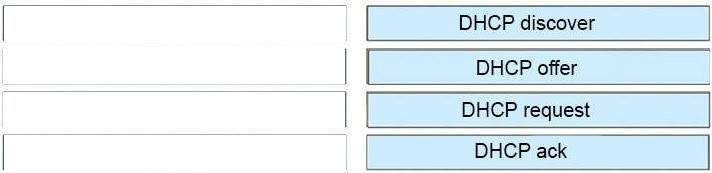
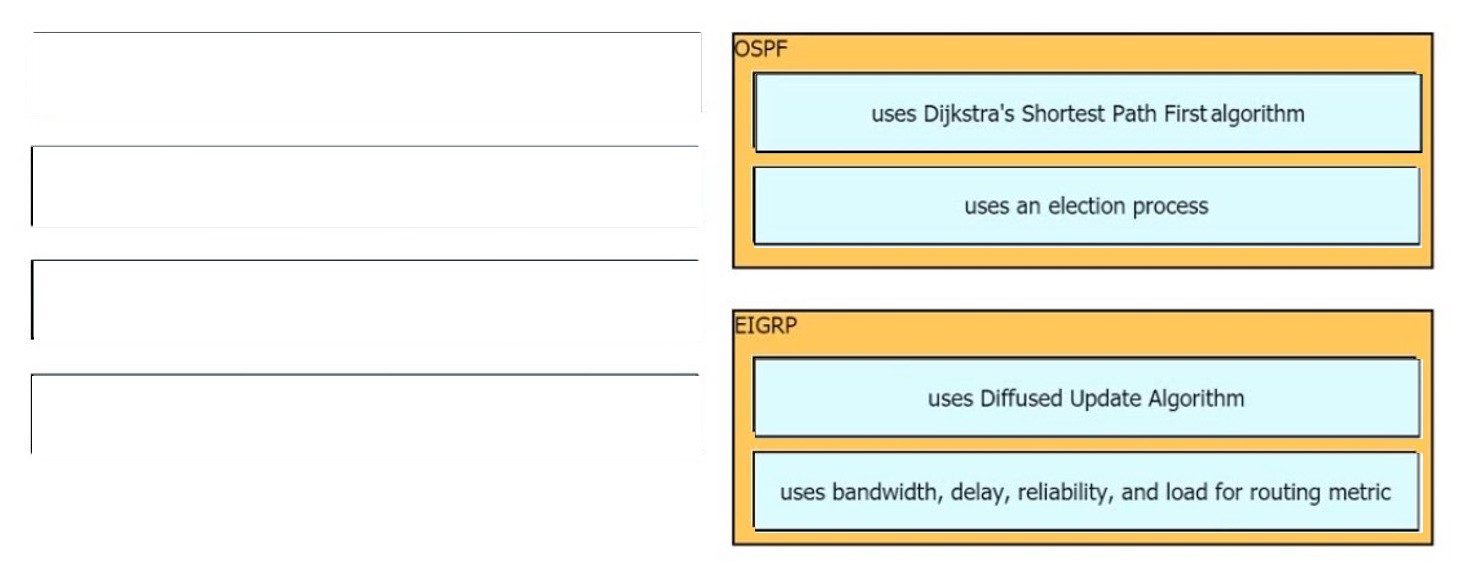
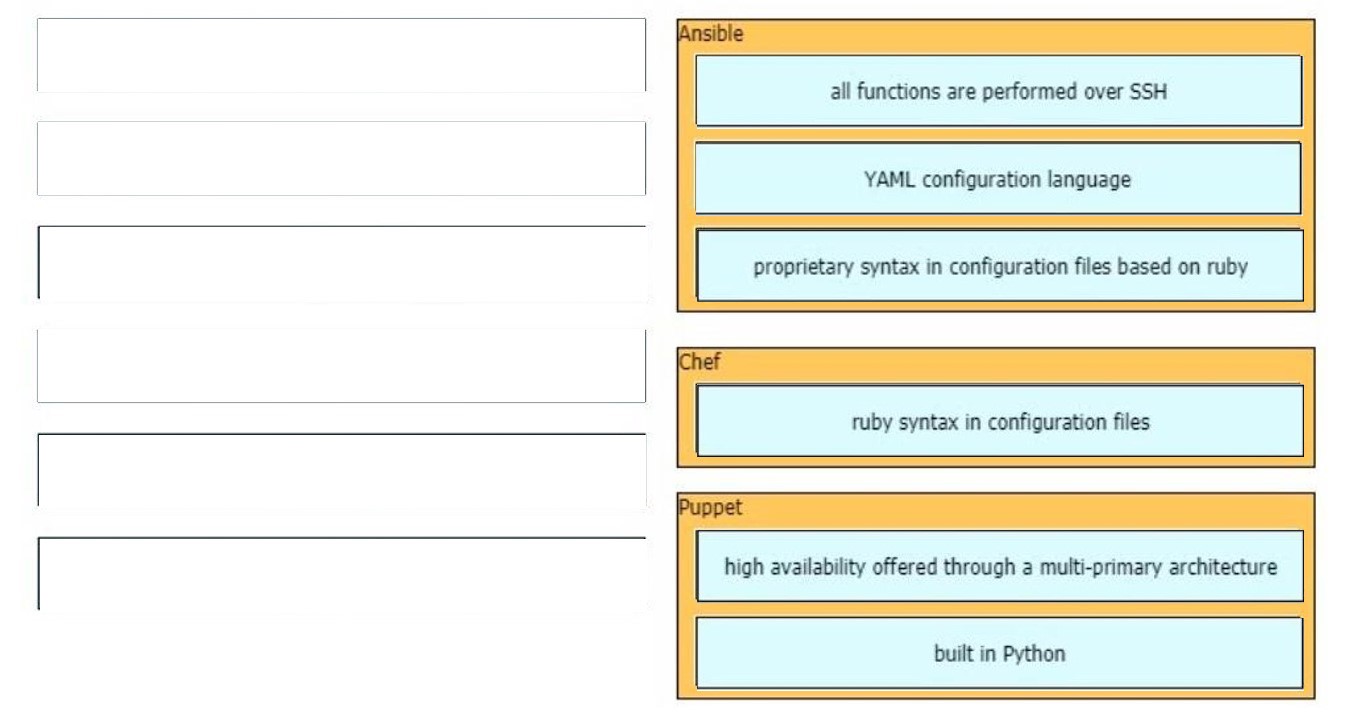
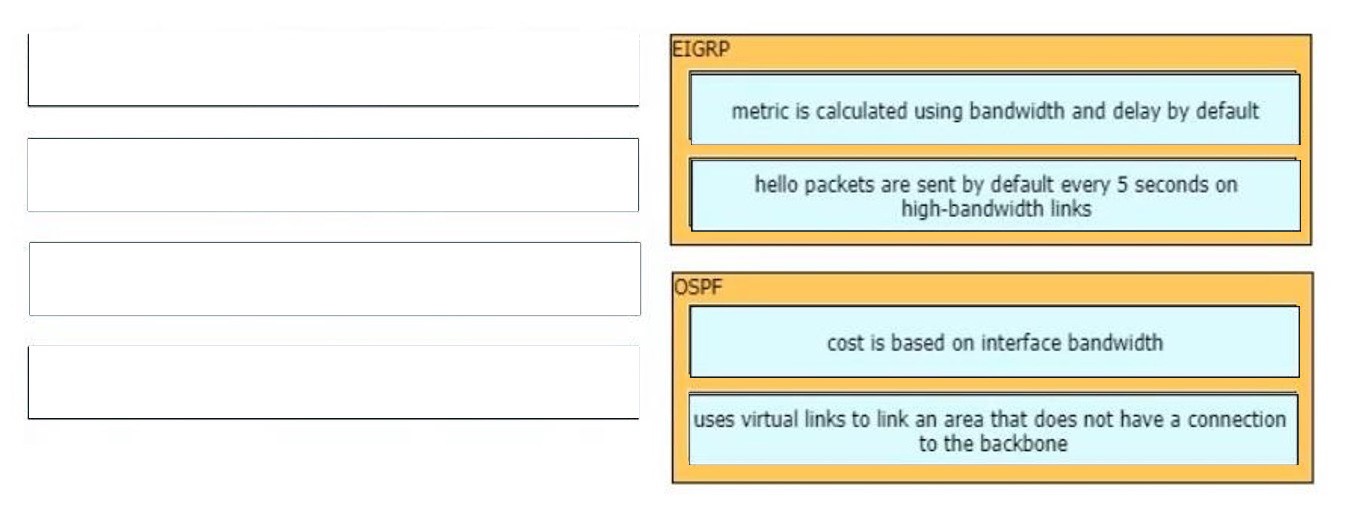
Free Cisco Dump, Free Dumps
Free 350-401 ENCOR Dump
Lưu ý: Free 350-401 ENCOR Dump chỉ dành cho mục đích học tập và làm quen với bài thi. Nội dung của Free 350-401 ENCOR Dump không được cập nhật mới nhất nên không đảm bảo Pass Exam. Liên hệ ITexamViet để Pass Exam Nhanh Nhất.
Multiple Choice
QUESTION 1
Refer to the exhibit. An engineer must configure a SPAN session. What is the effect of the configuration?
![]()
A. Traffic sent on VLANs 10, 11, and 12 is copied and sent to interface g0/1.
B. Traffic sent on VLANs 10 and 12 only is copied and sent to interface g0/1.
C. Traffic received on VLANs 10, 11, and 12 is copied and sent to Interface g0/1.
D. Traffic received on VLANs 10 and 12 only is copied and sent to interface g0/1.
QUESTION 2
Which statement about TLS is true when using RESTCONF to write configurations on network devices?
A. It is used for HTTP and HTTPS requests.
B. It requires certificates for authentication.
C. It is provided using NGINX acting as a proxy web server.
D. It is not supported on Cisco devices.
QUESTION 3
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
![]() Location A: -72 dBm
Location A: -72 dBm
![]() Location B: -75 dBm
Location B: -75 dBm
![]() Location C: -65 dBm
Location C: -65 dBm
![]() Location D: -80 dBm
Location D: -80 dBm
Which two statements does the engineer use to explain these values to the customer? (Choose two)
A. The signal strength at location B is 10 dB better than location C.
B. Location D has the strongest RF signal strength.
C. The signal strength at location C is too weak to support web surfing.
D. The RF signal strength at location B is 50% weaker than location A
E. The RF signal strength at location C is 10 times stronger than location B
QUESTION 4
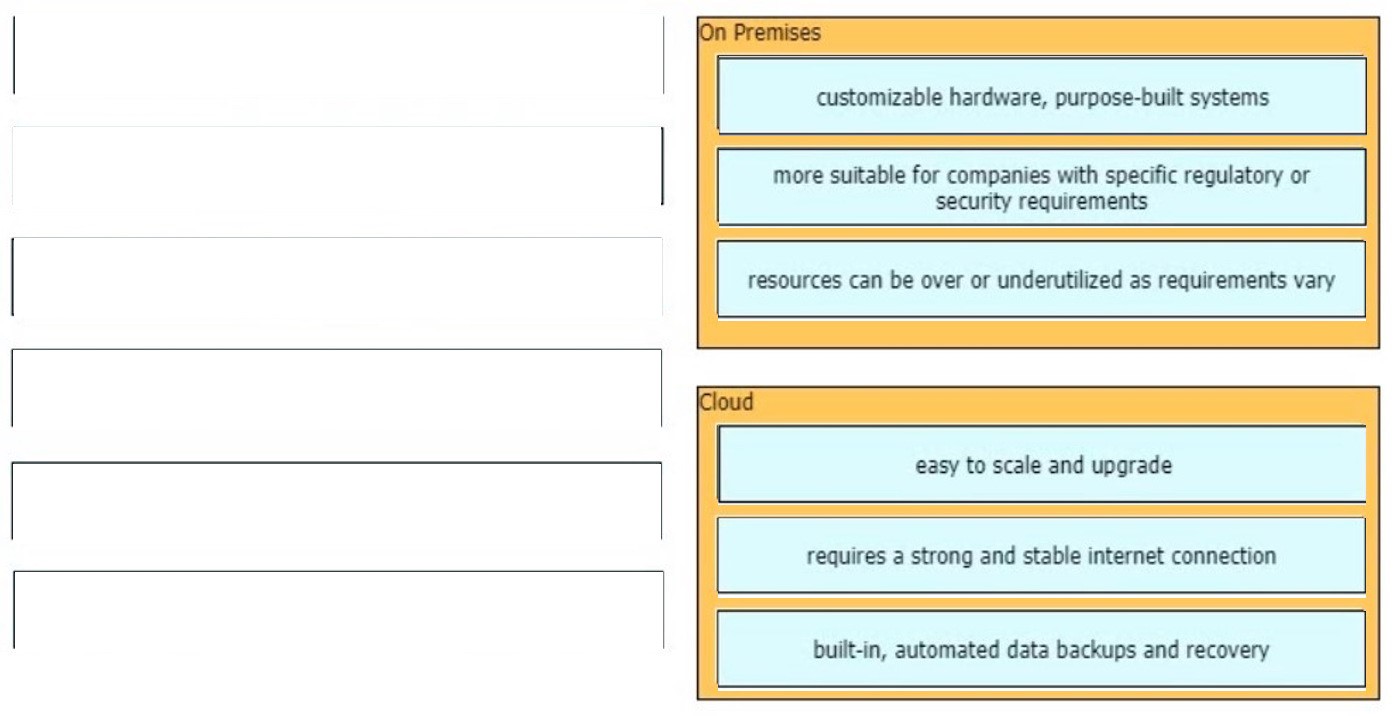
How does an on-premises infrastructure compare to a cloud infrastructure?
A. On-premises can increase compute power faster than cloud
B. On-premises requires less power and cooling resources than cloud
C. On-premises offers faster deployment than cloud
D. On-premises offer lower latency for physically adjacent systems than cloud.
QUESTION 5
At which layer does Cisco DNA Center support REST controls?
A. session layer
B. northbound APIs
C. EEM applets or scripts
D. YAML output from responses to API calls
QUESTION 6
Refer to the exhibit.
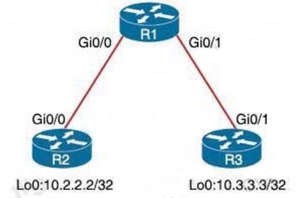
An engineer must deny Telnet traffic from the loopback interface of router R3 to the loopback interface of router R2 during the weekend hours. All other traffic between the loopback interfaces of routers R3 and R2 must be allowed at all times. Which command accomplish this task?
A. R3(config)#time-range WEEKEND
R3(config-time-range)#periodic Saturday Sunday 00:00 to 23:59
R3(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R3(config)#access-list 150 permit ip any any time-range WEEKENDR3(config)
#interface Gi0/1 R3(config-if)#ip access-group 150 out
B. R1(config)#time-range WEEKEND
R1(config-time-range)#periodic Friday Sunday 00:00 to 00:00
R1(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R1(config)#access-list 150 permit ip any any R1(config)#interface Gi0/1
R1(config-if)#ip access-group 150 in
C. R1(config)#time-range WEEKEND
R1(config-time-range)#periodic weekend 00:00 to 23:59
R1(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R1(config)#access-list 150 permit ip any any R1(config)#interface Gi0/1
R1(config-if)#ip access-group 150 in
D. R3(config)#time-range WEEKEND
R3(config-time-range)#periodic weekend 00:00 to 23:59
R3(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R3(config)#access-list 150 permit ip any any time-range WEEKEND R3(config)#interface Gi0/1
R3(config-if)#ip access-group 150 out
QUESTION 7
What is the function of cisco DNA center in a cisco SD-access deployment?
A. It is responsible for routing decisions inside the fabric
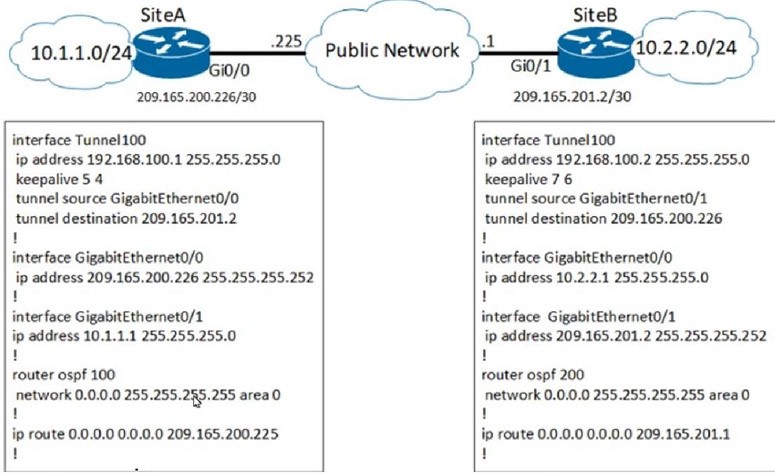
B. It is responsible for the design, management, deployment, provisioning, and assurance of the fabric network devices.
C. It possesses information about all endpoints, nodes and external networks to the fabric
D. IT provides integration and automation for all nonfabric nodes and their fabric
QUESTION 8
Refer to the exhibit.
ip sla 10
icmp-echo 192.168.10.20 timeout 500 frequency 3
ip sla schedule 10 life forever start-time now track 10 ip sla 10 reachability
The IP SLA is configured in a router. An engineer must configure an EEM applet to shut down the interface and bring it back up when there is a problem with the IP SLA. Which configuration should the engineer use?
A. event manager applet EEM_IP_SLAevent track 10 state down
B. event manager applet EEM_IP_SLAevent track 10 state unreachable
C. event manager applet EEM_IP_SLAevent sla 10 state unreachable
D. event manager applet EEM_IP_SLAevent sla 10 state down
QUESTION 9
What is a fact about Cisco EAP-FAST?
A. It requires a client certificate.
B. It is an IETF standard.
C. It does not require a RADIUS server certificate.
D. It operates in transparent mode.
QUESTION 10
Which threat defence mechanism, when deployed at the network perimeter, protects against zero-day attacks?
A. intrusion prevention
B. stateful inspection
C. sandbox
D. SSL decryption
QUESTION 11
Refer to the exhibit. Which configuration change will force BR2 to reach 209 165 201 0/27 via BR1?
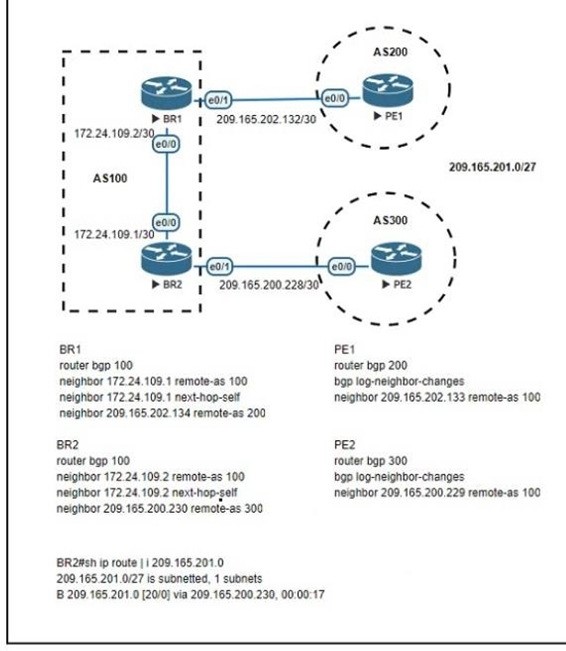
A. Set the weight attribute to 65.535 on BR1 toward PE1.
B. Set the local preference to 150 on PE1 toward BR1 outbound
C. Set the MED to 1 on PE2 toward BR2 outbound.
D. Set the origin to igp on BR2 toward PE2 inbound.
QUESTION 12
What is a benefit of data modeling languages like YANG?
A. They create more secure and efficient SNMP OIDs.
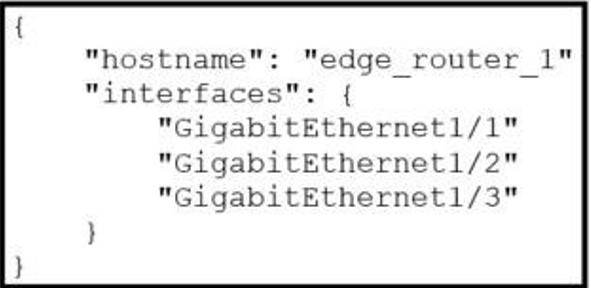
B. They provide a standardized data structure, which results in configuration scalability and consistency.
C. They enable programmers to change or write their own applications within the device operating system.
D. They make the CLI simpler and more efficient.
QUESTION 13
Which outbound access list, applied to the WAN interface of a router, permits all traffic except for http traffic sourced from the workstation with IP address 10.10.10.1?
A. ip access-list extended 200deny tcp host 10.10.10.1 eq 80 any permit ip any any
B. ip access-list extended 10deny tcp host 10.10.10.1 any eq 80 permit ip any any
C. ip access-list extended NO_HTTPdeny tcp host 10.10.10.1 any eq 80 D. ip access-list extended 100 deny tcp host 10.10.10.1 any eq 80 permit ip any any
QUESTION 14
What is one fact about Cisco SD-Access wireless network deployments?
A. The access point is part of the fabric underlay
B. The WLC is part of the fabric underlay
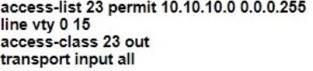
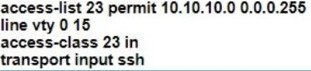
C. The access point is part the fabric overlay
D. The wireless client is part of the fabric overlay
QUESTION 15
When using TLS for syslog, which configuration allows for secure and reliable transportation of messages to its default port?
A. logging host 10.2.3.4 vrf mgmt transport tcp port 514
B. logging host 10.2.3.4 vrf mgmt transport udp port 514
C. logging host 10.2.3.4 vrf mgmt transport tcp port 6514
D. logging host 10.2.3.4 vrf mgmt transport udp port 6514
Correct Answer: C
QUESTION 16
Refer to the exhibit.
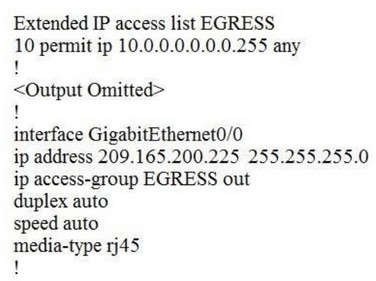
An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router. However, the router can still ping hosts on the 209.165.200.0/24 subnet. Which explanation of this behavior is true?
A. Access control lists that are applied outbound to a router interface do not affect traffic that is sourced from the router.
B. After an access control list is applied to an interface, that interface must be shut and no shut for the access control list to take effect.
C. Only standard access control lists can block traffic from a source IP address.
D. The access control list must contain an explicit deny to block traffic from the router.
QUESTION 17
Why is an AP joining a different WLC than the one specified through option 43?
A. The WLC is running a different software version
B. The API is joining a primed WLC
C. The AP multicast traffic unable to reach the WLC through Layer 3
D. The APs broadcast traffic is unable to reach the WLC through Layer 2
QUESTION 18
Refer to the exhibit.
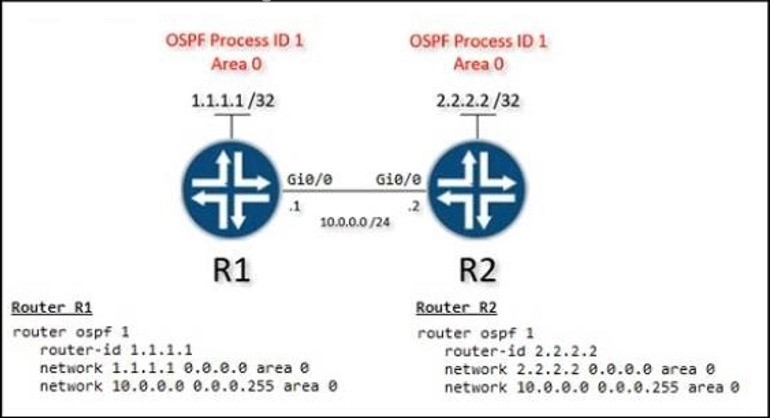
A network engineer is configuring OSPF between router R1 and router R2. The engineer must ensure that a DR/BDR election does not occur on the Gigabit Ethernet interfaces in area 0. Which configuration set accomplishes this goal?
A. R1 (config-if) #interface Gi0/0
R1 (config-if) #ip ospf network point-to-point
R2 (config-if) #interface Gi0/0
R2 (config-if) #ip ospf network point-to-point
B. R1 (config-if) #interface Gi0/0
R1 (config-if) #ip ospf network broadcast
R2(config-if)#interface Gi0/0
R2(config-if)#ip ospf network broadcast
C. R1(config-if)#interface Gi0/0
R1(config-if)#ip ospf database-filter all out
R2(config-if)#interface Gi0/0
R2(config-if)#ip ospf database-filter all out
D. R1(config-if)#interface Gi0/0
R1(config-if)#ip ospf priority 1
R2(config-if)#interface Gi0/0
R2(config-if)#ip ospf priority 1
QUESTION 19
Which solution do laaS service providers use to extend a Layer 2 segment across a Layer 3 network?
A. VLAN
B. VTEP
C. VXLAN
D. VRF
QUESTION 20
Which two components are supported by LISP? (choose two)
A. proxy ETR
B. egress tunnel router
C. route reflector
D. HMAC algorithm
E. spoke
QUESTION 21
What does the Cisco DMA REST response Indicate?

A. Cisco DNA Center has the incorrect credentials for cat3850-1
B. Cisco DNA Center Is unable to communicate with cat9000-1
C. Cisco DNA Center has the incorrect credentials for cat9000-1
D. Cisco DNA Center has the Incorrect credentials for RouterASR-1
QUESTION 22
What are two considerations when using SSO as a network redundancy feature? (Choose two)
A. both supervisors must be configured separately
B. the multicast state is preserved during switchover
C. must be combined with NSF to support uninterrupted Layer 2 operations
D. must be combined with NSF to support uninterrupted Layer 3 operations
E. requires synchronization between supervisors in order to guarantee continuous connectivity
QUESTION 23
Refer to the exhibit. Based on the configuration in this WLAN security setting, which method can a client use to authenticate to the network?
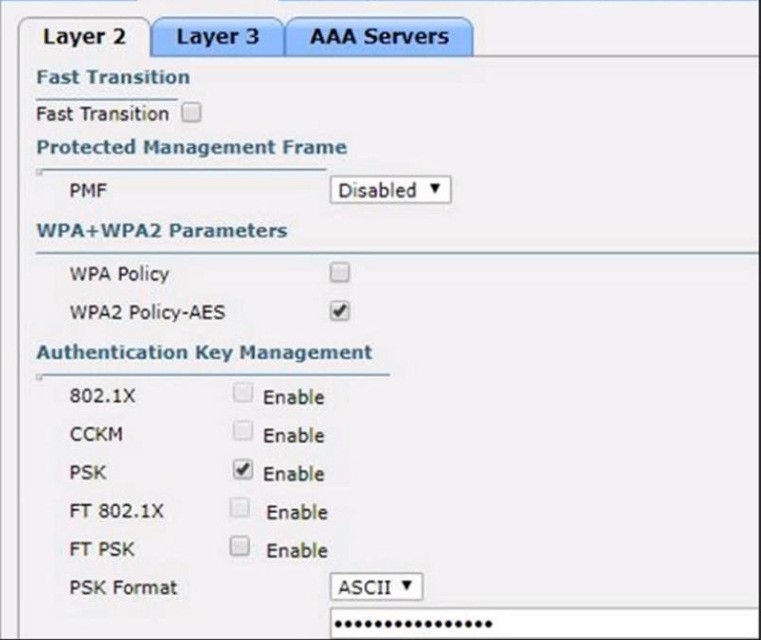
A. text string
B. username and password
C. RADIUS token
D. certificate
QUESTION 24
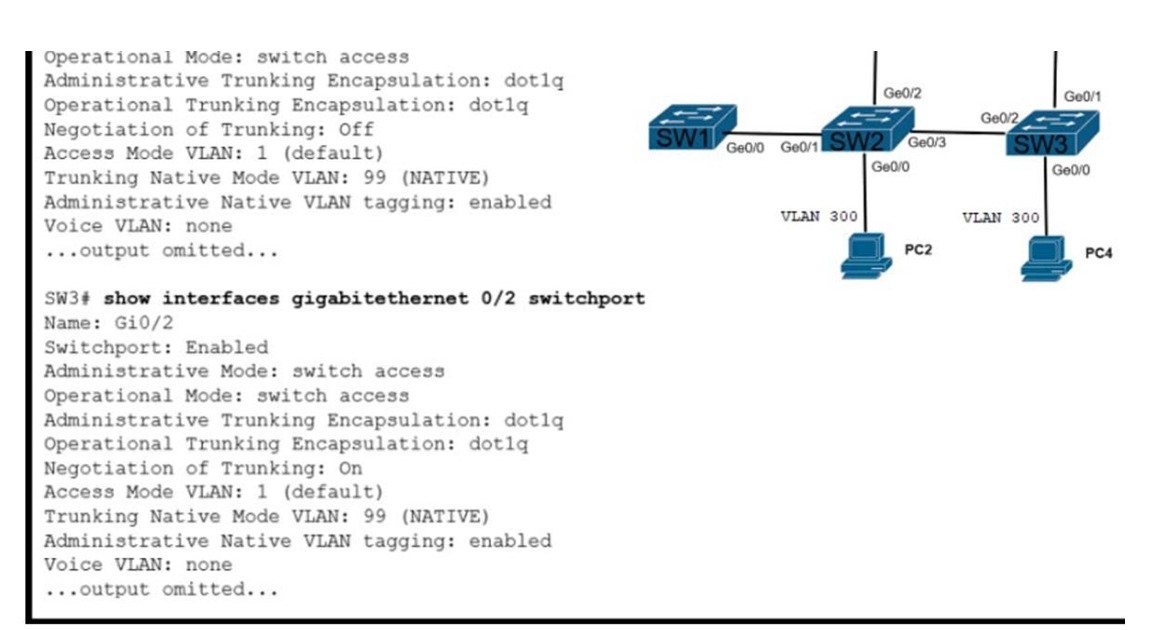
Refer to the exhibit. The trunk between SW2 and SW3 is not operational. Which action enables traffic for VLAN 200 to pass
A. Configure no switch mode trunk on SW2 and SW3.
B. Configure switchport nonegotiate SW2 and SW3.
C. Configure switchport mode dynamic desirable on SW2 and SW3.
D. Configure tp mode transparent on SW2 and SW3.
QUESTION 25
Which technology is used as the basis for the cisco SD-Access data plane?
A. IPsec
B. LISP
C. VXLAN
D. 802.1Q
QUESTION 26
Running the script causes the output in the exhibit. Which change to the first line of the script resolves the error?
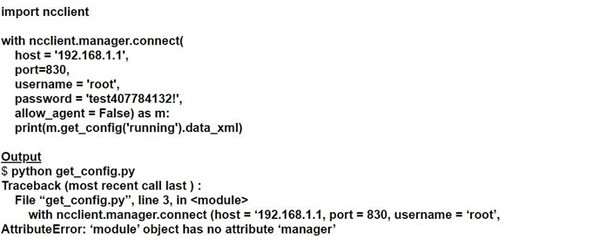
A. from ncclient import manager
B. import manager
C. from ncclient import*
D. ncclient manager import
QUESTION 27
Which method of account authentication does OAuth 2.0 within REST APIs?
A. username/role combination
B. access tokens
C. cookie authentication
D. basic signature workflow
QUESTION 28
An engineer configures a WLAN with fast transition enabled. Some legacy clients fail to connect to this WLAN. Which feature allows the legacy clients to connect while still allowing other clients to use fast transition based on their OUIs?
A. over the DS
B. 802.11k
C. adaptive R
D. 802.11v
QUESTION 29
Refer to the exhibit. What does the error message relay to the administrator who is trying to configure a Cisco IOS device?

