Free AWS Dump, Free Dumps
Free AWS SOA-C02 Dump
Question #40
A company runs an application on an Amazon EC2 instance. A SysOps administrator creates an Auto Scaling group and an Application Load Balancer (ALB) to handle an increase in demand. However, the EC2 instances are failing the health check.
What should the SysOps administrator do to troubleshoot this issue?
- A. Verify that the Auto Scaling group is configured to use all AWS Regions.
- B. Verify that the application is running on the protocol and the port that the listener is expecting.
- C. Verify the listener priority in the ALB. Change the priority if necessary.
- D. Verify the maximum number of instances in the Auto Scaling group. Change the number if necessary.
Correct Answer: D
Community vote distribution
B (96%)
Question #41
A SysOps administrator has created an AWS Service Catalog portfolio and has shared the portfolio with a second AWS account in the company. The second account is controlled by a different administrator.
Which action will the administrator of the second account be able to perform?
- A. Add a product from the imported portfolio to a local portfolio.
- B. Add new products to the imported portfolio.
- C. Change the launch role for the products contained in the imported portfolio.
- D. Customize the products in the imported portfolio.
Correct Answer: A
Community vote distribution
A (100%)
Question #42
A company has migrated its application to AWS. The company will host the application on Amazon EC2 instances of multiple instance families.
During initial testing, a SysOps administrator identifies performance issues on selected EC2 instances. The company has a strict budget allocation policy, so the
SysOps administrator must use the right resource types with the performance characteristics to match the workload.
What should the SysOps administrator do to meet this requirement?
- A. Purchase regional Reserved Instances (RIs) for immediate cost savings. Review and take action on the EC2 rightsizing recommendations in Cost Explorer. Exchange the RIs for the optimal instance family after rightsizing.
- B. Purchase zonal Reserved Instances (RIs) for the existing instances. Monitor the RI utilization in the AWS Billing and Cost Management console. Make adjustments to instance sizes to optimize utilization.
- C. Review and take action on AWS Compute Optimizer recommendations. Purchase Compute Savings Plans to reduce the cost that is required to run the compute resources.
- D. Review resource utilization metrics in the AWS Cost and Usage Report. Rightsize the EC2 instances. Create On-Demand Capacity Reservations for the rightsized resources.
Correct Answer: C
Community vote distribution
C (100%)
Question #43
A SysOps administrator is tasked with deploying a company’s infrastructure as code. The SysOps administrator want to write a single template that can be reused for multiple environments.
How should the SysOps administrator use AWS CloudFormation to create a solution?
- A. Use Amazon EC2 user data in a CloudFormation template.
- B. Use nested stacks to provision resources.
- C. Use parameters in a CloudFormation template.
- D. Use stack policies to provision resources.
Correct Answer: C
Community vote distribution
C (100%)
Question #44
A SysOps administrator is responsible for a large fleet of Amazon EC2 instances and must know whether any instances will be affected by upcoming hardware maintenance.
Which option would provide this information with the LEAST administrative overhead?
- A. Deploy a third-party monitoring solution to provide real-time EC2 instance monitoring.
- B. List any instances with failed system status checks using the AWS Management Console.
- C. Monitor AWS CloudTrail for StopInstances API calls.
- D. Review the AWS Personal Health Dashboard.
Correct Answer: D
Community vote distribution
D (100%)
Question #45
A SysOps administrator is attempting to deploy resources by using an AWS CloudFormation template. An Amazon EC2 instance that is defined in the template fails to launch and produces an InsufficientInstanceCapacity error.
Which actions should the SysOps administrator take to resolve this error? (Choose two.)
- A. Create a separate AWS CloudFormation template for the EC2 instance.
- B. Modify the AWS CloudFormation template to not specify an Availability Zone for the EC2 instance.
- C. Modify the AWS CloudFormation template to use a different EC2 instance type.
- D. Use a different Amazon Machine Image (AMI) for the EC2 instance.
- E. Use the AWS CLI’s validate-template command before creating a stack from the template.
Correct Answer: BC
Community vote distribution
BC (100%)
Question #46
A company hosts a web application on Amazon EC2 instances behind an Application Load Balancer (ALB). The company uses Amazon Route 53 to route traffic.
The company also has a static website that is configured in an Amazon S3 bucket.
A SysOps administrator must use the static website as a backup to the web application. The failover to the static website must be fully automated.
Which combination of actions will meet these requirements? (Choose two.)
- A. Create a primary failover routing policy record. Configure the value to be the ALB.
- B. Create an AWS Lambda function to switch from the primary website to the secondary website when the health check fails.
- C. Create a primary failover routing policy record. Configure the value to be the ALB. Associate the record with a Route 53 health check.
- D. Create a secondary failover routing policy record. Configure the value to be the static website. Associate the record with a Route 53 health check.
- E. Create a secondary failover routing policy record. Configure the value to be the static website.
Correct Answer: CD
Community vote distribution
CE (68%)
CD (23%)
Question #47
A data analytics application is running on an Amazon EC2 instance. A SysOps administrator must add custom dimensions to the metrics collected by the Amazon
CloudWatch agent.
How can the SysOps administrator meet this requirement?
- A. Create a custom shell script to extract the dimensions and collect the metrics using the Amazon CloudWatch agent.
- B. Create an Amazon EventBridge (Amazon CloudWatch Events) rule to evaluate the required custom dimensions and send the metrics to Amazon Simple Notification Service (Amazon SNS).
- C. Create an AWS Lambda function to collect the metrics from AWS CloudTrail and send the metrics to an Amazon CloudWatch Logs group.
- D. Create an append_dimensions field in the Amazon CloudWatch agent configuration file to collect the metrics.
Correct Answer: D
Community vote distribution
D (100%)
Question #48
A company stores its data in an Amazon S3 bucket. The company is required to classify the data and find any sensitive personal information in its S3 files.
Which solution will meet these requirements?
- A. Create an AWS Config rule to discover sensitive personal information in the S3 files and mark them as noncompliant.
- B. Create an S3 event-driven artificial intelligence/machine learning (AI/ML) pipeline to classify sensitive personal information by using Amazon Rekognition.
- C. Enable Amazon GuardDuty. Configure S3 protection to monitor all data inside Amazon S3.
- D. Enable Amazon Macie. Create a discovery job that uses the managed data identifier.
Correct Answer: D
Community vote distribution
D (100%)
Question #49
A company hosts a web portal on Amazon EC2 instances. The web portal uses an Elastic Load Balancer (ELB) and Amazon Route 53 for its public DNS service.
The ELB and the EC2 instances are deployed by way of a single AWS CloudFormation stack in the us-east-1 Region. The web portal must be highly available across multiple Regions.
Which configuration will meet these requirements?
- A. Deploy a copy of the stack in the us-west-2 Region. Create a single start of authority (SOA) record in Route 53 that includes the IP address from each ELB. Configure the SOA record with health checks. Use the ELB in us-east-1 as the primary record and the ELB in us-west-2 as the secondary record.
- B. Deploy a copy of the stack in the us-west-2 Region. Create an additional A record in Route 53 that includes the ELB in us-west-2 as an alias target. Configure the A records with a failover routing policy and health checks. Use the ELB in us-east-1 as the primary record and the ELB in us-west-2 as the secondary record.
- C. Deploy a new group of EC2 instances in the us-west-2 Region. Associate the new EC2 instances with the existing ELB, and configure load balancer health checks on all EC2 instances. Configure the ELB to update Route 53 when EC2 instances in us-west-2 fail health checks.
- D. Deploy a new group of EC2 instances in the us-west-2 Region. Configure EC2 health checks on all EC2 instances in each Region. Configure a peering connection between the VPCs. Use the VPC in us-east-1 as the primary record and the VPC in us-west-2 as the secondary record.
Correct Answer: A
Community vote distribution
B (100%)
Question #50
A SysOps administrator is investigating why a user has been unable to use RDP to connect over the internet from their home computer to a bastion server running on an Amazon EC2 Windows instance.
Which of the following are possible causes of this issue? (Choose two.)
- A. A network ACL associated with the bastion’s subnet is blocking the network traffic.
- B. The instance does not have a private IP address.
- C. The route table associated with the bastion’s subnet does not have a route to the internet gateway.
- D. The security group for the instance does not have an inbound rule on port 22.
- E. The security group for the instance does not have an outbound rule on port 3389.
Correct Answer: AC
Community vote distribution
AC (100%)
Question #51
A SysOps administrator is examining the following AWS CloudFormation template:
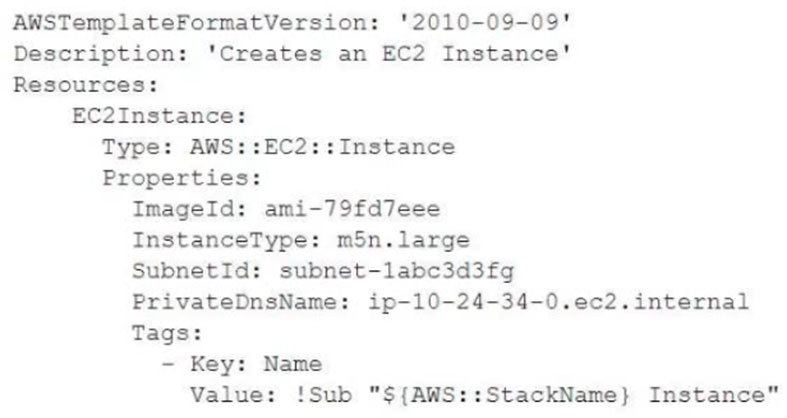
Why will the stack creation fail?
