Free Dumps, Free Microsoft Dump
Free AZ-900 Dump
Question #200Topic 1
HOTSPOT –
Select the answer that correctly completes the sentence.
Hot Area:
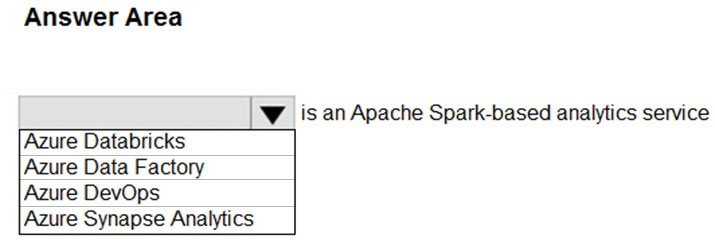
Correct Answer: 
Box: Azure Databricks –
Azure Databricks is a fast, easy, and collaborative Apache Spark-based big data analytics service designed for data science and data engineering.
Reference:
https://azure.microsoft.com/en-us/services/databricks/
Question #201Topic 1
HOTSPOT –
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
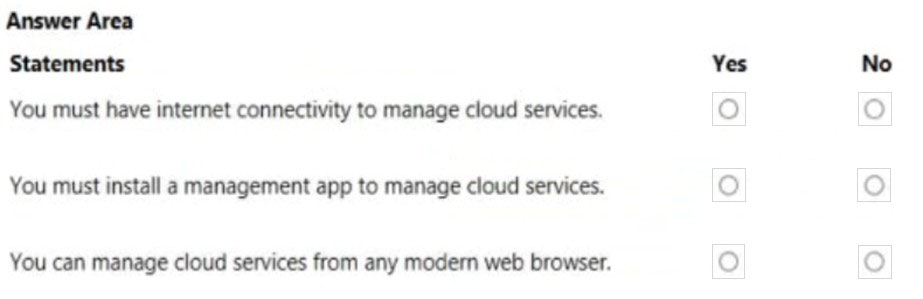
Correct Answer: 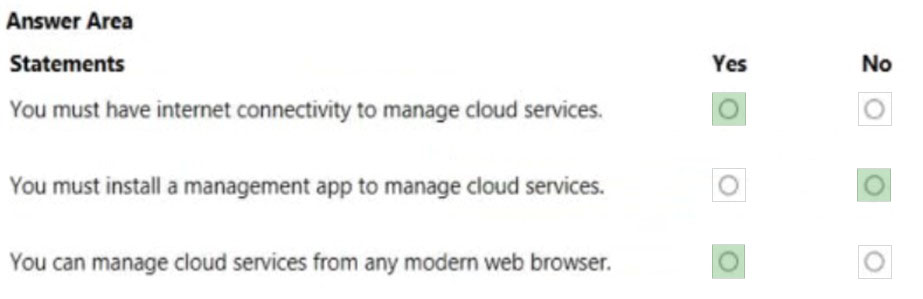
Box 1: Yes –
Box 2: No –
Cloud services can be managed through https://portal.azure.com/
In the Cloud Services area of the Azure portal, you can:
Update a service role or a deployment.
Promote a staged deployment to production.
Link resources to your cloud service so that you can see the resource dependencies and scale the resources together.
Delete a cloud service or a deployment.
Box 3: Yes –
Reference:
https://docs.microsoft.com/en-us/azure/cloud-services/cloud-services-how-to-manage-portal
Question #202Topic 1
DRAG DROP –
Match the Azure service to the correct definition.
Instructions: To answer, drag the appropriate Azure service from the column on the left to its description on the right. Each service may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.
Select and Place:
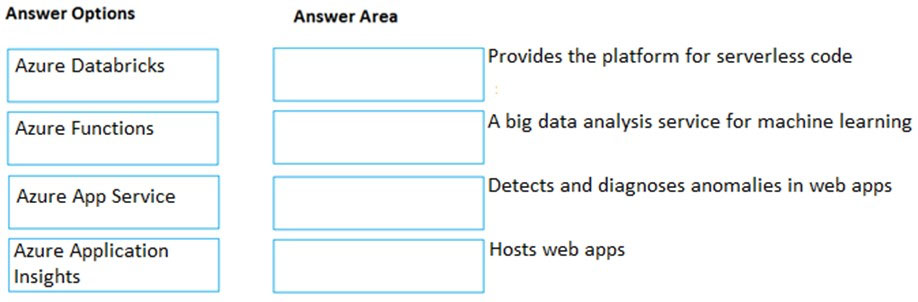
Correct Answer: 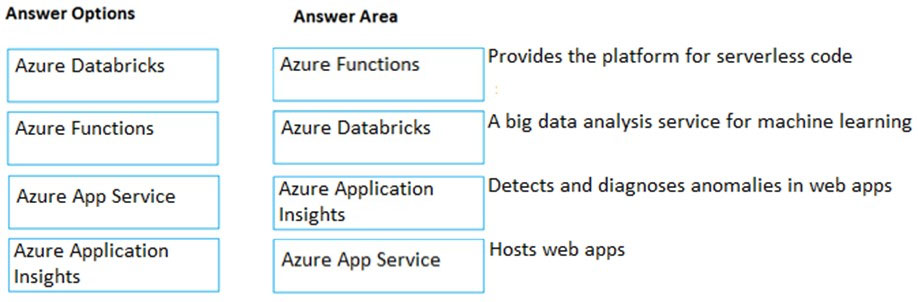
Box 1:
Azure Functions provides the platform for serverless code.
Azure Functions is a serverless compute service that lets you run event-triggered code without having to explicitly provision or manage infrastructure.
Box 2:
Azure Databricks is a big analysis service for machine learning.
Azure Databricks is an Apache Spark-based analytics platform. The platform consists of several components including ‘MLib’. Mlib is a Machine Learning library consisting of common learning algorithms and utilities, including classification, regression, clustering, collaborative filtering, dimensionality reduction, as well as underlying optimization primitives.
Box 3:
Azure Application Insights detects and diagnoses anomalies in web apps.
Application Insights, a feature of Azure Monitor, is an extensible Application Performance Management (APM) service for developers and DevOps professionals.
Use it to monitor your live applications. It will automatically detect performance anomalies, and includes powerful analytics tools to help you diagnose issues and to understand what users actually do with your app.
Box 4:
Azure App Service hosts web apps.
Azure App Service is an HTTP-based service for hosting web applications, REST APIs, and mobile back ends. You can develop in your favorite language, be it
.NET, .NET Core, Java, Ruby, Node.js, PHP, or Python. Applications run and scale with ease on both Windows and Linux-based environments.
References:
https://docs.microsoft.com/en-us/azure/azure-functions/
https://docs.microsoft.com/en-us/azure/azure-databricks/what-is-azure-databricks#apache-spark-based-analytics-platform https://docs.microsoft.com/en-us/azure/azure-monitor/app/app-insights-overview https://docs.microsoft.com/en-us/azure/app-service/overview
Question #203Topic 1
A team of developers at your company plans to deploy, and then remove, 50 customized virtual machines each week. Thirty of the virtual machines run Windows
Server 2016 and 20 of the virtual machines run Ubuntu Linux.
You need to recommend which Azure service will minimize the administrative effort required to deploy and remove the virtual machines.
What should you recommend?
- A. Azure Reserved Virtual Machines (VM) Instances
- B. Azure virtual machine scale sets
- C. Azure DevTest Labs
- D. Microsoft Managed Desktop
Correct Answer: C
DevTest Labs creates labs consisting of pre-configured bases or Azure Resource Manager templates.
By using DevTest Labs, you can test the latest versions of your applications by doing the following tasks:
✑ Quickly provision Windows and Linux environments by using reusable templates and artifacts.