A. A NETCONF request was made for a data model that does not exist.
B. The device received a valid NETCONF request and serviced it without error.
C. A NETCONF message with valid content based on the YANG data models was made, but the request failed.
D. The NETCONF running datastore is currently locked.
QUESTION 30
What are two benefits of YANG? (choose two)
A. it collects statistical constraint analysis information
B. In enforces the use of specific encoding format for NETCONF
C. in enforces configuration semantics
D. it enables multiple leaf statements to exist within a leaf list
E. it enforces configuration constraints
QUESTION 31
Refer to the exhibit.

An engineer must create a configuration that executes the show run command and then terminates the session when user CCNP logs in. Which configuration change is required”
A. Add the access-class keyword to the username command
B. Add the access-class keyword to the aaa authentication command
C. Add the autocommand keyword to the username command
D. Add the autocommand keyword to the aaa authentication command
QUESTION 32
Refer to the exhibit. An engineer configures a new HSRP group. While reviewing the HSRP status, the engineer sees the logging message generated on R2. Which is the cause of the message?
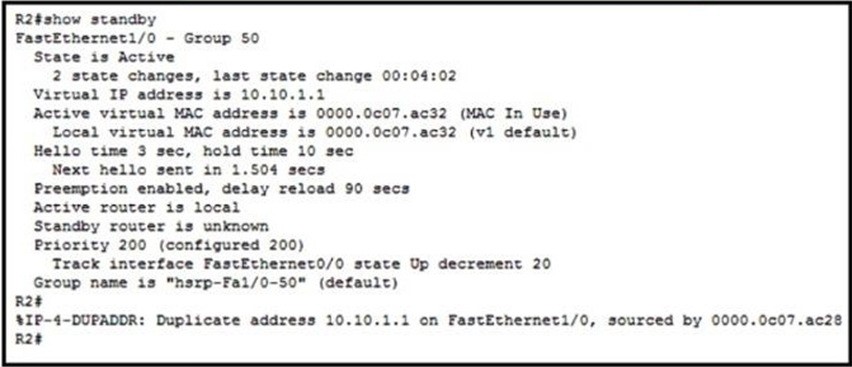
A. The same virtual IP address has been configured for two HSRP groups
B. The HSRP configuration has caused a spanning-tree loop
C. The HSRP configuration has caused a routing loop
D. A PC is on the network using the IP address 10.10.1.1
QUESTION 33
Which technology provides a secure communication channel for all traffic at Layer 2 of the OSI model?
A. SSL
B. Cisco TrustSec
C. MACsec
D. IPsec
QUESTION 34
What is the difference between CEF and process switching?
A. CEF processes packets that are too complex for process switching to manage.
B. CEF is more CPU-intensive than process switching.
C. CEF uses the FIB and the adjacency table to make forwarding decisions, whereas process switching punts each packet.
D. Process switching is faster than CEF.
QUESTION 35
An engineer must provide wireless converge in a square office. The engineer has only one AP and believes that it should be placed it in the middle of the room. Which antenna type should the engineer use?
A. directional
B. polarized
C. Yagi
D. omnidirectional
QUESTION 36
Which method creates an EEM applet policy that is registered with EEM and runs on demand or manually?
A. event manager applet ondemand
event none
action 1.0 syslog priority critical msg `This is a message from ondemand’
B. event manager applet
ondemand action
1.0 syslog priority critical msg `This is a message from ondemand’
C. event manager applet ondemand
event register
action 1.0 syslog priority critical msg `This is a message from ondemand’
D. event manager applet ondemand
event manual
action 1.0 syslog priority critical msg `This is a message from ondemand’
QUESTION 37
What is a benefit of YANG modules?
A. tightly coupled models with encoding to improve performance
B. easier multivendor interoperability provided by common or industry models
C. avoidance of ecosystem fragmentation by having fixed modules that cannot be changed
D. single protocol and model coupling to simplify maintenance and support
QUESTION 38
Refer to the exhibit. All switches are configured with the default port priority value. Which two commands ensure that traffic from PC1 is forwarded over Gi1/3 trunk port between DSW1 and DSW2? (Choose two)
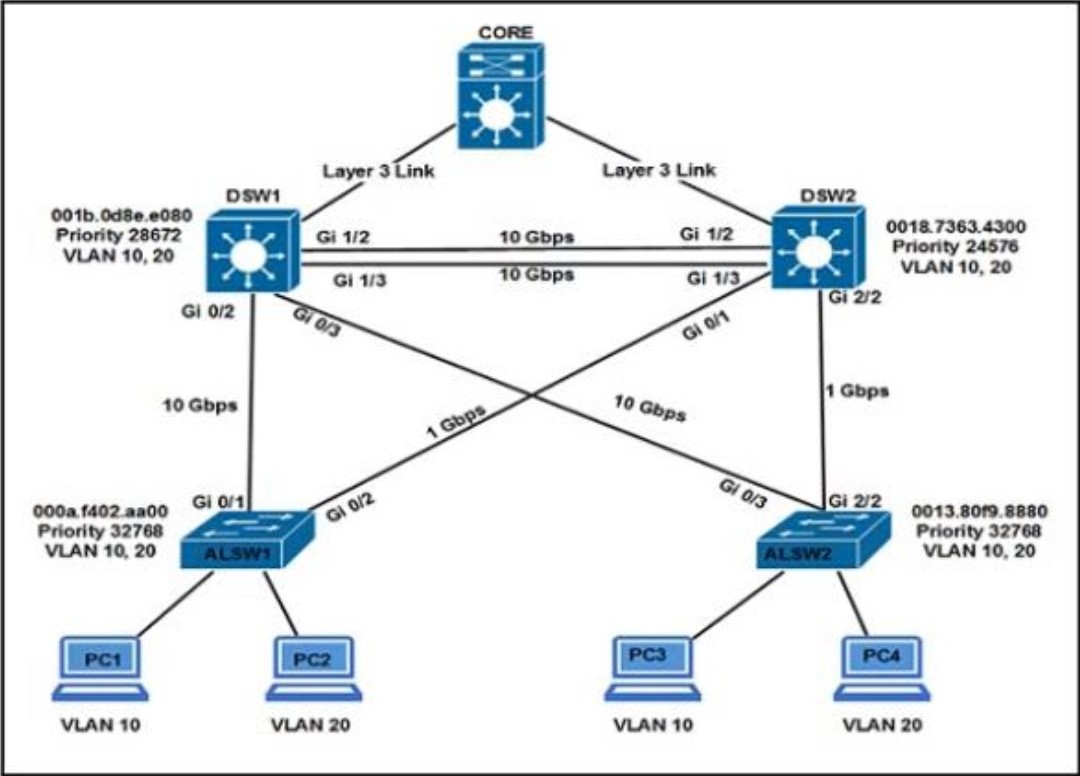
A. DSW2(config-if)#spanning-tree port-priority 128
B. DSW2(config-if)#spanning-tree port-priority 16
C. DSW2(config-if)#interface gi1/3
D. DSW1(config-if)#interface gi1/3
E. DWS1(config-if)#spanning-tree port-priority 0
QUESTION 39
How do the MAC address table and TCAM differ?
A. TCAM is populated from the ARP file, and the MAC address table is populated from the switch configuration file.
B. TCAM stores Layer 2 forwarding information, and the MAC address table stores QoS information.
C. TCAM is a type of memory, and the MAC address table is a logical structure.
D. TCAM lookups can match only 1s and 0s, and MAC address lookups can match 1s, Os, and a third “care/don’t care” state.
QUESTION 40
Which algorithms are used to secure REST API from brute attacks and minimize the impact?
A. SHA-512 and SHA-384
B. MD5 algorithm-128 and SHA-384
C. SHA-1, SHA-256, and SHA-512
D. PBKDF2, BCrypt, and SCrypt
QUESTION 41
A network administrator is implementing a routing configuration change and enables routing debugs to track routing behavior during the change. The logging output on the terminal is interrupting the command typing process.
Which two actions can the network administrator take to minimize the possibility of typing commands incorrectly? (Choose two.)
A. Configure the logging synchronous global configuration command.
B. Configure the logging synchronous command under the vty.
C. Increase the number of lines on the screen using the terminal length command.
D. Configure the logging delimiter feature.
E. Press the TAB key to reprint the command in a new line.
QUESTION 42
Refer to the exhibit.Which command must be applied to R2 for an OSPF neighborship to form?
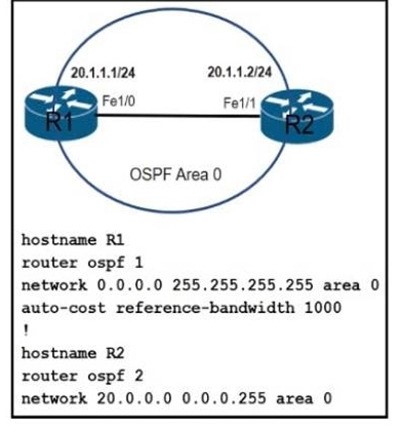
A. network 20.1.1.2.0.0.0.0 area 0
B. network 20.1.1.2 255.255.0.0. area 0
C. network 20.1.1.2.0.0.255.255 area 0
D. network 20.1.1.2 255.255.255 area 0
QUESTION 43
Which data is properly formatted with JSON?

A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: C
QUESTION 44
Refer to the exhibit. Which troubleshooting a routing issue, an engineer issues a ping from S1 to S2. When two actions from the initial value of the TTL? (Choose two.)
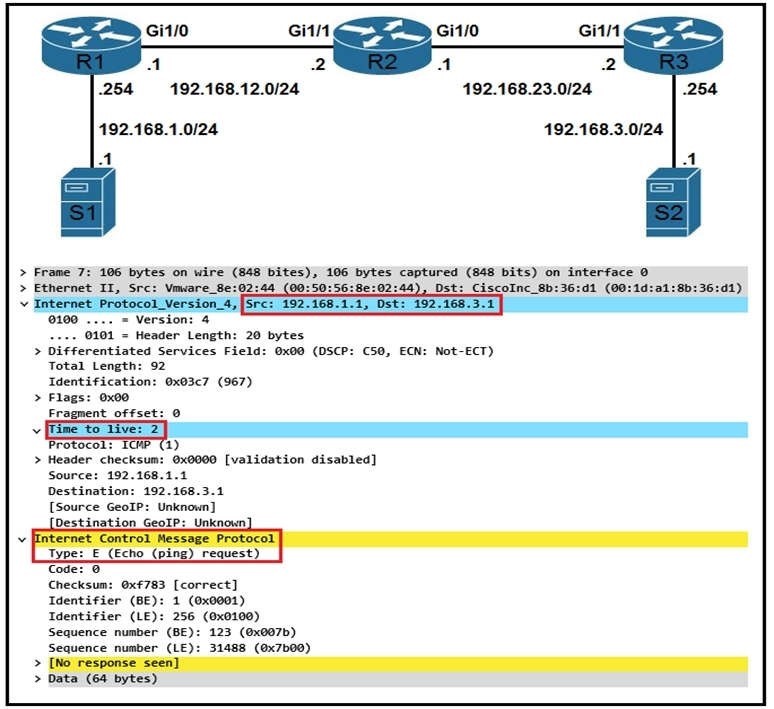
A. The packet reaches R3, and the TTL expires
B. R2 replies with a TTL exceeded message
C. R3 replies with a TTL exceeded message.
D. The packet reaches R2 and the TTL expires
E. R1 replies with a TTL exceeded message
F. The packet reaches R1 and the TTL expires.
QUESTION 45
Which two actions, when applied in the LAN network segment, will facilitate Layer 3 CAPWAP discovery for lightweight AP? (Choose two.)
A. Utilize DHCP option 17.
B. Configure WLC IP address on LAN switch.
C. Utilize DHCP option 43.
D. Configure an ip helper-address on the router interface
E. Enable port security on the switch port
QUESTION 46
Refer to the exhibit. What is required to configure a second export destination for IP address 192.168.10.1?
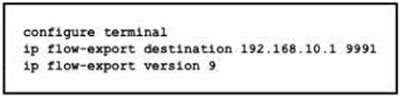
A. Specify a VRF.
B. Specify a different UDP port.
C. Specify a different flow ID
D. Configure a version 5 flow-export to the same destination.
E. Specify a different TCP port.
QUESTION 47
Refer to the exhibit. External users require HTTP connectivity to an internal company web server that is listening on TCP port 8080. Which command set accomplishes this requirement?
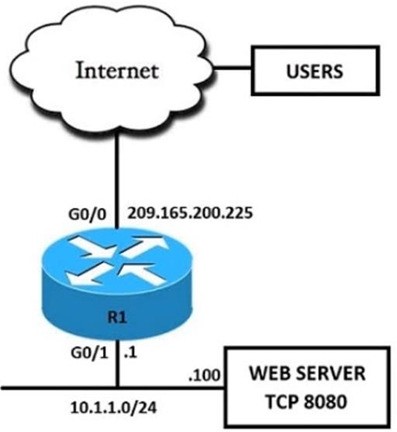

A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
QUESTION 48
Which measure is used by an NTP server to indicate its closeness to the authoritative time source?
A. time zone
B. hop count
C. stratum
D. latency
QUESTION 49
Which JSON syntax is valid?
A. {“switch”: “name”: “dist1”, “interfaces”: [“gig1”, “gig2”, “gig3″]}
B. {/”switch/”: {/”name/”: “dist1″, /”interfaces/”: [“gig1”, “gig2”, “gig3”]}}
C. {“switch”: {“name”: “dist1”, “interfaces”: [“gig1”, “gig2”, “gig3”]}}
D. {`switch’: (`name’: `dist1′, `interfaces’: [`gig1′, `gig2′, `gig3′])}
QUESTION 50
Which devices does Cisco DNA Center configure when deploying an IP-based access control policy?
A. All devices integrating with ISE
B. selected individual devices
C. all devices in selected sites
D. all wired devices
QUESTION 51
Refer to the exhibit.

An engineer reconfigures the pot-channel between SW1 and SW2 from an access port to a trunk and immediately notices this error in SW1’s log.
%PM-SP-4-ERR_DISABLE: bpduguard error detected on Gi0/0, putting Gi0/0 in errdisable state.
Which command set resolves this error?
A. Sw1(config)# interface G0/0
Sw1(config-if)# spanning-tree bpduguard enable
Sw1(config-if)# shut
Sw1(config-if)# no shut
B. Sw1(config)# interface G0/0
Sw1(config-if)# no spanning-tree bpduguard enable
Sw1(config-if)# shut
Sw1(config-if)# no shut
C. Sw1(config)# interface G0/1
Sw1(config-if)# spanning-tree bpduguard enable
Sw1(config-if)# shut
Sw1(config-if)# no shut
D. Sw1(config)# interface G0/0
Sw1(config-if)# no spanning-tree bpdufilter
Sw1(config-if)# shut
Sw1(config-if)# no shut
QUESTION 52
Refer to the exhibit. What is the effect of the configuration?

A. The device will allow users at 192.168.0.202 to connect to vty lines 0 through 4 using the password ciscotestkey
B. The device will allow only users at 192 168.0.202 to connect to vty lines 0 through 4
C. When users attempt to connect to vty lines 0 through 4. the device will authenticate them against TACACS* if local authentication fails
D. The device will authenticate all users connecting to vty lines 0 through 4 against TACACS+
QUESTION 53
Refer to the exhibit. After implementing the configuration 172.20.20.2 stops replaying to ICMP echoes, but the default route fails to be removed. What is the reason for this behavior?
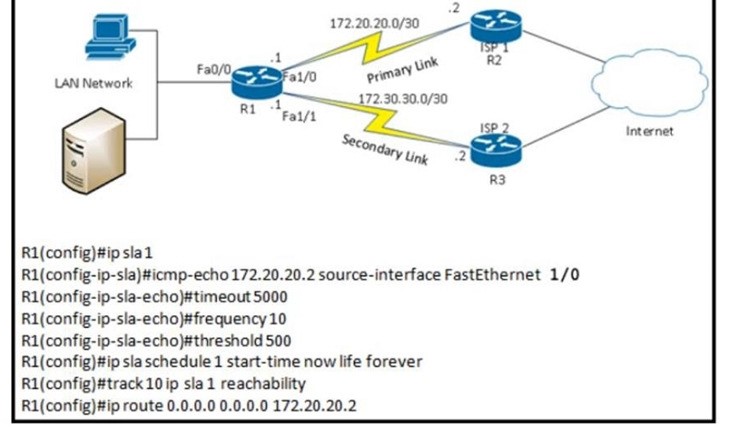
A. The source-interface is configured incorrectly.
B. The destination must be 172.30.30.2 for icmp-echo
C. The default route is missing the track feature
D. The threshold value is wrong.
QUESTION 54
Refer to the exhibit. Communication between London and New York is down. Which command set must be applied to the NewYork switch to resolve the issue?
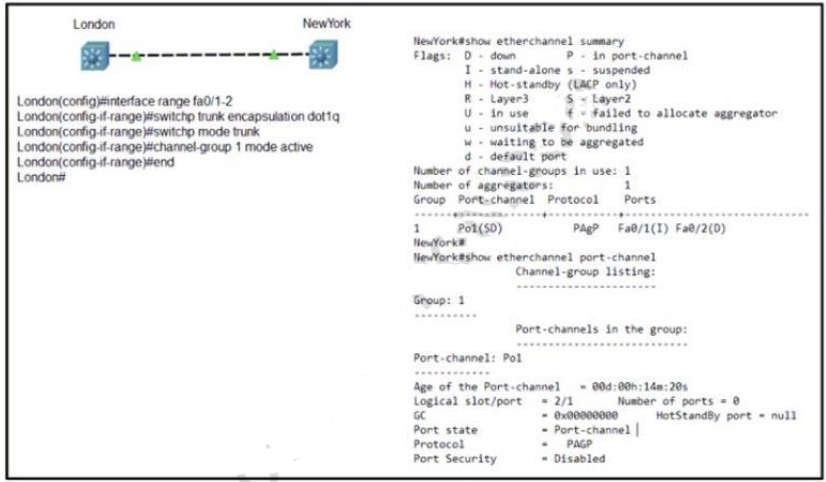
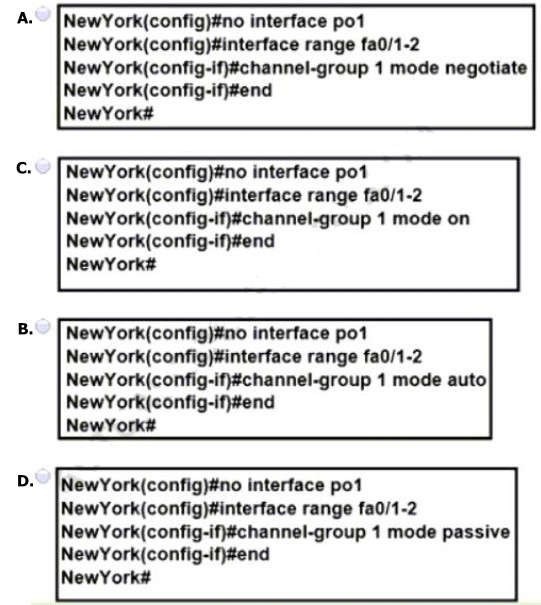
A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 55
Refer to the exhibit.Which configuration establishes EBGP connected neighborship between these two directly connected neighbors and exchanges the loopback network of the two routers through BGP?
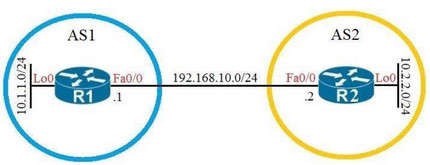
A. R1(config)#router bgp 1
R1(config-router)#neighbor 192.168.10.2 remote-as 2
R1(config-router)#network 10.1.1.0 mask 255.255.255.0
R2(config)#router bgp 2
R2(config-router)#neighbor 192.168.10.1 remote-as 1
R2(config-router)#network 10.2.2.0 mask 255.255.255.0
B. R1(config)#router bgp 1
R1(config-router)#neighbor 10.2.2.2 remote-as 2
R1(config-router)#network 10.1.1.0 mask 255.255.255.0
R2(config)#router bgp 2
R2(config-router)#neighbor 10.1.1.1 remote-as 1
R2(config-router)#network 10.2.2.0 mask 255.255.255.0
C. R1(config)#router bgp 1
R1(config-router)#neighbor 192.168.10.2 remote-as 2
R1(config-router)#network 10.0.0.0 mask 255.0.0.0
R2(config)#router bgp 2
R2(config-router)#neighbor 192.168.10.1 remote-as 1
R2(config-router)#network 10.0.0.0 mask 255.0.0.0
D. R1(config)#router bgp 1
R1(config-router)#neighbor 10.2.2.2 remote-as 2
R1(config-router)#neighbor 10.2.2.2 update-source |o0
R1(config-router)#network 10.1.1.0 mask 255.255.255.0
R2(config)#router bgp 2
R2(config-router)#neighbor 10.1.1.1 remote-as 1
R2(config-router)#neighbor 10.1.1.1 update-source |o0
R2(config-router)#network 10.2.2.0 mask 255.255.255.0
QUESTION 56
Refer to the exhibit.

What is the JSON syntax that is formed from the data?
A. {Name: Bob Johnson, Age: 75, Alive: true, Favorite Foods: [Cereal, Mustard, Onions]}
B. {“Name”: “Bob Johnson”, “Age”: 75, “Alive”: true, “Favorite Foods”: [“Cereal”, “Mustard”, “Onions”]}
C. {`Name’: `Bob Johnson’, `Age’: 75, `Alive’: True, `Favorite Foods’: `Cereal’, `Mustard’, `Onions’}
D. {“Name”: “Bob Johnson”, “Age”: Seventyfive, “Alive”: true, “Favorite Foods”: [“Cereal”, “Mustard”, “Onions”]}
QUESTION 57
Refer to the exhibit.

VLANs 50 and 60 exist on the trunk links between all switches. All access ports on SW3 are configured for VLAN 50 and SW1 is the VTP server. Which command ensures that SW3 receives frames only from VLAN 50?
A. SW1(config)#vtp mode transparent
B. SW3(config)#vtp mode transparent
C. SW2(config)#vtp pruning
D. SW1(config)#vtp pruning
QUESTION 58
A customer has several small branches and wants to deploy a Wi-Fi solution with local management using CAPWAP. Which deployment model meets this requirement?
A. local mode
B. autonomous
C. SD-Access wireless
D. Mobility Express
QUESTION 59
Which OSPF network types are compatible and allow communication through the two peering devices?
A. point-to-multipoint to nonbroadcast
B. broadcast to nonbroadcast
C. point-to-multipoint to broadcast
D. broadcast to point-to-point
QUESTION 60
Refer to the exhibit.
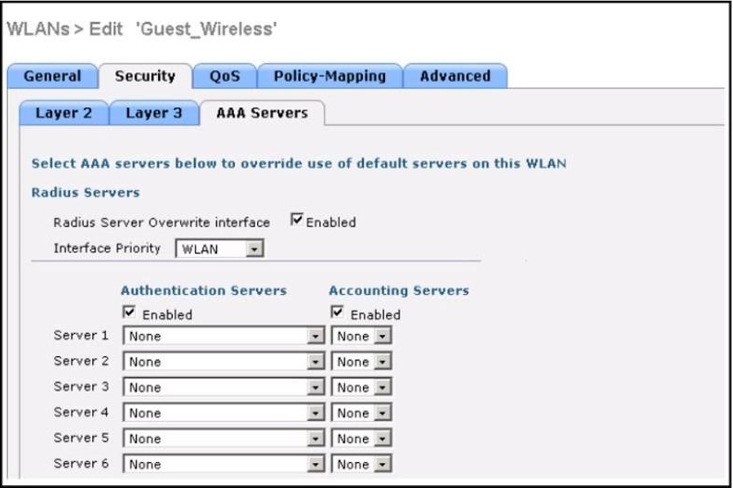
Assuming the WLC’s interfaces are not in the same subnet as the RADIUS server, which interface would the WLC use as the source for all RADIUS related traffic?
A. the interface specified on the WLAN configuration
B. any interface configured on the WLC
C. the controller management interface
D. the controller virtual interface
QUESTION 61
Refer to the exhibit.
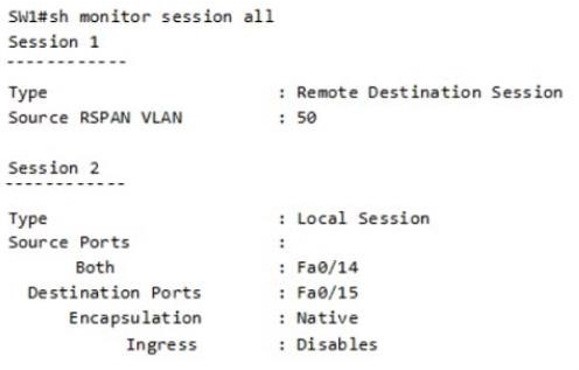
An engineer configures monitoring on SW1 and enters the show command to verify operation. What does the output confirm?
A. SPAN session 1 monitors activity on VLAN 50 of a remote switch
B. SPAN session 2 only monitors egress traffic exiting port FastEthernet 0/14.
C. SPAN session 2 monitors all traffic entering and exiting port FastEthernet 0/15.
D. RSPAN session 1 is incompletely configured for monitoring
QUESTION 62
What is the role of the RP in PIM sparse mode?
A. The RP responds to the PIM join messages with the source of requested multicast group
B. The RP maintains default aging timeouts for all multicast streams requested by the receivers
C. The RP acts as a control-plane node and does not receive or forward multicast packets
D. The RP is the multicast that is the root of the PIM-SM shared multicast distribution tree
QUESTION 63
Refer to the exhibit. After running the code in the exhibit. Which step reduces the amount of data that NETCONF server returns to the NETCONF client, to only the interface’s configuration?
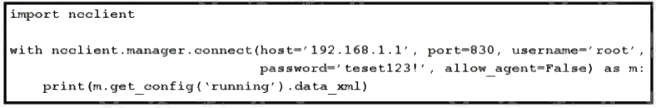
A. Use the txml library to parse the data returned by the NETCONF server for the interface’s configuration
B. Create an XML filter as a string and pass it to get_config() method as an argument.
C. Create a JSON filter as a string and pass it to the get_config() method as an argument.
D. Use the JSON library to parse the data returned by the NETCONF server for the interface’s configuration.
QUESTION 64
Refer to the exhibit. Communication between London and New York is down Which command set must be applied to resolve this issue?