- A. The Outputs section of the CloudFormation template was omitted.
- B. The Parameters section of the CloudFormation template was omitted.
- C. The PrivateDnsName cannot be set from a CloudFormation template.
- D. The VPC was not specified in the CloudFormation template.
Correct Answer: C
Community vote distribution
C (100%)
Question #52
A new application runs on Amazon EC2 instances and accesses data in an Amazon RDS database instance. When fully deployed in production, the application fails. The database can be queried from a console on a bastion host. When looking at the web server logs, the following error is repeated multiple times:
*** Error Establishing a Database Connection
Which of the following may be causes of the connectivity problems? (Choose two.)
- A. The security group for the database does not have the appropriate egress rule from the database to the web server.
- B. The certificate used by the web server is not trusted by the RDS instance.
- C. The security group for the database does not have the appropriate ingress rule from the web server to the database.
- D. The port used by the application developer does not match the port specified in the RDS configuration.
- E. The database is still being created and is not available for connectivity.
Correct Answer: CE
Community vote distribution
CD (91%)
4%
Question #53
A compliance team requires all administrator passwords for Amazon RDS DB instances to be changed at least annually.
Which solution meets this requirement in the MOST operationally efficient manner?
- A. Store the database credentials in AWS Secrets Manager. Configure automatic rotation for the secret every 365 days.
- B. Store the database credentials as a parameter in the RDS parameter group. Create a database trigger to rotate the password every 365 days.
- C. Store the database credentials in a private Amazon S3 bucket. Schedule an AWS Lambda function to generate a new set of credentials every 365 days.
- D. Store the database credentials in AWS Systems Manager Parameter Store as a secure string parameter. Configure automatic rotation for the parameter every 365 days.
Correct Answer: A
Community vote distribution
A (100%)
Question #54
A SysOps administrator is responsible for managing a fleet of Amazon EC2 instances. These EC2 instances upload build artifacts to a third-party service. The third-party service recently implemented a strict IP allow list that requires all build uploads to come from a single IP address.
What change should the systems administrator make to the existing build fleet to comply with this new requirement?
- A. Move all of the EC2 instances behind a NAT gateway and provide the gateway IP address to the service.
- B. Move all of the EC2 instances behind an internet gateway and provide the gateway IP address to the service.
- C. Move all of the EC2 instances into a single Availability Zone and provide the Availability Zone IP address to the service.
- D. Move all of the EC2 instances to a peered VPC and provide the VPC IP address to the service.
Correct Answer: A
Community vote distribution
A (100%)
Question #55
A company uses an Amazon CloudFront distribution to deliver its website. Traffic logs for the website must be centrally stored, and all data must be encrypted at rest.
Which solution will meet these requirements?
- A. Create an Amazon OpenSearch Service (Amazon Elasticsearch Service) domain with internet access and server-side encryption that uses the default AWS managed customer master key (CMK). Configure CloudFront to use the Amazon OpenSearch Service (Amazon Elasticsearch Service) domain as a log destination.
- B. Create an Amazon OpenSearch Service (Amazon Elasticsearch Service) domain with VPC access and server-side encryption that uses AES-256. Configure CloudFront to use the Amazon OpenSearch Service (Amazon Elasticsearch Service) domain as a log destination.
- C. Create an Amazon S3 bucket that is configured with default server-side encryption that uses AES-256. Configure CloudFront to use the S3 bucket as a log destination.
- D. Create an Amazon S3 bucket that is configured with no default encryption. Enable encryption in the CloudFront distribution, and use the S3 bucket as a log destination.
Correct Answer: C
Community vote distribution
C (100%)
Question #56
An organization created an Amazon Elastic File System (Amazon EFS) volume with a file system ID of fs-85ba41fc, and it is actively used by 10 Amazon EC2 hosts. The organization has become concerned that the file system is not encrypted.
How can this be resolved?
- A. Enable encryption on each host’s connection to the Amazon EFS volume. Each connection must be recreated for encryption to take effect.
- B. Enable encryption on the existing EFS volume by using the AWS Command Line Interface.
- C. Enable encryption on each host’s local drive. Restart each host to encrypt the drive.
- D. Enable encryption on a newly created volume and copy all data from the original volume. Reconnect each host to the new volume.
Correct Answer: D
Community vote distribution
D (92%)
Question #57
A company uses an AWS Service Catalog portfolio to create and manage resources. A SysOps administrator must create a replica of the company’s existing AWS infrastructure in a new AWS account.
What is the MOST operationally efficient way to meet this requirement?
- A. Create an AWS CloudFormation template to use the AWS Service Catalog portfolio in the new AWS account.
- B. In the new AWS account, manually create an AWS Service Catalog portfolio that duplicates the original portfolio.
- C. Run an AWS Lambda function to create a new AWS Service Catalog portfolio based on the output of the DescribePortfolio API operation.
- D. Share the AWS Service Catalog portfolio with the new AWS account. Import the portfolio into the new AWS account.
Correct Answer: D
Community vote distribution
D (100%)
Question #58
A SysOps administrator must manage the security of an AWS account. Recently, an IAM user’s access key was mistakenly uploaded to a public code repository.
The SysOps administrator must identify anything that was changed by using this access key.
How should the SysOps administrator meet these requirements?
- A. Create an Amazon EventBridge (Amazon CloudWatch Events) rule to send all IAM events to an AWS Lambda function for analysis.
- B. Query Amazon EC2 logs by using Amazon CloudWatch Logs Insights for all events initiated with the compromised access key within the suspected timeframe.
- C. Search AWS CloudTrail event history for all events initiated with the compromised access key within the suspected timeframe.
- D. Search VPC Flow Logs for all events initiated with the compromised access key within the suspected timeframe.
Correct Answer: C
Community vote distribution
C (100%)
Question #59
A company runs a retail website on multiple Amazon EC2 instances behind an Application Load Balancer (ALB). The company must secure traffic to the website over an HTTPS connection.
Which combination of actions should a SysOps administrator take to meet these requirements? (Choose two.)
- A. Attach the certificate to each EC2 instance.
- B. Attach the certificate to the ALB.
- C. Create a private certificate in AWS Certificate Manager (ACM).
- D. Create a public certificate in AWS Certificate Manager (ACM).
- E. Export the certificate, and attach it to the website.
Correct Answer: BD
Community vote distribution
BD (100%)
Question #60
SIMULATION –
Instructions –
If the copy-paste functionality is not working in your environment, refer to the instructions file on the VM desktop and use Ctrl+C, Ctrl+V or Command-C,
Command-V.
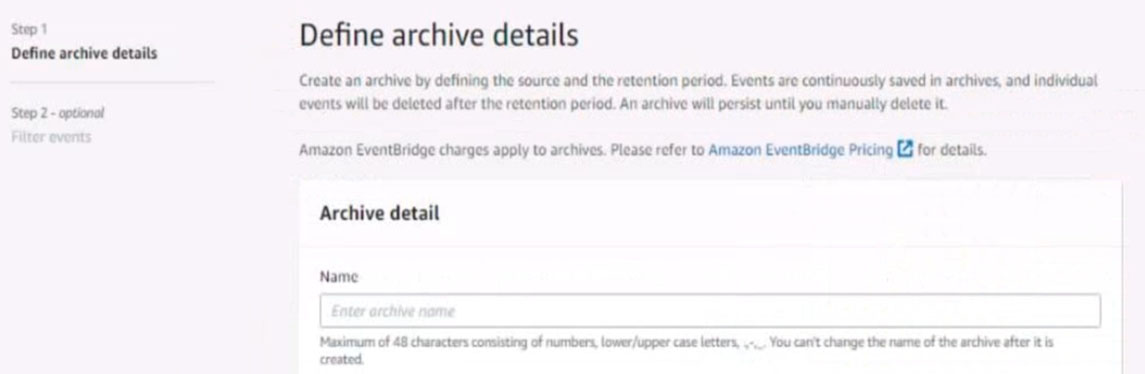
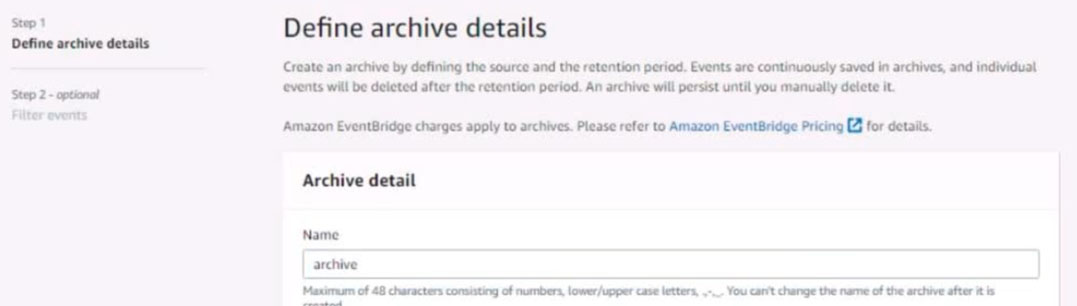
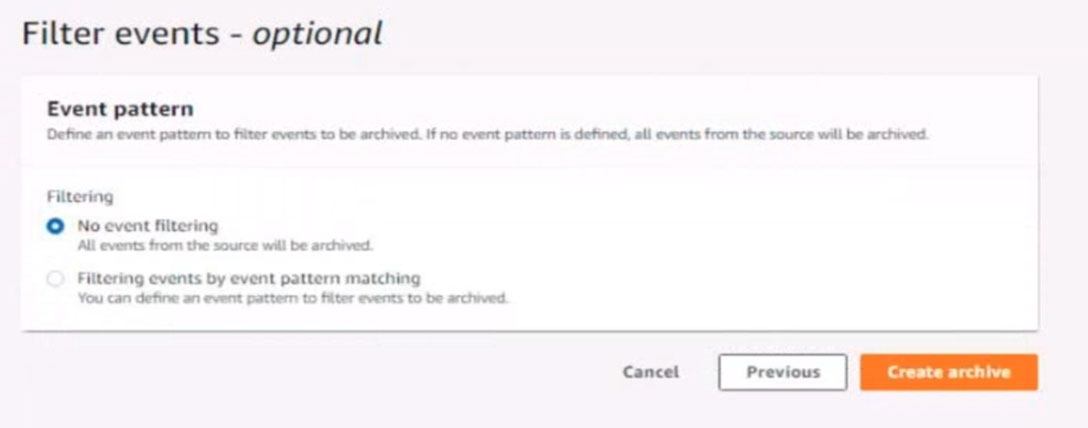
Configure Amazon EventBridge to meet the following requirements.
