Free AWS Dump, Free Dumps
Free AWS SOA-C02 Dump
Question #360
A manufacturing company uses an Amazon RDS DB instance to store inventory of all stock items. The company maintains several AWS Lambda functions that interact with the database to add, update, and delete items. The Lambda functions use hardcoded credentials to connect to the database.
A SysOps administrator must ensure that the database credentials are never stored in plaintext and that the password is rotated every 30 days.
Which solution will meet these requirements in the MOST operationally efficient manner?
- A. Store the database password as an environment variable for each Lambda function. Create a new Lambda function that is named PasswordRotate. Use Amazon EventBridge to schedule the PasswordRotate function every 30 days to change the database password and update the environment variable for each Lambda function.
- B. Use AWS Key Management Service (AWS KMS) to encrypt the database password and to store the encrypted password as an environment variable for each Lambda function. Grant each Lambda function access to the KMS key so that the database password can be decrypted when required. Create a new Lambda function that is named PasswordRotate to change the password every 30 days.
- C. Use AWS Secrets Manager to store credentials for the database. Create a Secrets Manager secret, and select the database so that Secrets Manager will use a Lambda function to update the database password automatically. Specify an automatic rotation schedule of 30 days. Update each Lambda function to access the database password from Secrets Manager.
- D. Use AWS Systems Manager Parameter Store to create a secure string to store credentials for the database. Create a new Lambda function called PasswordRotate. Use Amazon EventBridge to schedule the PasswordRotate function every 30 days to change the database password and to update the secret within Parameter Store. Update each Lambda function to access the database password from Parameter Store.
Correct Answer: C
Community vote distribution
C (100%)
Question #361
A developer creates a web application that runs on Amazon EC2 instances behind an Application Load Balancer (ALB). The instances are in an Auto Scaling group. The developer reviews the deployment and notices some suspicious traffic to the application. The traffic is malicious and is coming from a single public IP address. A SysOps administrator must block the public IP address.
Which solution will meet this requirement?
- A. Create a security group rule to deny all inbound traffic from the suspicious IP address. Associate the security group with the ALB.
- B. Implement Amazon Detective to monitor traffic and to block malicious activity from the internet. Configure Detective to integrate with the ALB.
- C. Implement AWS Resource Access Manager (AWS RAM) to manage traffic rules and to block malicious activity from the internet. Associate AWS RAM with the ALB.
- D. Add the malicious IP address to an IP set in AWS WAF. Create a web ACL. Include an IP set rule with the action set to BLOCK. Associate the web ACL with the ALB.
Correct Answer: B
Community vote distribution
D (93%)
7%
Question #362
A SysOps administrator is creating resources from an AWS. CloudFbrmation template that defines an Auto Scaling group of Amazon EC2 instances. The Auto Scaling group launch template provisions each EC2 instance by using a user data script. The creation of the Auto Scaling group resource is failing because of an error. The wait condition is not receiving the required number of signals.
How should the SysOps administrator resolve this error?
- A. Run cfn-signal at the completion of the user data script.
- B. Modify the EC2 instances’ security group to allow outgoing traffic on port 443.
- C. Reduce the Auto Scaling group’s DesiredCapacity value in the CloudFormation template.
- D. Set the AssociatePublicIpAddress property to True in the Auto Scaling group launch template.
Correct Answer: A
Community vote distribution
A (100%)
Question #363
A company is trying to connect two applications. One application runs in an on-premises data center that has a hostname of host1.onprem private. The other application runs on an Amazon EC2 instance that has a hostname of host1.awscloud private. An AWS Site-to-Site VPN connection is in place between the on-premises network and AWS.
The application that runs in the data center tries to connect to the application that runs on the EC2 instance, but DNS resolution fails. A SysOps administrator must implement DNS resolution between on-premises and AWS resources.
Which solution allows the on-premises application to resolve the EC2 instance hostname?
- A. Set up an Amazon Route 53 inbound resolver endpoint with a forwarding rule for the onprem.private hosted zone. Associate the resolver with the VPC of the EC2 instance. Configure the on-premises DNS resolver to forward onprem.private DNS queries to the inbound resolver endpoint.
- B. Set up an Amazon Route 53 inbound resolver endpoint. Associate the resolver with the VPC of the EC2 instance. Configure the on-premises DNS resolver to forward awscloud.private DNS queries to the inbound resolver endpoint.