✑ Easily integrate your deployment pipeline with DevTest Labs to provision on-demand environments.
✑ Scale up your load testing by provisioning multiple test agents and create pre-provisioned environments for training and demos.
Reference:
https://docs.microsoft.com/en-us/azure/lab-services/devtest-lab-overview
Community vote distribution
C (100%)
Question #204Topic 1
HOTSPOT –
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer: 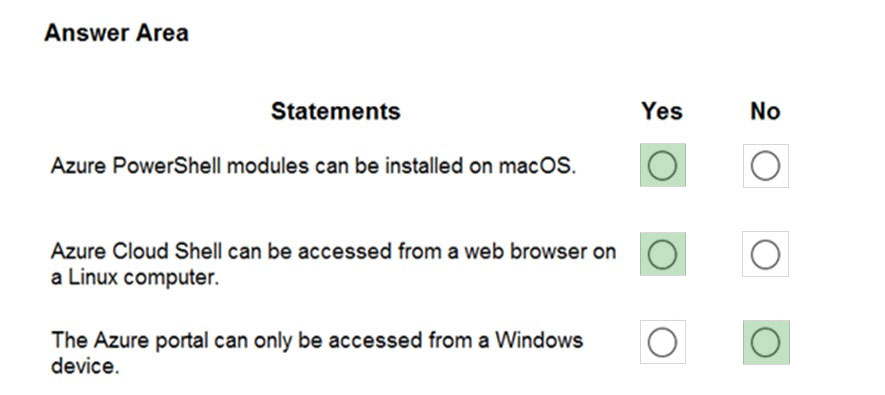
You can install the Az PowerShell module locally on Windows, macOS, and Linux. It can also be used from a browser through Azure Cloud Shell or inside a
Docker container.
Reference:
https://docs.microsoft.com/en-us/powershell/azure/what-is-azure-powershell?view=azps-6.6.0 https://serverfault.com/questions/323973/how-do-i-access-the-windows-azure-management-portal-from-ubuntu
Question #205Topic 1
A support engineer plans to perform several Azure management tasks by using the Azure CLI.
You install the CLI on a computer.
You need to tell the support engineer which tools to use to run the CLI.
Which two tools should you instruct the support engineer to use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Command Prompt
- B. Azure Resource Explorer
- C. Windows PowerShell
- D. Windows Defender Firewall
- E. Network and Sharing Center
Correct Answer: AC
For Windows the Azure CLI is installed via an MSI, which gives you access to the CLI through the Windows Command Prompt (CMD) or PowerShell.
References:
https://docs.microsoft.com/en-us/cli/azure/install-azure-cli-windows?view=azure-cli-latest
Community vote distribution
AC (100%)
Question #206Topic 1
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure environment. You need to create a new Azure virtual machine from a tablet that runs the Android operating system.
Solution: You use PowerShell in Azure Cloud Shell.
Does this meet the goal?
- A. Yes
- B. No
Correct Answer: A
Azure Cloud Shell is a browser-based shell experience to manage and develop Azure resources.
Cloud Shell offers a browser-accessible, pre-configured shell experience for managing Azure resources without the overhead of installing, versioning, and maintaining a machine yourself.
Being browser-based, Azure Cloud Shell can be run on a browser from a tablet that runs the Android operating system.
References:
https://docs.microsoft.com/en-us/azure/cloud-shell/features
Community vote distribution
A (90%)
10%
Question #207Topic 1
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure environment. You need to create a new Azure virtual machine from a tablet that runs the Android operating system.
Solution: You use the PowerApps portal.
Does this meet the goal?
- A. Yes
- B. No
Correct Answer: B
PowerApps lets you quickly build business applications with little or no code. It is not used to create Azure virtual machines. Therefore, this solution does not meet the goal.
PowerApps Portals allow organizations to create websites which can be shared with users external to their organization either anonymously or through the login provider of their choice like LinkedIn, Microsoft Account, other commercial login providers.
References:
https://powerapps.microsoft.com/en-us/blog/introducing-powerapps-portals-powerful-low-code-websites-for-external-users/
Community vote distribution
B (100%)
Question #208Topic 1
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure environment. You need to create a new Azure virtual machine from a tablet that runs the Android operating system.
Solution: You use the Azure portal.
Does this meet the goal?
- A. Yes
- B. No
Correct Answer: A
The Azure portal is a web-based, unified console that provides an alternative to command-line tools. With the Azure portal, you can manage your Azure subscription using a graphical user interface. You can build, manage, and monitor everything from simple web apps to complex cloud deployments. Create custom dashboards for an organized view of resources. Configure accessibility options for an optimal experience.
Being web-based, the Azure portal can be run on a browser from a tablet that runs the Android operating system.
References:
https://docs.microsoft.com/en-us/azure/azure-portal/azure-portal-overview
Community vote distribution
A (89%)
11%
Question #209Topic 1
HOTSPOT –
Select the answer that correctly completes the sentence.
Hot Area:

Correct Answer: 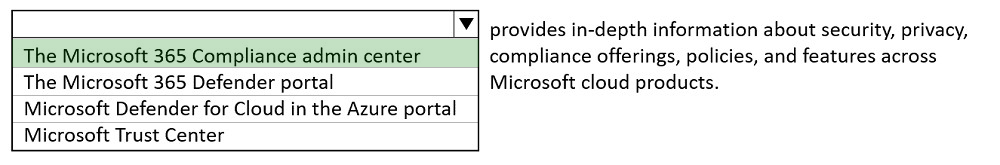
Microsoft 365 compliance is now called Microsoft Purview and the solutions within the compliance area have been rebranded.
When you first visit the compliance portal, the card section on the home page shows you at a glance how your organization is doing with data compliance, what solutions are available for your organization, and a summary of any active alerts.
From here, you can:
* Review the Microsoft Purview Compliance Manager card, which leads you to the Compliance Manager solution. Compliance Manager helps simplify the way you manage compliance.
* Review the new Solution catalog card, which links to collections of integrated solutions you can use to help you manage end-to-end compliance scenarios. A solution’s capabilities and tools might include a combination of policies, alerts, reports, and more.
* Review the Active alerts card, which includes a summary of the most active alerts and includes a link where you can view more detailed information, such as
Severity, Status, Category, and more.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/microsoft-365-compliance-center
Question #210Topic 1
HOTSPOT –
Select the answer that correctly completes the sentence.
Hot Area:

Correct Answer: 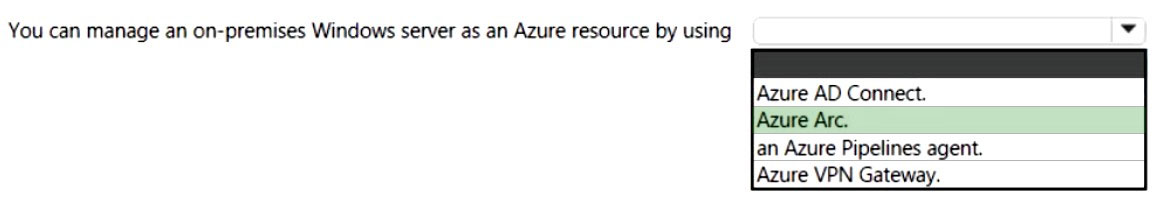
Azure Arc simplifies governance and management by delivering a consistent multi-cloud and on-premises management platform.
Azure Arc provides a centralized, unified way to:
Manage your entire environment together by projecting your existing non-Azure and/or on-premises resources into Azure Resource Manager.
Manage virtual machines, Kubernetes clusters, and databases as if they are running in Azure.
Etc.
Incorrect:
* Why use Azure AD Connect?