A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 65
When a wireless client roams between two different wireless controllers, a network connectivity outage is experience for a period of time. Which configuration issue would cause this problem?
A. Not all of the controllers in the mobility group are using the same mobility group name
B. Not all of the controllers within the mobility group are using the same virtual interface IP address
C. All of the controllers within the mobility group are using the same virtual interface IP address
D. All of the controllers in the mobility group are using the same mobility group name
QUESTION 66
An engineer must configure a GRE tunnel interface in the default mode. The engineer has assigned an IPv4 address on the tunnel and sourced the tunnel from an ethernet interface. Which additional configuration must be made on the tunnel interface?
A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 67
Refer to the exhibit. isco DNA Center has obtained the username of the client and the multiple devices that the client is using on the network. How is Cisco DNA Center getting these context details?
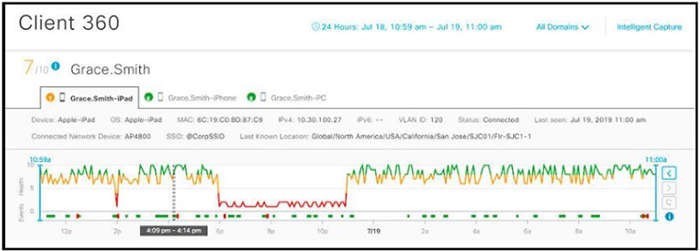
A. The administrator had to assign the username to the IP address manually in the user database tool on Cisco DNA Center.
B. Those details are provided to Cisco DNA Center by the Identity Services Engine
C. Cisco DNA Center pulled those details directly from the edge node where the user connected.
D. User entered those details in the Assurance app available on iOS and Android devices
QUESTION 68
Refer to the exhibit.

An engineer must modify the access control list EGRESS to allow all IP traffic from subnet 10.1.10.0/24 to 10.1.2.0/24. The access control list is applied in the outbound direction on router interface GigabitEthernet 0/1. Which configuration commands can the engineer use to allow this traffic without disrupting existing traffic flows?
A.
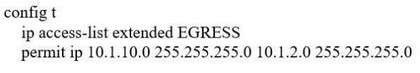
B.

C.

D.

QUESTION 69
A network engineer configures a new GRE tunnel and enters the show run command. What does the output verify?
A. The tunnel will be established and work as expected
B. The tunnel destination will be known via the tunnel interface
C. The tunnel keepalive is configured incorrectly because they must match on both sites
D. The default MTU of the tunnel interface is 1500 byte.
QUESTION 70
When configuring WPA2 Enterprise on a WLAN, which additional security component configuration is required?
A. PKI server
B. NTP server
C. RADIUS server
D. TACACS server
QUESTION 71
Refer to the exhibit. A GRE tunnel has been created between HQ and BR routers. What is the tunnel IP on the HQ router?

A. 10.111.111.1
B. 10.111.111.2
C. 209.165.202.130
D. 209.165.202.134
QUESTION 72
Which technology is used as the basis for the cisco SD-Access data plane?
A. IPsec
B. LISP
C. VXLAN
D. 802.1Q
QUESTION 73
Refer to the exhibit. Which single security feature is recommended to provide Network Access Control in the enterprise?
A. MAB
B. 802.1X
C. WebAuth
D. port security sticky MAC
QUESTION 74
How is Layer 3 roaming accomplished in a unified wireless deployment?
A. An EoIP tunnel is created between the client and the anchor controller to provide seamless connectivity as the client is associated with the new AP.
B. The client entry on the original controller is passed to the database on the new controller.
C. The new controller assigns an IP address from the new subnet to the client
D. The client database on the original controller is updated the anchor entry, and the new controller database is updated with the foreign entry.
QUESTION 75
A company plans to implement intent-based networking in its campus infrastructure. Which design facilities a migrate from a traditional campus design to a programmer fabric designer?
A. Layer 2 access
B. three-tier
C. two-tier
D. routed access
QUESTION 76
A customer has recently implemented a new wireless infrastructure using WLC-5520S at a site directly next to a large commercial airport Users report that they intermittently lose Wi-Fi connectivity, and troubleshooting reveals it is due to frequent channel changes Which two actions fix this issue? (Choose two)
A. Remove UNII-2 and Extended UNII-2 channels from the 5 Ghz channel list
B. Restore the OCA default settings because this automatically avoids channel interference
C. Disable DFS channels to prevent interference writ) Doppler radar
D. Enable DFS channels because they are immune to radar interference
E. Configure channels on the UNII-2 and the Extended UNII-2 sub-bands of the 5 Ghz band only
QUESTION 77
Where is radio resource management performed in a cisco SD-access wireless solution?
A. DNA Center
B. control plane node
C. wireless controller
D. Cisco CMX
QUESTION 78
When is an external antenna used inside a building?
A. only when using Mobility Express
B. when it provides the required coverage
C. only when using 2 4 GHz
D. only when using 5 GHz
QUESTION 79
Which three elements determine Air Time efficiency? (Choose three)
A. evert-driven RRM
B. data rate (modulation density) or QAM
C. channel bandwidth
D. number of spatial streams and spatial reuse
E. RF group leader
F. dynamic channel assignment
QUESTION 80
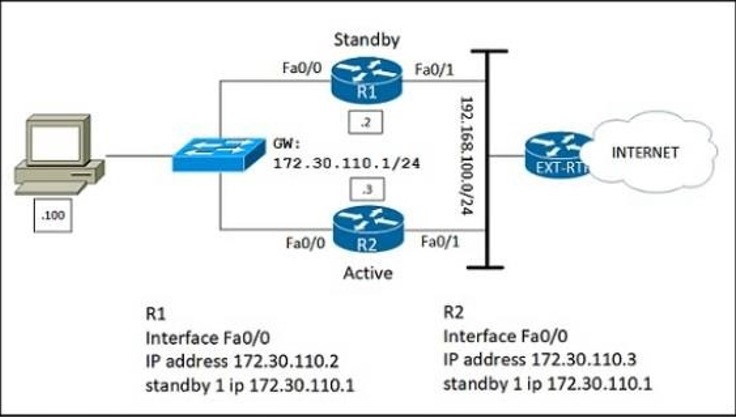
Refer to the exhibit. Which configuration change ensures that R1 is the active gateway whenever it is in a functional state for the 172.30.110.0/24 network?

A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 81
Which protocol does REST API rely on to secure the communication channel?
A. HTTP
B. SSH
C. HTTPS
D. TCP
QUESTION 82
Which element enables communication between guest VMs within a virtualized environment?
A. hypervisor
B. vSwitch
C. virtual router
D. pNIC
QUESTION 83
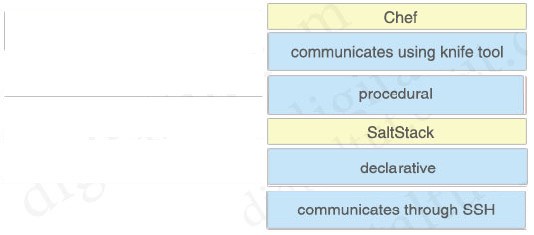
Which characteristic distinguishes Ansible from Chef?
A. Ansible lacs redundancy support for the master server. Chef runs two masters in an active/active mode.
B. Ansible uses Ruby to manage configurations. Chef uses YAML to manage configurations.
C. Ansible pushes the configuration to the client. Chef client pulls the configuration from the server.
D. The Ansible server can run on Linux, Unix or Windows. The Chef server must run on Linux or Unix.
QUESTION 84
Refer to the exhibit. An engineer attempts to configure a router on a stick to route packets between Clients, Servers, and Printers; however, initial tests show that this configuration is not working. Which command set resolves this issue?

A. router eigrp 1
network 10.0.0.0 255.0.0.0
network 172.16.0.0 255.255.0.0
network 192.168.1.0 255.255.0.0
B. router eigrp 1
network 10.0.0.0 255.255.255.0
network 172.16.0.0 255.255.255.0
network 192.168.1.0 255.255.255.0
C. interface Vlan10
no ip vrf forwarding Clients
!
interface Vlan20
no ip vrf forwarding Servers
!
interface Vlan30
no ip vrf forwarding Printers
D. interface Vlan10
no ip vrf forwarding Clients
ip address 192.168.1.2 255.255.255.0
!
interface Vlan20
no ip vrf forwarding Servers
ip address 172.16.1.2 255.255.255.0
!
interface Vlan30
no ip vrf forwarding Printers
ip address 10.1.1.2 255.255.255.0
QUESTION 85
Refer to the exhibit. Security policy requires all idle-exec sessions to be terminated in 600 seconds. Which configuration achieves this goal?

A. line vty 0 15 absolute-timeout 600
B. line vty 0 15 exec-timeout
C. line vty 0 15 exec-timeout 10 0
D. line vty 0 4 exec-timeout 600
QUESTION 86
What is a type 2 hypervisor?
A. Installed as an application on an already installed operating system.
B. Runs directly on a physical server and includes its own operating system.
C. Supports over-allocation of physical resources.
D. Also referred to as a “bare metal hypervisor” because it sits directly on the physical
QUESTION 87
What are two characteristics of VXLAN? (Choose two)
A. It uses VTEPs to encapsulate and decapsulate frames.
B. It has a 12-bit network identifier
C. It allows for up to 16 million VXLAN segments
D. It lacks support for host mobility
E. It extends Layer 2 and Layer 3 overlay networks over a Layer 2 underlay.
QUESTION 88
What is the difference between the MAC address table and TCAM?
A. The MAC address table is contained in TCAM. ACL and QoS information is stored in CAM.
B. Router prefix lookups happen in TCAM. MAC address table lookups happen in CAM.
C. TCAM is used to make L2 forwarding decisions. CAM is used to build routing tables
D. The MAC address table supports partial matches. TCAM requires an exact match.
QUESTION 89
Refer the exhibit. Which router is the designated router on the segment 192.168.0.0/24?
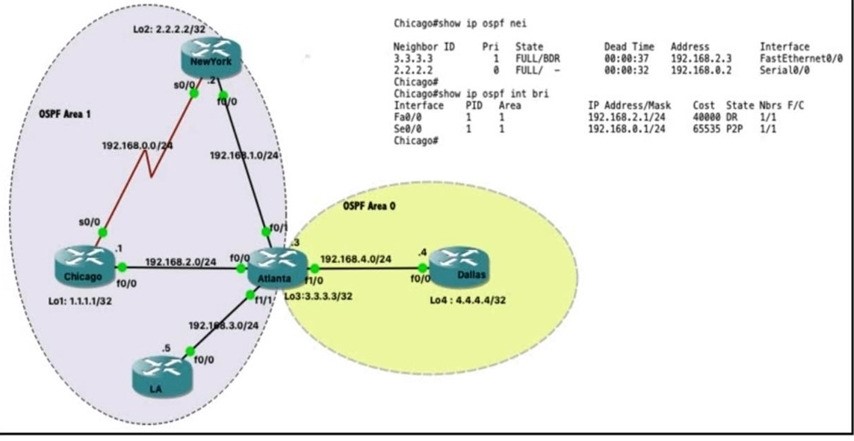
A. This segment has no designated router because it is a nonbroadcast network type.
B. This segment has no designated router because it is a p2p network type.
C. Router Chicago because it has a lower router ID
D. Router NewYork because it has a higher router ID
QUESTION 90
Refer to the exhibit.Which IP address becomes the active next hop for 192.168.102.0/24 when 192.168.101.2 fails?
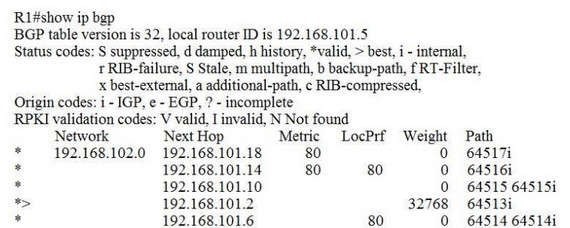
A. 192.168.101.10
B. 192.168.101.14
C. 192.168.101.6
D. 192.168.101.18
QUESTION 91
Which two threats does AMP4E have the ability to block? (Choose two.)
A. DDoS
B. ransomware
C. Microsoft Word macro attack
D. SQL injection
E. email phishing
QUESTION 92
In an SD-WAN deployment, which action in the vSmart controller responsible for?
A. handle, maintain, and gather configuration and status for nodes within the SD-WAN fabric
B. onboard vEdge nodes into the SD-WAN fabric
C. gather telemetry data from yEdge routers
D. distribute policies that govern data forwarding performed within the SD-WAN fabric
QUESTION 93
Which two operations are valid for RESTCONF? (Choose two.)
A. PULL
B. PUSH
C. PATCH
D. REMOVE
E. ADD
F. HEAD
QUESTION 94
Refer to the exhibit. An engineer must ensure that all traffic entering AS 200 from AS 100 will choose Link 2 as an entry point. Assuming that all BGP neighbor relationships have been formed and that the attributes have not been changed on any of the routers, which configuration accomplish task?
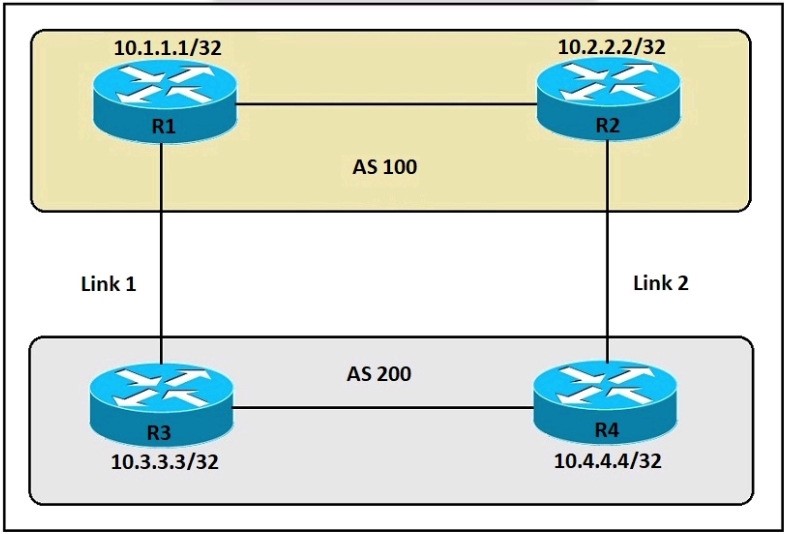
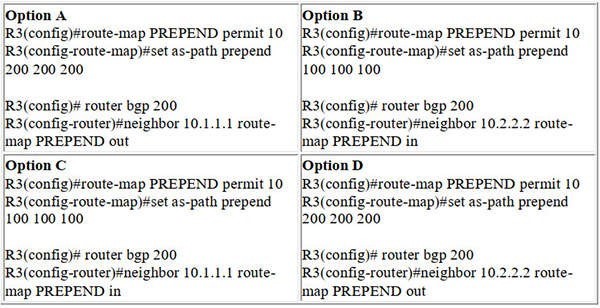
A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 95
Which function is handled by vManage in the Cisco SD-WAN fabric?
A. Establishes BFD sessions to test liveliness of links and nodes
B. Distributes policies that govern data forwarding
C. Performs remote software upgrades for WAN Edge. vSmart and vBond
D. Establishes IPsec tunnels with nodes.
QUESTION 96
Refer to the exhibit. What does the snippet of code achieve?
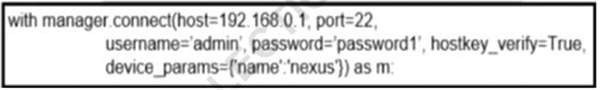
A. It creates a temporary connection to a Cisco Nexus device and retrieves a token to be used for API calls.
B. It opens a tunnel and encapsulates the login information, if the host key is correct.
C. It opens an ncclient connection to a Cisco Nexus device and maintains it for the duration of the context.
D. It creates an SSH connection using the SSH key that is stored, and the password is ignored.
QUESTION 97
Which configuration restricts the amount of SSH that a router accepts 100 kbps?
A. class-map match-all CoPP_SSH match access-group name CoPP_SSH
!
Policy-map CoPP_SSH class CoPP_SSHpolice cir 100000 exceed-action drop
! ! !
Interface GigabitEthernet0/1 ip address 209.165.200.225 255.255.255.0 ip access-group CoPP_SSH out
duplex auto speed auto media-type rj45
service-policy input CoPP_SSH
!
ip access-list extended CoPP_SSH permit tcp any any eq 22
!
B. class-map match-all CoPP_SSH match access-group name CoPP_SSH
!
Policy-map CoPP_SSH class CoPP_SSH police cir CoPP_SSH
exceed-action drop
!
Interface GigabitEthernet0/1
ip address 209.165.200.225 255.255.255.0
ip access-group … out duplex auto speed auto media-type rj45
service-policy input CoPP_SSH
!
Ip access-list extended CoPP_SSH deny tcp any any eq 22
!
C. class-map match-all CoPP_SSH match access-group name CoPP_SSH
!
Policy-map CoPP_SSH class CoPP_SSH police cir 100000
exceed-action drop
! !
!
Control-plane
service-policy input CoPP_SSH
!
ip access-list extended CoPP_SSH permit tcp any any eq 22
!
D. class-map match-all CoPP_SSH match access-group name CoPP_SSH
!
Policy-map CoPP_SSH class CoPP_SSH
police cir 100000 exceed-action drop
!
Control-plane transit
service-policy input CoPP_SSH
!
Ip access-list extended CoPP_SSH permit tcp any any eq 22
!
QUESTION 98
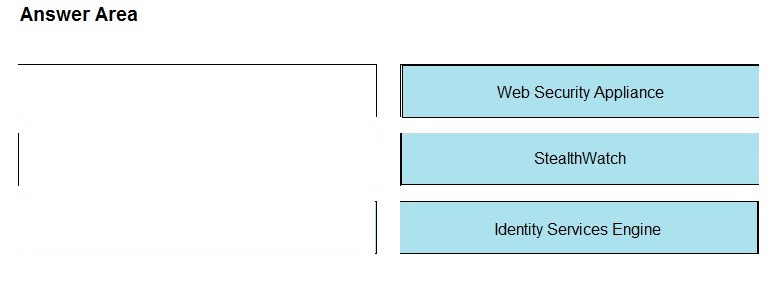
Which component of the Cisco Cyber Threat Defense solution provides user and flow context analysis?
A. Cisco Firepower and FireSIGHT
B. Cisco Stealth watch system
C. Advanced Malware Protection
D. Cisco Web Security Appliance
QUESTION 99
The login method is configured on the VTY lines of a router with these parameters. ![]() The first method for authentication is TACACS
The first method for authentication is TACACS
![]() If TACACS is unavailable, login is allowed without any provided credentials
If TACACS is unavailable, login is allowed without any provided credentials
Which configuration accomplishes this task?
A. R1#sh run | include aaaaaa new-model
aaa authentication login VTY group tacacs+ none
aaa session-id common R1#sh run | section vty line vty 0 4
password 7 0202039485748 R1#sh run | include username
R1#
B. R1#sh run | include aaaaaa new-model
aaa authentication login telnet group tacacs+ none
aaa session-id common R1#sh run | section vty
line vty 0 4
R1#sh run | include username
R1#
C. R1#sh run | include aaaaaa new-model
aaa authentication login default group tacacs+ none
aaa session-id common R1#sh run | section vty line vty 0 4
password 7 0202039485748
D. R1#sh run | include aaa aaa new-model
aaa authentication login default group tacacs+
aaa session-id common
R1#sh run | section vty
line vty 0 4
transport input none
R1#
QUESTION 100
What is YANG used for?
A. scraping data via CLI
B. processing SNMP read-only polls
C. describing data models
D. providing a transport for network configuration data between client and server
Correct Answer: C
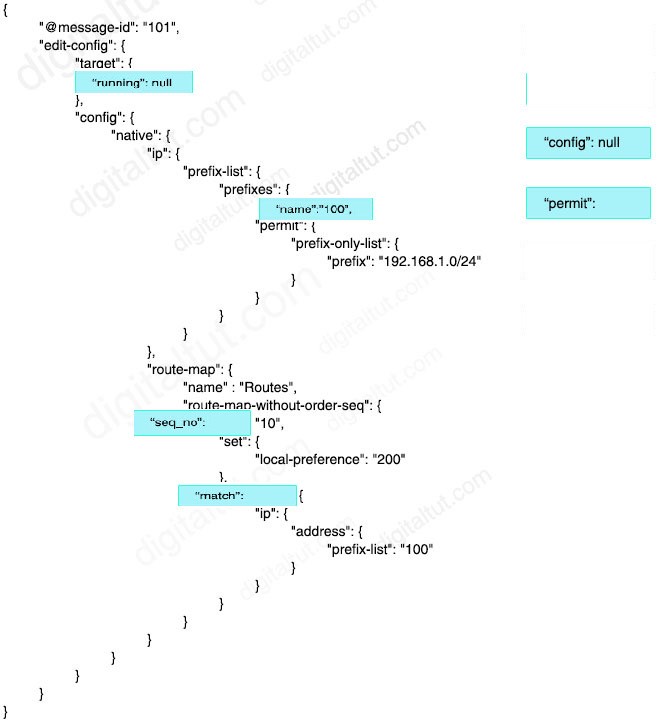
QUESTION 101
Which command set configures RSPAN to capture outgoing traffic from VLAN 3 on interface GigabitEthernet 0/3 while ignoring other VLAN traffic on the same interface?

A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 102
Which encryption hashing algorithm does NTP use for authentication?
A. SSL
B. MD5
C. AES128
D. AES256
QUESTION 103
An engineer runs the code against an API of Cisco DNA Center, and the platform returns this output What does the response indicate?
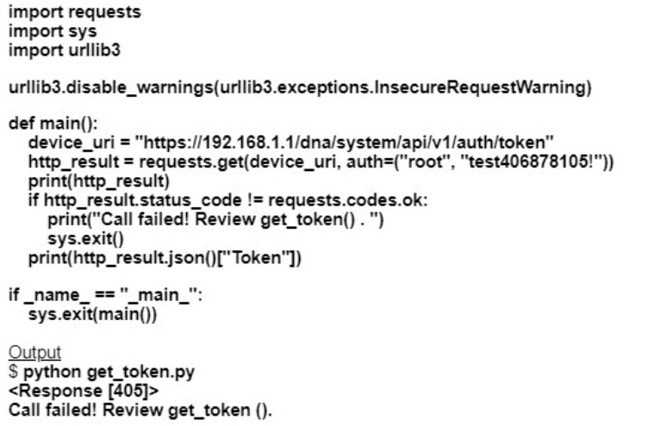
A. The authentication credentials are incorrect
B. The URl string is incorrect.
C. The Cisco DNA Center API port is incorrect
D. The HTTP method is incorrect
Correct Answer: D
QUESTION 104
Refer to the exhibit. What is the effect of these commands on the BR and HQ tunnel interfaces?
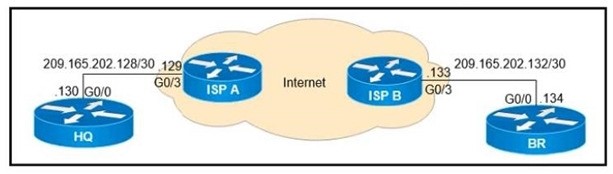

A. The tunnel line protocol goes down when the keepalive counter reaches 6
B. The keepalives are sent every 5 seconds and 3 retries
C. The keepalives are sent every 3 seconds and 5 retries.
D. The tunnel line protocol goes down when the keepalive counter reaches 5
QUESTION 105
Which exhibit displays a valid JSON file?
A.

B.
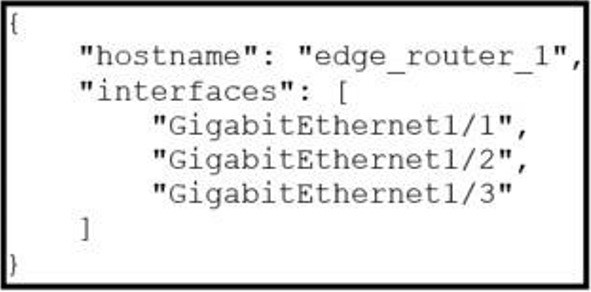
C.
D.
QUESTION 106
What is one benefit of implementing a VSS architecture?
A. It provides multiple points of management for redundancy and improved support.
B. It uses GLBP to balance traffic between gateways
C. It provides a single point of management for improved efficiency
D. It uses a single database to manage configuration for multiple switches
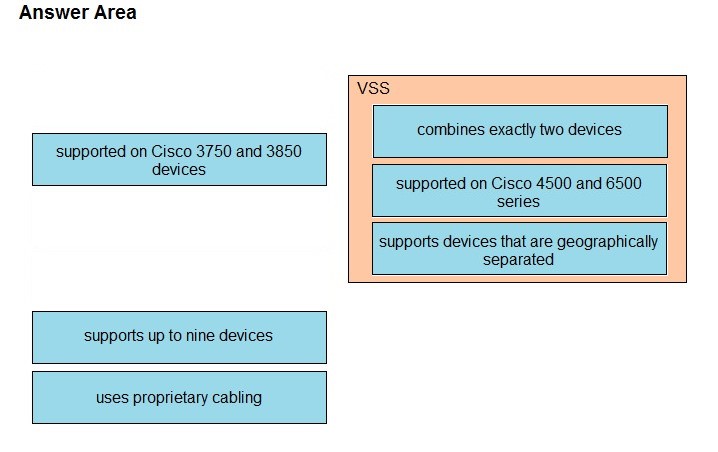
QUESTION 107
Which two results occur if Cisco DNA Center loses connectivity to devices in the SD-Access fabric? (Choose two)
A. All devices reload after detecting loss of connection to Cisco DNA Center B. Already connected users are unaffected, but new users cannot connect
C. User connectivity is unaffected.
D. Cisco DNA Center is unable to collect monitoring data in Assurance.
E. Users lose connectivity
QUESTION 108
Refer to the exhibit. An engineer is troubleshooting a connectivity issue and executes a traceroute. What does the result confirm?
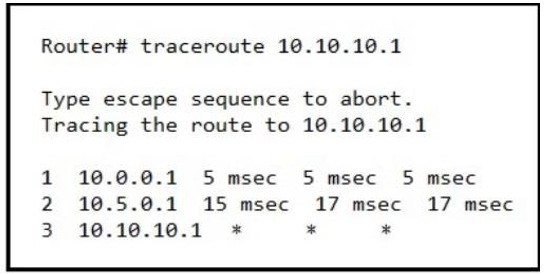
A. The destination server reported it is too busy
B. The protocol is unreachable
C. The destination port is unreachable
D. The probe timed out
QUESTION 109
Which method does Cisco DNA Center use to allow management of non-Cisco devices through southbound protocols?
A. It creates device packs through the use of an SDK
B. It uses an API call to interrogate the devices and register the returned data.
C. It obtains MIBs from each vendor that details the APIs available.
D. It imports available APIs for the non-Cisco device in a CSV format.
QUESTION 110
An engineer is troubleshooting the Ap join process using DNS. Which FQDN must be resolvable on the network for the access points to successfully register to the WLC?
A. wlcbostname.domain.com
B. cisco-capwap-controller.domain.com
C. ap-manager.domain.com
D. primary-wlc.domain.com
QUESTION 111
Refer to the exhibit. R1 is able to ping the R3 fa0/1 interface. Why do the extended pings fail?
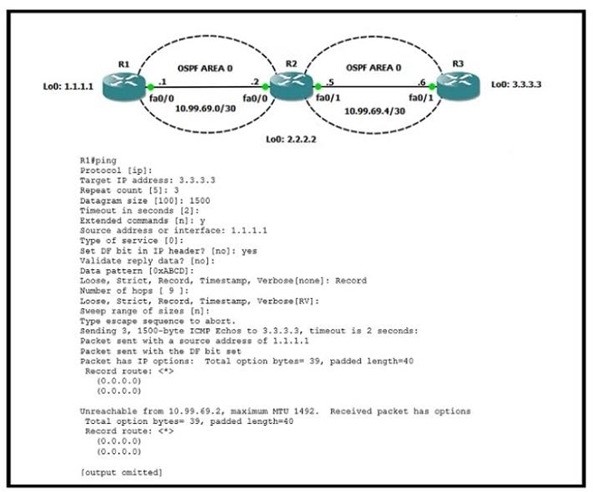
A. The maximum packet size accepted by the command is 1476 bytes.
B. R3 is missing a return route to 10.99.69.0/30
C. R2 and R3 do not have an OSPF adjacency
D. The DF bit has been set
QUESTION 112
Refer to the exhibit. Which Python code snippet prints the descriptions of disabled interfaces only?


A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 113
What is the structure of a JSON web token?
A. three parts separated by dots: header, payload, and signature
B. three parts separated by dots: version, header, and signature
C. header and payload
D. payload and signature
QUESTION 114
After a redundant route processor failure occurs on a Layer 3 device, which mechanism allows for packets to be forwarded from a neighboring router based on the most recent tables?
A. RPVST+
B. NSF
C. BFD
D. RP failover
QUESTION 115
Which control plane protocol is used between Cisco SD-WAN routers and vSmart controllers?
A. BGP
B. OMP
C. TCP
D. UDP
QUESTION 116
Which method should an engineer use to deal with a long-standing contention issue between any two VMs on the same host?
A. Adjust the resource reservation limits
B. Live migrate the VM to another host
C. Reset the VM
D. Reset the host
QUESTION 117
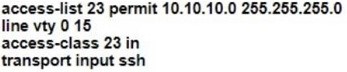
Refer to the exhibit.
line vty 0 4 session-timeout 30 exec-timeout 120 0 session-limit 30 login local line vty 5 15 session-timeout 30 exec-timeout 30 0 session-limit 30 login local
Only administrators from the subnet 10.10.10.0/24 are permitted to have access to the router. A secure protocol must be used for the remote access and management of the router instead of clear-text protocols.
Which configuration achieves this goal?
A.