- C. Set up an Amazon Route 53 outbound resolver endpoint with a forwarding rule for the onprem.private hosted zone. Associate the resolver with the AWS Region of the EC2 instance. Configure the on-premises DNS resolver to forward onprem.private DNS queries to the outbound resolver endpoint.
- D. Set up an Amazon Route 53 outbound resolver endpoint. Associate the resolver with the AWS Region of the EC2 instance. Configure the on-premises DNS resolver to forward awscloud.private DNS queries to the outbound resolver endpoint.
Correct Answer: B
Community vote distribution
B (64%)
A (36%)
Question #364
A company needs to deploy instances of an application and associated infrastructure to multiple AWS Regions. The company wants to use a single AWS CloudFormation template to achieve this goal. The company uses AWS Organizations and wants to administer and run this template from a central administration account.
What should a SysOps administrator do to meet these requirements?
- A. Create a CloudFormation template that is stored in Amazon S3. Configure Cross-Region Replication (CRR) on the S3 bucket. Reference the required accounts and remote Regions in the input template parameters.
- B. In the central administration account, create a CloudFormation primary template that loads CloudFormation nested stacks from Amazon S3 buckets in the target Regions.
- C. Create CloudFormation nested stacks by using a primary template in the central administration account. Configure the required accounts and Regions for deployment of the nested stacks.
- D. Create a CloudFormation stack set that includes service-managed permissions. Deploy the stack set into the required accounts and Regions from the central administration account.
Correct Answer: C
Community vote distribution
D (100%)
Question #365
A company’s SysOps administrator manages a fleet of hundreds of Amazon EC2 instances that run Windows-based workloads and Linux-based workloads. Each EC2 instance has a tag that identifies its operating system. All the EC2 instances run AWS Systems Manager Session Manager.
A zero-day vulnerability is reported, and no patches are available. The company’s security team provides code for all the relevant operating systems to reduce the risk of the vulnerability. The SysOps administrator needs to implement the code on the EC2 instances and must provide a report that shows that the code has successfully run on all the instances.
What should the SysOps administrator do to meet these requirements as quickly as possible?
- A. Use Systems Manager Run Command. Choose either the AWS-RunShellScript document or the AWS-RunPowerShellScript document. Configure Run Command with the code from the security team. Specify the operating system tag in the Targets parameter. Run the command. Provide the command history’s evidence to the security team.
- B. Create an AWS Lambda function that connects to the EC2 instances through Session Manager. Configure the Lambda function to identify the operating system, run the code from the security team, and return the results to an Amazon RDS DB instance. Query the DB instance for the results. Provide the results as evidence to the security team.
- C. Log on to each EC2 instance. Run the code from the security team on each EC2 instance. Copy and paste the results of each run into a single spreadsheet. Provide the spreadsheet as evidence to the security team.
- D. Update the launch templates of the EC2 instances to include the code from the security team in the user data. Relaunch the EC2 instances by using the updated launch templates. Retrieve the EC2 instance logs of each instance. Provide the EC2 instance logs as evidence to the security team.
Correct Answer: D
Community vote distribution
A (100%)
Question #366
A company has an application that collects notifications from thousands of alarm systems. The notifications include alarm notifications and information notifications. The information notifications include the system arming processes, disarming processes, and sensor status.
All notifications are kept as messages in an Amazon Simple Queue Service (Amazon SQS) queue. Amazon EC2 instances that are in an Auto Scaling group process the messages. A SysOps administrator needs to implement a solution that prioritizes alarm notifications over information notifications.
Which solution will meet these requirements?
- A. Adjust the Auto Scaling group to scale faster when a high number of messages is in the queue.
- B. Use the Amazon Simple Notification Service (Amazon SNS) fanout feature with Amazon SQS to send the notifications in parallel to all the C2 instances
- C. Add an Amazon DynamoDB stream to accelerate the message processing
- D. Create a queue for alarm notifications and a queue for information notifications. Update the application to collect messages from the alarm notifications queue first.
Correct Answer: A
Community vote distribution
D (100%)
Question #367
A SysOps administrator needs to deploy an application in multiple AWS Regions. The SysOps administrator must implement a solution that routes users to the Region with the lowest latency. In case of failure, the solution must automatically route requests to a Region with a healthy instance of the application. The company needs a solution with the shortest time to failover.