1. Use the us-east-2 Region for all resources.
2. Unless specified below, use the default configuration settings.
3. Use your own resource naming unless a resource name is specified below.
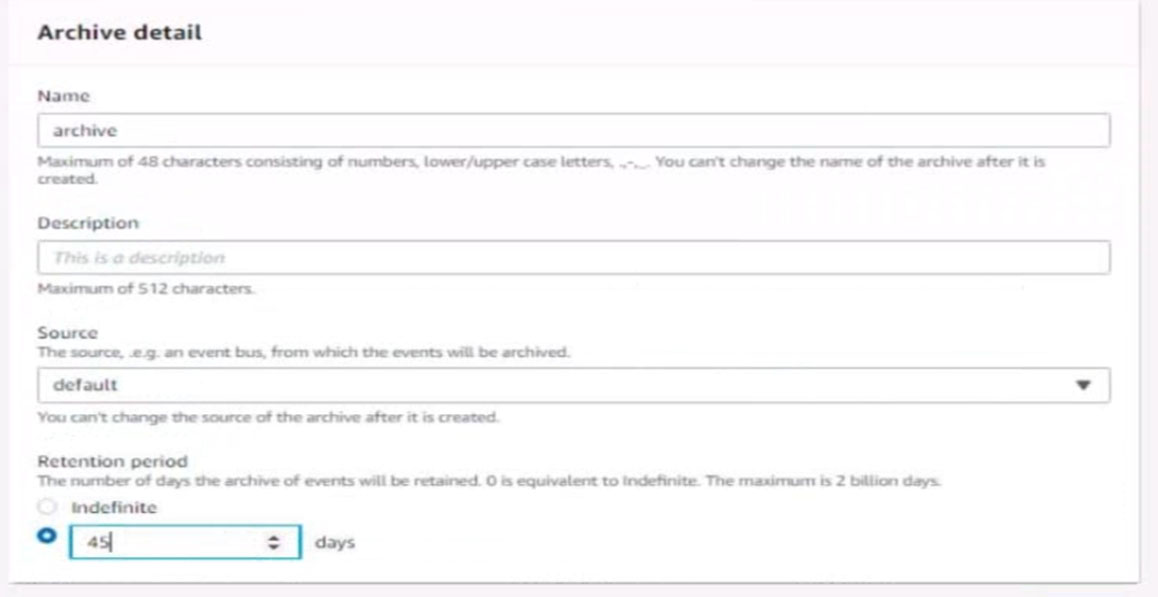
4. Ensure all Amazon EC2 events in the default event bus are replayable for the past 45 days.
5. Create a rule named RunFunction to send the exact message {“name”:”example”) every 15 minutes to an existing AWS Lambda function named LogEventFunction
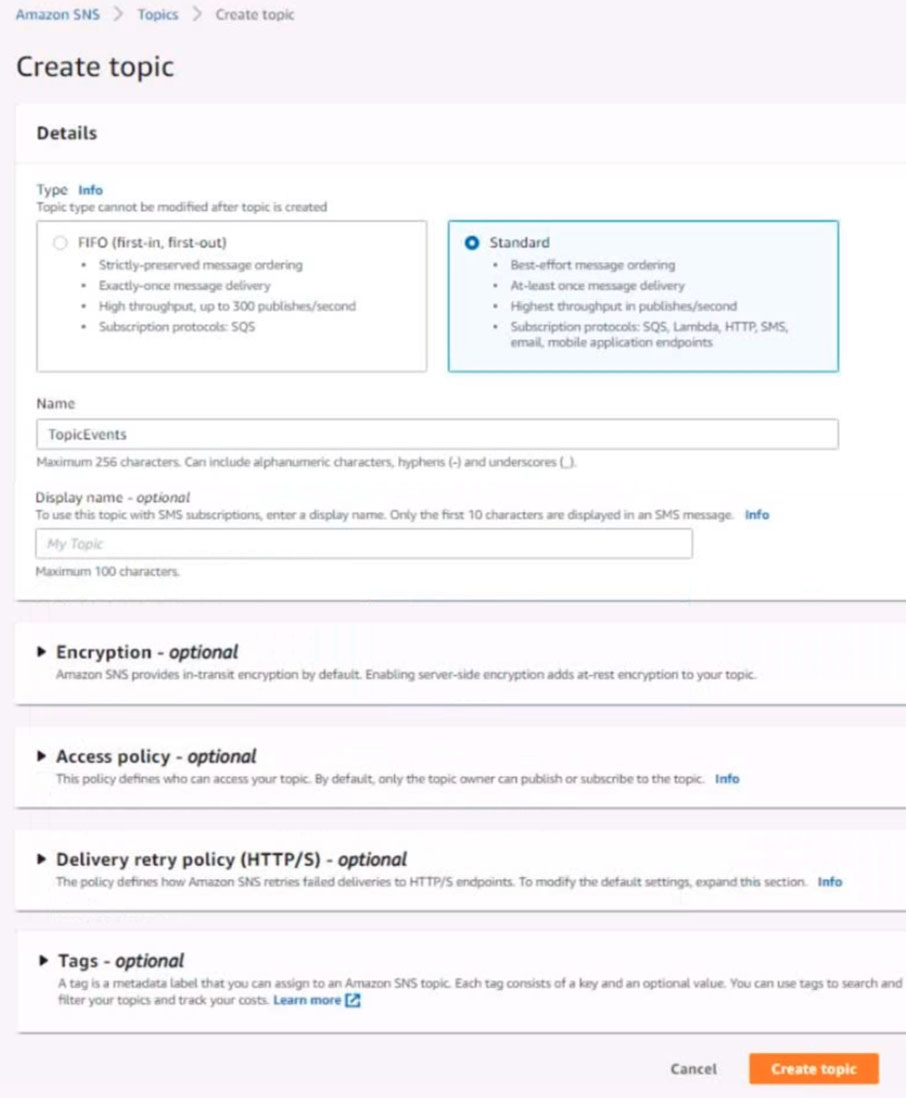
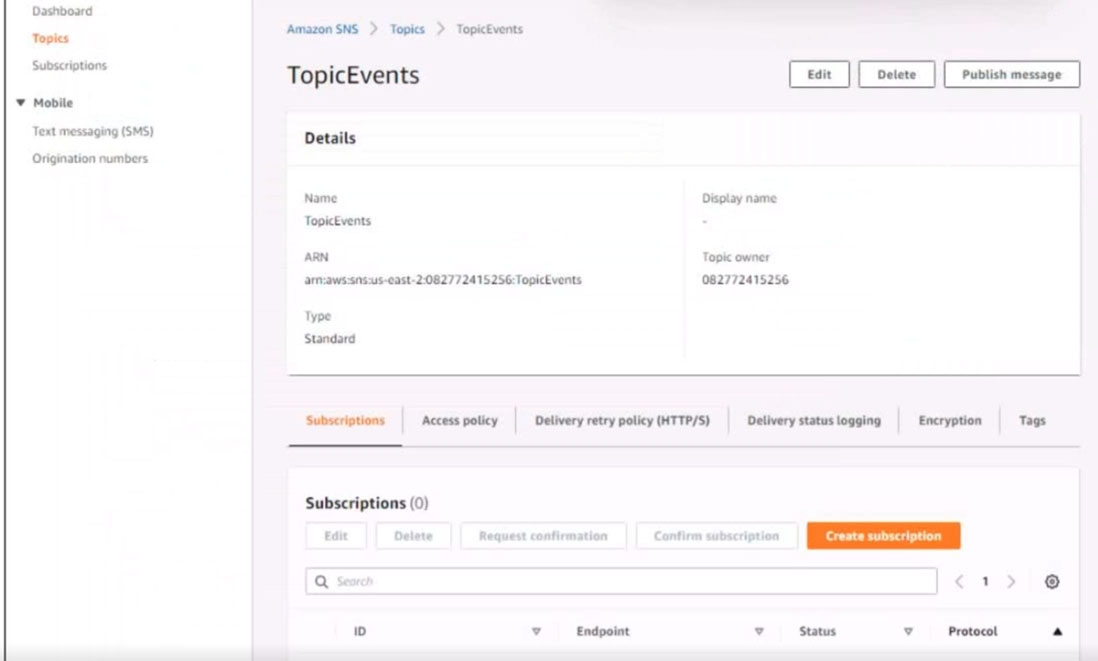
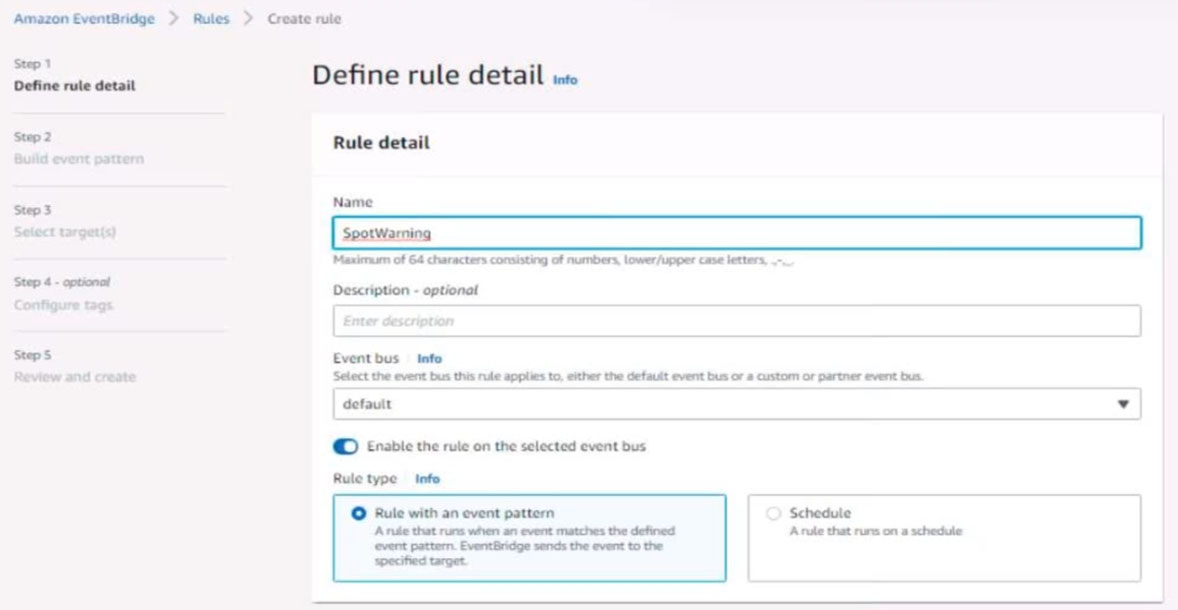
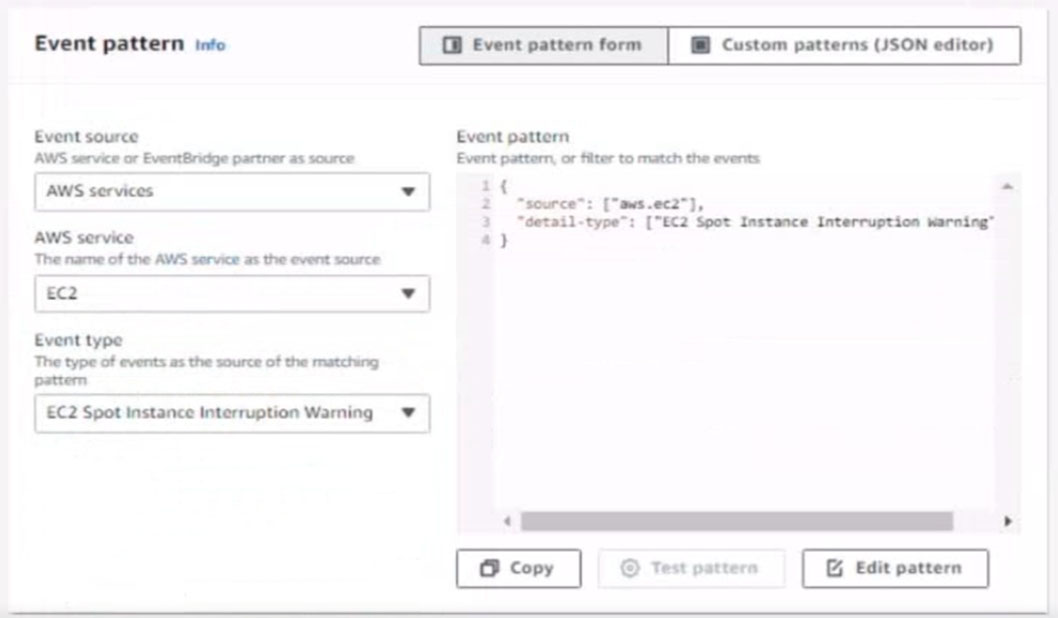
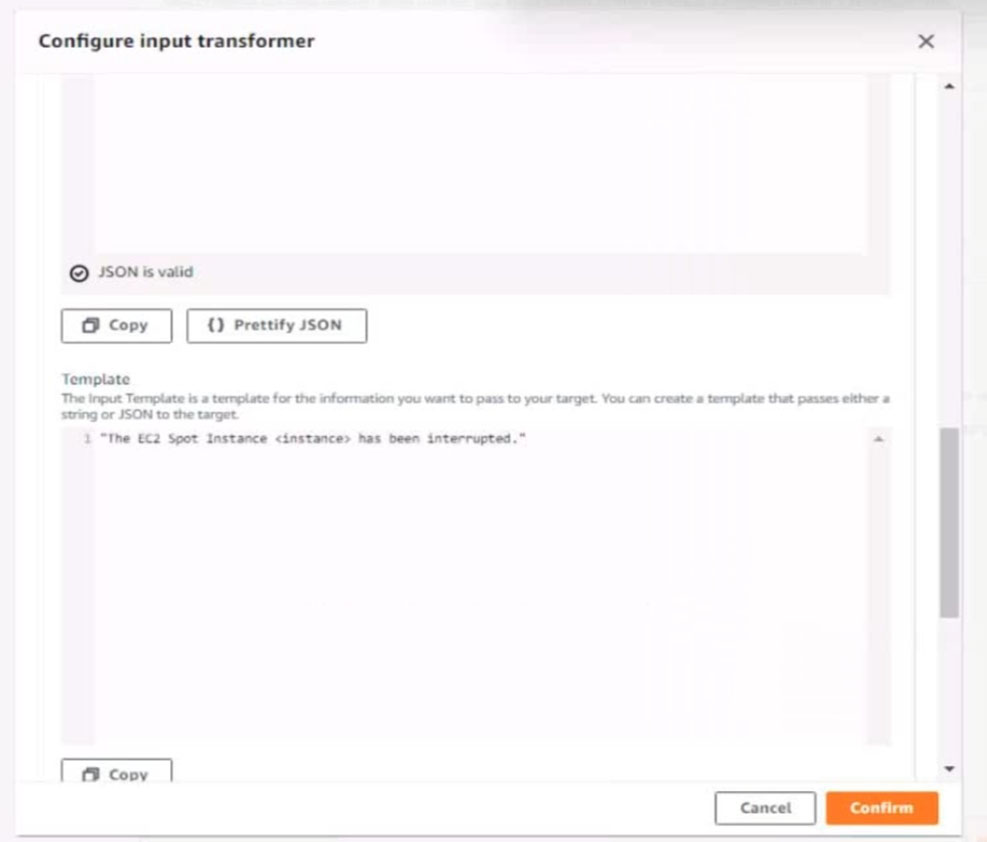
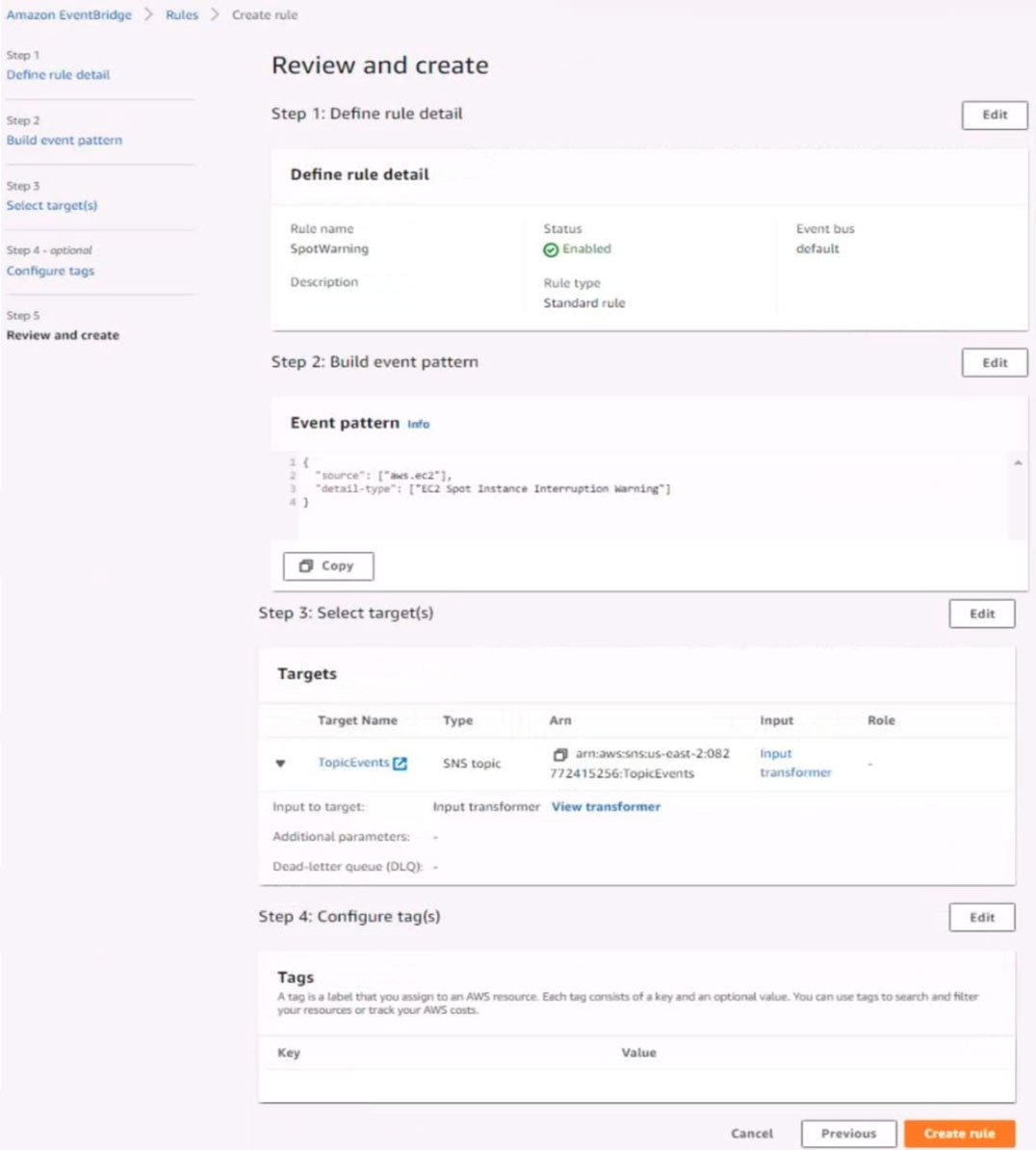
6. Create a rule named SpotWarning to send a notification to a new standard Amazon SNS topic named TopicEvents whenever an Amazon EC2 Spot Instance is interrupted. Do NOT create any topic subscriptions. The notification must match the following structure:
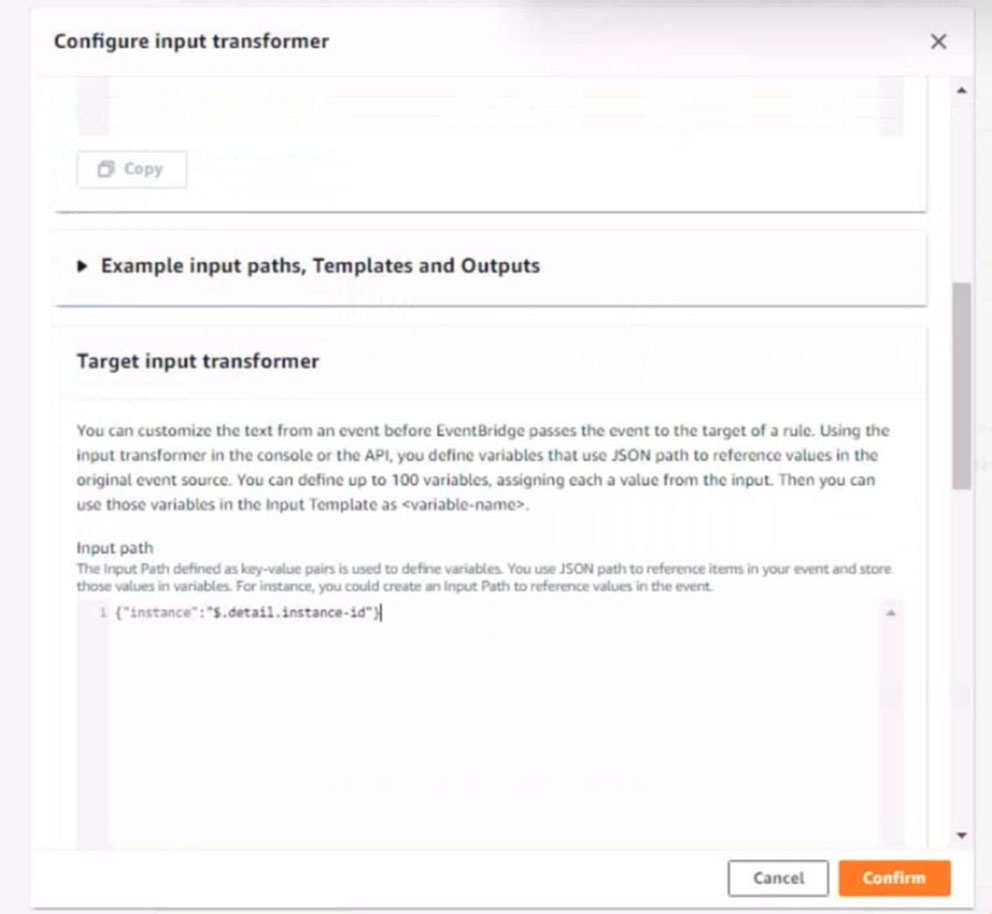
Input path:
{`instance`:`detail.instance-id}
Input template:
`The EC2 Spot Instance <instance> has been interrupted.`
Important: Click the Next button to complete this lab and continue to the next lab. Once you click the Next button, you will NOT be able to return to this lab.
Correct Answer: See explanation below.
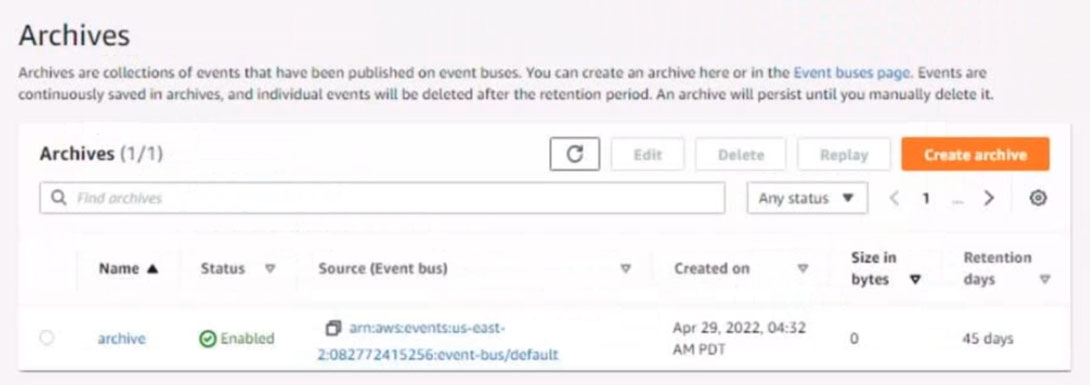
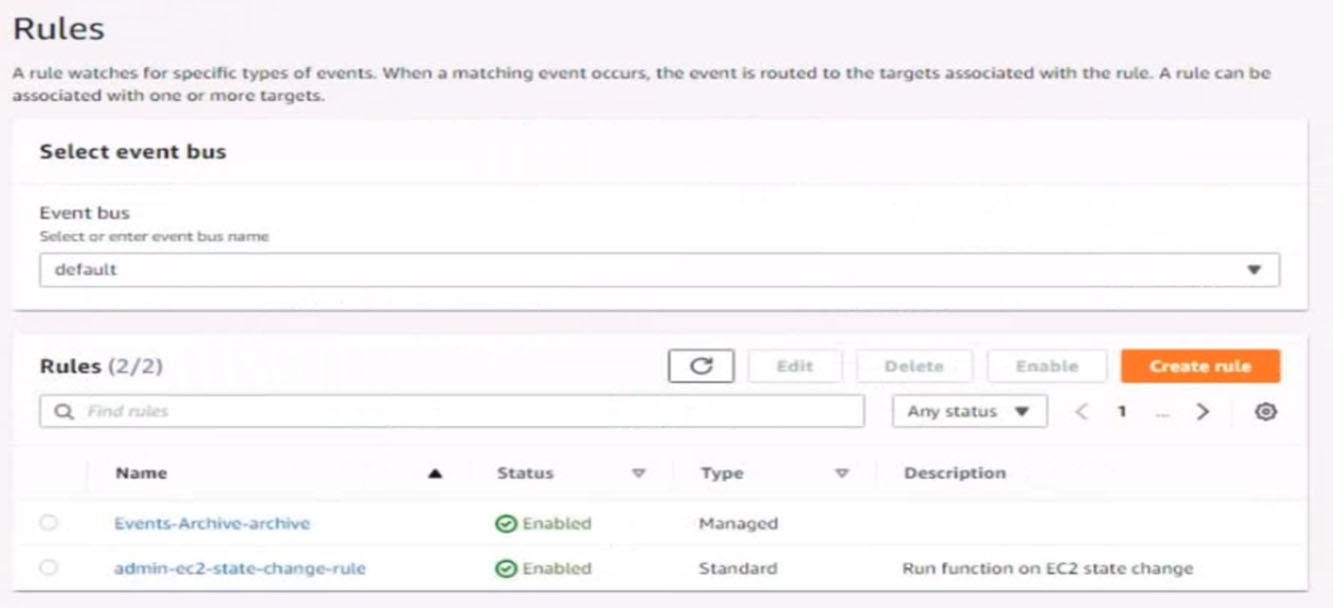
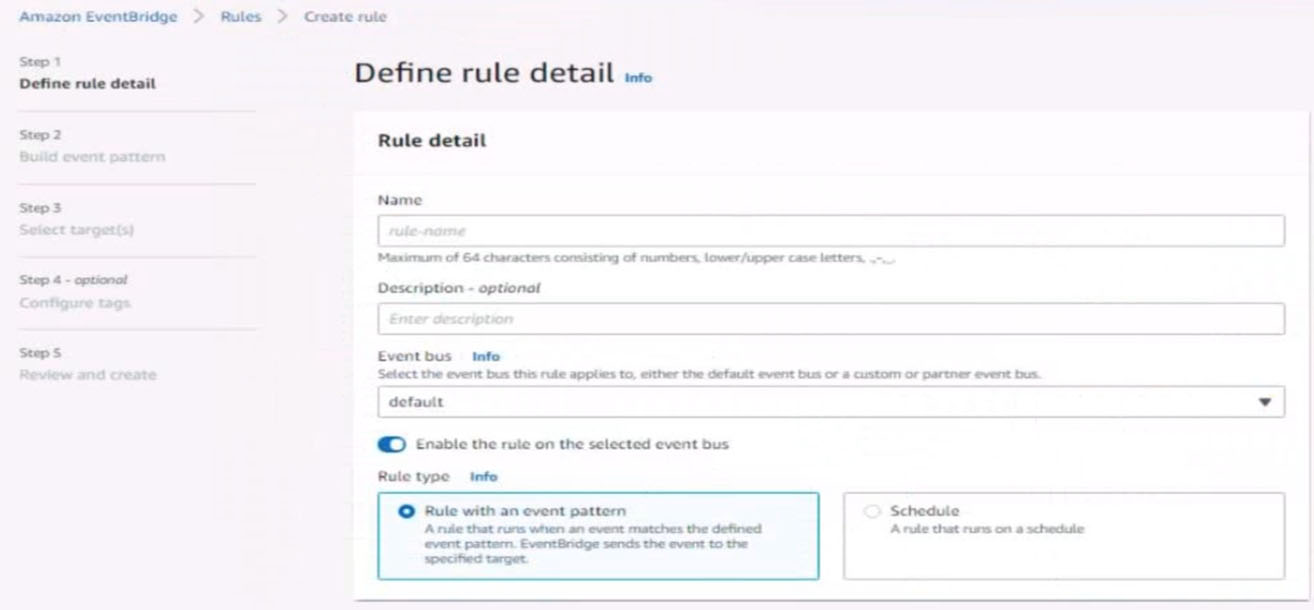

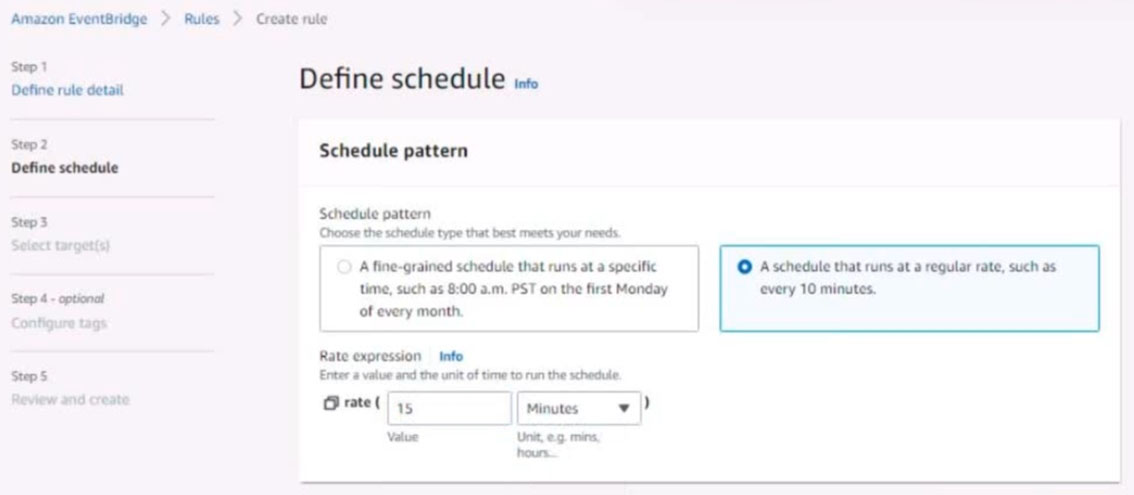

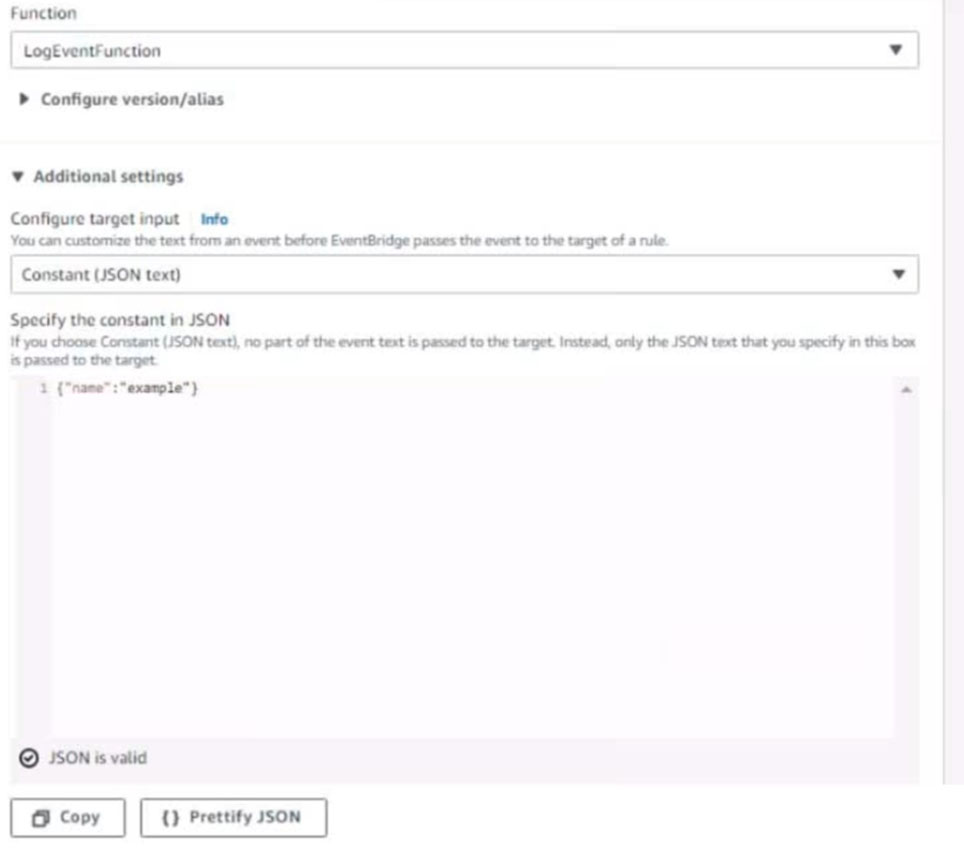

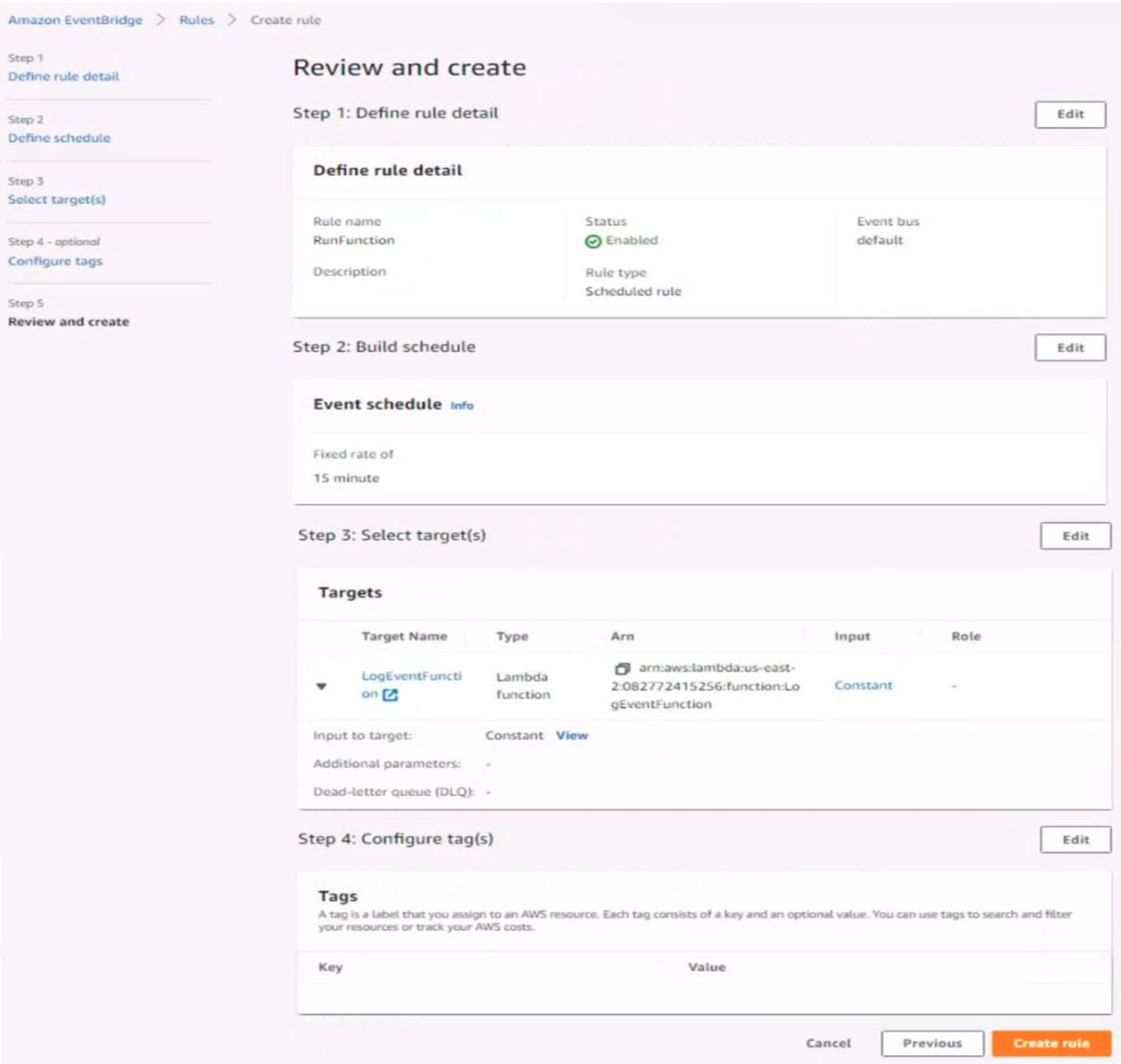
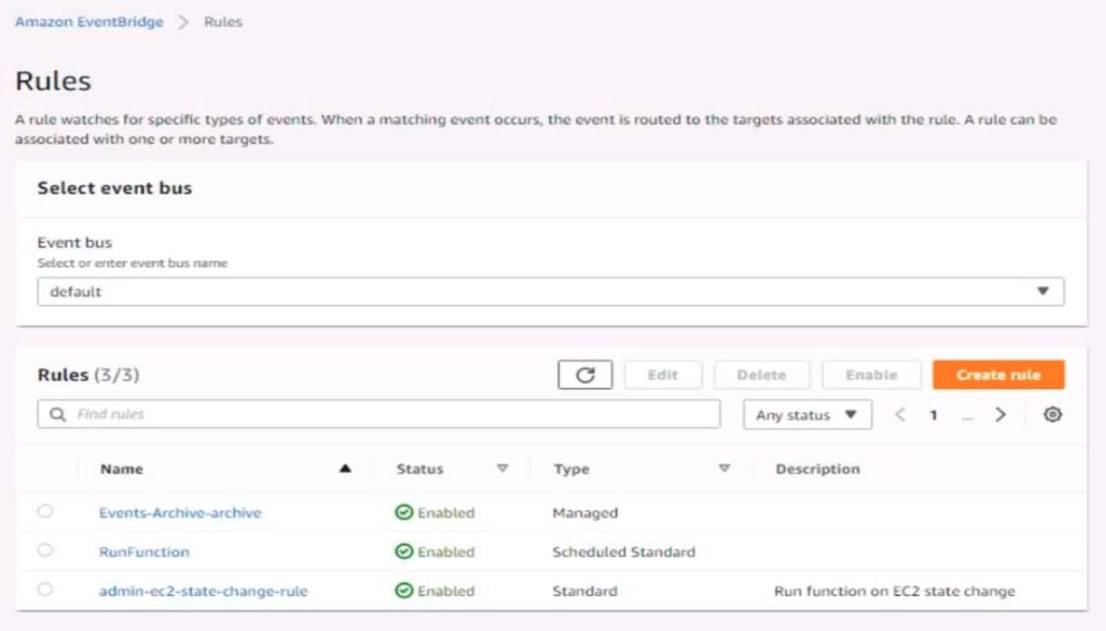

Question #61
A company has a stateful, long-running workload on a single xlarge general purpose Amazon EC2 On-Demand Instance Metrics show that the service is always using 80% of its available memory and 40% of its available CPU. A SysOps administrator must reduce the cost of the service without negatively affecting performance.