Integrating your on-premises directories with Azure AD makes your users more productive by providing a common identity for accessing both cloud and on- premises resources. Users and organizations can take advantage of:
Users can use a single identity to access on-premises applications and cloud services such as Microsoft 365.
Single tool to provide an easy deployment experience for synchronization and sign-in.
Provides the newest capabilities for your scenarios. Azure AD Connect replaces older versions of identity integration tools such as DirSync and Azure AD Sync.
* VPN Gateway sends encrypted traffic between an Azure virtual network and an on-premises location over the public Internet. You can also use VPN Gateway to send encrypted traffic between Azure virtual networks over the Microsoft network. A VPN gateway is a specific type of virtual network gateway.
* Pipeline agent is machine where your build is performed. An agent is installable software that runs one job at a time. Agent job is a set of steps which is recognized as execution boundary. Each job runs on an agent. All of the steps run together on the same agent.
Reference:
https://docs.microsoft.com/en-us/azure/azure-arc/overview
Question #211Topic 1
HOTSPOT –
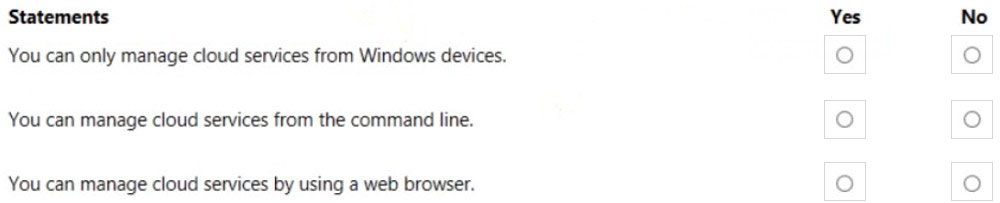
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer: 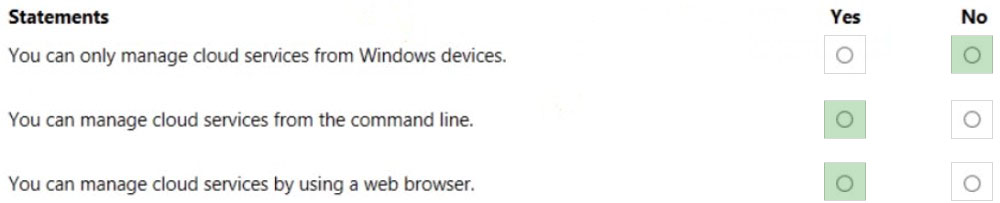
Box 1: No –
Easily manage your Azure storage accounts in the cloud, from Windows, macOS, or Linux, using Azure Storage Explorer.
Box 2: Yes –
Azure cloud services can be managed in Azure Automation by using the PowerShell cmdlets that are available in the Azure PowerShell tools.
Box 3: Yes –
Reference:
https://azure.microsoft.com/en-us/features/storage-explorer/
https://docs.microsoft.com/en-us/azure/cloud-services/automation-manage-cloud-services
Question #212Topic 1
HOTSPOT –
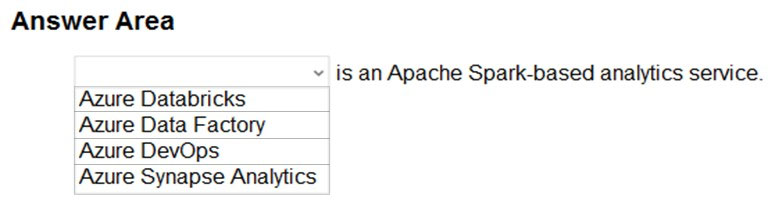
To complete the sentence, select the appropriate option in the answer area.
Hot Area:
Correct Answer: 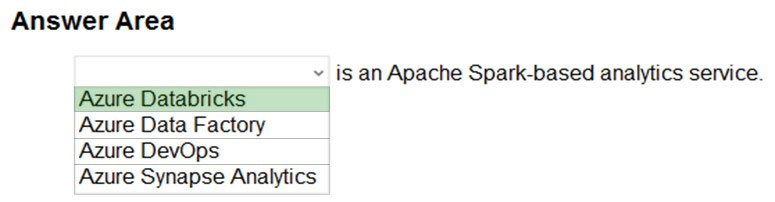
Azure Databricks is an Apache Spark-based analytics platform. The platform consists of several components including ‘MLib’. Mlib is a Machine Learning library consisting of common learning algorithms and utilities, including classification, regression, clustering, collaborative filtering, dimensionality reduction, as well as underlying optimization primitives.
Reference:
https://docs.microsoft.com/en-us/azure/azure-databricks/what-is-azure-databricks#apache-spark-based-analytics-platform
Question #213Topic 1
HOTSPOT –
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer: 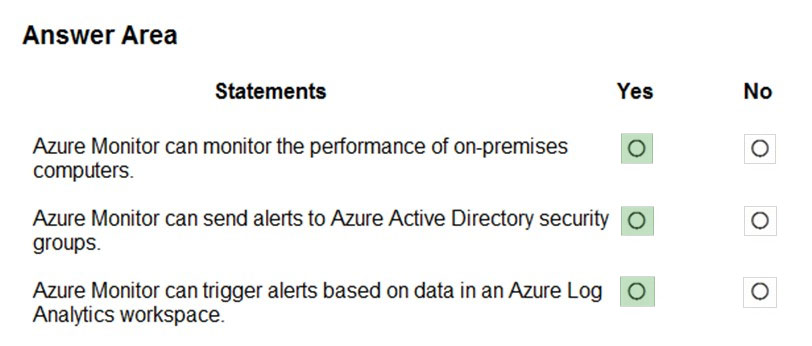
Box 1: Yes –
Azure Monitor maximizes the availability and performance of your applications and services by delivering a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments.
Box 2: Yes –
Alerts in Azure Monitor proactively notify you of critical conditions and potentially attempt to take corrective action.
Box 3: Yes –
Azure Monitor uses Target Resource, which is the scope and signals available for alerting. A target can be any Azure resource. Example targets: a virtual machine, a storage account, a virtual machine scale set, a Log Analytics workspace, or an Application Insights resource.
References:
https://docs.microsoft.com/en-us/azure/azure-monitor/overview https://docs.microsoft.com/en-us/azure/azure-monitor/platform/alerts-overview
Question #214Topic 1
Which Azure service provides a set of version control tools to manage code?
- A. Azure Repos
- B. Azure DevTest Labs
- C. Azure Storage
- D. Azure Cosmos DB
Correct Answer: A
Azure Repos is a set of version control tools that you can use to manage your code.
Incorrect Answers:
B: Azure DevTest Labs creates labs consisting of pre-configured bases or Azure Resource Manager templates. These have all the necessary tools and software that you can use to create environments.
D: Azure Cosmos DB is Microsoft’s globally distributed, multi-model database service.
References:
https://docs.microsoft.com/en-us/azure/devops/repos/get-started/what-is-repos?view=azure-devops
Community vote distribution
A (100%)
Question #215Topic 1
HOTSPOT –
You need to manage Azure by using Azure Cloud Shell.
Which Azure portal icon should you select? To answer, select the appropriate icon in the answer area.
Hot Area:

Correct Answer: 
You can access Azure Cloud Shell in the Azure portal by clicking the icon.
Azure Cloud Shell is an interactive, authenticated, browser-accessible shell for managing Azure resources. It provides the flexibility of choosing the shell experience that best suits the way you work, either Bash or PowerShell.
Cloud Shell enables access to a browser-based command-line experience built with Azure management tasks in mind.
References:
https://docs.microsoft.com/en-us/azure/cloud-shell/overview?view=azure-cli-latest
Question #216Topic 1
You have a virtual machine named VM1 that runs Windows Server 2016. VM1 is in the East US Azure region.