Which solution will meet these requirements?
- A. Create Amazon Route 53 A records that have the same name for each endpoint. Use a latency routing policy. Associate a health check with each record.
- B. Create Amazon Route 53 A records that have the same name for each endpoint. Use a failover routing policy. Associate a health check with each record.
- C. Create an AWS Global Accelerator standard accelerator. Create an endpoint group for each Region. Add a listener to the accelerator. Associate the endpoint group with the listener.
- D. Create Amazon Route 53 A records that have the same name for each endpoint. Use a geolocation routing policy. Associate a health check with each record.
Correct Answer: C
Community vote distribution
C (86%)
14%
Question #368
A company runs an application on Amazon EC2 instances behind an Application Load Balancer. The EC2 instances are in an Auto Scaling group. The application sometimes becomes slow and unresponsive. Amazon CloudWatch metrics show that some EC2 instances are experiencing high CPU load.
A SysOps administrator needs to create a CloudWatch dashboard that can automatically display CPU metrics of all the EC2 instances. The metrics must include new instances that are launched as part of the Auto Scaling group.
What should the SysOps administrator do to meet these requirements in the MOST operationally efficient way?
- A. Create a CloudWatch dashboard. Use activity notifications from the Auto Scaling group to invoke a custom AWS Lambda function. Use the Lambda function to update the CloudWatch dashboard to monitor the CPUUtilization metric for the new instance IDs.
- B. Create a CloudWatch dashboard. Run a custom script on each EC2 instance to stream the CPU utilization to the dashboard.
- C. Use CloudWatch metrics explorer to filter by the aws:autoscaling:groupName tag and to create a visualization for the CPUUtilization metric. Add the visualization to a CloudWatch dashboard.
- D. Use CloudWatch metrics explorer to filter by instance state and to create a visualization for the CPUUtilization metric. Add the visualization to a CloudWatch dashboard.
Correct Answer: A
Community vote distribution
C (100%)
Question #369
A company has an encrypted Amazon S3 bucket that is hosted in the ap-southeast-2 Region. Users from the eu-west-2 Region access the S3 bucket over the internet. The users from eu-west-2 need faster transfers to and from the S3 bucket for large files.
Which solution will meet these requirements?
- A. Reduce the length of the S3 bucket prefixes within the S3 bucket.
- B. Change the server-side encryption on the S3 bucket from AES to RSA.
- C. Create a new S3 bucket that has an identical name in eu-west-2. Use the new S3 bucket endpoint’s domain name for access.
- D. Enable S3 Transfer Acceleration on the S3 bucket. Use the new s3-accelerate endpoint’s domain name for access.
Correct Answer: D
Community vote distribution
D (100%)
Question #370
A company has a large on-premises tape backup solution. The company has started to use AWS Storage Gateway. The company created a Tape Gateway to replace the existing on-premises hardware. The company’s backup engineer noticed that some of the backup jobs that were supposed to write to AWS failed to run because of a “Not Enough Space” error.
The company does not want these failures to happen again. The company also wants to consistently have enough tape available on AWS.
What is the MOST operationally efficient way for a SysOps administrator to meet these requirements?
- A. Create an AWS Lambda function that runs on an hourly basis and checks how many tapes have available space. If the available tapes are below a certain threshold, provision more.
- B. Install the Amazon CloudWatch agent on the on-premises system. Push the log files to a CloudWatch log group. Create an AWS Lambda function that creates more tapes when the “Not Enough Space” error appears. Create a metric filter and a metric alarm that launches the Lambda function.
- C. Create an additional Tape Gateway with its own set of tapes. Configure Amazon Simple Notification Service (Amazon SNS) to send a notification to the backup engineer if the tapes that are associated with the primary Tape Gateway do not have available space.
- D. Configure tape auto-create on the Tape Gateway. In the auto-create settings, configure a minimum number of tapes, an appropriate barcode prefix, and a tape pool.
Correct Answer: B
Community vote distribution
D (100%)
Question #371
A SysOps administrator manages a company’s Amazon S3 buckets. The SysOps administrator has identified 5 GB of incomplete multipart uploads in an S3 bucket in the company’s AWS account. The SysOps administrator needs to reduce the number of incomplete multipart upload objects in the S3 bucket.
Which solution will meet this requirement?