Which change in instance type will meet these requirements?
- A. Change to one large compute optimized On-Demand Instance.
- B. Change to one large memory optimized On-Demand Instance.
- C. Change to one xlarge general purpose Spot Instance.
- D. Change to two large general purpose On-Demand Instances.
Correct Answer: B
Community vote distribution
B (81%)
C (19%)
Question #62
A company asks a SysOps administrator to ensure that AWS CloudTrail files are not tampered with after they are created. Currently, the company uses AWS
Identity and Access Management (IAM) to restrict access to specific trails. The company’s security team needs the ability to trace the integrity of each file.
What is the MOST operationally efficient solution that meets these requirements?
- A. Create an Amazon EventBridge (Amazon CloudWatch Events) rule that invokes an AWS Lambda function when a new file is delivered. Configure the Lambda function to compute an MD5 hash check on the file and store the result in an Amazon DynamoDB table. The security team can use the values that are stored in DynamoDB to verify the integrity of the delivered files.
- B. Create an AWS Lambda function that is invoked each time a new file is delivered to the CloudTrail bucket. Configure the Lambda function to compute an MD5 hash check on the file and store the result as a tag in an Amazon 53 object. The security team can use the information in the tag to verify the integrity of the delivered files.
- C. Enable the CloudTrail file integrity feature on an Amazon S3 bucket. Create an IAM policy that grants the security team access to the file integrity logs that are stored in the S3 bucket.
- D. Enable the CloudTrail file integrity feature on the trail. The security team can use the digest file that is created by CloudTrail to verify the integrity of the delivered files.