Which Azure service should you use from the Azure portal to view service failure notifications that can affect the availability of VM1?
- A. Azure Service Fabric
- B. Azure Monitor
- C. Azure virtual machines
- D. Azure Advisor
Correct Answer: C
In the Azure virtual machines page in the Azure portal, there is a named Maintenance Status. This column will display service issues that could affect your virtual machine. A service failure is rare but host server maintenance that could affect your virtual machines is more common.
Azure periodically updates its platform to improve the reliability, performance, and security of the host infrastructure for virtual machines. The purpose of these updates ranges from patching software components in the hosting environment to upgrading networking components or decommissioning hardware.
References:
https://docs.microsoft.com/en-us/azure/virtual-machines/maintenance-and-updates
Community vote distribution
B (66%)
C (34%)
Question #217Topic 1
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify an Azure Traffic Manager profile.
Does this meet the goal?
- A. Yes
- B. No
Correct Answer: B
Azure Traffic Manager is a DNS-based load balancing solution. It is not used to ensure that a virtual machine named VM1 is accessible from the Internet over
HTTP.
To ensure that a virtual machine named VM1 is accessible from the Internet over HTTP, you need to modify a network security group or Azure Firewall.
In this question, we need to add a rule to a network security group or Azure Firewall to allow the connection to the virtual machine on port 80 (HTTP).
References:
https://docs.microsoft.com/en-us/azure/traffic-manager/traffic-manager-overview
Question #218Topic 1
Your company plans to deploy several web servers and several database servers to Azure.
You need to recommend an Azure solution to limit the types of connections from the web servers to the database servers.
What should you include in the recommendation?
- A. network security groups (NSGs)
- B. Azure Service Bus
- C. a local network gateway
- D. a route filter
Correct Answer: A
A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network.
You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
References:
https://docs.microsoft.com/en-us/azure/virtual-network/security-overview
Community vote distribution
A (100%)
Question #219Topic 1
HOTSPOT –
To complete the sentence, select the appropriate option in the answer area.
Hot Area:
Correct Answer: 
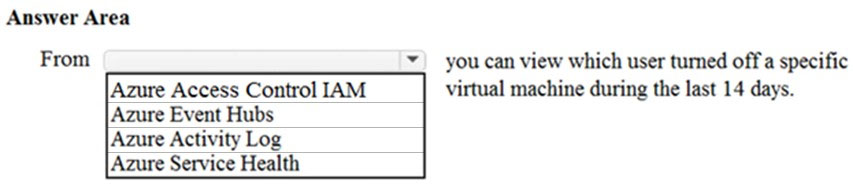
You would use the Azure Activity Log, not Access Control to view which user turned off a specific virtual machine during the last 14 days.
Activity logs are kept for 90 days. You can query for any range of dates, as long as the starting date isn’t more than 90 days in the past.
In this question, we would create a filter to display shutdown operations on the virtual machine in the last 14 days.
Reference:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-audit
Question #220Topic 1
Which service provides network traffic filtering across multiple Azure subscriptions and virtual networks?
- A. Azure Firewall
- B. an application security group
- C. Azure DDoS protection
- D. a network security group (NSG)
Correct Answer: A
You can restrict traffic to multiple virtual networks in multiple subscriptions with a single Azure firewall.
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It’s a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
You can centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks. Azure Firewall uses a static public IP address for your virtual network resources allowing outside firewalls to identify traffic originating from your virtual network.
References:
https://docs.microsoft.com/en-us/azure/firewall/overview
Community vote distribution
A (100%)
Question #221Topic 1
Which Azure service should you use to store certificates?
- A. Azure Security Center
- B. an Azure Storage account
- C. Azure Key Vault
- D. Azure Information Protection
Correct Answer: C
Azure Key Vault is a secure store for storage various types of sensitive information including passwords and certificates.
Azure Key Vault can be used to Securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets.
Secrets and keys are safeguarded by Azure, using industry-standard algorithms, key lengths, and hardware security modules (HSMs). The HSMs used are
Federal Information Processing Standards (FIPS) 140-2 Level 2 validated.
Access to a key vault requires proper authentication and authorization before a caller (user or application) can get access. Authentication establishes the identity of the caller, while authorization determines the operations that they are allowed to perform.
References:
https://docs.microsoft.com/en-us/azure/key-vault/key-vault-overview
Community vote distribution
C (100%)
Question #222Topic 1
Which Azure service can you use as a security information and event management (SIEM) solution?
- A. Azure Analysis Services
- B. Azure Sentinel
- C. Azure Information Protection
- D. Azure Cognitive Services
Correct Answer: B
Reference:
https://azure.microsoft.com/en-in/services/azure-sentinel/
Community vote distribution
B (100%)
Question #223Topic 1
HOTSPOT –
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 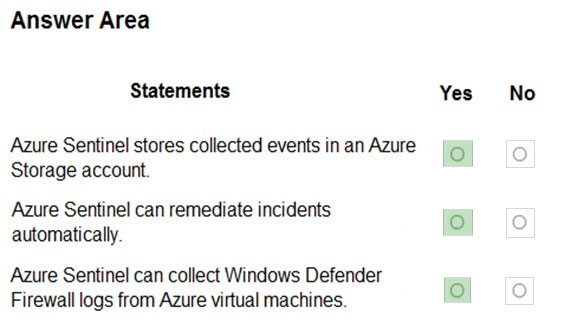
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
Question #224Topic 1
DRAG DROP –
Match the Azure Services service to the correct descriptions.