- A. Create an S3 Lifecycle rule on the S3 bucket to delete expired markers or incomplete multipart uploads.
- B. Require users that perform uploads of files into Amazon S3 to use the S3 TransferUtility.
- C. Enable S3 Versioning on the S3 bucket that contains the incomplete multipart uploads.
- D. Create an S3 Object Lambda Access Point to delete incomplete multipart uploads.
Correct Answer: C
Community vote distribution
A (100%)
Question #372
A SysOps administrator needs to create an Amazon S3 bucket as a resource in an AWS CloudFormation template. The bucket name must be randomly generated, and the bucket must be encrypted. Other resources in the template will reference the bucket.
Which CloudFormation resource definition should the SysOps administrator use to meet these requirements?
- A.
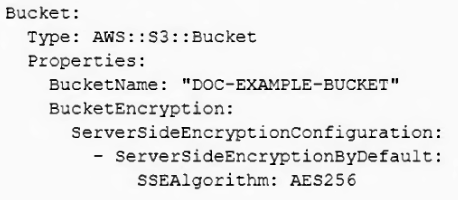
- B.
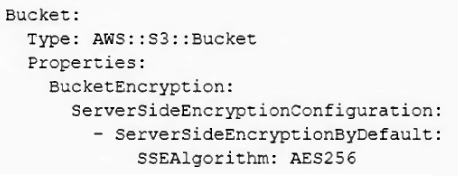
- C.

- D.
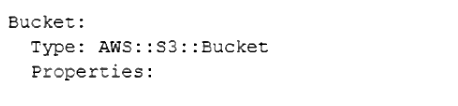
Correct Answer: A
Community vote distribution
B (100%)
Question #373
A SysOps administrator manages policies for many AWS member accounts in an AWS Organizations structure. Administrators on other teams have access to the account root user credentials of the member accounts. The SysOps administrator must prevent all teams, including their administrators, from using Amazon DynamoDB. The solution must not affect the ability of the teams to access other AWS services.
Which solution will meet these requirements?
- A. In all member accounts, configure IAM policies that deny access to all DynamoDB resources for all users, including the root user.
- B. Create a service control policy (SCP) in the management account to deny all DynamoDB actions. Apply the SCP to the root of the organization
- C. In all member accounts, configure IAM policies that deny AmazonDynamoDBFullAccess to all users, including the root user.
- D. Remove the default service control policy (SCP) in the management account. Create a replacement SCP that includes a single statement that denies all DynamoDB actions.
Correct Answer: C
Community vote distribution
B (100%)
Question #374
A company has users that deploy Amazon EC2 instances that have more disk performance capacity than is required. A SysOps administrator needs to review all Amazon Elastic Block Store (Amazon EBS) volumes that are associated with the instances and create cost optimization recommendations based on IOPS and throughput.
What should the SysOps administrator do to meet these requirements in the MOST operationally efficient way?
- A. Use the monitoring graphs in the EC2 console to view metrics for EBS volumes. Review the consumed space against the provisioned space on each volume. Identify any volumes that have low utilization.
- B. Stop the EC2 instances from the EC2 console. Change the EC2 instance type for Amazon EBS-optimized. Start the EC2 instances.
- C. Opt in to AWS Compute Optimizer. Allow sufficient time for metrics to be gathered. Review the Compute Optimizer findings for EBS volumes.
- D. Install the fio tool onto the EC2 instances and create a .cfg file to approximate the required workloads. Use the benchmark results to gauge whether the provisioned EBS volumes are of the most appropriate type.
Correct Answer: A
Community vote distribution
C (100%)
Question #375
A SysOps administrator has many Windows Amazon EC2 instances that need to share a file system between nodes. The SysOps administrator creates an Amazon Elastic File System (Amazon EFS) file share. After creation of the file share, the SysOps administrator is having trouble mounting the file share to the EC2 instances.
Which action should the SysOps administrator take so that the EC2 instances can share the files?
- A. Delete the EFS file share. Create an Amazon FSx for Windows File Server file share for the EC2 instances.
- B. Use the correct IAM credentials to mount the EFS file share.
- C. Configure NFSv4 support on the Windows operating system that is running on the EC2 instances.
- D. Allow the correct port for NFS through the security group and network ACL.
