily available in part through implemented security controls?
- A. Security Assessment Report (SAR)
- B. Organizational risk tolerance
- C. Risk assessment report
- D. Information Security Continuous Monitoring (ISCM)
Correct Answer: C
Community vote distribution
D (100%)
Question #340
When conducting a remote access session using Internet Protocol Security (IPSec), which Open Systems Interconnection (OSI) model layer does this connection use?
- A. Presentation
- B. Transport
- C. Network
- D. Data link
Correct Answer: C
Community vote distribution
C (100%)
Question #341
Which of the following is the MOST effective corrective control to minimize the effects of a physical intrusion?
- A. Rapid response by guards or police to apprehend a possible intruder
- B. Sounding a loud alarm to frighten away a possible intruder
- C. Automatic videotaping of a possible intrusion
- D. Activating bright lighting to frighten away a possible intruder
Correct Answer: D
Community vote distribution
A (94%)
6%
Question #342
Which of the following are the three MAIN categories of security controls?
- A. Preventative, corrective, detective
- B. Administrative, technical, physical
- C. Corrective, detective, recovery
- D. Confidentiality, integrity, availability
Correct Answer: B
Community vote distribution
B (100%)
Question #343
Which is the PRIMARY mechanism for providing the workforce with the information needed to protect an agency’s vital information resources?
- A. Implementation of access provisioning process for coordinating the creation of user accounts
- B. Incorporating security awareness and training as part of the overall information security program
- C. An information technology (IT) security policy to preserve the confidentiality, integrity, and availability of systems
- D. Execution of periodic security and privacy assessments to the organization
Correct Answer: C
Community vote distribution
B (58%)
C (42%)
Question #344
Which of the following is considered the FIRST step when designing an internal security control assessment?
- A. Create a plan based on comprehensive knowledge of known breaches.
- B. Create a plan based on reconnaissance of the organization’s infrastructure.
- C. Create a plan based on a recognized framework of known controls.
- D. Create a plan based on recent vulnerability scans of the systems in question.
Correct Answer: B
Community vote distribution
C (44%)
B (33%)
A (22%)
Question #345
The Open Web Application Security Project’s (OWASP) Software Assurance Maturity Model (SAMM) allows organizations to implement a flexible software security strategy to measure organizational impact based on what risk management aspect?
- A. Risk exception
- B. Risk tolerance
- C. Risk treatment
- D. Risk response
Correct Answer: D
Community vote distribution
D (50%)
C (28%)
B (22%)
Question #346
DRAG DROP –
Match the roles for an external audit to the appropriate responsibilities. Drag each role on the left to its corresponding responsibility on the right.
Select and Place:
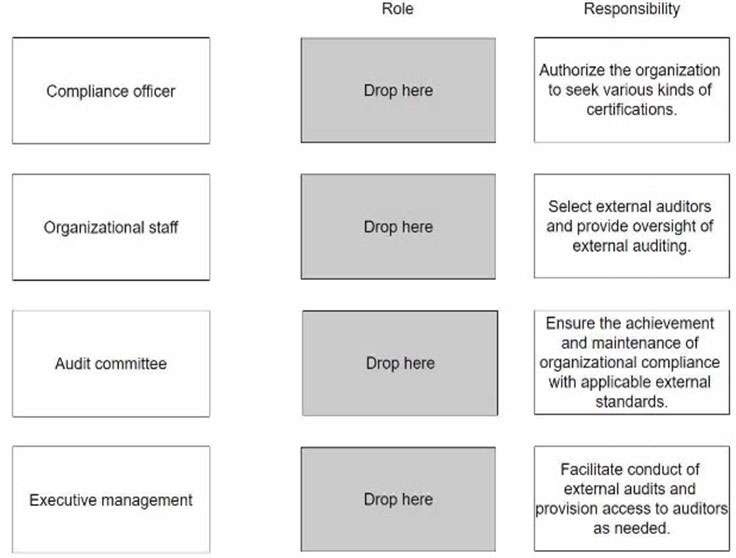
Correct Answer: 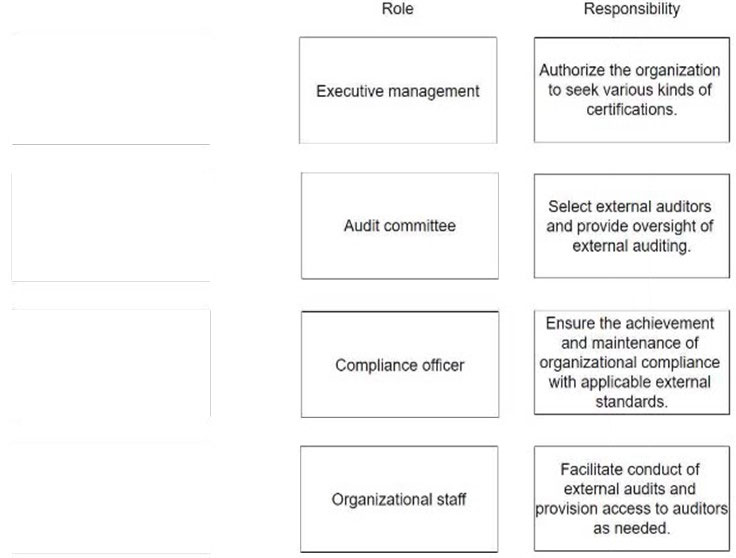
Question #347
What is the PRIMARY reason that a bit-level copy is more desirable than a file-level copy when replicating a hard drives contents for an e-discovery investigation?
- A. The corruption of files is less likely.
- B. Files that have been deleted will be transferred.
- C. The file and directory structure is retained.
- D. File-level security settings will be preserved.
Correct Answer: B
Community vote distribution
B (100%)
Question #348
An organization outgrew its internal data center and is evaluating third-party hosting facilities. In this evaluation, which of the following is a PRIMARY factor for selection?
- A. Facility provides an acceptable level of risk
- B. Facility provides disaster recovery (DR) services
- C. Facility has physical access protection measures
- D. Facility provides the most cost-effective solution
Correct Answer: D
Community vote distribution
A (64%)
D (36%)
Question #349
A large manufacturing organization arranges to buy an industrial machine system to produce a new line of products. The system includes software provided to the vendor by a third-party organization. The financial risk to the manufacturing organization starting production is high. What step should the manufacturing organization take to minimize its financial risk in the new venture prior to the purchase?
- A. Require that the software be thoroughly tested by an accredited independent software testing company.
- B. Hire a performance tester to execute offline tests on a system.
- C. Calculate the possible loss in revenue to the organization due to software bugs and vulnerabilities, and compare that to the system’s overall price.
- D. Place the machine behind a Layer 3 firewall.
Correct Answer: C
Community vote distribution
C (61%)
A (39%)