Instructions: To answer, drag the appropriate service from the column on the left to its description on the right. Each service may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place:
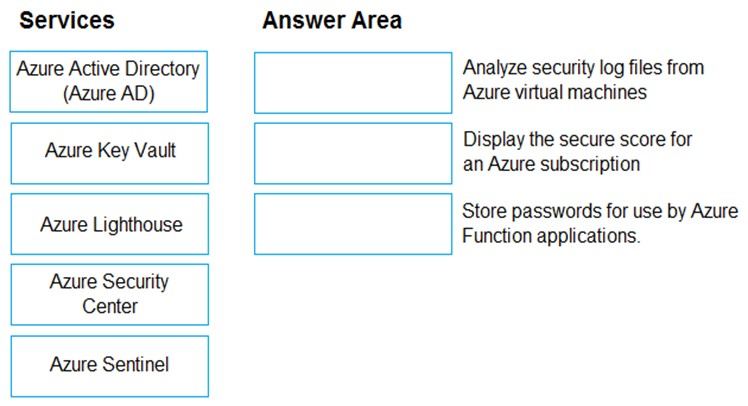
Correct Answer: Incorrect Answer:
Box 1: Azure Sentinel –
Box 2: Azure Security Center –
Box 3: Azure Key Vault –
✑ Azure Active Directory (Azure AD)
Azure AD is an identity and access management service, which helps your employees sign in and access resources
✑ Azure Lighthouse
Azure Lighthouse is used for cross- and multi-tenant management.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
https://docs.microsoft.com/en-us/azure/security-center/secure-score-security-controls https://practical365.com/securing-sensitive-information-in-azure-functions-with-the-azure-key-vault/ https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-whatis https://docs.microsoft.com/en-us/azure/lighthouse/overview
Question #225Topic 1
HOTSPOT –
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
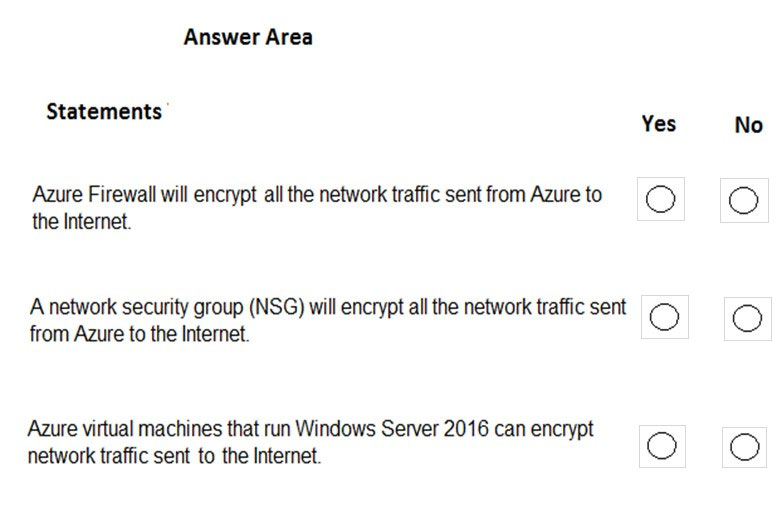
Correct Answer: 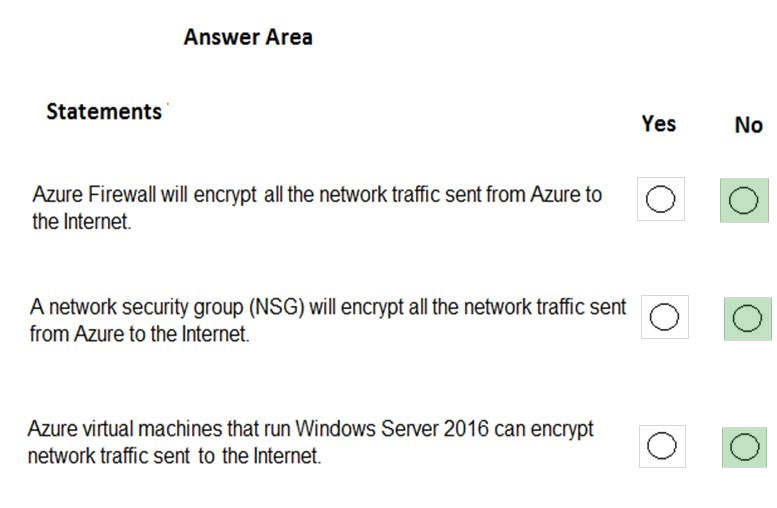
Box 1: No –
Azure firewall does not encrypt network traffic. It is used to block or allow traffic based on source/destination IP address, source/destination ports and protocol.
Box 2: No –
A network security group does not encrypt network traffic. It works in a similar way to a firewall in that it is used to block or allow traffic based on source/ destination IP address, source/destination ports and protocol.
Box 3: No –
The question is rather vague as it would depend on the configuration of the host on the Internet. Windows Server does come with a VPN client and it also supports other encryption methods such IPSec encryption or SSL/TLS so it could encrypt the traffic if the Internet host was configured to require or accept the encryption.
However, the VM could not encrypt the traffic to an Internet host that is not configured to require the encryption.
Reference:
https://docs.microsoft.com/en-us/azure/security/azure-security-data-encryption-best-practices#protect-data-in-transit
Question #226Topic 1
HOTSPOT –
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
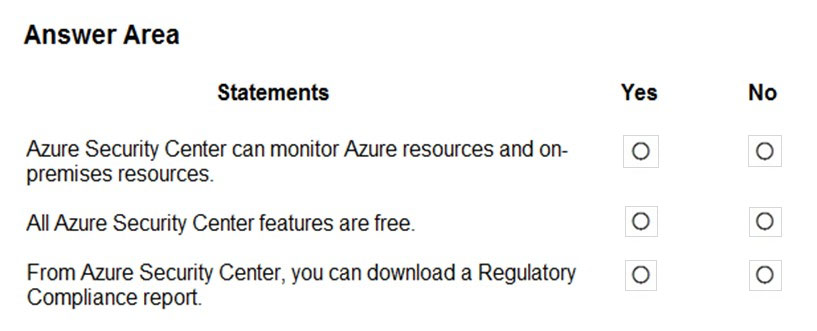
Correct Answer: 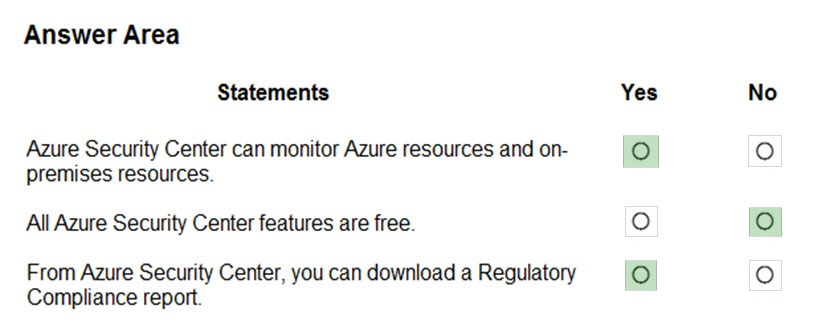
Box 1: Yes –
Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud – whether they’re in Azure or not – as well as on premises.
Box 2: No –
Only two features: Continuous assessment and security recommendations, and Azure secure score, are free.
Box 3: Yes –
The advanced monitoring capabilities in Security Center also let you track and manage compliance and governance over time. The overall compliance provides you with a measure of how much your subscriptions are compliant with policies associated with your workload.
References:
https://docs.microsoft.com/en-us/azure/security-center/security-center-intro
Question #227Topic 1
DRAG DROP –
You need to complete the defense-in-depth strategy used in a datacenter.
What should you do? To answer, drag the appropriate layers to the correct positions in the model. Each layer may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
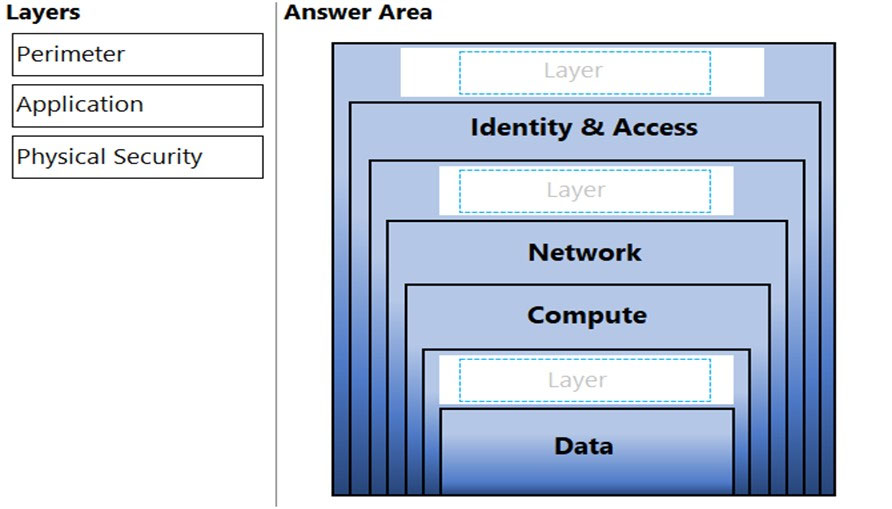
Correct Answer: 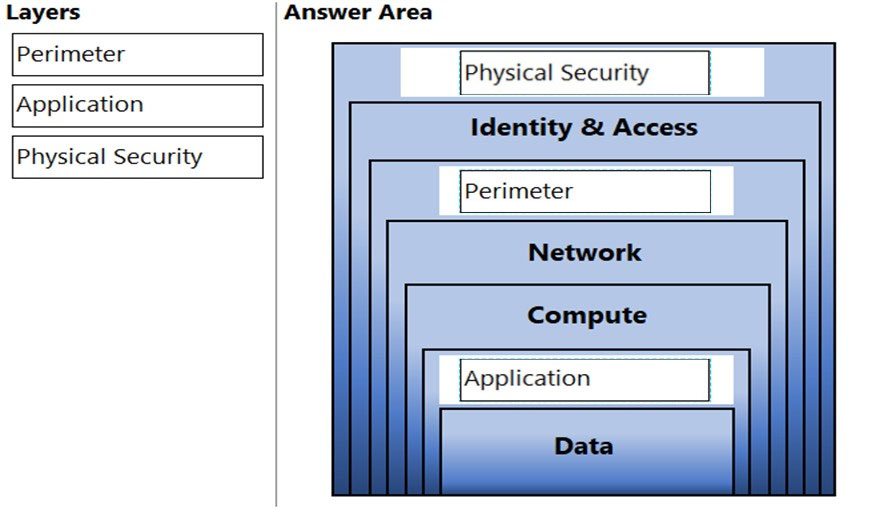
Defence in depth layers (from bottom to top):
✑ Data
– In almost all cases attackers are after data.