B.
C.
D.
QUESTION 118
Refer to the exhibit. An engineer implemented several configuration changes and receives the logging message on switch1. Which action should the engineer take to resolve this issue?
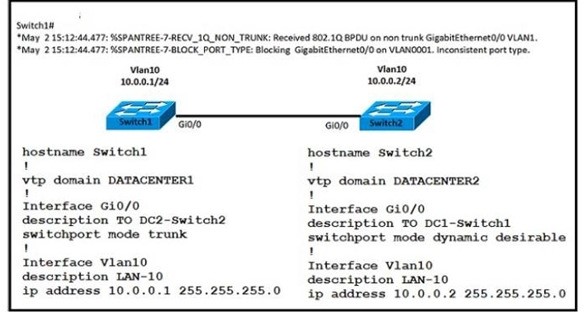
A. Change the VTP domain to match on both switches
B. Change Switch2 to switch port mode dynamic auto
C. Change Switch1 to switch port mode dynamic auto
D. Change Switch1 to switch port mode dynamic desirable
QUESTION 119
What is the function of the LISP map resolver?
A. to send traffic to non-LISP sites when connected to a service provider that does not accept nonroutable EIDs as packet sources
B. to connect a site to the LISP-capable part of a core network, publish the EID-to-RLOC mappings for the site and respond to map-request messages
C. to decapsulate map-request messages from ITRs and forward the messages to the MS
D. to advertise routable non-USP traffic from one address family to LISP sites in a different address family
QUESTION 120
How does the RIB differ from the FIB?
A. The RIB is used to create network topologies and routing tables. The FIB is a list of routes to particular network destinations.
B. The FIB includes many routes a single destination. The RIB is the best route to a single destination.
C. The RIB includes many routes to the same destination prefix. The FIB contains only the best route
D. The FIB maintains network topologies and routing tables. The RIB is a Iist of routes to particular network destinations.
QUESTION 121
Refer to the exhibit. Which JSON syntax is derived from this data?
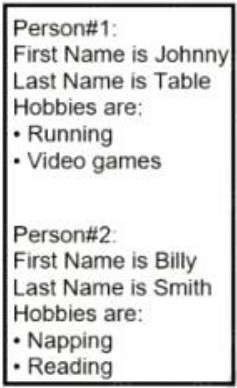

A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 122
Refer to the exhibit. A network engineer must simplify the IPsec configuration by enabling IPsec over GRE using IPsec profiles. Which two configuration changes accomplish this? (Choose two).
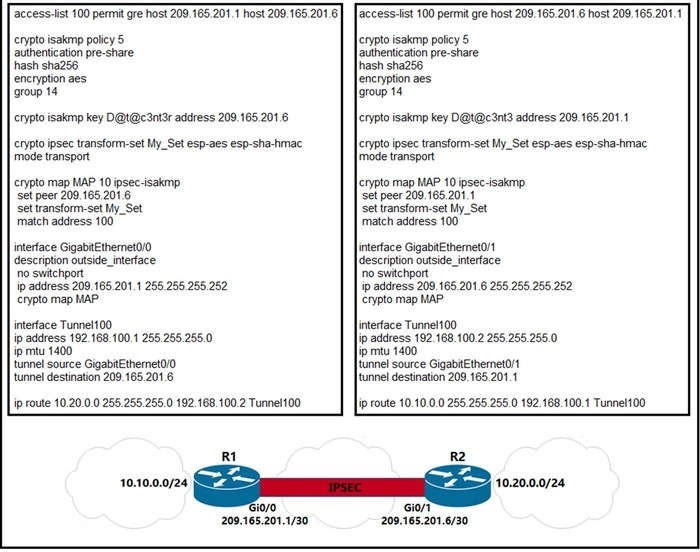
A. Create an IPsec profile, associate the transform-set ACL, and apply the profile to the tunnel interface.
B. Apply the crypto map to the tunnel interface and change the tunnel mode to tunnel mode ipsec ipv4.
C. Remove all configuration related to crypto map from R1 and R2 and eliminate the ACL.
D. Create an IPsec profile, associate the transform-set, and apply the profile to the tunnel interface.
E. Remove the crypto map and modify the ACL to allow traffic between 10.10.0.0/24 to 10.20.0.0/24.
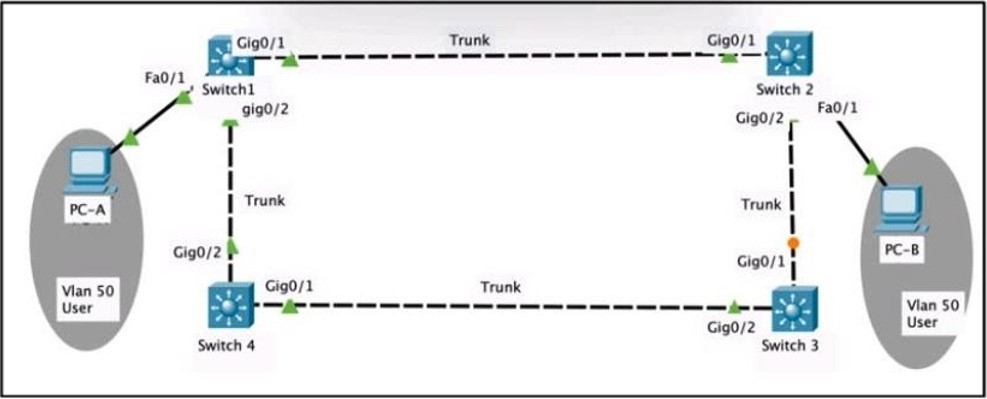
QUESTION 123
Refer to the exhibit. Rapid PVST+ is enabled on all switches. Which command set must be configured on switch1 to achieve the following results on port fa0/1?
• When a device is connected, the port transitions immediately to a forwarding state
• The interface should not send or receive BPDUs
• If a BPDU is received, it continues operating normally.
A.

B.
C.

D.

QUESTION 124
A company has an existing Cisco 5520 HA cluster using SSO. An engineer deploys a new single Cisco Catalyst 9800 WLC to test new features. The engineer successfully configures a mobility tunnel between the 5520 cluster and 9800 WLC. Clients connected to the corporate WLAN roam seamlessly between access points on the 5520 and 9800 WLC. After a failure on the primary 5520 WLC, all WLAN services remain functional; however clients cannot roam between the 5520 and 9800 controllers without dropping their connection. Which feature must be configured to remedy the issue?
A. mobility MAC on the 5520 cluster
B. mobility MAC on the 9800 WLC
C. new mobility on the 5520 cluster
D. new mobility on the 9800 WLC
QUESTION 125
Refer to the exhibit.
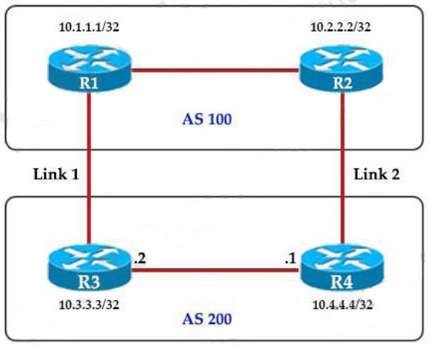
An engineer must ensure that all traffic leaving AS 200 will choose Link 2 as the exit point. Assuming that all BGP neighbor relationships have been formed and that the attributes have not been changed on any of the routers, which configuration accomplish task?
A. R4(config-router)#bgp default local-preference 200 B. R3(config-router)#neighbor 10.1.1.1 weight 200
C. R3(config-router)#bgp default local-preference 200
D. R4(config-router)#neighbor 10.2.2.2 weight 200
QUESTION 126
In a wireless Cisco SD-Access deployment, which roaming method is used when a user moves from one access point to another on a different access switch using a single WLC?
A. Layer 3
B. inter-xTR
C. auto anchor
D. fast roam
QUESTION 127
Which congestion queuing method on Cisco IOS based routers uses four static queues?
A. Priority
B. custom
C. weighted fair
D. low latency
QUESTION 128
Refer to the exhibit. What are two effects of this configuration? (Choose two.)
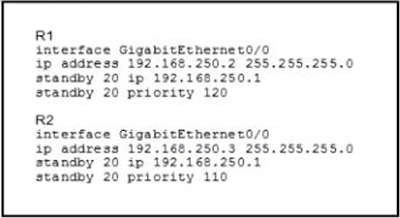
A. R1 becomes the active router.
B. R1 becomes the standby router.
C. If R2 goes down, R1 becomes active but reverts to standby when R2 comes back online.
D. If R1 goes down. R2 becomes active and remains the active device when R1 comes back online.
E. If R1 goes down, R2 becomes active but reverts to standby when R1 comes back online.
QUESTION 129
Wireless users report frequent disconnections from the wireless network. While troubleshooting a network engineer finds that after the user a disconnect, the connection reestablishes automatically without any input required. The engineer also notices these message logs.
Which action reduces the user impact?

A. increase the dynamic channel assignment interval
B. increase BandSelect
C. increase the AP heartbeat timeout
D. enable coverage hole detection
QUESTION 130
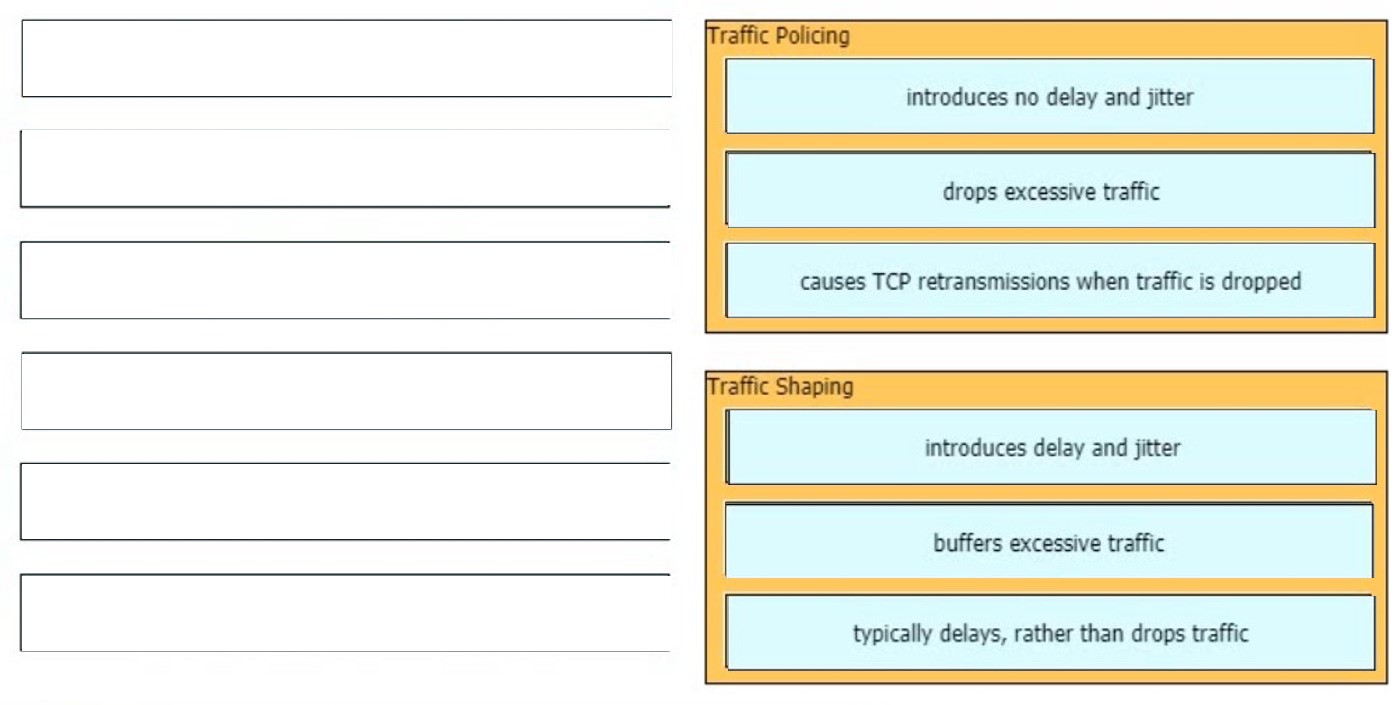
An engineer is describing QoS to a client. Which two facts apply to traffic policing? (Choose two)
A. Policing adapts to network congestion by queuing excess traffic
B. Policing should be performed as close to the destination as possible
C. Policing drops traffic that exceeds the defined rate
D. Policing typically delays the traffic, rather than drops it
E. Policing should be performed as close to the source as possible
QUESTION 131
“HTTP/1.1 204 No Content” is returned when the curl -i -x DELETE command is issued. Which situation has occurred?
A. The object could not be located at the URI path
B. The command succeeded in deleting the object
C. The object was located at the URI, but it could not be deleted.
D. The URI was invalid
QUESTION 132
An engineer is configuring local web authentication on a WLAN. The engineer chooses the Authentication radio button under the Layer 3 Security options for Web Policy. Which device presents the web authentication for the WLAN?
A. ISE server
B. RADIUS server
C. anchor WLC
D. local WLC
QUESTION 133
Which two methods are used to reduce the AP coverage area? (Choose two.)
A. Increase minimum mandatory data rate
B. Reduce AP transmit power
C. Disable 2.4 GHz and use only 5 GHz.
D. Enable Fastlane.
E. Reduce channel width from 40 MHz to 20 MHz
QUESTION 134
How do cloud deployments differ from on-prem deployments?
A. Cloud deployments require longer implementation times than on-premises deployments
B. Cloud deployments are more customizable than on-premises deployments.
C. Cloud deployments have lower upfront costs than on-premises deployments.
D. Cloud deployments require less frequent upgrades than on-premises deployments.
QUESTION 135
What is a consideration when designing a Cisco SD-Access underlay network?
A. End user subnets and endpoints are part of the underlay network.
B. The underlay switches provide endpoint physical connectivity for users.
C. Static routing is a requirement,
D. It must support IPv4 and IPv6 underlay networks.
QUESTION 136
Refer to the exhibit. An engineer is configuring an EtherChannel between Switch1 and Switch2 and notices the console message on Switch2. Based on the output, which action resolves this issue?
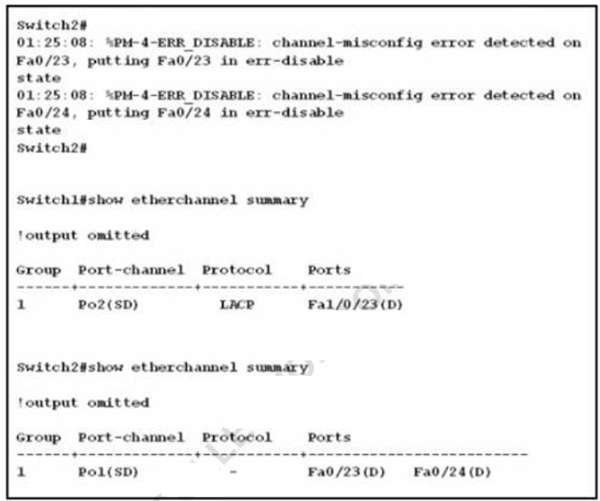
A. Configure less member ports on Switch2.
B. Configure the same port channel interface number on both switches C. Configure the same EtherChannel protocol on both switches
D. Configure more member ports on Switch1.
QUESTION 137
An engineer uses the Design workflow to create a new network infrastructure in Cisco DNA Center. How is the physical network device hierarchy structured?
A. by location
B. by role
C. by organization
D. by hostname naming convention
QUESTION 138
Which deployment option of Cisco NGFW provides scalability?
A. tap
B. inline tap
C. high availability
D. clustering
QUESTION 139
Refer to the exhibit.Which privilege level is assigned to VTY users?
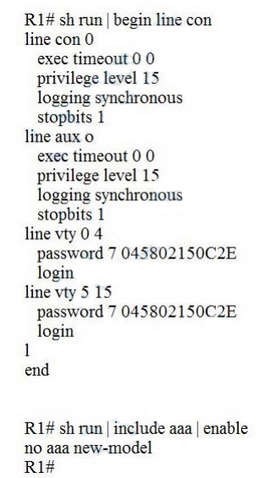
A. 1
B. 7
C. 13
D. 15
QUESTION 140
How are the different versions of IGMP compatible?
A. IGMPv2 is compatible only with IGMPv1. B. IGMPv2 is compatible only with IGMPv2.
C. IGMPv3 is compatible only with IGMPv3.
D. IGMPv3 is compatible only with IGMPv1
QUESTION 141
Refer to the exhibit. A network engineer configures OSPF and reviews the router configuration Which interface or interfaces are able to establish OSPF adjacency?
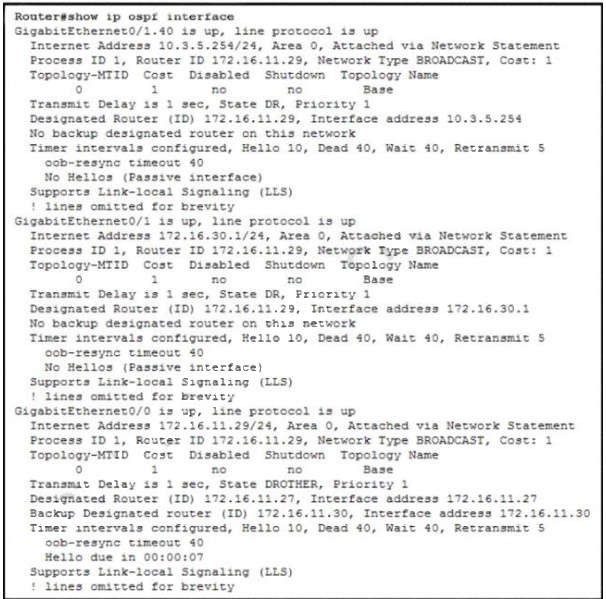
A. GigabitEthemet0/1 and GigabitEthernet0/1.40
B. only GigabitEthernet0/1
C. only GigabttEthernet0/0
D. Gigabit Ethernet0/0 and GigabitEthemet0/1
QUESTION 142
Refer to Exhibit. MTU has been configured on the underlying physical topology, and no MTU command has been configured on the tunnel interfaces. What happens when a 1500-byte IPv4 packet traverses the GRE tunnel from host X to host Y, assuming the DF bit is cleared?
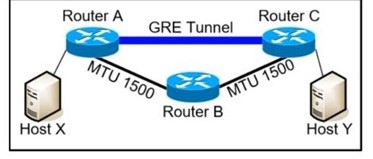
A. The packet arrives on router C without fragmentation.
B. The packet is discarded on router A
C. The packet is discarded on router BD. The packet arrives on router C fragmented.
QUESTION 143
Refer to the exhibit. Which two commands are needed to allow for full reachability between AS 1000 and AS 2000? (Choose two)
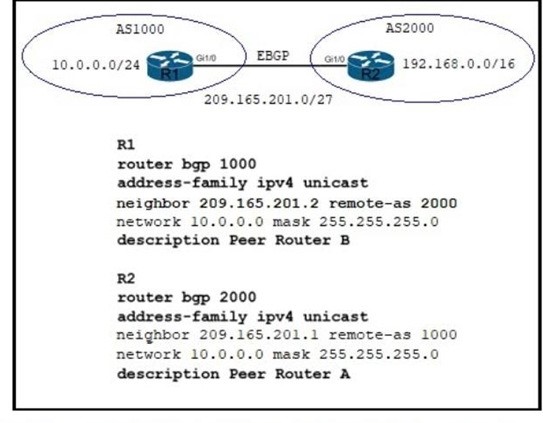
A. R1#network 19.168.0.0 mask 255.255.0.0
B. R2#network 10.0.0.0 255.255.255.0
C. R2#network 192.168.0.0 mask 255.255.0.0
D. R2#network 209.165.201.0 mask 255.255.192.0
E. R1#no network 10.0.0.0 255.255.255.0
QUESTION 144
Refer to the exhibit. A network engineer configures a GRE tunnel and enters the show Interface tunnel command. What does the output confirm about the configuration?

A. The keepalive value is modified from the default value.
B. Interface tracking is configured.
C. The tunnel mode is set to the default.
D. The physical interface MTU is 1476 bytes.
QUESTION 145
Refer to the exhibit.Which HTTP JSON response does the python code output give?

A. NameError: name `json’ is not defined
B. KeyError `kickstart_ver_str’
C. 7.61
D. 7.0(3)I7(4)
QUESTION 146
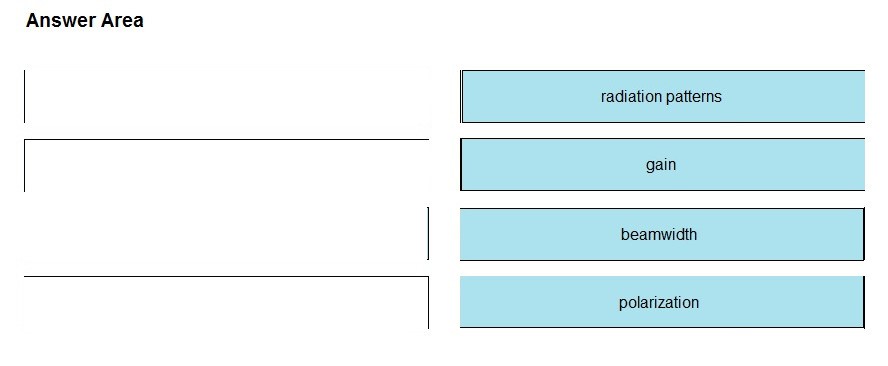
Refer to the exhibit. Which type of antenna do the radiation patterns present?
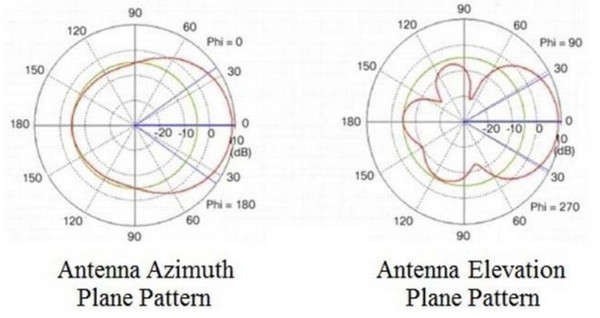
A. Yagi
B. patch
C. omnidirectional
D. dipole
QUESTION 147
An engineer must configure HSRP group 300 on a Cisco IOS router. When the router is functional, it must be the active HSRP router. The peer router has been configured using the default priority value. Which command set is required?
A. standby version 2standby 300 priority 110 standby 300 preempt
B. standby 300 priority 110standby 300 timers 1 110
C. standby 300 priority 90 standby 300 preempt
D. standby version 2 standby 300 priority 90 standby 300 preempt
QUESTION 148
Refer to exhibit. What are two reasons for IP SLA tracking failure? (Choose two )
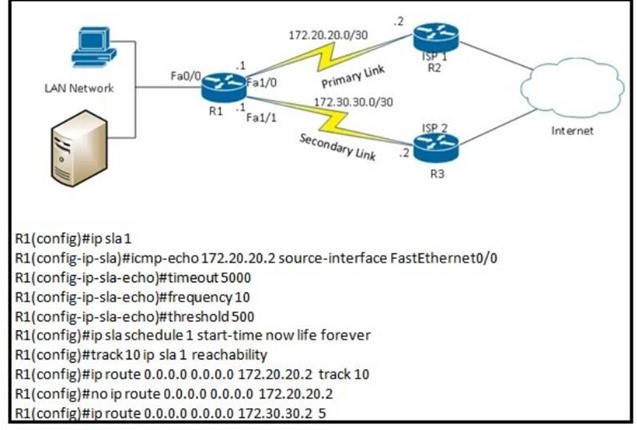
A. The destination must be 172.30 30 2 for icmp-echo
B. The threshold value is wrong
C. A route back to the R1 LAN network is missing in R2
D. The source-interface is configured incorrectly.
E. The default route has the wrong next hop IP address
QUESTION 149
What is the purpose of the LISP routing and addressing architecture?
A. It creates two entries for each network node, one for Its identity and another for its location on the network.
B. It allows LISP to be applied as a network visualization overlay though encapsulation.
C. It allows multiple Instances of a routing table to co-exist within the same router.
D. It creates head-end replication used to deliver broadcast and multicast frames to the entire network.
QUESTION 150
Refer to the exhibit. An engineer is investigating why guest users are able to access other guest user devices when the users are connected to the customer guest WLAN. What action resolves this issue?
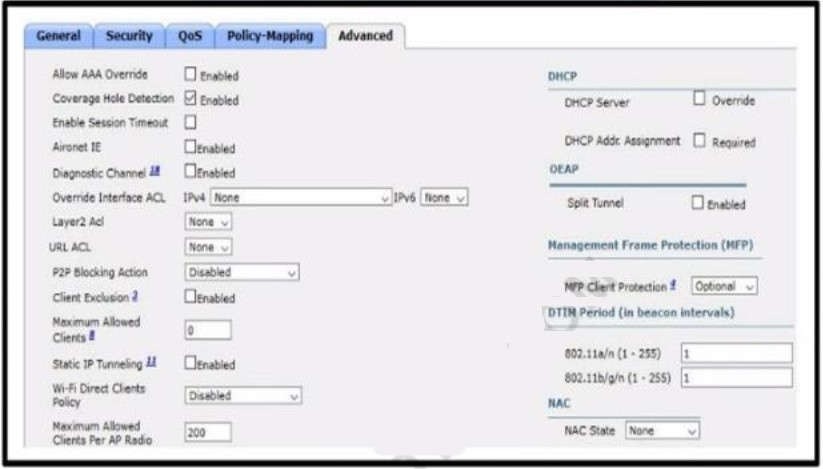
A. implement MFP client protection
B. implement split tunneling
C. implement P2P blocking
D. implement Wi-Fi direct policy
QUESTION 151
How does Cisco TrustSec enable more flexible access controls for dynamic networking environments and data centers?
A. uses flexible NetFlow
B. assigns a VLAN to the endpoint
C. classifies traffic based on advanced application recognition
D. classifies traffic based on the contextual identity of the endpoint rather than its IP address
QUESTION 152
Which DHCP option helps lightweight APs find the IP address of a wireless LAN controller?
A. Option 43 B. Option 60
C. Option 67
D. Option 150
QUESTION 153
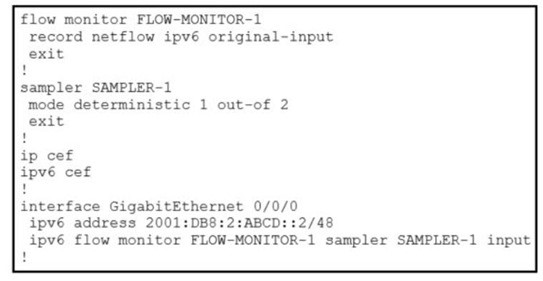
Refer to the exhibit. What is the effect of introducing the sampler feature into the Flexible NetFlow configuration on the router?
A. NetFlow updates to the collector are sent 50% less frequently.
B. Every second IPv4 packet is forwarded to the collector for inspection.
C. CPU and memory utilization are reduced when compared with what is required for full NetFlow.
D. The resolution of sampling data increases, but it requires more performance from the router.
QUESTION 154
An engineer must configure a ACL that permits packets which include an ACK In the TCP header. Which entry must be Included In the ACL?
A. access-list 110 permit tcp any any eq 21 tcp-ack
B. access-list 10 permit ip any any eq 21 tcp-ack
C. access-list 10 permit tcp any any eq 21 established
D. access-list 110 permit tcp any any eq 21 established
QUESTION 155
Which AP mode allows an engineer to scan configured channels for rogue access points?
A. sniffer
B. monitor
C. bridge
D. local
QUESTION 156
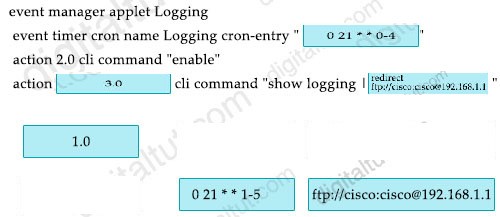
Refer to the exhibit. An engineer must create a script that appends the output of the show process cpu sorted command to a file. Which action completes the configuration? `