Correct Answer: C
Community vote distribution
D (100%)
Question #63
When the AWS Cloud infrastructure experiences an event that may impact an organization, which AWS service can be used to see which of the organization’s resources are affected?
- A. AWS Service Health Dashboard
- B. AWS Trusted Advisor
- C. AWS Personal Health Dashboard
- D. AWS Systems Manager
Correct Answer: C
Reference:
https://docs.aws.amazon.com/health/latest/ug/getting-started-phd.html
Community vote distribution
C (100%)
Question #64
A company is using an AWS KMS customer master key (CMK) with imported key material. The company references the CMK by its alias in the Java application to encrypt data. The CMK must be rotated every 6 months.
What is the process to rotate the key?
- A. Enable automatic key rotation for the CMK, and specify a period of 6 months.
- B. Create a new CMK with new imported material, and update the key alias to point to the new CMK.
- C. Delete the current key material, and import new material into the existing CMK.
- D. Import a copy of the existing key material into a new CMK as a backup, and set the rotation schedule for 6 months.
Correct Answer: B
Reference:
https://aws.amazon.com/kms/faqs/
Community vote distribution
B (100%)
Question #65
The security team is concerned because the number of AWS Identity and Access Management (IAM) policies being used in the environment is increasing. The team tasked a SysOps administrator to report on the current number of IAM policies in use and the total available IAM policies.
Which AWS service should the administrator use to check how current IAM policy usage compares to current service limits?
- A. AWS Trusted Advisor
- B. Amazon Inspector
- C. AWS Config
- D. AWS Organizations
Correct Answer: A
Reference:
https://docs.aws.amazon.com/awssupport/latest/user/trusted-advisor-check-reference.html#iam-policies
Community vote distribution
A (100%)
Question #66
A SysOps administrator is trying to set up an Amazon Route 53 domain name to route traffic to a website hosted on Amazon S3. The domain name of the website is www.example.com and the S3 bucket name DOC-EXAMPLE-BUCKET. After the record set is set up in Route 53, the domain name www.anycompany.com does not seem to work, and the static website is not displayed in the browser.
Which of the following is a cause of this?
- A. The S3 bucket must be configured with Amazon CloudFront first.
- B. The Route 53 record set must have an IAM role that allows access to the S3 bucket.
- C. The Route 53 record set must be in the same region as the S3 bucket.
- D. The S3 bucket name must match the record set name in Route 53.
Correct Answer: D
Reference:
https://aws.amazon.com/premiumsupport/knowledge-center/route-53-no-targets/
Community vote distribution
D (100%)
Question #67
A SysOps administrator has used AWS CloudFormation to deploy a serverless application into a production VPC. The application consists of an AWS Lambda function, an Amazon DynamoDB table, and an Amazon API Gateway API. The SysOps administrator must delete the AWS CloudFormation stack without deleting the DynamoDB table.
Which action should the SysOps administrator take before deleting the AWS CloudFormation stack?
- A. Add a Retain deletion policy to the DynamoDB resource in the AWS CloudFormation stack.
- B. Add a Snapshot deletion policy to the DynamoDB resource in the AWS CloudFormation stack.
- C. Enable termination protection on the AWS CloudFormation stack.
- D. Update the application’s IAM policy with a Deny statement for the dynamodb:DeleteTable action.
Correct Answer: A
Community vote distribution
A (100%)
Question #68