– Data can be in database, stored on disk inside VMs, on a SaaS application such as Office 365 or in cloud storage.
– Those storing and controlling access to data to ensures that it’s properly secured
– Often regulatory requirements dictates controls & processes
– to ensure confidentiality, integrity, and availability.
✑ Application
– Ensure applications are secure and free of vulnerabilities.
– Store sensitive application secrets in a secure storage medium.
– Make security a design requirement for all application development.
– Integrate security into the application development life cycle.
✑ Compute
– Secure access to virtual machines.
– Implement endpoint protection and keep systems patched and current.
– Malware, unpatched systems, and improperly secured systems open your environment to attacks.
✑ Networking
– Limit communication between resources.
– Deny by default.
– Allow only what is required
– Restrict inbound internet access and limit outbound, where appropriate.
– Implement secure connectivity to on-premises networks.
✑ Perimeter
– Use distributed denial of service (DDoS) protection to filter large-scale attacks before they can cause a denial of service for end users.
– Use perimeter firewalls to identify and alert on malicious attacks against your network.
✑ Identity and access
– Control access to infrastructure and change control.
– Access granted is only what is needed
– Use single sign-on and multi-factor authentication.
– Audit events and changes.
✑ Physical security
– Building security & controlling access to computing hardware.
– First line of defense.
Reference:
https://github.com/undergroundwires/Azure-in-bullet-points/blob/master/AZ-900%20Microsoft%20Azure%20Fundamentals/4.2.%20Defence%20in%20Depth.md
Question #228Topic 1
You have an Azure virtual machine named VM1.
You plan to encrypt VM1 by using Azure Disk Encryption.
Which Azure resource must you create first?
- A. an Azure Storage account
- B. an Azure Key Vault
- C. an Azure Information Protection policy
- D. an Encryption key
Correct Answer: B
Azure Disk Encryption requires an Azure Key Vault to control and manage disk encryption keys and secrets.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/disk-encryption-overview
Community vote distribution
B (100%)
Question #229Topic 1
Which resources can be used as a source for a Network security group inbound security rule?
- A. Service Tags only
- B. IP Addresses, Service tags and Application security groups
- C. Application security groups only
- D. IP Addresses only
Correct Answer: B
Source or destination:
Any, or an individual IP address, classless inter-domain routing (CIDR) block (10.0.0.0/24, for example), service tag, or application security group.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
Community vote distribution
B (100%)
Question #230Topic 1
HOTSPOT –
To complete the sentence, select the appropriate option in the answer area.
Hot Area:
Correct Answer: 
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
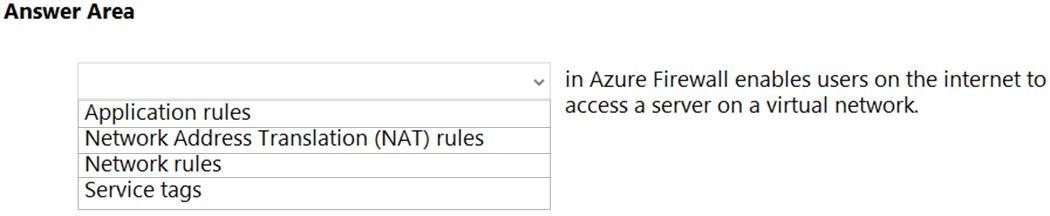
Question #231Topic 1
HOTSPOT –
To complete the sentence, select the appropriate option in the answer area.
Hot Area:
Correct Answer: 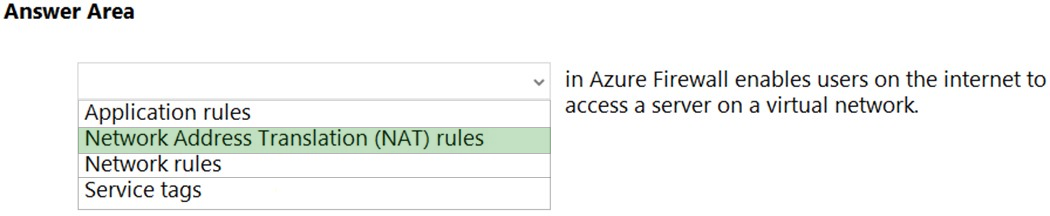
Reference:
https://docs.microsoft.com/en-us/azure/firewall/tutorial-firewall-dnat-policy
Question #232Topic 1
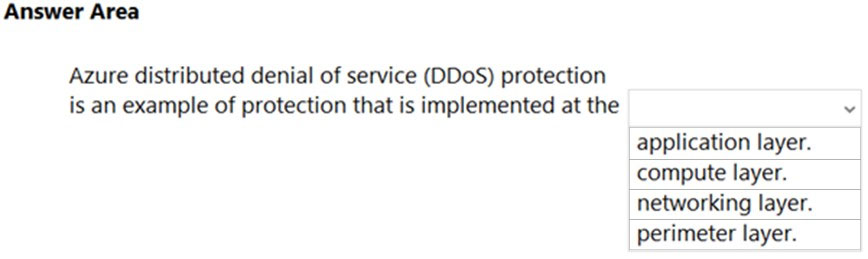
HOTSPOT –
To complete the sentence, select the appropriate option in the answer area.
Hot Area:
Correct Answer: 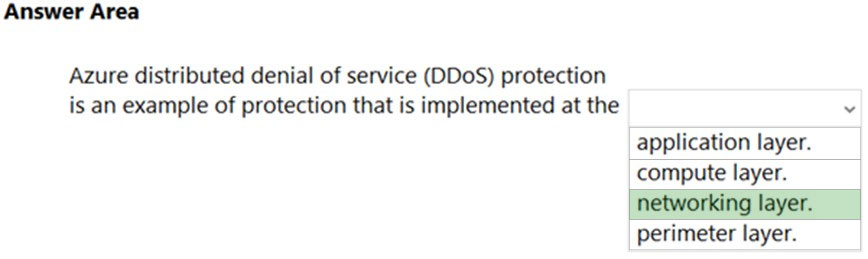
Reference:
https://docs.microsoft.com/en-us/azure/ddos-protection/ddos-protection-overview
Question #233Topic 1
You have an Azure Sentinel workspace.
You need to automate responses to threats detected by Azure Sentinel.
What should you use?
- A. adaptive network hardening in Azure Security Center
- B. Azure Service Health
- C. Azure Monitor workbooks
- D. adaptive application controls in Azure Security Center
Correct Answer: C
Community vote distribution
C (100%)
Question #234Topic 1
DRAG DROP –
Match the Azure services benefits to the correct descriptions.