Correct Answer: B
Community vote distribution
A (88%)
13%
Question #376
A company has a multi-account environment. Account A has a production application that is hosted on an Amazon EC2 instance. The application needs to query data in an Amazon DynamoDB table that is hosted in Account B.
A SysOps administrator needs to provide the EC2 instance in Account A with access to the DynamoDB table in Account B.
What is the MOST secure solution that will meet these requirements?
- A. Update the IAM policy that is attached to the EC2 instance’s IAM role to allow the dynamodb:Query permission on the DynamoDB table in Account B. Add a policy in Account A to allow the DynamoDB service principal to use the PassRole action to pass the role to Account B.
- B. In Account B, create an IAM role that has permission to query the DynamoDB table. Add the EC2 instance’s IAM role to the trust policy on the newly created IAM role in Account Update the IAM policy that is attached to the EC2 instance’s IAM role to allow the sts:AssumeRole permission on the newly created IAM role in Account B.
- C. Update the IAM policy that is attached to the EC2 instance’s IAM role to allow the dynamodb:Query permission on the DynamoDB table in Account B. Update the DynamoDB table’s resource policy to allow the query action from the EC2 instance’s IAM role.
- D. In Account B, create a static IAM key that has the appropriate permissions to query the DynamoDB table. Embed these credentials into the credentials file on the EC2 instance. Reference the credentials every time the application needs to query the table.
Correct Answer: B
Community vote distribution
B (100%)
Question #377
A company has implemented a Kubernetes cluster on Amazon Elastic Kubernetes Service (Amazon ECS) to host a microservices-based application. The company expects application traffic to increase significantly for the next month and wants to prevent the application from crashing because of the high number of requests.
Which solution will meet these requirements with the LEAST administrative overhead?
- A. Create a second EKS cluster. Load balance the workload between the two clusters.
- B. Implement the Kubernetes Horizontal Pod Autoscaler. Set a target CPU utilization percentage.
- C. Migrate the application from Amazon EKS to Amazon EC2 for the next month. Migrate the application back to Amazon EKS when the month ends.
- D. Implement the Kubernetes Vertical Pod Autoscaler. Set a target CPU utilization percentage.
Correct Answer: B
Community vote distribution
B (100%)
Question #378
A company deploys a new application to Amazon EC2 instances. The application code is stored in an AWS CodeCommit repository. The company uses an AWS CodePipeline pipeline to deploy the code to the EC2 instances through a continuous integration and continuous delivery (CI/CD) process.
A SysOps administrator needs to ensure that sensitive database information is configured properly on the EC2 instances to prevent accidental leakage of credentials.
Which solutions will store and retrieve the sensitive information in the MOST secure manner? (Choose two.)
- A. Store the values in AWS Secrets Manager. Update the code to retrieve these values when the application starts. Store the values as environmental variables that the application can use.
- B. Store the values in AWS Systems Manager Parameter Store as secret strings. Update the code to retrieve these values when the application starts. Store the values as environmental variables that the application can use.
- C. Store the values in an AWS Lambda function. Update the code to invoke the Lambda function when the application starts. Configure the Lambda function to inject the values as environmental variables that the application can use.
- D. Store the configuration information in a file on the EC2 instances. Ensure that the underlying drives are encrypted by AWS Key Management Service (AWS KMS). Update the application to read the file when the application starts. Store the values as environmental variables.
- E. Store the values in a text file in an Amazon S3 bucket. In the CI/CD pipeline, copy the file to the EC2 instance in an appropriate location on a disk that the application can read.
Correct Answer: AB
Community vote distribution
AB (100%)
Question #379
A SysOps administrator configured VPC flow logs by using the default format. The SysOps administrator specified Amazon CloudWatch Logs as the destination. This solution has worked successfully for several months. However, because of additional troubleshooting requirements, the SysOps administrator needs to include the tcp-flags field on the flow logs.
What should the SysOps administrator do to meet this requirement?
- A. Create a new flow log. Include the tcp-flags field in the custom log format. Delete the original flow log.
- B. In the CloudWatch Logs log group, modify the filter to include the tcp-flags field and the type field.
- C. In CloudWatch Metrics, modify the metric configuration to include the tcp-flags field.
- D. Modify the existing flow log. Include the tcp-flags field and the type field in the custom log format. Save the configuration.
Correct Answer: A
Community vote distribution
A (100%)
1