A SysOps administrator is notified that an Amazon EC2 instance has stopped responding. The AWS Management Console indicates that the system checks are failing.
What should the administrator do first to resolve this issue?
- A. Reboot the EC2 instance so it can be launched on a new host.
- B. Stop and then start the EC2 instance so that it can be launched on a new host.
- C. Terminate the EC2 instance and relaunch it.
- D. View the AWS CloudTrail log to investigate what changed on the EC2 instance.
Correct Answer: B
Community vote distribution
B (100%)
Question #69
A software development company has multiple developers who work on the same product. Each developer must have their own development environments, and these development environments must be identical. Each development environment consists of Amazon EC2 instances and an Amazon RDS DB instance. The development environments should be created only when necessary, and they must be terminated each night to minimize costs.
What is the MOST operationally efficient solution that meets these requirements?
- A. Provide developers with access to the same AWS CloudFormation template so that they can provision their development environment when necessary. Schedule a nightly cron job on each development instance to stop all running processes to reduce CPU utilization to nearly zero.
- B. Provide developers with access to the same AWS CloudFormation template so that they can provision their development environment when necessary. Schedule a nightly Amazon EventBridge (Amazon CloudWatch Events) rule to invoke an AWS Lambda function to delete the AWS CloudFormation stacks.
- C. Provide developers with CLI commands so that they can provision their own development environment when necessary. Schedule a nightly Amazon EventBridge (Amazon CloudWatch Events) rule to invoke an AWS Lambda function to terminate all EC2 instances and the DB instance.