Instructions: To answer, drag the appropriate benefit from the column on the left to its description on the right. Each benefit may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place:
Correct Answer: 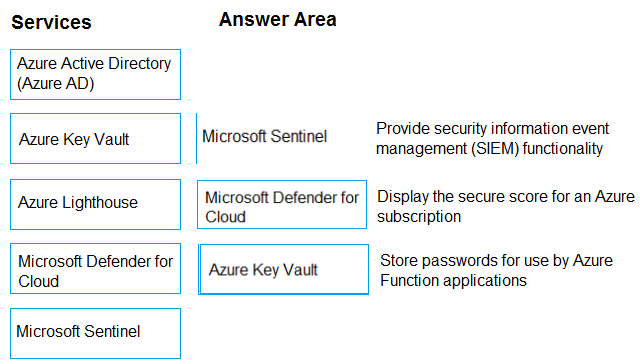
Box 1: Microsoft Sentinel –
Microsoft Sentinel is a scalable, cloud-native, security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for attack detection, threat visibility, proactive hunting, and threat response.
Box 2: Microsoft Defender for Cloud
You can find your overall secure score, as well as your score per subscription, through the Azure portal. Defender for Cloud displays your secure score prominently in the portal.
Box 3: Azure Key Vault –
A favored approach to store the credentials or keys in the Azure Key Vault as secrets and reference the secrets as environment variables in our Azure functions apps.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
https://docs.microsoft.com/en-us/azure/defender-for-cloud/secure-score-access-and-track https://levelup.gitconnected.com/a-secure-way-to-use-credentials-and-secrets-in-azure-functions-7ec91813c807
Question #235Topic 1
Which Azure service can you use as a security information and event management (SIEM) solution?
- A. Azure Analysis Services
- B. Microsoft Sentinel
- C. Azure Information Protection
- D. Azure Cognitive Services
Correct Answer: B
Microsoft Sentinel is a scalable, cloud-native, security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for attack detection, threat visibility, proactive hunting, and threat response.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
Community vote distribution
B (100%)
Question #236Topic 1
HOTSPOT –
Select the answer that correctly completes the sentence.
Hot Area:
Correct Answer: 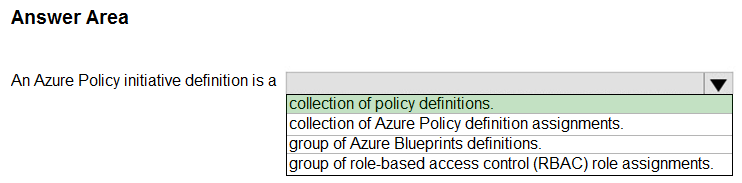
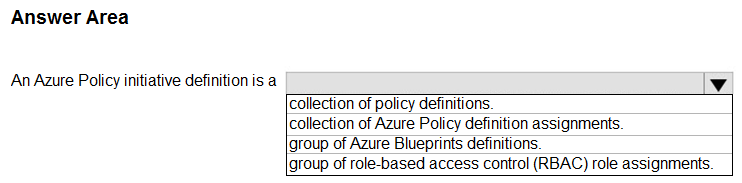
Box: collection of policy definitions
An Azure Policy initiative is a collection of Azure Policy definitions, or rules, that are grouped together towards a specific goal or purpose. Azure initiatives simplify management of your policies by grouping a set of policies together, logically, as a single item.
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/security-policy-concept
Question #237Topic 1
You have an Azure subscription.
You need to review your secure score.
What should you use?
- A. Azure Monitor
- B. Azure Advisor
- C. Help + support
- D. Microsoft Defender for Cloud
Correct Answer: D
The central feature in Defender for Cloud that enables you to achieve those goals is secure score.
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/secure-score-security-controls
Community vote distribution
D (100%)
Question #238Topic 1
HOTSPOT –
Select the answer that correctly completes the sentence.
Hot Area:

Correct Answer: 
Box: Microsoft Defender for Cloud
Lock down inbound traffic to your Azure Virtual Machines with Microsoft Defender for Cloud’s just-in-time (JIT) virtual machine (VM) access feature. This reduces exposure to attacks while providing easy access when you need to connect to a VM.
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/just-in-time-access-usage
Question #239Topic 1
HOTSPOT –
Select the answer that correctly completes the sentence.
Hot Area:
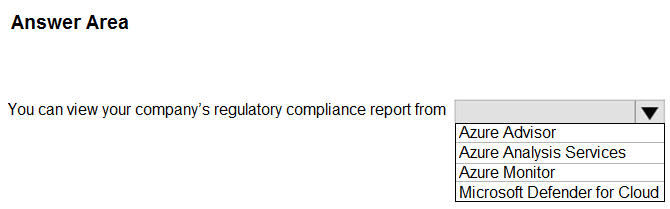
Correct Answer: 
Box: Microsoft Defender for Cloud
Microsoft Defender for Cloud helps streamline the process for meeting regulatory compliance requirements, using the regulatory compliance dashboard.
You can download PDF/CSV reports as well as certification reports of your compliance status.
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/regulatory-compliance-dashboard
Question #240Topic 1
You need to collect and automatically analyze security events from Azure Active Directory (Azure AD).
What should you use?
- A. Microsoft Sentinel
- B. Azure Synapse Analytics
- C. Azure AD Connect
- D. Azure Key Vault
Correct Answer: A
Microsoft Sentinel is a scalable, cloud-native, security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution.
Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for attack detection, threat visibility, proactive hunting, and threat response.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
Community vote distribution
A (100%)
Question #241Topic 1
HOTSPOT –
Select the answer that correctly completes the sentence.
Hot Area:
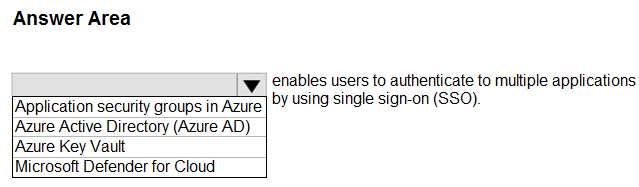
Correct Answer: 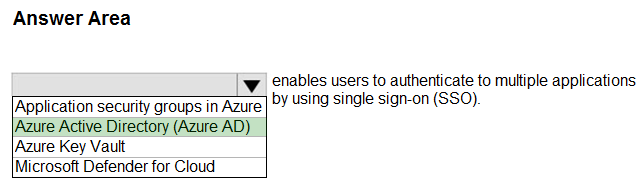
Box: Azure Active Directory (Azure AD)
You can enable single sign-on for an enterprise application through Azure Active Directory (Azure AD.
Incorrect:
Application security groups enable you to configure network security as a natural extension of an application’s structure, allowing you to group virtual machines and define network security policies based on those groups.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/add-application-portal-setup-sso
Question #242Topic 1
HOTSPOT –
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer: 
Box 1: No –
Azure creates the default rules in each network security group that you create. These rules allow some traffic.
Box 2: Yes –
A network security group contains zero, or as many rules as desired. These rules can refer to application security groups.
Box 3: Yes –
Azure creates the Inbound and OutBound default rules in each network security group that you create.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
Question #243Topic 1
DRAG DROP –
Match the term to the appropriate description.
To answer, drag the appropriate term from the column on the left to its description on the right. Each term may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place:
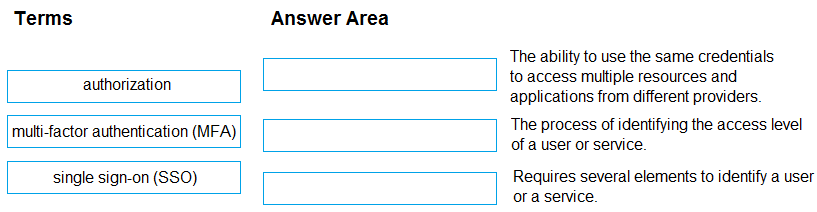
Correct Answer: 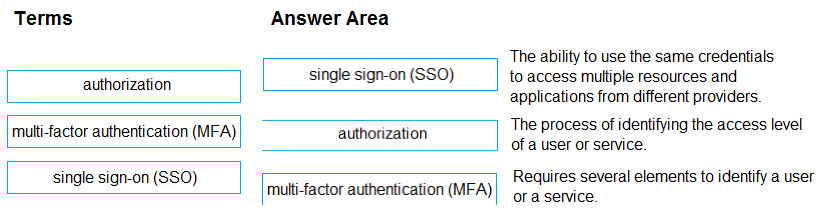
Question #244Topic 1
Your company plans to automate the deployment of servers to Azure.