A. action 4.0 syslog command “show process cpu sorted | append flash:high-cpu-file”
B. action 4.0 cli command “show process cpu sorted | append flash:high-cpu-file”
C. action 4.0 ens-event “show process cpu sorted | append flash:high-cpu-file”
D. action 4.0 publish-event “show process cpu sorted | append flash:high-cpu-file”
QUESTION 157
Which measurement is used from a post wireless survey to depict the cell edge of the access points?
A. SNR
B. Noise
C. RSSI
D. CCI
QUESTION 158
A server running Linux is providing support for virtual machines along with DNS and DHCP services for a small business. Which technology does this represent?
A. container
B. Type 1 hypervisor
C. hardware pass-thru
D. Type 2 hypervisor
QUESTION 159
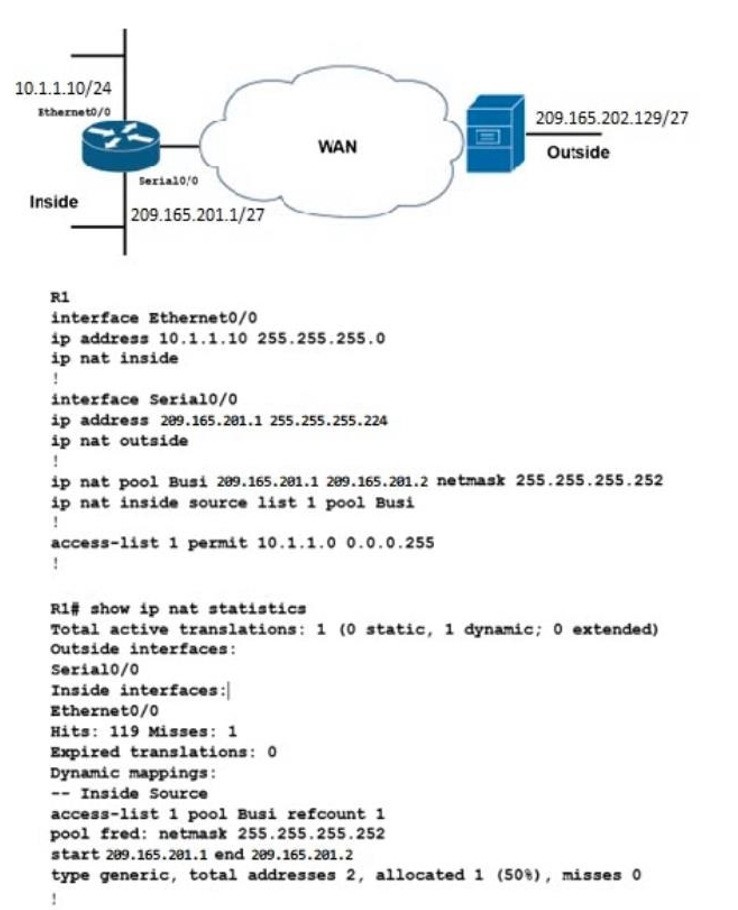
Refer to the exhibit. A network engineer configures NAT on R1 and enters the show command to verify the configuration What does the output confirm?
A. The first pocket triggered NAT to add on entry to NAT table
B. R1 is configured with NAT overload parameters
C. A Telnet from 160.1.1 1 to 10.1.1.10 has been initiated.
D. R1 to configured with PAT overload parameters
QUESTION 160
What is the centralized control policy in a Cisco SD-WAN deployment?
A. list of ordered statements that define user access policies
B. set of statements that defines how routing is performed
C. set of rules that governs nodes authentication within the cloud
D. list of enabled services for all nodes within the cloud
QUESTION 161
When a wired client connects to an edge switch in an SDA fabric, which component decides whether the client has access to the network?
A. control-plane node
B. Identity Service Engine
C. RADIUS server
D. edge node
QUESTION 162
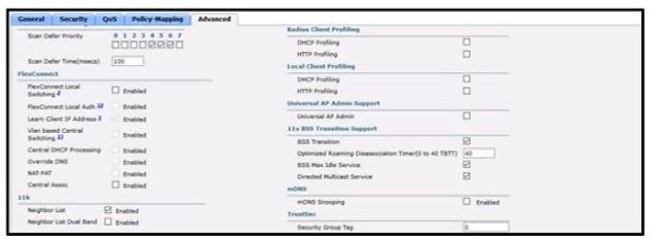
Refer to the exhibit. An engineer configured the Bonjour Gateway on a Cisco WLC to support Apple Airplay. Users cannot see Apple TV while on the WLAN. Which action resolves this
A. Enable FlexConnect Local Switching.
B. Enable mDNS Snooping.
C. Disable Neighbor List Dual Band.
D. Disable Directed Multicast
QUESTION 163
Refer to the exhibit. Which type of antenna is show on the radiation patterns?
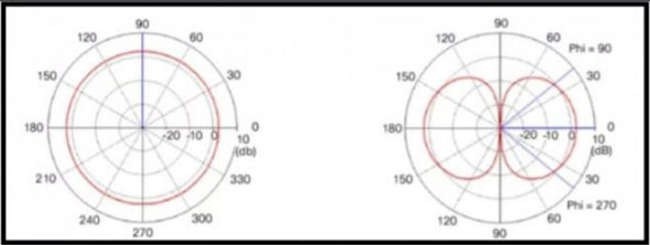
A. Dipole
B. Yagi
C. Patch
D. Omnidirectional
QUESTION 164
What function does vxlan perform in an SD-Access deployment?
A. policy plane forwarding
B. control plane forwarding
C. data plane forwarding
D. systems management and orchestration
QUESTION 165
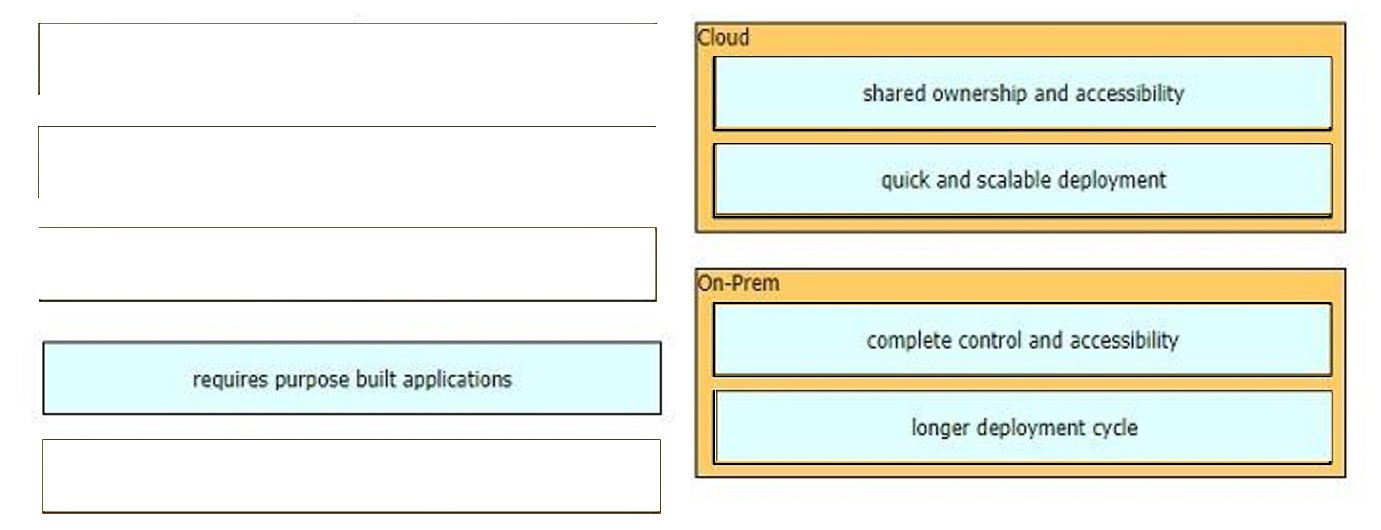
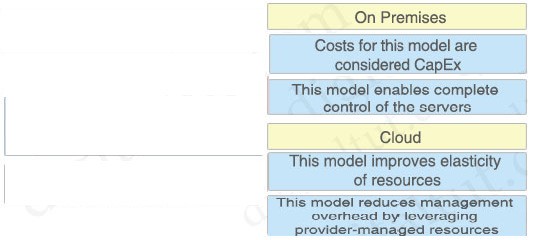
Why would a customer implement an on-premises solution instead of a cloud solution?
A. On-premises offers greater compliance for government regulations than cloud.
B. On-premises is more secure than cloud.
C. On-premises offers shorter deployment time than cloud.
D. On-premises offers greater scalability than cloud.
QUESTION 166
Refer to the exhibit.Which HTTP JSON response does the python code output give?

A. NameError: name `json’ is not defined
B. KeyError `kickstart_ver_str’
C. 7.61
D. 7.0(3)I7(4)
QUESTION 167
Refer to the exhibit How was spanning-tree configured on this interface?
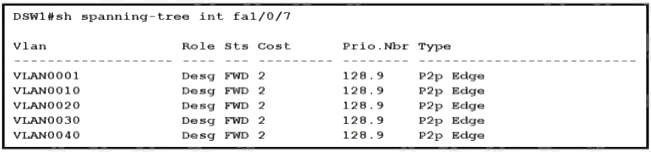
A. By entering the command spanning-tree portfast trunk in the interface configuration mode.
B. By entering the command spanning-tree portfast in the interface configuration mode
C. By entering the command spanning-tree mst1 vlan 10,20,30,40 in the global configuration mode
D. By entering the command spanning-tree vlan 10,20,30,40 root primary in the interface configuration mode
QUESTION 168
A network administrator applies the following configuration to an IOS device.
aaa new-model aaa authentication login default local group tacacs+
What is the process of password checks when a login attempt is made to the device?
A. A TACACS+ server is checked first. If that check fail, a database is checked
B. A TACACS+ server is checked first. If that check fail, a RADIUS server is checked. If that check fail, a local database is checked
C. A local database is checked first. If that fails, a TACACS+server is checked, if that check fails, a RADIUS server is checked
D. A local database is checked first. If that check fails, a TACACS+server is checked
QUESTION 169
Refer to the exhibit.
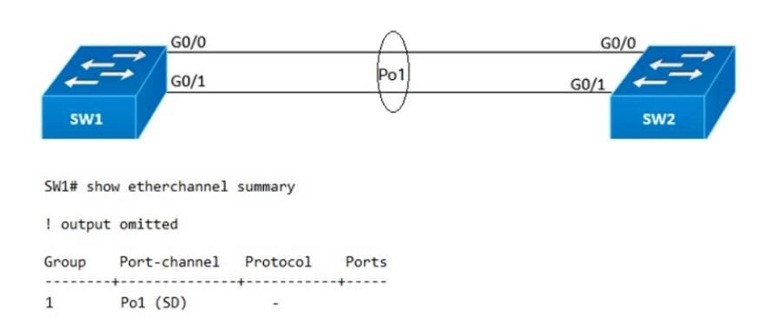
After an engineer configures an EtherChannel between switch SW1 and switch SW2, this error message is logged on switch SW2.

Based on the output from SW1 and the log message received on Switch SW2, what action should the engineer take to resolve this issue?
A. Configure the same protocol on the EtherChannel on switch SW1 and SW2.
B. Connect the configuration error on interface Gi0/1 on switch SW1.
C. Define the correct port members on the EtherChannel on switch SW1.
D. Correct the configuration error on interface Gi0/0 switch SW1.
QUESTION 170
Which two characteristics define the Intent API provided by Cisco DNA Center? (Choose two.)
A. northbound API
B. business outcome oriented
C. device-oriented
D. southbound API
E. procedural
QUESTION 171
What NTP stratum level is a server that is connected directly to an authoritative time source?
A. Stratum 0
B. Stratum 1
C. Stratum 14
D. Stratum 15
QUESTION 172
How is 802.11 traffic handled in a fabric-enabled SSID?
A. centrally switched back to WLC where the user traffic is mapped to a VXLAN on the WLC
B. converted by the AP into 802.3 and encapsulated into VXLAN
C. centrally switched back to WLC where the user traffic is mapped to a VLAN on the WLC
D. converted by the AP into 802.3 and encapsulated into a VLAN
QUESTION 173
Which DHCP option provides the CAPWAP APs with the address of the wireless controller(s)?
A. 43
B. 66
C. 69
D. 150
QUESTION 174
Refer to the exhibit. An engineer has configured Cisco ISE to assign VLANs to clients based on their method of authentication, but this is not working as expected. Which action will resolve this issue?
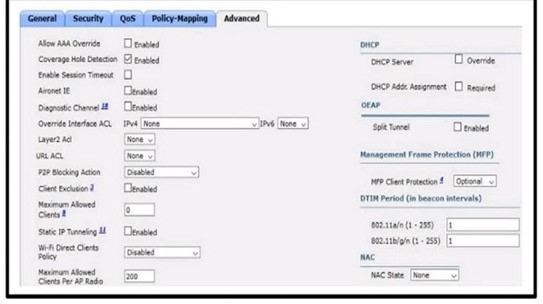
A. require a DHCP address assignment
B. utilize RADIUS profiling
C. set a NAC state
D. enable AAA override
QUESTION 175
What is the recommended MTU size for a Cisco SD-Access Fabric?
A. 1500
B. 9100
C. 4464
D. 17914
QUESTION 176
Refer to the exhibit. A network engineer must configure a password expiry mechanism on the gateway router for all local passwords to expire after 60 days. What is required to complete this task?
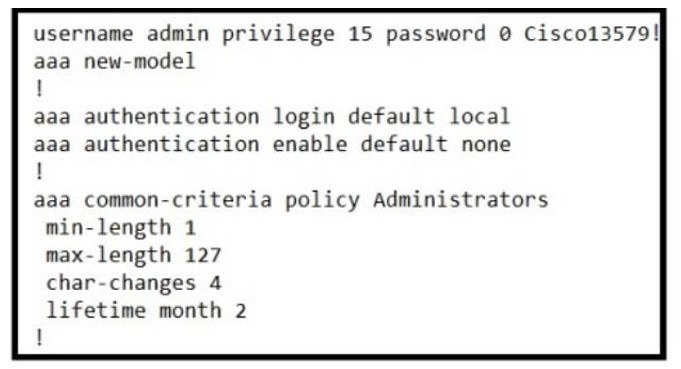
A. Add the username admin privilege 15 common-criteria-policy Administrators password Cisco13579! command.
B. Add the aaa authentication enable default Administrators command.
C. The password expiry mechanism is on the AAA server and must be configured there.
D. No further action is required. The configuration is complete
QUESTION 177
Refer to the exhibit. POSTMAN is showing an attempt to retrieve network device information from Cisco DNA Center API. What is the issue?
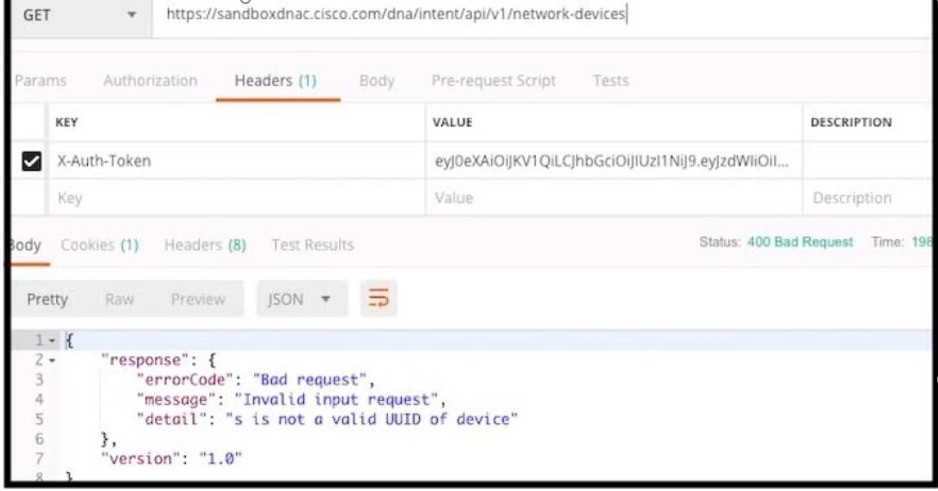
A. The URI string is incorrect
B. The token has expired.
C. Authentication has failed
D. The JSON payload contains the incorrect UUID
QUESTION 178
Which TCP setting is tuned to minimize the risk of fragmentation on a GRE/IP tunnel?
A. MSS
B. MTU
C. MRU
D. window size
QUESTION 179
Refer to the exhibit. On which interfaces should VRRP commands be applied to provide first hop redundancy to PC-01 and PC-02?
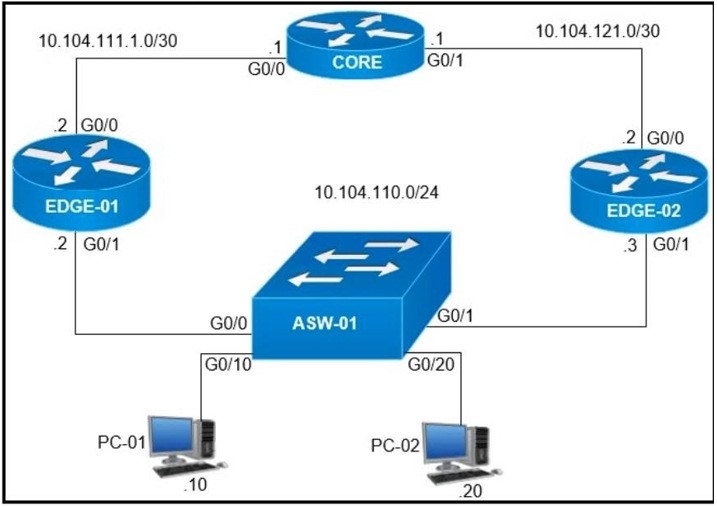
A. G0/0 and G0/1 on Core
B. G0/0 on Edge-01 and G0/0 on Edge-02
C. G0/1on Edge-01 and G0/1 on Edge-02
D. G0/0 and G0/1 on ASW-01
QUESTION 180
A customer requests a network design that supports these requirements:
* FHRP redundancy
* multivendor router environment* IPv4 and IPv6 hosts
Which protocol does the design include?
A. GLBP
B. VRRP version 2
C. VRRP version 3
D. HSRP version 2
QUESTION 181
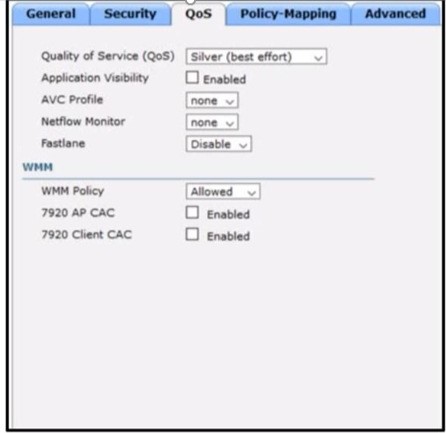

QUESTION 182
What is the responsibility of a secondary WLC?
A. It shares the traffic load of the LAPs with the primary controller.
B. It avoids congestion on the primary controller by sharing the registration load on the LAPs.
C. It registers the LAPs if the primary controller fails.
D. It enables Layer 2 and Layer 3 roaming between Itself and the primary controller.
QUESTION 183
Which protocol infers that a YANG data model is being used?
A. SNMP
B. REST
C. RESTCONF
D. NX-API
QUESTION 184
Refer to the exhibit. Which result does the python code achieve?
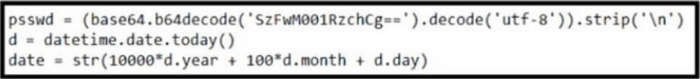
A. The code encrypts a base64 decrypted password.
B. The code converts time to the “year/month/day” time format.
C. The code converts time to the yyyymmdd representation.
D. The code converts time to the Epoch LINUX time format.
QUESTION 185
Which outcome is achieved with this Python code?

A. connects to a Cisco device using SSH and exports the routing table information
B. displays the output of the show command in a formatted way
C. connects to a Cisco device using SSH and exports the BGP table for the prefix
D. connects to a Cisco device using Telnet and exports the routing table information
QUESTION 186
Refer to the exhibit. After implementing the configuration 172.20.20.2 stops replaying to ICMP echoes, but the default route fails to be removed. What is the reason for this behavior?
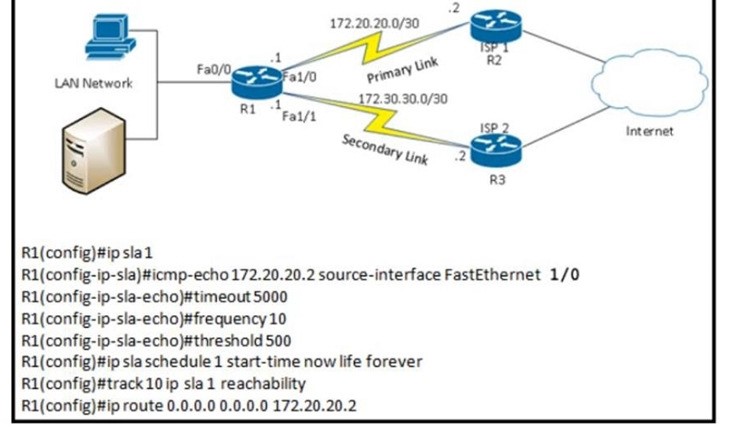
A. The source-interface is configured incorrectly.
B. The destination must be 172.30.30.2 for icmp-echo
C. The default route is missing the track feature
D. The threshold value is wrong.
QUESTION 187
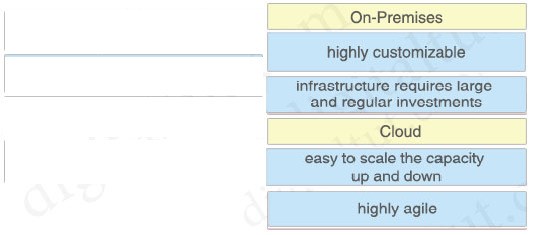
Which benefit is offered by a cloud infrastructure deployment but is lacking in an on-premises deployment?
A. efficient scalability
B. virtualization
C. storage capacity
D. supported systems
QUESTION 188
What is the data policy in a Cisco SD-WAN deployment?
A. list of ordered statements that define node configurations and authentication used within the SDWAN overlay
B. Set of statements that defines how data is forwarded based on IP packet information and specific VPNs
C. detailed database mapping several kinds of addresses with their corresponding location
D. group of services tested to guarantee devices and links liveliness within the SD-WAN overlay
QUESTION 189
Refer to the exhibit. PC-1 must access the web server on port 8080. To allow this traffic, which statement must be added to an access control list that is applied on SW2 port G0/0 in the inbound direction?
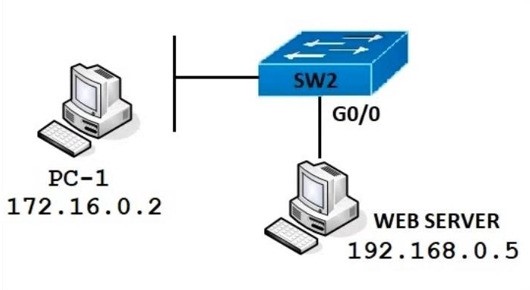
A. permit host 172.16.0.2 host 192.168.0.5 eq 8080
B. permit host 192.168.0.5 host 172.16.0.2 eq 8080
C. permit host 192.168.0.5 eq 8080 host 172.16.0.2
D. permit host 192.168.0.5 it 8080 host 172.16.0.2
QUESTION 190
Refer to the exhibit. After configurating an IPsec VPN, an engineer enters the show command to verify the ISAKMP SA status. What does the status show?
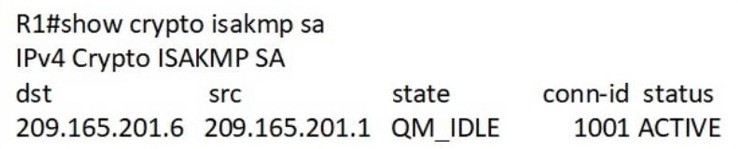
A. ISAKMP SA is authenticated and can be used for Quick Mode.
B. Peers have exchanged keys, but ISAKMP SA remains unauthenticated.
C. VPN peers agreed on parameters for the ISAKMP SA
D. ISAKMP SA has been created, but it has not continued to form.
QUESTION 191
Which antenna type should be used for a site-to-site wireless connection?
A. Omnidirectional
B. dipole
C. patch
D. Yagi
QUESTION 192
Which controller is capable of acting as a STUN server during the onboarding process of Edge devices?
A. vBond
B. vSmart
C. vManage
D. PNP server
QUESTION 193
Refer to the exhibit. Which configuration allows Customer2 hosts to access the FTP server of Customer1 that has the IP address of 192.168.1.200?

A. ip route vrf Customerl 172.16.1.0 255.255.255.0 172.16.1.1 global
ip route vrf Customer 192.168.1.200 255.255.255.255 192.168.1.1 global
ip route 192.168.1.0 255.255.255.0 VlanlO
ip route 172.16.1.0 255.255.255.0 Vlan20
B. ip route vrf Customerl 172.16.1.0 255.255.255.0 172.16.1.1 Customer2
ip route vrf Customer 192.168.1.200 255.255.255.255 192.168.1.1 Customerl
C. ip route vrf Customerl 172.16.1.0 255.255.255.0 172.16.1.1 Customerl
ip route vrf Customer 192.168.1.200 255.255.255.255 192.168.1.1 Customer2
D. ip route vrf Customerl 172.16.1.1 255.255.255.255 172.16.1.1 global
ip route vrf Customer 192.168.1.200 255.255.255.0 192.168.1.1 global
ip route 192.168.1.0 255.255.255.0 VlanlO
ip route 172.16.1.0 255.255.255.0 Vlan20
QUESTION 194
An engineer must configure the strongest password authentication to locally authenticate on a router. Which configuration must be used?
A. username netadmin secret 5 $1$b1JUSkZbBS1Pyh4OzwXyZ1kSZ2
B. username netadmin secret $15b1JuSk404850110QzwXyZ1k SZ2
C. line Console 0 password $15b1Ju$
D. username netadmin secret 9 $9$vFpMfBelbRVV8SseX/bDAxtuV
QUESTION 195
What does the Cisco DNA Center use to enable the delivery of applications through a network and to yield analytics for innovation?
A. process adapters
B. Command Runner
C. intent-based APIs
D. domain adapters
QUESTION 196
Which entity is responsible for maintaining Layer 2 isolation between segments In a VXLAN environment?
A. switch fabric
B. VTEP
C. VNID
D. host switch
QUESTION 197
Running the script causes the output in the exhibit. Which change to the first line of the script resolves the error?
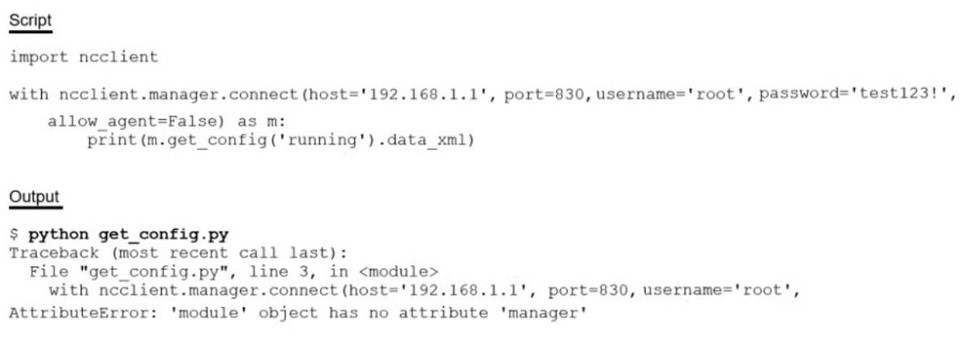
A. from ncclient import manager
B. import manager
C. from ncclient import*
D. ncclient manager import
QUESTION 198
What is the wireless received signal strength indicator?
A. The value given to the strength of the wireless signal received compared to the noise level
B. The value of how strong the wireless signal Is leaving the antenna using transmit power, cable loss, and antenna gain
C. The value of how much wireless signal is lost over a defined amount of distance
D. The value of how strong a tireless signal is receded, measured in dBm
QUESTION 199
Which two operational models enable an AP to scan one or more wireless channels for rouge access points and at the same time provide wireless services to clients?
A. Rouge detector
B. Sniffer
C. FlexConnect
D. Local
E. Monitor
QUESTION 200
Refer to the exhibit. An engineer attempts to configure a trunk between switch sw1 and switch SW2 using DTP, but the trunk does not form. Which command should the engineer apply to switch SW2 to resolve this issue?