- D. Provide developers with CLI commands so that they can provision their own development environment when necessary. Schedule a nightly Amazon EventBridge (Amazon CloudWatch Events) rule to cause AWS CloudFormation to delete all of the development environment resources.
Correct Answer: C
Community vote distribution
B (100%)
Question #70
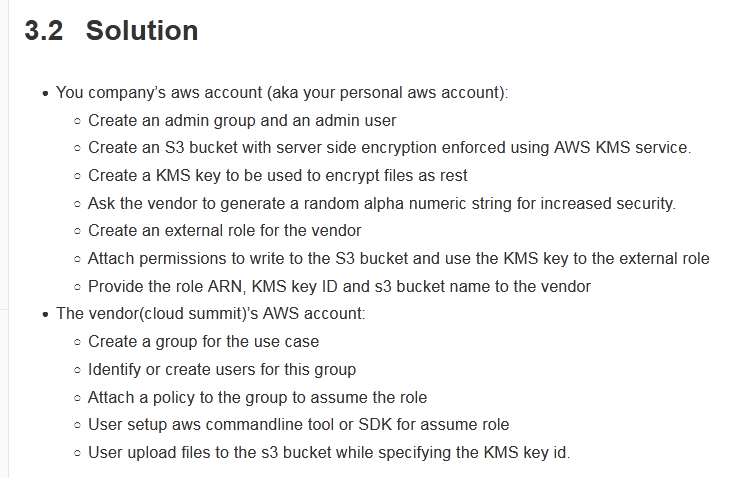
A company is partnering with an external vendor to provide data processing services. For this integration, the vendor must host the company’s data in an Amazon
S3 bucket in the vendor’s AWS account. The vendor is allowing the company to provide an AWS Key Management Service (AWS KMS) key to encrypt the company’s data. The vendor has provided an IAM role Amazon Resources Name (ARN) to the company for this integration.
What should a SysOps administrator do to configure this integration?
- A. Create a new KMS key. Add the vendor’s IAM role ARN to the KMS key policy. Provide the new KMS key ARN to the vendor.
- B. Create a new KMS key. Create a new IAM key. Add the vendor’s IAM role ARN to an inline policy that is attached to the IAM user. Provide the new IAM user ARN to the vendor.
- C. Configure encryption using the KMS managed S3 key. Add the vendor’s IAM role ARN to the KMS key policy. Provide the KMS managed S3 key ARN to the vendor.
- D. Configure encryption using the KMS managed S3 key. Create an S3 bucket. Add the vendor’s IAM role ARN to the S3 bucket policy. Provide the S3 bucket ARN to the vendor.
Correct Answer: D
Reference:
https://bookdown.org/bingweiliu11/aws-tutorial-book/use-case.html
Community vote distribution
A (79%)
13%
8%
Question #71
A SysOps administrator is using AWS Systems Manager Patch Manager to patch a fleet of Amazon EC2 instances. The SysOps administrator has configured a patch baseline and a maintenance window. The SysOps administrator also has used an instance tag to identify which instances to patch.
The SysOps administrator must give Systems Manager the ability to access the EC2 instances.
Which additional action must the SysOps administrator perform to meet this requirement?
- A. Add an inbound rule to the instances’ security group.
- B. Attach an IAM instance profile with access to Systems Manager to the instances.
- C. Create a Systems Manager activation. Then activate the fleet of instances.
- D. Manually specify the instances to patch instead of using tag-based selection.
Correct Answer: B
Community vote distribution
B (100%)
Question #72
A company hosts its website on Amazon EC2 instances in the us-east-1 Region. The company is preparing to extend its website into the eu-central-1 Region, but the database must remain only in us-east-1. After deployment, the EC2 instances in eu-central-1 are unable to connect to the database in us-east-1.
What is the MOST operationally efficient solution that will resolve this connectivity issue?
- A. Create a VPC peering connection between the two Regions. Add the private IP address range of the instances to the inbound rule of the database security group.
- B. Create a VPC peering connection between the two Regions. Add the security group of the instances in eu-central-1 to the outbound rule of the database security group.
- C. Create a VPN connection between the two Regions. Add the private IP address range of the instances to the outbound rule of the database security group.
- D. Create a VPN connection between the two Regions. Add the security group of the instances in eu-central-1 to the inbound rule of the database security group.
Correct Answer: A
Community vote distribution
A (85%)
B (15%)
Question #73
A company wants to create an automated solution for all accounts managed by AWS Organizations to detect any security groups that use 0.0.0.0/0 as the source address for inbound traffic. The company also wants to automatically remediate any noncompliant security groups by restricting access to a specific CIDR block that corresponds with the company’s intranet.
Which set of actions should the SysOps administrator take to create a solution?
- A. Create an AWS Config rule to detect noncompliant security groups. Set up automatic remediation to change the 0.0.0.0/0 source address to the approved CIDR block.
- B. Create an IAM policy to deny the creation of security groups that have 0.0.0.0/0 as the source address. Attach this IAM policy to every user in the company.
- C. Create an AWS Lambda function to inspect new and existing security groups. Check for a noncompliant 0.0.0.0/0 source address and change the source address to the approved CIDR block.
- D. Create a service control policy (SCP) for the organizational unit (OU) to deny the creation of security groups that have the 0.0.0.0/0 source address. Set up automatic remediation to change the 0.0.0.0/0 source address to the approved CIDR block.
Correct Answer: A
Community vote distribution
A (100%)
Question #74
A company requires that all activity in its AWS account be logged using AWS CloudTrail. Additionally, a SysOps administrator must know when CloudTrail log files are modified or deleted.
How should the SysOps administrator meet these requirements?
- A. Enable log file integrity validation. Use the AWS CLI to validate the log files.
- B. Enable log file integrity validation. Use the AWS CloudTrail Processing Library to validate the log files.
- C. Use CloudTrail Insights to monitor the log files for modifications.
- D. Use Amazon CloudWatch Logs to monitor the log files for modifications.
Correct Answer: B
Community vote distribution
A (94%)
6%
Question #75
A company is planning to host its stateful web-based applications on AWS. A SysOps administrator is using an Auto Scaling group of Amazon EC2 instances. The web applications will run 24 hours a day, 7 days a week throughout the year. The company must be able to change the instance type within the same instance family later in the year based on the traffic and usage patterns.
Which EC2 instance purchasing option will meet these requirements MOST cost-effectively?
- A. Convertible Reserved Instances
- B. On-Demand Instances
- C. Spot Instances
- D. Standard Reserved Instances
Correct Answer: A
Community vote distribution
A (67%)
D (30%)
2%
Question #76
An application runs on Amazon EC2 instances in an Auto Scaling group. Following the deployment of a new feature on the EC2 instances, some instances were marked as unhealthy and then replaced by the Auto Scaling group. The EC2 instances terminated before a SysOps administrator could determine the cause of the health status changes. To troubleshoot this issue, the SysOps administrator wants to ensure that an AWS Lambda function is invoked in this situation.
How should the SysOps administrator meet these requirements?
- A. Activate the instance scale-in protection setting for the Auto Scaling group. Invoke the Lambda function through Amazon EventBridge (Amazon CloudWatch Events).
- B. Activate the instance scale-in protection setting for the Auto Scaling group. Invoke the Lambda function through Amazon Route 53.
- C. Add a lifecycle hook to the Auto Scaling group to invoke the Lambda function through Amazon EventBridge (Amazon CloudWatch Events).
- D. Add a lifecycle hook to the Auto Scaling group to invoke the Lambda function through Amazon Route 53.
Correct Answer: C
Community vote distribution
C (89%)
11%
Question #77
A company runs an application that hosts critical data for several clients. The company uses AWS CloudTrail to track user activities on various AWS resources. To meet new security requirements, the company needs to protect the CloudTrail log files from being modified, deleted, or forged.
Which solution will meet these requirement?
- A. Enable CloudTrail log file integrity validation.
- B. Use Amazon S3 MFA Delete on the S3 bucket where the CloudTrail log files are stored.
- C. Use Amazon S3 Versioning to keep all versions of the CloudTrail log files.
- D. Use AWS Key Management Service (AWS KMS) security keys to secure the CloudTrail log files.
Correct Answer: C
Community vote distribution
A (65%)
C (23%)
13%
Question #78
A global company operates out of five AWS Regions. A SysOps administrator wants to identify all the company’s tagged and untagged Amazon EC2 instances.
The company requires the output to display the instance ID and tags.
What is the MOST operationally efficient way for the SysOps administrator to meet these requirements?
- A. Create a tag-based resource group in AWS Resource Groups.
- B. Use AWS Trusted Advisor. Export the EC2 On-Demand Instances check results from Trusted Advisor.
- C. Use Cost Explorer. Choose a service type of EC2-Instances, and group by Resource.
- D. Use Tag Editor in AWS Resource Groups. Select all Regions, and choose a resource type of AWS::EC2::Instance.
Correct Answer: D
Community vote distribution
D (100%)
Question #79
A company needs to upload gigabytes of files every day. The company need to achieve higher throughput and upload speeds to Amazon S3.
Which action should a SysOps administrator take to meet this requirement?
- A. Create an Amazon CloudFront distribution with the GET HTTP method allowed and the S3 bucket as an origin.
- B. Create an Amazon ElastiCache cluster and enable caching for the S3 bucket.
- C. Set up AWS Global Accelerator and configure it with the S3 bucket.
- D. Enable S3 Transfer Acceleration and use the acceleration endpoint when uploading files.
Correct Answer: D
Community vote distribution
D (100%)