Your manager is concerned that you may expose administrative credentials during the deployment.
You need to recommend an Azure solution that encrypts the administrative credentials during the deployment.
What should you include in the recommendation?
- A. Azure Key Vault
- B. Azure Information Protection
- C. Microsoft Defender for Cloud
- D. Azure Multi-Factor Authentication (MFA)
Correct Answer: A
Azure Key Vault protects cryptographic keys, certificates (and the private keys associated with the certificates), and secrets (such as connection strings and passwords) in the cloud.
Reference:
https://docs.microsoft.com/en-us/azure/key-vault/general/security-features
Community vote distribution
A (100%)
Question #245Topic 1
HOTSPOT –
Select the answer that correctly completes the sentence.
Hot Area:
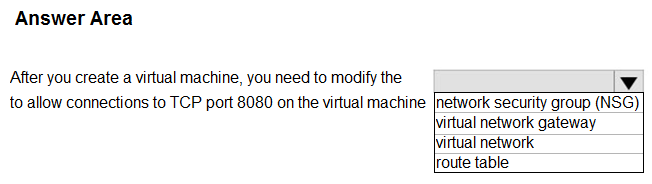
Correct Answer: 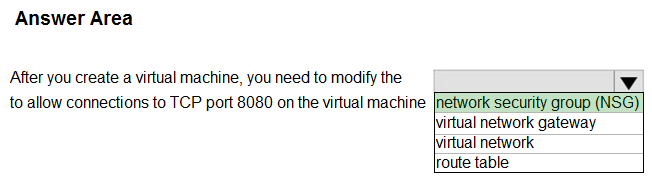
Box: network Security group (NSG)
You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
Question #246Topic 1
HOTSPOT –
Select the answer that correctly completes the sentence.
Hot Area:

Correct Answer: 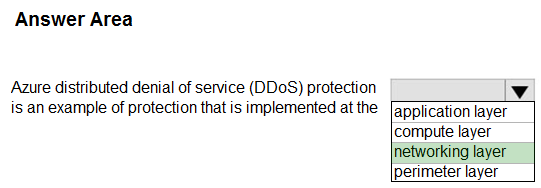
Box: networking layer –
DDoS Protection defends against a comprehensive set of network layer (layer 3/4) attacks.
Reference:
https://azure.microsoft.com/en-us/services/ddos-protection
Question #247Topic 1
HOTSPOT –
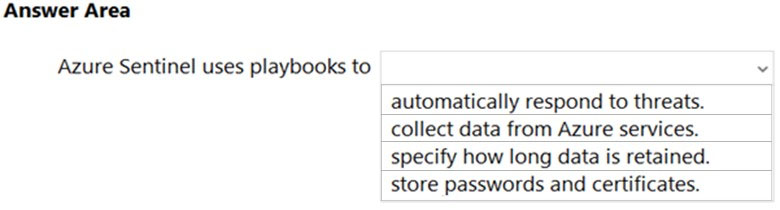
Select the answer that correctly completes the sentence.
Hot Area:
Correct Answer: 
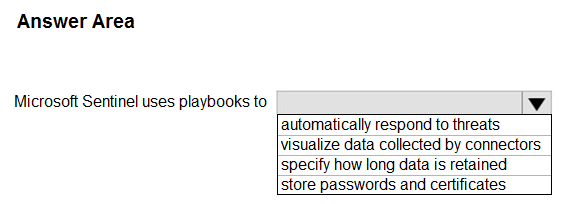
Box: automatically respond to threats
Playbooks are collections of procedures that can be run from Microsoft Sentinel in response to an alert or incident. A playbook can help automate and orchestrate your response, and can be set to run automatically when specific alerts or incidents are generated, by being attached to an analytics rule or an automation rule, respectively.
Note: Automation rules help you triage incidents in Microsoft Sentinel. You can use them to automatically assign incidents to the right personnel, close noisy incidents or known false positives, change their severity, and add tags. They are also the mechanism by which you can run playbooks in response to incidents.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
Question #248Topic 1
You need to configure an Azure solution that meets the following requirements:
✑ Secures websites from attacks
✑ Generates reports that contain details of attempted attacks
What should you include in the solution?
- A. Azure Firewall
- B. a network security group (NSG)
- C. Azure Information Protection
- D. DDoS protection
Correct Answer: D
DDoS is a type of attack that tries to exhaust application resources. The goal is to affect the application’s availability and its ability to handle legitimate requests.
DDoS attacks can be targeted at any endpoint that is publicly reachable through the internet.
Azure has two DDoS service offerings that provide protection from network attacks: DDoS Protection Basic and DDoS Protection Standard.
DDoS Basic protection is integrated into the Azure platform by default and at no extra cost.
You have the option of paying for DDoS Standard. It has several advantages over the basic service, including logging, alerting, and telemetry. DDoS Standard can generate reports that contain details of attempted attacks as required in this question.
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/ddos-best-practices
Community vote distribution
D (100%)
Question #249Topic 1
HOTSPOT –
You plan to implement several security services for an Azure environment. You need to identify which Azure services must be used to meet the following security requirements:
✑ Monitor threats by using sensors
✑ Enforce Azure Multi-Factor Authentication (MFA) based on a condition
Which Azure service should you identify for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer: 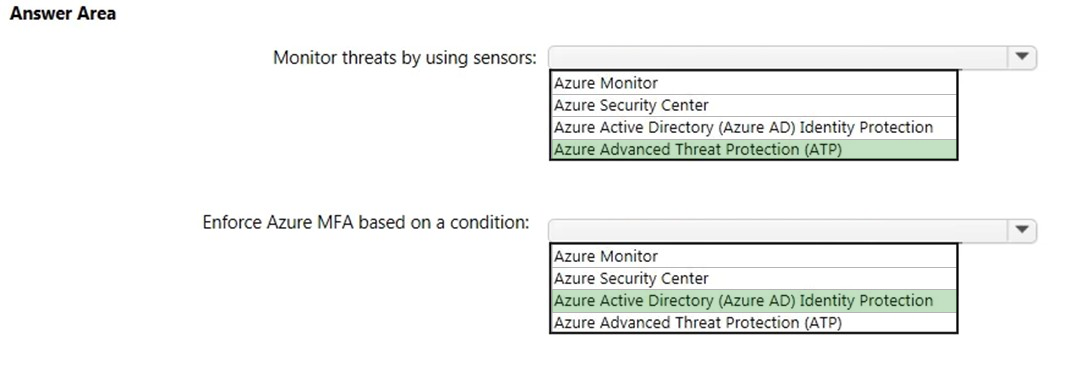
Box 1:
To monitor threats by using sensors, you would use Azure Advanced Threat Protection (ATP).
Azure Advanced Threat Protection (ATP) is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Sensors are software packages you install on your servers to upload information to Azure ATP.
Box 2:
To enforce MFA based on a condition, you would use Azure Active Directory Identity Protection.
Azure AD Identity Protection helps you manage the roll-out of Azure Multi-Factor Authentication (MFA) registration by configuring a Conditional Access policy to require MFA registration no matter what modern authentication app you are signing in to.
References:
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/what-is-atp https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-mfa-policy