A. switchport mode dynamic desirable
B. switchport nonegotiate
C. no switchport
D. switchport mode access
QUESTION 201
What is a characteristic of MACsec?
A. 802.1AE provides encryption and authentication services
B. 802.1AE is bult between the host and switch using the MKA protocol, which negotiates encryption keys based on the master session key from a successful 802 1X session
C. 802.1AE is bult between the host and switch using the MKA protocol using keys generated via the Diffie- Hellman algorithm (anonymous encryption mode)
D. 802.1AE is negotiated using Cisco AnyConnect NAM and the SAP protocol
QUESTION 202
What is used to perform QoS packet classification?
A. the Options field in the Layer 3 header
B. the Type field in the Layer 2 frame
C. the Flags field in the Layer 3 header
D. the TOS field in the Layer 3 header
QUESTION 203
Which OSPF network types are compatible and allow communication through the two peering devices?
A. point-to-multipoint to nonbroadcast
B. broadcast to nonbroadcast
C. point-to-multipoint to broadcast
D. broadcast to point-to-point
QUESTION 204
What is a characteristic of a virtual machine?
A. It must be aware of other virtual machines, in order to allocate physical resources for them
B. It is deployable without a hypervisor to host it
C. It must run the same operating system as its host
D. It relies on hypervisors to allocate computing resources for it
QUESTION 205
What is the function of a VTEP in VXLAN?
A. provide the routing underlay and overlay for VXLAN headers
B. dynamically discover the location of end hosts in a VXLAN fabric
C. encapsulate and de-encapsulate traffic into and out of the VXLAN fabric
D. statically point to end host locations of the VXLAN fabric
QUESTION 206
While configuring an IOS router for HSRP with a virtual IP of 10.1.1.1. an engineer sees this log message.
Which configuration change must the engineer make?
Jan 1 12:12:12.111 : %HSRP-4-DIFFVIP1: GigabitEthernet0/0 Grp 1 active routers virtual IP address 10.1.1.1 is different to the locally configured address 10.1.1.25
A. Change the HSRP group configuration on the remote router to 1.
B. Change the HSRP group configuration on the local router to 1.
C. Change the HSRP virtual address on the remote router to 10.1.1.1
D. Change the HSRP virtual address on the local router to 10.1.1.1
QUESTION 207
A network is being migrated from IPv4 to IPv6 using a dual-stack approach. Network management is already 100% IPv6 enabled.
In a dual-stack network with two dual-stack NetFlow collectors, how many flow exporters are needed per network device in the flexible NetFlow configuration?
A. 1
B. 2
C. 4
D. 8
QUESTION 208
In an SD-Access solution what is the role of a fabric edge node?
A. to connect external Layer 3- network to the SD-Access fabric
B. to connect wired endpoint to the SD-Access fabric
C. to advertise fabric IP address space to external network
D. to connect the fusion router to the SD-Access fabric
QUESTION 209
Which cisco DNA center application is responsible for group-based access control permissions?
A. Design
B. Provision
C. Assurance
D. Policy
QUESTION 210
Which two network problems indicate a need to implement QoS in a campus network? (Choose two)
A. port flapping
B. excess jitter
C. misrouted network packets
D. duplicate IP addresses
E. bandwidth-related packet loss
QUESTION 211
Refer to the exhibit. An engineer configures CoPP and enters the show command to verify the implementation. What is the result of the configuration?
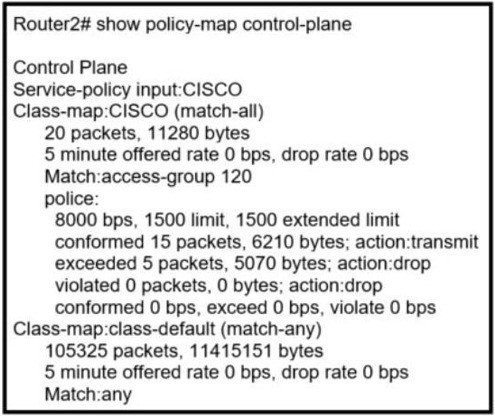
A. All traffic will be policed based on access-list 120.
B. If traffic exceeds the specified rate, it will be transmitted and remarked.
C. Class-default traffic will be dropped.
D. ICMP will be denied based on this configuration.
QUESTION 212
A client device roams between access points located on different floors in an atrium. The access points joined to the same controller and configuration in local mode. The access points are in different IP addresses, but the client VLAN in the group same. What type of roam occurs?
A. inter-controller
B. inter-subnet
C. intra-VLAN
D. intra-controller
QUESTION 213
What is a benefit of a virtual machine when compared with a physical server?
A. Multiple virtual servers can be deployed on the same physical server without having to buy additional hardware.
B. Virtual machines increase server processing performance.
C. The CPU and RAM resources on a virtual machine cannot be affected by other virtual machines.
D. Deploying a virtual machine is technically less complex than deploying a physical server.
QUESTION 214
In a Cisco SD-Access solution, what is the role of the Identity Services Engine?
A. It is leveraged for dynamic endpoint to group mapping and policy definition.
B. It provides GUI management and abstraction via apps that share context.
C. it is used to analyze endpoint to app flows and monitor fabric status.
D. It manages the LISP EID database.
QUESTION 215
Refer to the exhibit. Which set of commands on router R1 Allow deterministic translation of private hosts PC1, PC2, and PC3 to addresses in the public space?
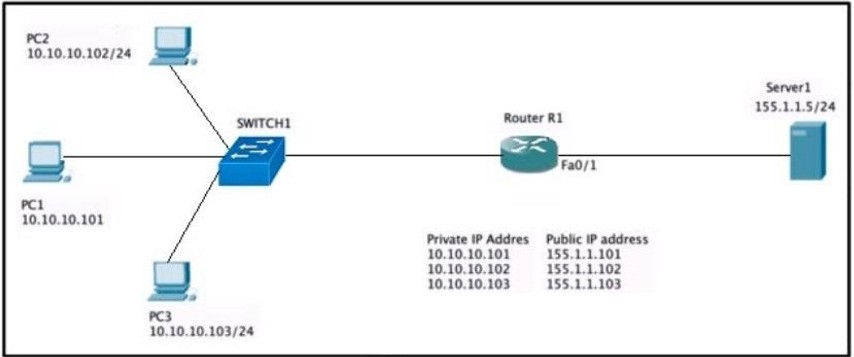
A.
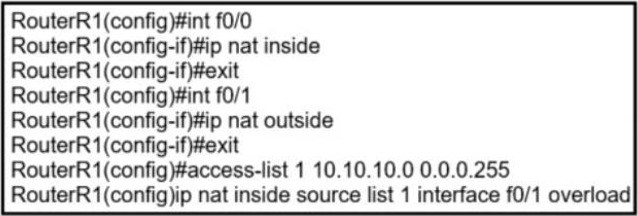
B.

C.
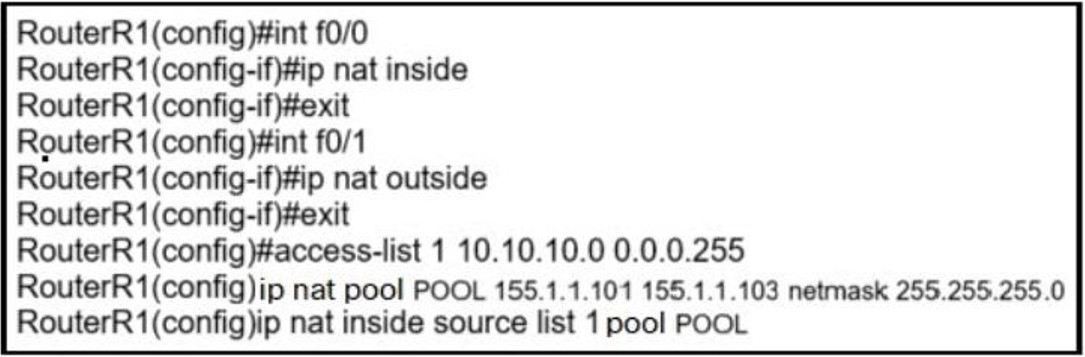
D.

QUESTION 216
Refer to the exhibit. Which command when applied to the Atlanta router reduces type 3 LSA flooding into the backbone area and summarizes the inter-area routes on the Dallas router?
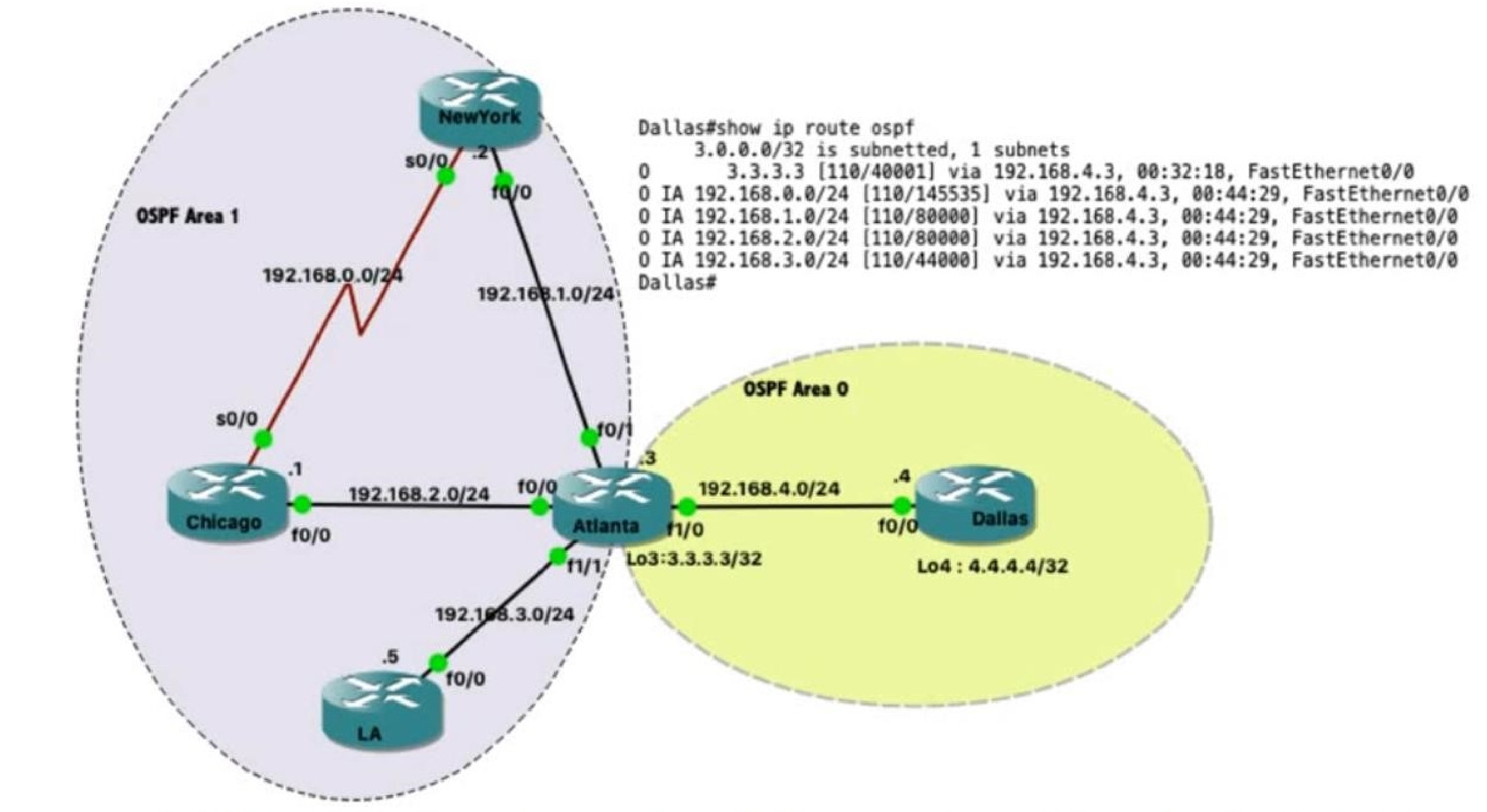 A. Atlanta(config-route)#area 0 range 192.168.0.0 255.255.248.0
A. Atlanta(config-route)#area 0 range 192.168.0.0 255.255.248.0
B. Atlanta(config-route)#area 0 range 192.168.0.0 255.255.252.0
C. Atlanta(config-route)#area 1 range 192.168.0.0 255.255.252.0
D. Atlanta(config-route)#area 1 range 192.168.0.0 255.255.248.0
QUESTION 217
Refer to me exhibit. What is the cause of the log messages?
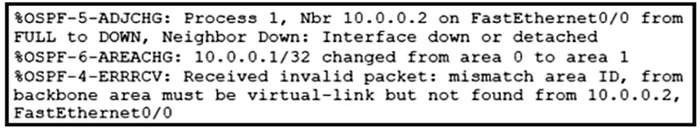
A. hello packet mismatch
B. OSPF area change
C. MTU mismatch
D. IP address mismatch
QUESTION 218
A network engineer is configuring Flexible NetFlow and enters these commands:
Sampler Netflow1 mode random one-out-of 100 interface fastethernet 1/0 flow-sampler netflow1
Which are two results of implementing this feature instead of traditional NetFlow? (Choose two)
A. Only the flows of top 100 talkers are exported
B. CPU and memory utilization are reduced
C. The data export flow is more secure
D. The accuracy of the data to be analyzed is improved
E. The number of packets to be analyzed are reduced
QUESTION 219
An engineer configures GigabitEthernet 0/1 for VRRP group 115. The router must assume the primary role when it has the highest priority in the group. Which command set is required to complete this task?
interface GigabitEthernet0/1 ip address 10.10.10.2 255.255.255.0 vrrp 115 ip 10.10.10.1 vrrp 115 authentication 409692526
A. Router(config-if)#vrrp 115 priority 100
B. Router(config-if)#standby 115 priority 100Router(config-if)#standby 115 preempt
C. Router(config-if)#vrrp 115 track 1 decrement 10Router(config-if)#vrrp 115 preempt
D. Router(config-if)#vrrp 115 track 1 decrement 100Router(config-if)#vrrp 115 preempt
QUESTION 220
What is a characteristic of a next-generation firewall?
A. only required at the network perimeter
B. required in each layer of the network
C. filters traffic using Layer 3 and Layer 4 information only
D. provides intrusion prevention
QUESTION 221
Which three methods does Cisco DNA Centre use to discover devices? (Choose three)
A. CDP
B. SNMP
C. LLDP
D. ping
E. NETCONF
F. a specified range of IP addresses
QUESTION 222
Which two mechanisms are available to secure NTP? (Choose two.)
A. IPsec
B. IP prefix list-based
C. encrypted authentication
D. TACACS-based authentication
E. IP access list-based
QUESTION 223
What is the function of the fabric control plane node In a Cisco SD-Access deployment?
A. It is responsible for policy application and network segmentation in the fabric.
B. It performs traffic encapsulation and security profiles enforcement in the fabric.
C. It holds a comprehensive database that tracks endpoints and networks in the fabric.
D. It provides Integration with legacy nonfabric-enabled environments.
QUESTION 224
Refer to the exhibit. Which action completes the configuration to achieve a dynamic continuous mapped NAT for all users?
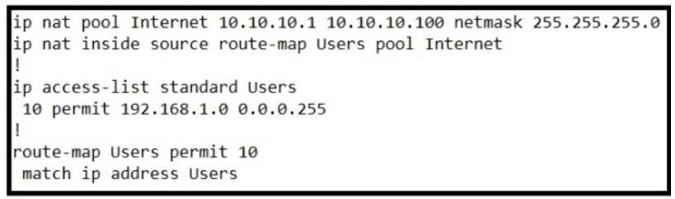
A. Configure a match-host type NAT pool
B. Reconfigure the pool to use the 192.168 1 0 address range
C. Increase the NAT pool size to support 254 usable addresses
D. Configure a one-to-one type NAT pool
QUESTION 225
How is MSDP used to interconnect multiple PIM-SM domains?
A. MSDP depends on BGP or multiprotocol BGP for interdomain operation.
B. MSDP SA request messages are used to request a list of active sources for a specific group
C. MSDP allows a rendezvous point to dynamically discover active sources outside of its domain
D. MSDP messages are used to advertise active sources in a domain
QUESTION 226
What is the difference between a RIB and a FIB?
A. The FIB is populated based on RIB content.
B. The RIB maintains a minor image of the FIB.
C. The RIB is used to make IP source prefix-based switching decisions.
D. The FIB is where all IP routing information is stored.
QUESTION 227
What is required for a virtual machine to run?
A. a Type 1 hypervisor and a host operating system
B. a hypervisor and physical server hardware
C. only a Type 1 hypervisor
D. only a Type 2 hypervisor
QUESTION 228
How does EIGRP differ from OSPF?
A. EIGRP is more prone to routing loops than OSPF
B. EIGRP has a full map of the topology, and OSPF only knows directly connected neighbors
C. EIGRP supports equal or unequal path cost, and OSPF supports only equal path cost.
D. EIGRP uses more CPU and memory than OSPF
QUESTION 229
Which device makes the decision for a wireless client to roam?
A. wireless client
B. wireless LAN controller
C. access point
D. WCS location server
QUESTION 230
A network administrator has designed a network with two multilayer switches on the distribution layer, which act as default gateways for the end hosts. Which two technologies allow every end host in a VLAN to use both gateways? (Choose two)
A. GLBP
B. HSRP
C. MHSRP
D. VSS
E. VRRP
QUESTION 231
Refer to the exhibit. Which code results in the working python script displaying a list of network devices from the Cisco DNA center?
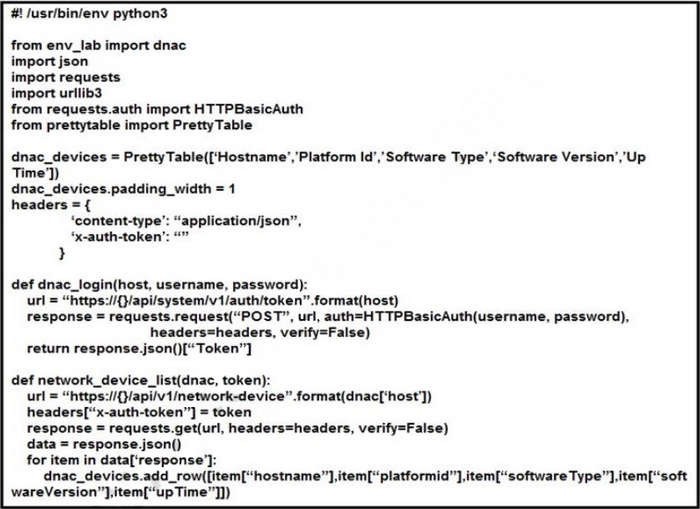

A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 232
Refer to the exhibit.Which type of antenna does the radiation pattern represent?
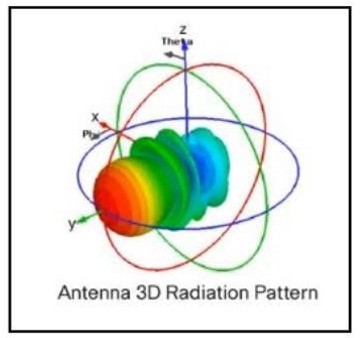
A. Yagi
B. multidirectional
C. directional patch
D. omnidirectional
QUESTION 233
Which technology uses network traffic telemetry, contextual information, and file reputation to provide insight into cyber threats?
A. threat defense
B. security services
C. security intelligence
D. segmentation
QUESTION 234
Refer to the exhibit.
SwitchC connects HR and Sales to the Core switch However, business needs require that no traffic from the Finance VLAN traverse this switch. Which command meets this requirement?


A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: D
QUESTION 235
Refer to the exhibit. Which configuration must be applied to R1 to enable R1 to reach the server at 172.16.0.1?
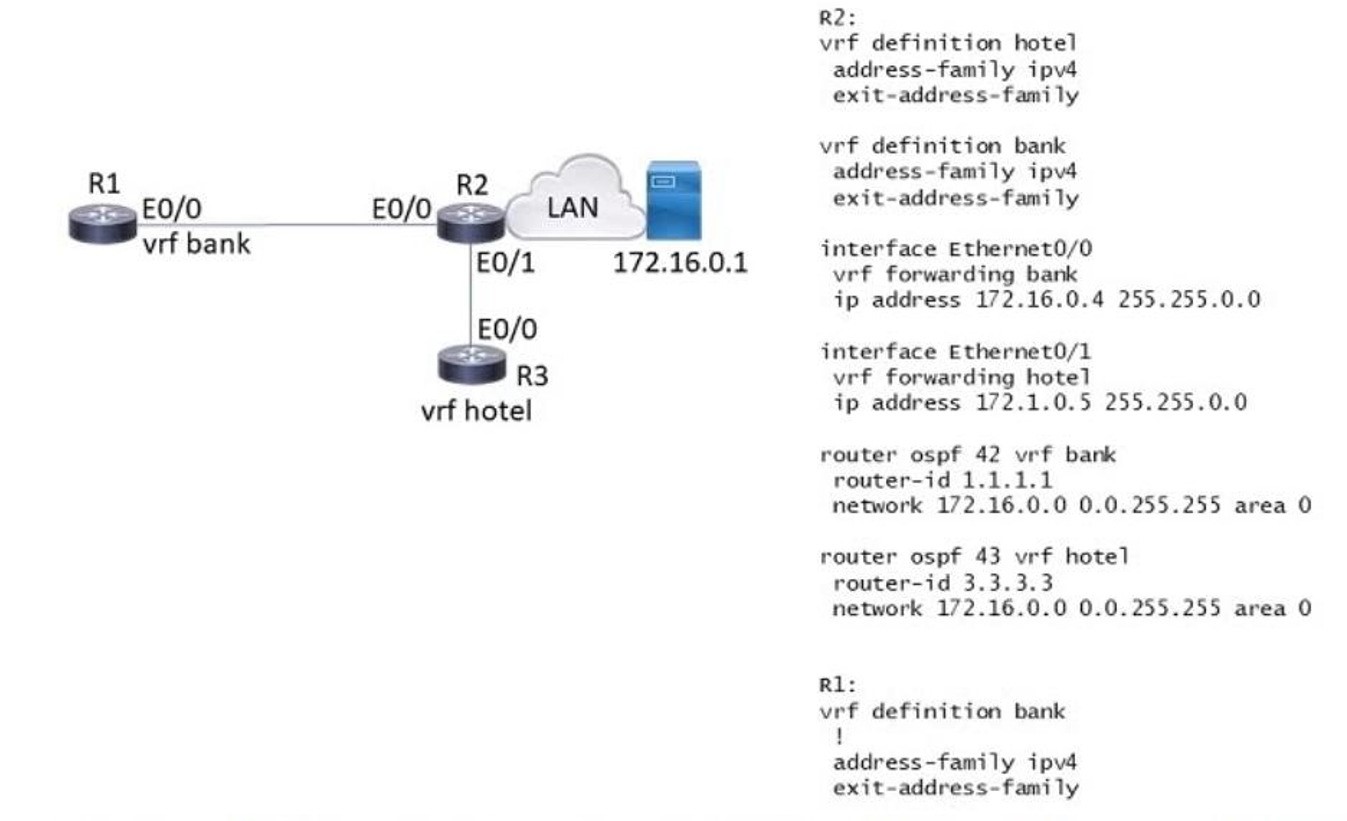
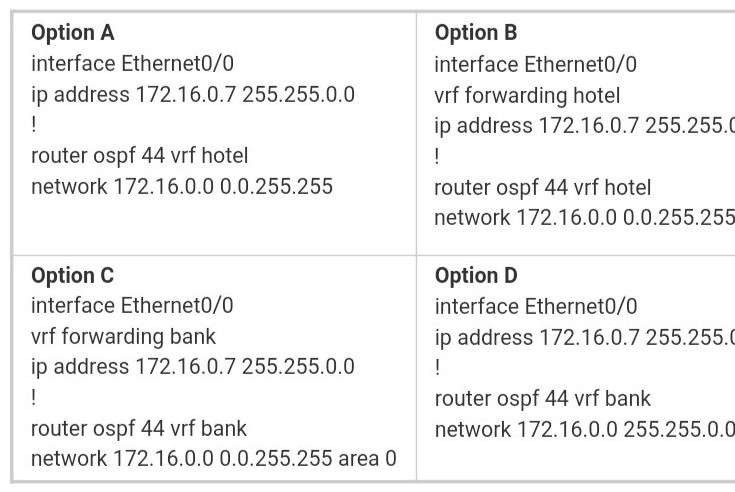
A. Option A
B. Option B
C. Option C
D. Option D
QUESTION 236
Which DNS lookup does an access point perform when attempting CAPWAP discovery?
A. CISCO-CONTROLLER.local
B. CAPWAP-CONTROLLER.local
C. CISCO-CAPWAP-CONTROLLER.local
D. CISCO-DNA-CONTROLLER.local
QUESTION 237
Under which network conditions is an outbound QoS policy that is applied on a router WAN interface most beneficial?
A. under all network conditions
B. under network convergence conditions
C. under traffic classification and marking conditions
D. under interface saturation conditions
QUESTION 238
How does the EIGRP metric differ from the OSPF metric?
A. The EIGRP metric is calculated based on bandwidth only. The OSPF metric is calculated on delay only.
B. The EIGRP metric is calculated based on delay only. The OSPF metric is calculated on bandwidth and delay.
C. The EIGRP metric Is calculated based on bandwidth and delay. The OSPF metric is calculated on bandwidth only.
D. The EIGRP metric Is calculated based on hop count and bandwidth. The OSPF metric is calculated on bandwidth and delay.
QUESTION 239
What is a characteristic of vManage?
A. It leverages the overlay management protocol to interface with WAN Edge devices.
B. It supports protocols such as SPF to integrate with legacy network devices.
C. It requires a public IP address to allow WAN Edge devices to discover fabric components.
D. It uses NETCONF to configure Smart devices to build the overlay network data plane.
QUESTION 240
Which new enhancement was implemented in Wi-Fi 6?
A. Wi-Fi Protected Access 3
B. 4096 Quadrature Amplitude Modulation Mode
C. Channel bonding
D. Uplink and Downlink Orthogonal Frequency Division Multiple Access
QUESTION 241
Refer to the exhibit. What step resolves the authentication issue?

A. use basic authentication
B. change the port to 12446
C. target 192.168.100.82 in the URI
D. restart the vsmart host
QUESTION 242
An engineer must protect their company against ransom ware attacks. Which solution allows the engineer to block the execution stage and prevent file encryption?
A. Use Cisco AMP deployment with the Malicious Activity Protection engine enabled.
B. Use Cisco AMP deployment with the Exploit Prevention engine enabled
C. Use Cisco Firepower and block traffic to TOR networks
D. Use Cisco Firepower with Intrusion Policy and snort rules blocking SMB exploitation
QUESTION 243
Refer to the exhibit. Which action resolves the EtherChannel issue between SW2 and SW3?

A. Configure switchport mode trunk on SW2.
B. Configure switchport nonegotiate on SW3
C. Configure channel-group 1 mode desirable on both interfaces.
D. Configure channel-group 5 mode active on both interfaces.
QUESTION 244
Which two GRE features are configured to prevent fragmentation? (Choose two.)
A. TCP window size
B. IP MTU
C. TCP MSS
D. DF bit clear
E. MTU ignore
QUESTION 245
Which technology does VXLAN use to provide segmentation for Layer 2 and Layer 3 traffic?
A. bridge domain
B. VLAN
C. VRF
D. VNI
QUESTION 246
What are two benefits of virtual switching when compared to hardware switching? (Choose two.)
A. increased MTU size
B. hardware independence
C. VM-level isolation
D. increased flexibility
E. extended 802.1Q VLAN range
QUESTION 247
What do Cisco DNA southbound APIs provide?
A. interface between the controller and the consumer
B. RESTful API interface for orchestrator communication
C. interface between the controller and the network devices D. NETCONF API interface for orchestrator communication
QUESTION 248
Which feature does Cisco TrustSec use to provide scalable, secure communication throughout a network?
A. security group tag ACL assigned to each port on a switch
B. security group tag number assigned to each user on a switch
C. security group tag number assigned to each port on a network
D. security group tag ACL assigned to each router on a network
QUESTION 249
Refer to the Exhibit. An engineer is installing a new pair of routers in a redundant configuration. When checking on the standby status of each router the engineer notices that the routers are not functioning as expected. Which action will resolve the configuration error?
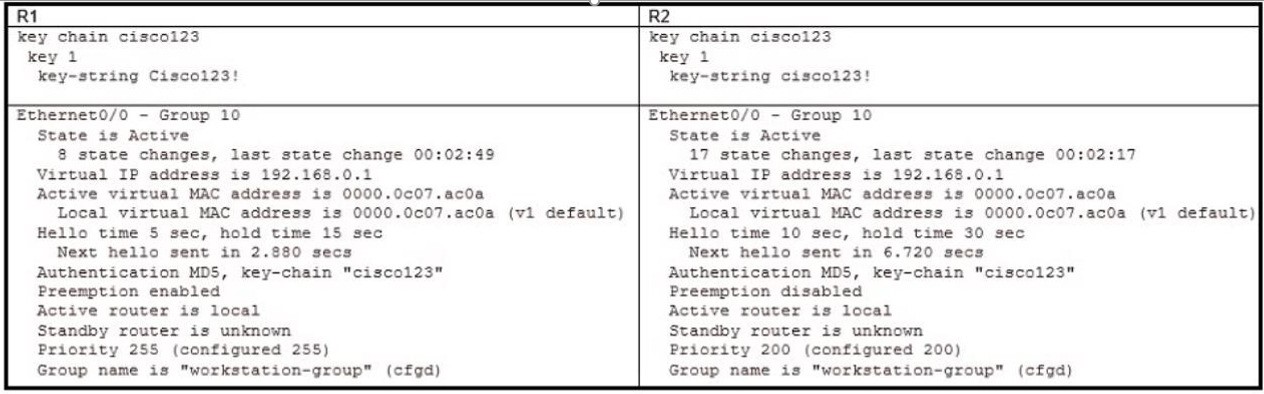
A. configure matching hold and delay timers
B. configure matching key-strings
C. configure matching priority values
D. configure unique virtual IP addresses
QUESTION 250
Refer to the exhibit. The EtherChannel between SW2 and SW3 is not operational which action resolves this issue?
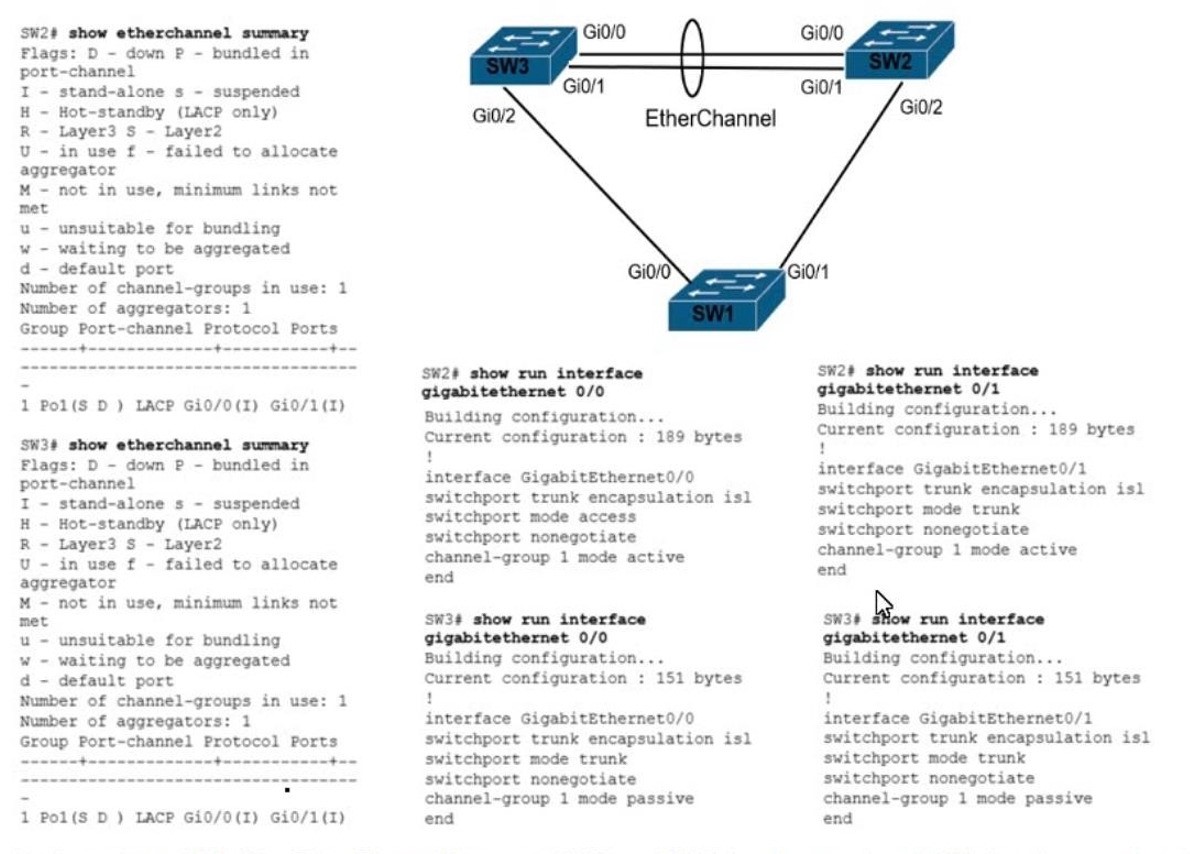
A. Configure the channel-group mode on SW2 Gi0/0 and Gi0/1 to on.
B. Configure the channel-group mode on SW3 Gi0/0 and Gi0/1 to active
C. Configure the mode on SW2 Gi0/0 to trunk
D. Configure the mode on SW2 Gi0/1 to access
QUESTION 251
Which entity is a Type 1 hypervisor?
A. Oracle VM VirtualBox
B. VMware server
C. Citrix XenServer
D. Microsoft Virtual PC
QUESTION 252
In a three-tier hierarchical campus network design, which action is a design best-practice for the core layer?
A. provide QoS prioritization services such as marking, queueing, and classification for critical network traffic
B. provide redundant Layer 3 point-to-point links between the core devices for more predictable and faster convergence
C. provide advanced network security features such as 802. IX, DHCP snooping, VACLs, and port security
D. provide redundant aggregation for access layer devices and first-hop redundancy protocols such as VRRP
QUESTION 253
An engineer has deployed a single Cisco 5520 WLC with a management IP address of 172.16.50.5/24. The engineer must register 50 new Cisco AIR-CAP2802I-E-K9 access points to the WLC using DHCP option 43. The access points are connected to a switch in VLAN 100 that uses the 172.16.100.0/24 subnet. The engineer has configured the DHCP scope on the switch as follows:

The access points are failing to join the wireless LAN controller. Which action resolves the issue?
A. configure option 43 Hex F104.AC10.3205
B. configure option 43 Hex F104.CA10.3205
C. configure dns-server 172.16.50.5
D. configure dns-server 172.16.100.1
QUESTION 254
Which function does a fabric edge node perform in an SD-Access deployment?
A. Connects endpoints to the fabric and forwards their traffic.
B. Encapsulates end-user data traffic into LISP.
C. Connects the SD-Access fabric to another fabric or external Layer 3 networks.
D. Provides reachability between border nodes in the fabric underlay.
QUESTION 255
What is a VPN in a Cisco SD-WAN deployment?
A. common exchange point between two different services
B. attribute to identify a set of services offered in specific places in the SD-WAN fabric
C. virtualized environment that provides traffic isolation and segmentation in the SD-WAN fabric
D. virtual channel used to carry control plane information
QUESTION 256
Refer to the exhibit.
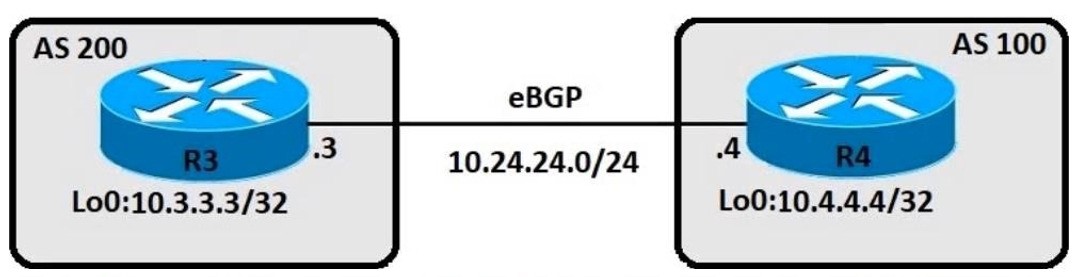
An engineer must establish eBGP peering between router R3 and router R4. Both routers should use their loopback interfaces as the BGP router ID. Which configuration set accomplishes this task?
A. R3(config)#router bgp 200
R3(config-router)#neighbor 10.24.24.4 remote-as 100
R3(config-router)#bgp router-id 10.3.3.3
R4(config)#router bgp 100
R4(config-router)#neighbor 10.24.24.3 remote-as 200
R4(config-router)#bgp router-id 10.4.4.4
B. R3(config)#router bgp 200
R3(config-router)#neighbor 10.4.4.4 remote-as 100
R3(config-router)#neighbor 10.4.4.4 update-source loopback0
R4(config)#router bgp 100
R4(config-router)#neighbor 10.3.3.3 remote-as 200
R4(config-router)#neighbor 10.3.3.3 update-source loopback0
C. R3(config)#router bgp 200
R3(config-router)#neighbor 10.24.24.4 remote-as 100
R3(config-router)#neighbor 10.24.24.4 update-source loopback0
R4(config)#router bgp 100
R4(config-router)#neighbor 10.24.24.3 remote-as 200
R4(config-router)#neighbor 10.24.24.3 update-source loopback0
QUESTION 257
Refer to the exhibit. The connection between SW1 and SW2 is not operational. Which two actions resolve the issue? (Choose two.)
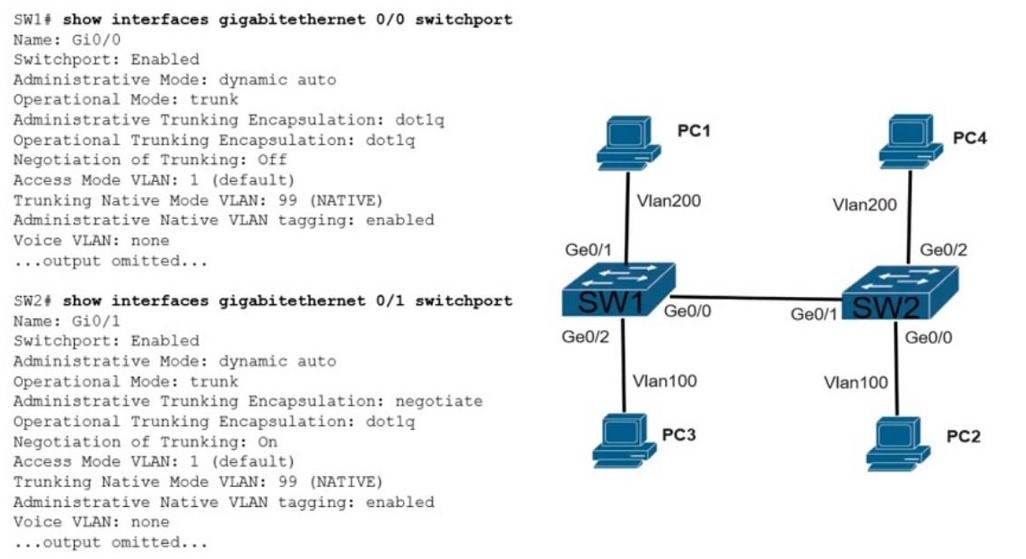
A. configure switchport mode access on SW2
B. configure switchport nonegotiate on SW2
C. configure switchport mode trunk on SW2
D. configure switchport nonegotiate on SW1
E. configure switchport mode dynamic desirable on SW2
QUESTION 258
Which access point mode allows a supported AP to function like a WLAN client would, associating and identifying client connectivity issues?
A. client mode
B. SE-connect mode
C. sensor mode
D. sniffer mode
QUESTION 259
Refer to the exhibit. What is the result when a switch that is running PVST+ is added to this network?
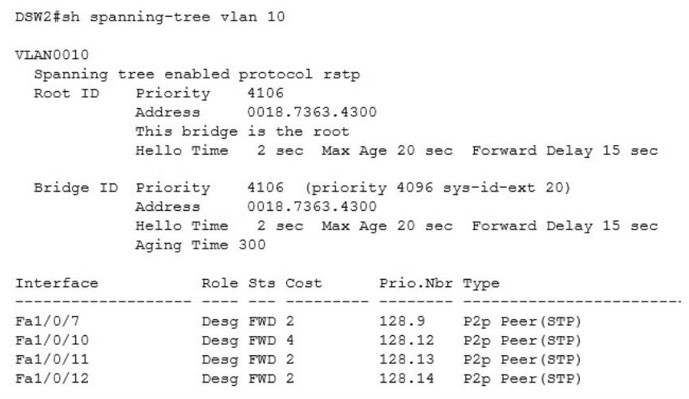
A. DSW2 operates in Rapid PVST+ and the new switch operates in PVST+
B. Both switches operate in the PVST+ mode
C. Spanning tree is disabled automatically on the network
D. Both switches operate in the Rapid PVST+ mode.
QUESTION 260
An engineer must create an EEM applet that sends a syslog message in the event a change happens in the network due to trouble with an OSPF process. Which action should the engineer use?
![]()
A. action 1 syslog msg “OSPF ROUTING ERROR”
B. action 1 syslog send “OSPF ROUTING ERROR”
C. action 1 syslog pattern “OSPF ROUTING ERROR”
D. action 1syslog write “OSPF ROUTING ERROR”
QUESTION 261
In cisco SD_WAN, which protocol is used to measure link quality?
A. OMP
B. BFD
C. RSVP
D. IPsec
QUESTION 262
Refer to the exhibit. Router 1 is currently operating as the HSRP primary with a priority of 110 Router1 fails and Router2 take over the forwarding role. Which command on router1 causes it to take over the forwarding role when it return to service?
A. standby 10 priority
B. standby 10 timers
C. standby 10 track
D. standby 10 preempt
QUESTION 263
Which HTTP status code is the correct response for a request with an incorrect password applied to a REST API session?
A. HTTP Status Code: 200 B. HTTP Status Code: 302 C. HTTP Status Code: 401
D. HTTP Status Code: 504
QUESTION 264
What is the function of a fabric border node in a Cisco SD-Access environment?
A. To collect traffic flow information toward external networks
B. To connect the Cisco SD-Access fabric to another fabric or external Layer 3 networks
C. To attach and register clients to the fabric
D. To handle an ordered list of IP addresses and locations for endpoints in the fabric.
QUESTION 265
What is provided by the Stealthwatch component of the Cisco Cyber Threat Defense solution?
A. real-time threat management to stop DDoS attacks to the core and access networks
B. real-time awareness of users, devices and traffic on the network
C. malware control
D. dynamic threat control for web traffic
QUESTION 266
If the noise floor is -90 dBm and the wireless client is receiving a signal of -75 dBm, what is the SNR?
A. 15
B. 1.2
C. -165
D. .83
QUESTION 267
An engineer must update the local web authentication details on a Cisco 5520 WLC. The engineer has one active SSID configured for web authentication and plans to update the virtual interface with a nonroutable IP address. Which command must the engineer apply?
A. config interface address dynamic-interface virtual 192.0.2.1
B. config interface address virtual 1.1.1.1
C. config interface address virtual 192.0,2.1
D. config wan create wlan_idname
QUESTION 268
What are two differences between the RIB and the FIB? (Choose two.)
A. The FIB is derived from the data plane, and the RIB is derived from the FIB.
B. The RIB is a database of routing prefixes, and the FIB is the Information used to choose the egress interface for each packet.
C. FIB is a database of routing prefixes, and the RIB is the information used to choose the egress interface for each packet.
D. The FIB is derived from the control plane, and the RIB is derived from the FIB.
E. The RIB is derived from the control plane, and the FIB is derived from the RIB.
QUESTION 269
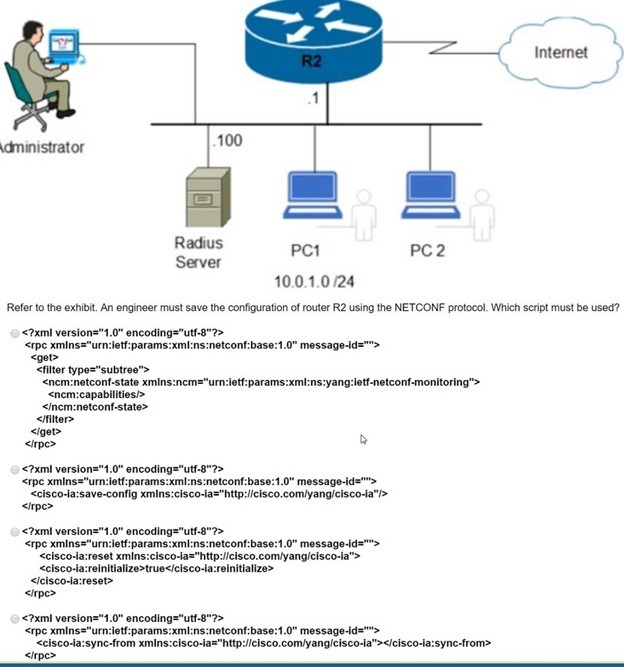
QUESTION 270
Refer to the exhibit. What ate two effects of this configuration? (Choose two.)
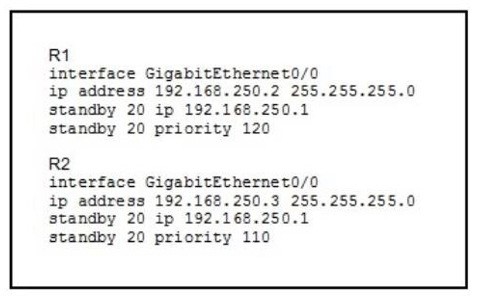
A. R1 becomes the active router.
B. If R1 goes down, R2 becomes active but reverts to standby when Rl comes back online.
C. R1 becomes the standby router.
D. If R2 goes down, R1 becomes active but reverts to standby when R2 comes back online.
E. If R1 goes down, R2 becomes active and remains the active device when R1 comes back online.
QUESTION 271

Refer to the exhibit. What is the value of the variable list after the code is run?
A. [1, 2, 1, 2, 1, 2]
B. [3, 6]
C. [1, 2]*3
D. [1, 21], [1, 2], [1, 2]
QUESTION 272
Which version of NetFlow does Cisco Threat Defense utilize to obtain visibility into the network?
A. NBAR2
B. IPFIX
C. 8
D. flexible
QUESTION 273
Refer to the exhibit. How should the programmer access the list of VLANs that were received via the API call?

A. VlanNames[‘Vlan1’]
B. list(VlanNames)
C. VlanNames[0]
D. VlanNames[‘response’]
QUESTION 274
Refer to the exhibit. Which action automatically enables privilege exec mode when logging in via SSH?

A. Configure a password under the line configuration.
B. Configure privilege level 15 under the line configuration.
C. Configure the enable secret to be the same as the secret for user “Cisco”
D. Configure user “cisco” with privilege level 15.
QUESTION 275
A client device roams between wireless LAN controllers that are mobility peers. Both controllers have dynamic interfaces on the same client VLAN. Which type of roam is described?
A. intra-VLAN
B. inter-controller
C. intra-controller
D. inter-subnet
QUESTION 276
What is an advantage of utilizing data models in a multivendor environment?
A. removing the distinction between configuration and runtime state data
B. improving communication security with binary-encoded protocols
C. facilitating a unified approach to configuration and management
D. lowering CPU load incurred to managed devices
QUESTION 277
Which authorization framework gives third-party applications limited access to HTTP services?
A. Basic Auth
B. Auth 2.0
C. GRE
D. IPsec
QUESTION 278
Why are stateless calls executed by REST API useful in cloud applications?
A. They use HTTPS to implement all calls.
B. They rely on data stored on the server for calls
C. They control URL decoding
D. They are easy to redeploy and to scale.
QUESTION 279
Which network devices secure API platforms?
A. content switches
B. next-generation intrusion detection systems
C. Layer 3 transit network devices
D. web application firewalls
QUESTION 280
Which LISP component is required for a LISP site to communicate with a non-LISP site?
A. Proxy ITR
B. Proxy ETR
C. CITR
D. ETR
QUESTION 281
Which feature is offered by the Cisco Advanced Malware Protection for Endpoints solution?
A. File Sandboxing
B. TrustSec
C. NetFlow
D. DNS Protection
QUESTION 282
Refer to the exhibit. A network engineer attempts to connect to the Router 1 console port. Which configuration is needed to allow Telnet connections?

A. Router1 (config)# line vty 0 15
Router1 (config-line)# transport output telnet
B. Router1 (config)# telnet client
C. Router1 (config)# access-list 100 permit tcp any any eq telnet
Router1 (config)# line console 0
Router1 (config-line)# access-class 100 out
D. Router1 (config)# line console 0
Router1(config-line)# transport output telnet
QUESTION 283
A customer has two Cisco WLCs that manage seperate APs throughout a building. Each WLC advertises the same SSID but terminates on different inderfaces. Users report that they drop their connections and change IP addresses when roaming. Which action resolves this issue?
A. Enable client load balancing.
B. Configure mobility groups.C. Configure high availability.
D. Enable fast roaming.
QUESTION 284
A script contains the statement “while loop !=999.” Which value terminates the loop?
A. A value greater than or equal to 999
B. A value equal to 999
C. A value not equal to 999.
D. A value less than or equal to 999.
QUESTION 285
How does Cisco Express Forwarding switching differ from process switching on Cisco devices?
A. Cisco Express Forwarding switching uses a proprietary protocol based on IS-IS for MAC address lookup and process switching uses the MAC address table.
B. Cisco Express Forwarding switching uses adjacency tables built by the CDP protocol and process switching uses the routing table
C. Cisco Express Forwarding switching uses dedicated hardware processors and process switching uses the main processor
D. Cisco Express Forwarding switching saves memory by storing adjacency tables in dedicated memory on the line cards, and process switching stores all tables in the main memory
QUESTION 286
Which element is unique to a type 2 hypervisor?
A. memory
B. host hardware
C. VM OS
D. host OS
QUESTION 287
Refer to the exhibit. What does the Python code accomplish?

A. It configures interface e1/32 to be in an admin down state B. It generates a status code of 403 because the type is incorrect. C. It configures interface e1/32 to be in an err-disable state,
D. It returns data in JSON-RPC format.
QUESTION 288
An engineer must configure AAA on a Cisco 9800 WLC for central web authentication. Which two commands are needed to accomplish this task? (Choose two.)
A. Device(config)# aaa server radius dynamic-author
B. Device(config-locsvr-da-radius)# client 10.10.10.12 server-key 0 SECRET
C. (Cisco Controller) > config wlan aaa-override enable <wlan-id>
D. (Cisco Controller) > config radius acct add 10.10.10.12 1812 SECRET
E. (Cisco Controller) > config wlan aaa-override disable <wlan-id>
QUESTION 289
Refer to the exhibit. An engineer must configure an ERSPAN tunnel that mirrors traffic from Linux1 on Switch 1 to Linux2 on Switch2. Which command must be added to the source configuration to enable the ERSPAN tunnel?
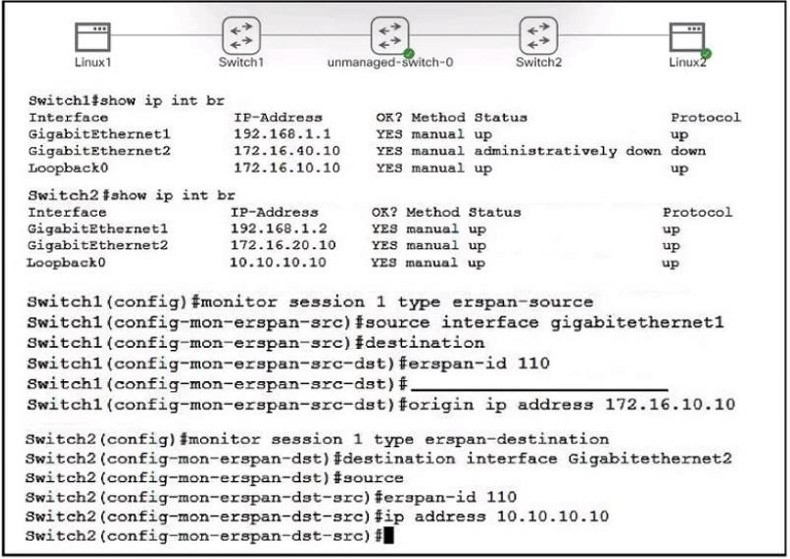
A. (config-mon-erspan-src-dst)#monitor session 1 activate
B. (config-mon-erspan-src-dst)# no shut
C. (config-mon-erspan-src-dst)# ip address 10.10.10.10
D. (config-mon-erspan-src-dst)# traffic bidirectional
QUESTION 290

Refer to the exhibit. What is displayed when the code is run?
A. The answer is 25
B. The answer is 70
C. The answer is 5
D. The answer is 100
QUESTION 291
Which feature provides data-plane security for Cisco SD-WAN networks?
A. IPsec
B. IPS
C. SSH
D. TLS/DTLS
QUESTION 292
What is a characteristic of Cisco DNA Northbound APls?
A. They utilize multivendor support APIs.
B. They enable automation of network infrastructure based on intent.
C. They simplify the management of network infrastructure devices.
D. They utilize RESTCONF.
Drag and Drop
QUESTION 1
Drag and drop the Qos mechanisms from the left to the correct descriptions on the right.
Select and Place:
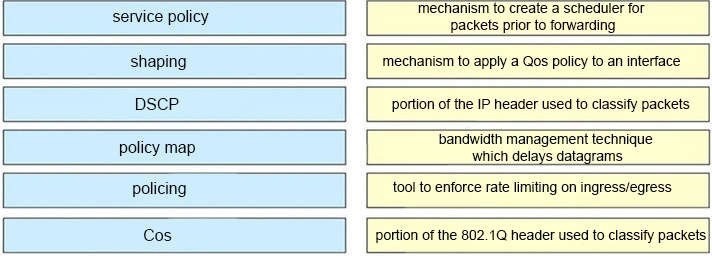
QUESTION 2
Drag and drop the descriptions of the VSS technology from the left to the right. Not all options are used.
Select and Place:
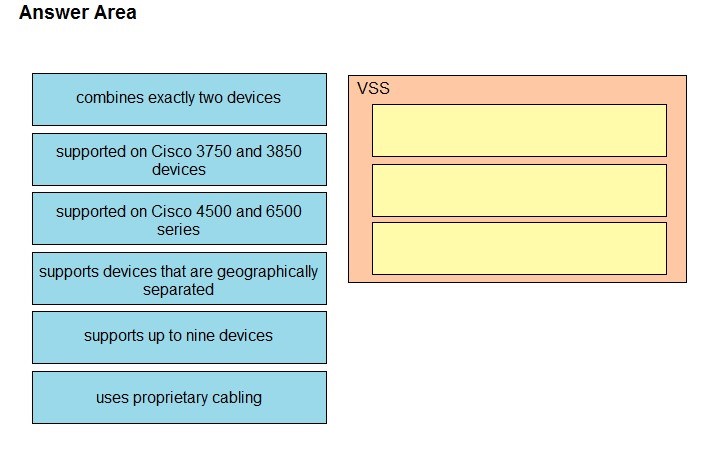
QUESTION 3
Drag and drop the characteristics from the left onto the routing protocols they describes on the right.
Select and Place:
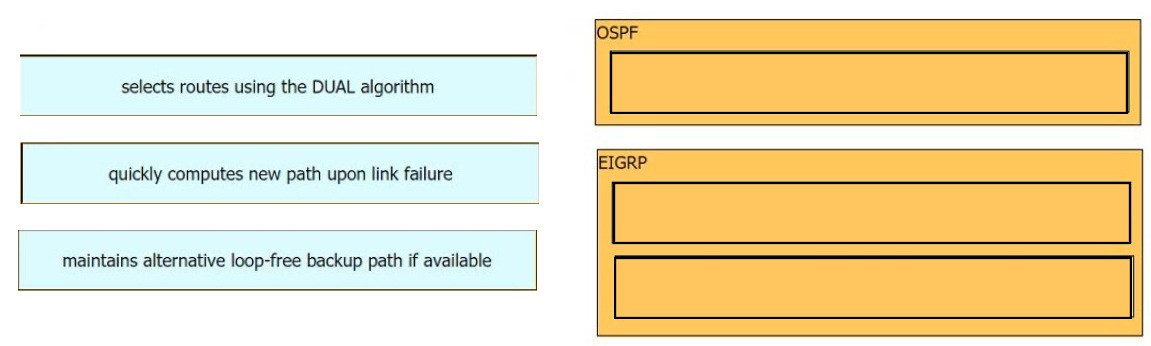
QUESTION 4
Refer to the exhibit. An engineer must deny HTTP traffic from host A to host B while allowing all other communication between the hosts, drag and drop the commands into the configuration to achieve these results. Some commands may be used more than once. Not all commands are used.
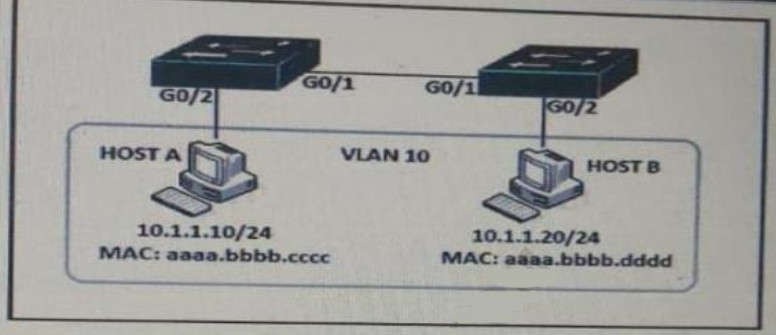
Select and Place:
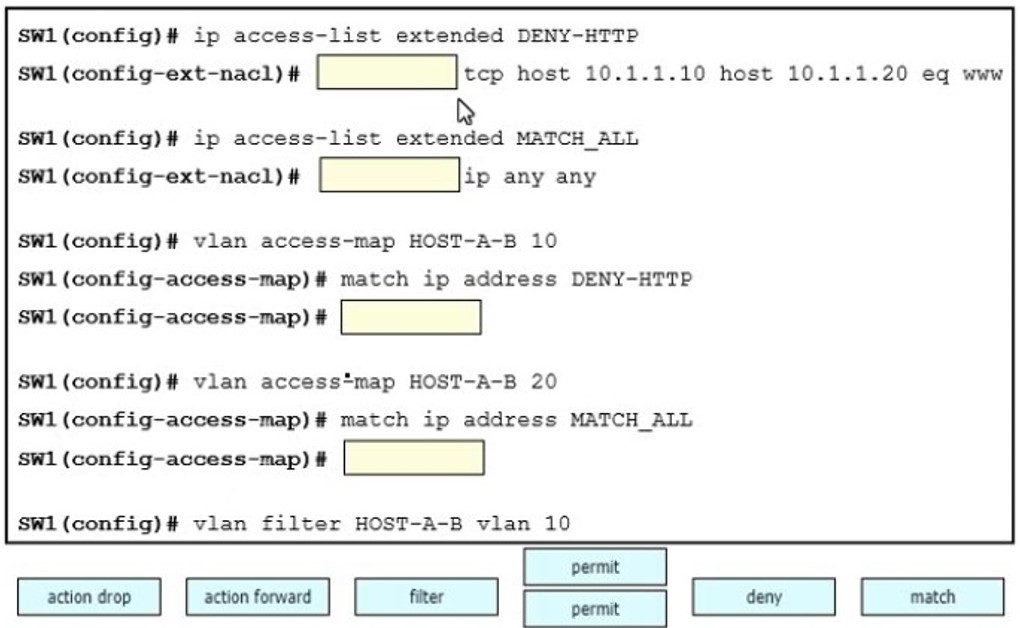
QUESTION 5
Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
Select and Place:
QUESTION 6
Drag and drop the LISP components from the left onto the function they perform on the right. Not all options are used.
Select and Place:
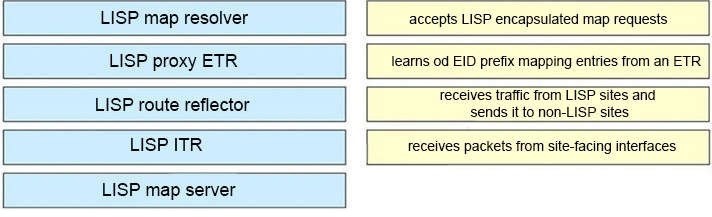
QUESTION 7
Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
Select and Place:
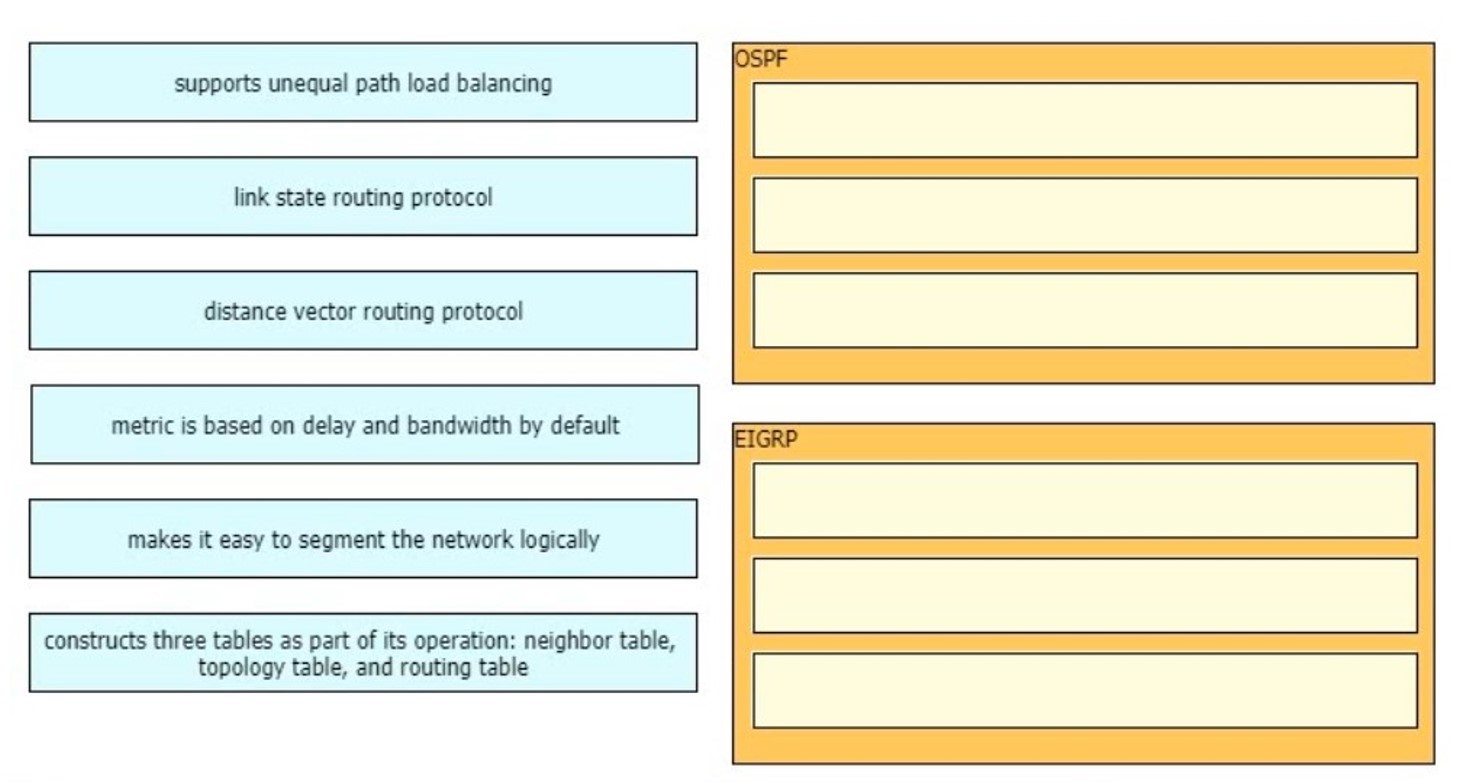
QUESTION 8
Drag and drop the characteristics from the left onto the orchestration tools they describe on the right.
Select and Place:
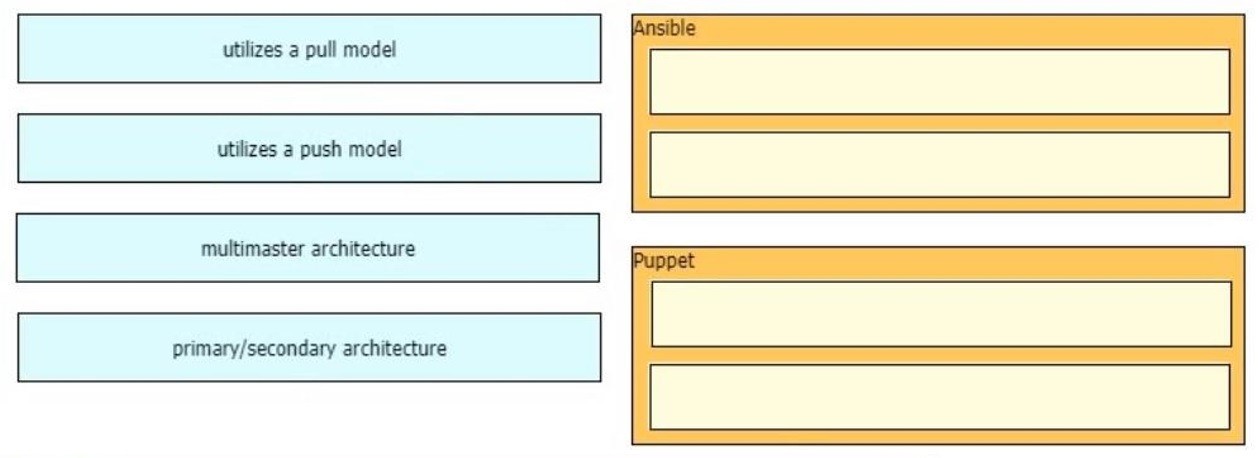
QUESTION 9
Drag and drop the characteristics from the left onto the correct infrastructure deployment types on the right.
Select and Place:
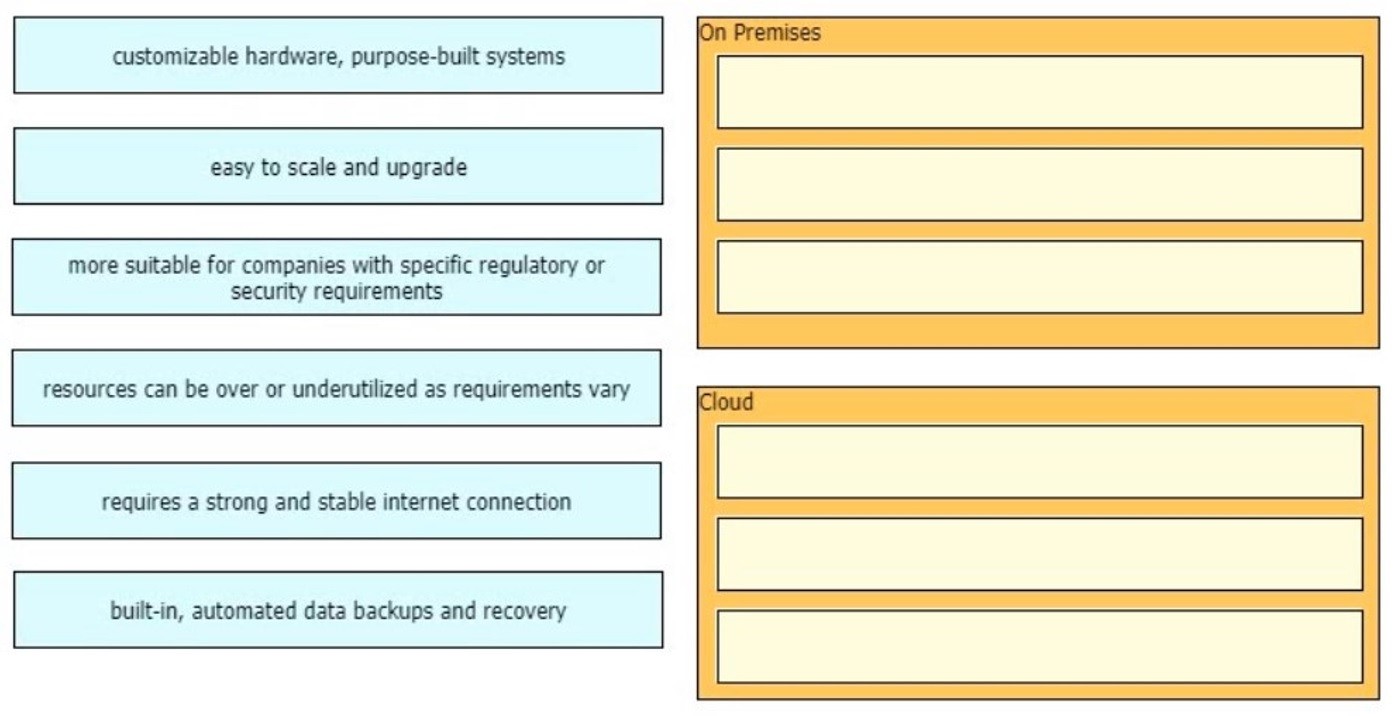
QUESTION 10
Drag and drop the REST API authentication method from the left to the description on the right.
Select and Place:

QUESTION 11
Drag and drop the descriptions from the left onto the routing protocol they describe on the right.
Select and Place:
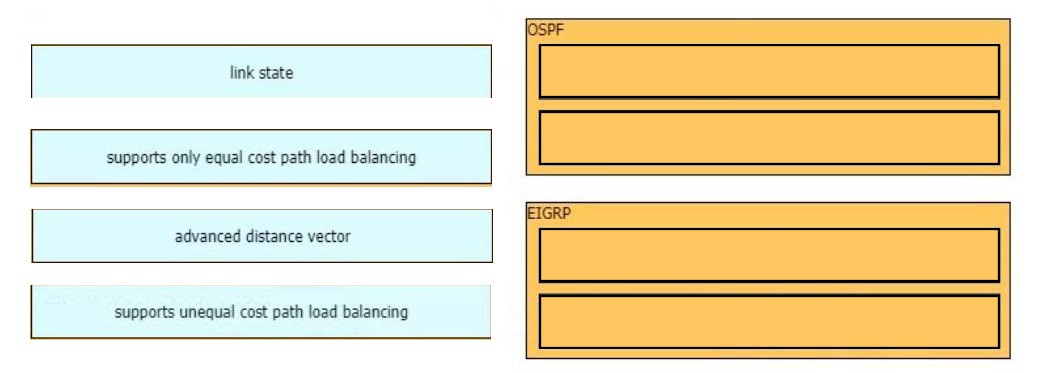
QUESTION 12
Drag and drop the characteristic from the left onto the orchestration tools that they describe on the right.
Select and Place:
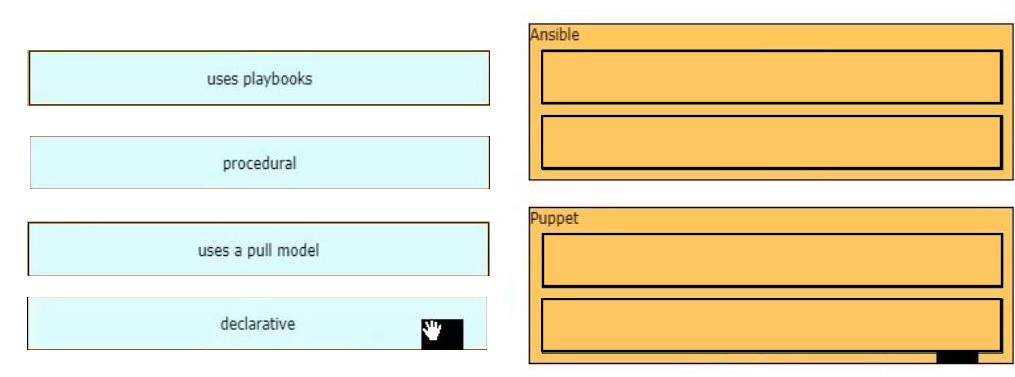
QUESTION 13
Drag and drop the wireless elements on the left to their definitions on the right.
Select and Place:
QUESTION 14
Drag and drop the solutions that comprise Cisco Cyber Threat Defense from the left onto the objectives they accomplish on the right.
Select and Place:
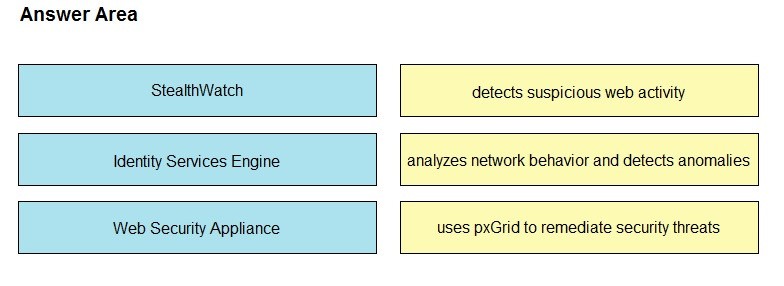
QUESTION 15
Drag and drop the virtual component from the left onto their descriptions on the right.
Select and Place:
QUESTION 16
Drag and drop characteristics of PIM dense mode from the left to the right Select and Place:

QUESTION 17
Drag and drop the descriptions from the left onto the correct QoS components on the right.
Select and Place:
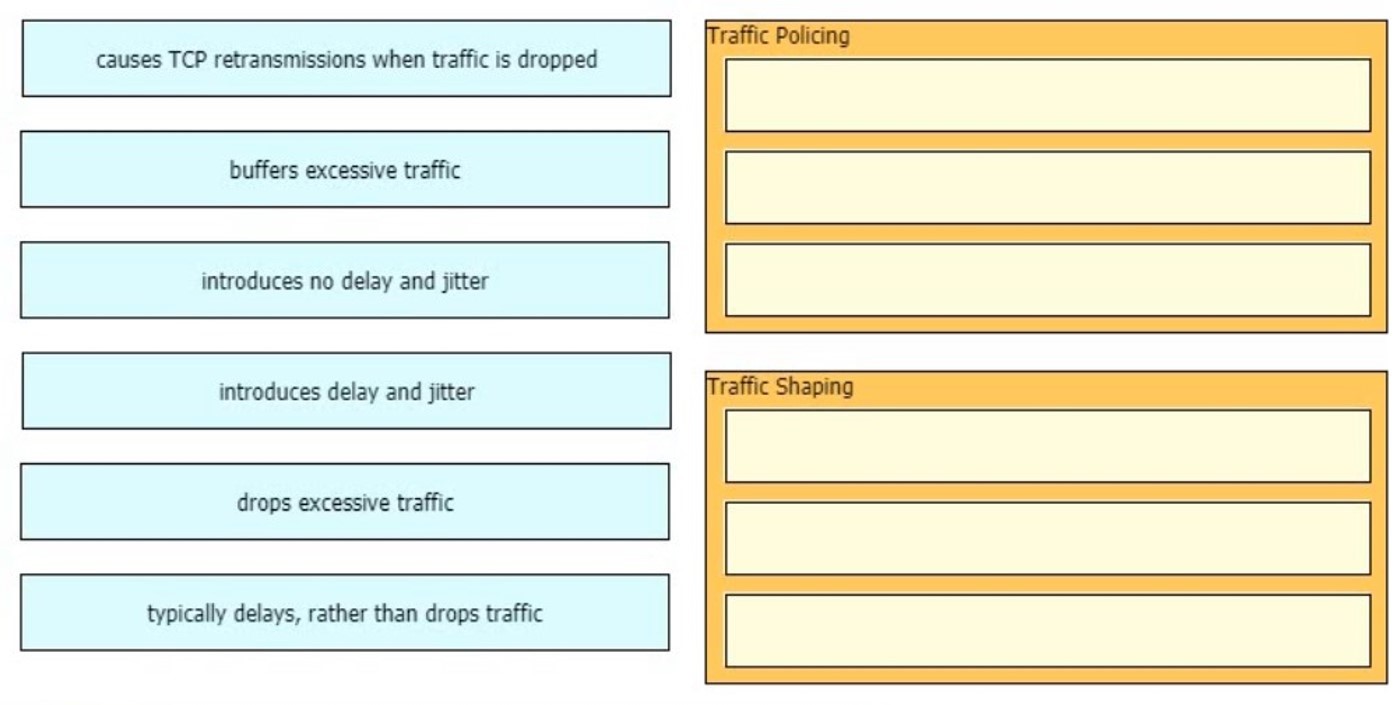
QUESTION 18
Drag and drop the DHCP messages that are exchanged between a client and an AP into the order they are exchanged on the right.
Select and Place:

QUESTION 19
Drag and drop the characteristics from the left onto the protocols they apply to on the right?
Select and Place:
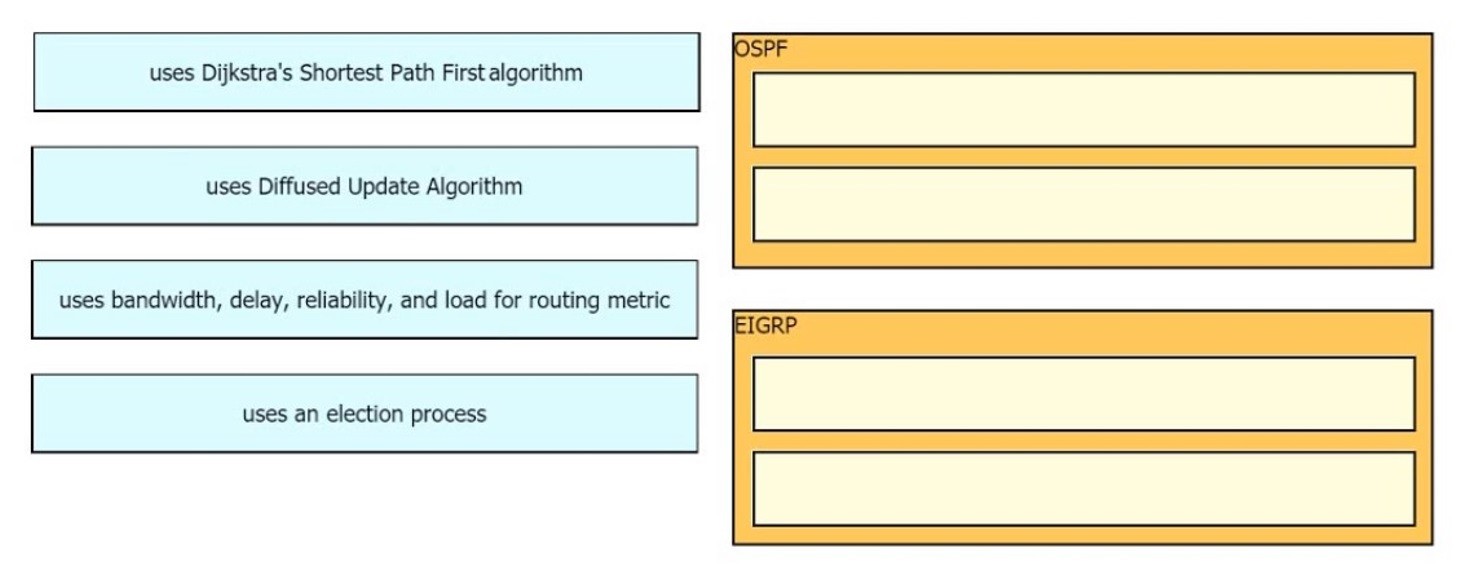
QUESTION 20
Drag and drop the automation characteristic from the left to correcsponding tools on the right
Select and Place:
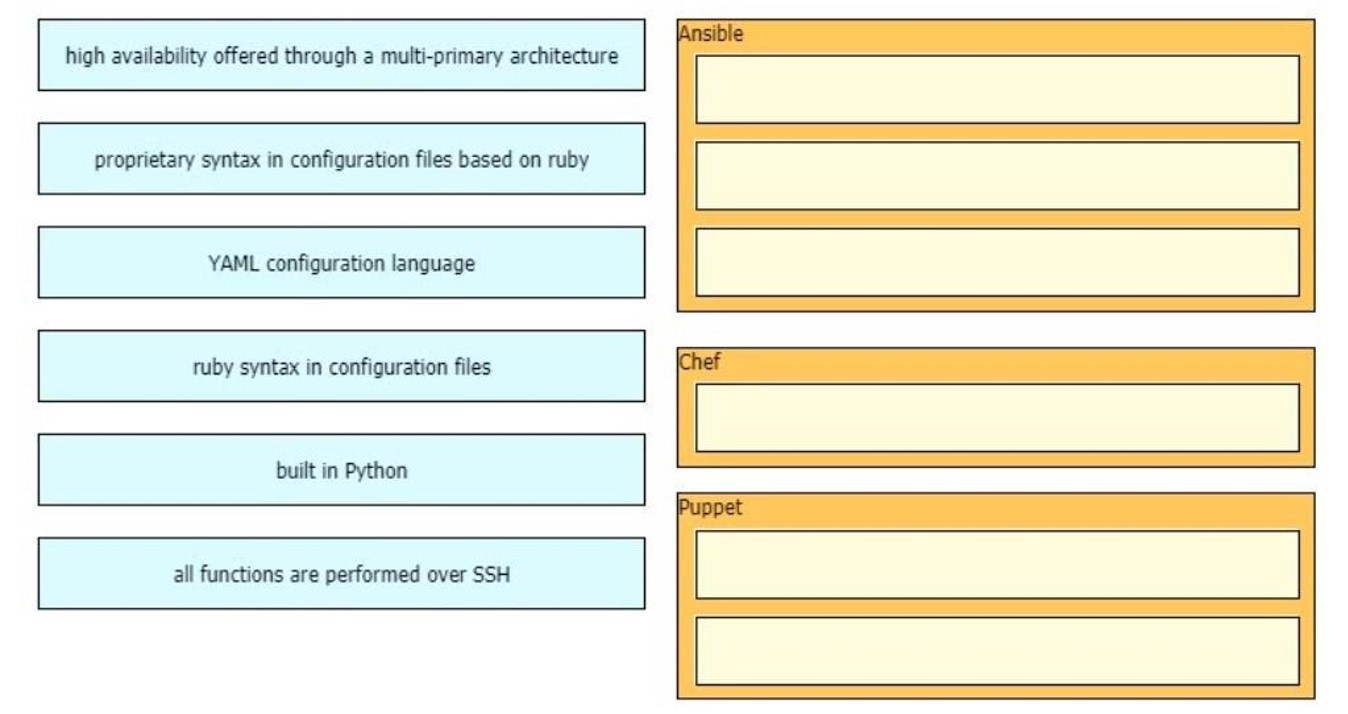
QUESTION 21
Drag and drop the characteristics from the left onto the protocols they describe on the right?
Select and Place:

QUESTION 22
Select and Place:
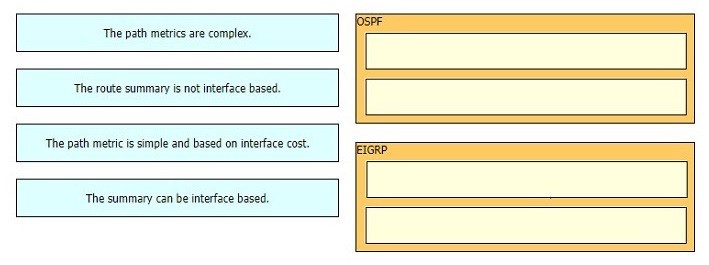
QUESTION 23
Drag and drop the characteristics from the left onto the deployment models on the right. Not all options are used.
Select and Place:
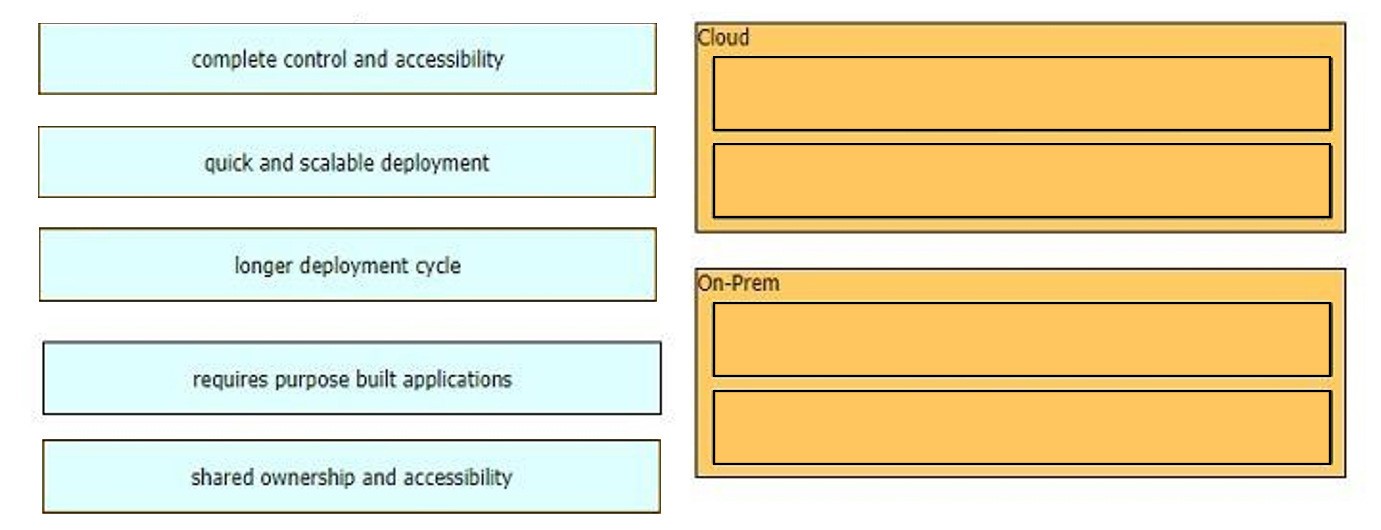
New Questions
QUESTION 1
What is the function of a control-plane node in a Cisco SD-Access solution?
A. To connect APs and wireless endpoints to the SD-Access fabric
B. To connect external Layer 3 networks to the SD Access fabric
C. To implement policies and communicate with networks outside the fabric
D. To run a mapping system that manages endpoint to network device relationships
QUESTION 2
What are two benefits of implementing a Cisco SD-WAN architecture
A. It provides resilient and effective traffic flow using MPLS
B. It improves endpoint protection by integrating embedded and cloud security features
C. It allows configuration of application-aware policies with real time enforcement
D. It simplifies endpoint provisioning through standalone router management
E. It enforces a single, scalable, hub-and-spoke topology
QUESTION 3
Which component does Cisco Threat Defense use to measure bandwidth, application performance, and utilization?
A. NetFlow
B. Cisco Umbrella
C. TrustSec
D. Advanced Malware Protection for Endpoints
QUESTION 4
Which CISCO SD-WAN component authenticates the routers and the vSmart controllers?
A. vAnalytics
B. vBond orchestrator
C. vEdge
D. vManage NMS
QUESTION 5
When voice services are deployed over a wireless environment, which service must be disabled to ensure the quality of calls?
A. Aggressive load balancing
B. Dynamic transmit power control
C. Priority queuing
D. Fastlane
QUESTION 6
What is a characteristic of an AP operating in FlexConnect Mode?
A. All traffic traverses the WLC to ensure policy enforcement on client traffic
B. Forwarding continues when the AP loses connectivity to the WLC
C. APs connect in a mesh topology and elect a root AP
D. FlexConnect enables an AP to connect to multiple WLCs
QUESTION 7
Refer to the exhibit.
list = [1, 2, 3, 4] list[3] = 10 print(list)
What is the value of the variable list after the code is run?
A. [1, 10, 10, 10]
B. [1, 2, 10]
C. [1, 2, 10, 4]
D. [1, 2, 3, 10]
QUESTION 8
A vulnerability assessment highlighted that remote access to the switches is permitted using unsecure and unencrypted protocols Which configuration must be applied to allow only secure and reliable remote access for device administration?
A. line vty 0 15 login local transport input none B. line vty 0 15 login local transport input ssh C. line vty 0 15 login local
transport input telnet ssh D. line vty 0 15 login local transport input all
QUESTION 9
How can an engineer prevent basic replay attacks from people who try to brute force a system via REST API?
A. Use HTTPS
B. Use a password hash
C. Add OAuth to the request in the API header
D. Add a timestamp to the request in the API header
QUESTION 10
A network monitoring system uses SNMP polling to record the statistics of router interfaces. The SNMP queries work as expected until an engineer installs a new interface and reloads the router. After this action, all SNMP queries for the router fail. What is the cause of this issue?
A. The SNMP community is configured incorrectly
B. The SNMP interface index changed after reboot
C. The SNMP server traps are disabled for the interface index
D. The SNMP server traps are disabled for the link state
QUESTION 11
If a client’s radio device receives a signal strength of -67 dBm and the noise floor is -85 dBm, what is the SNR value?
A. 15 dB
B. 16 dB
C. 18 dB
D. 20 dB
QUESTION 12
Refer to the exhibit.

VPN-A sends point-to-point traffic to VPN-B and receives traffic only from VPN-C. VPN-B sends point-to-point traffic to VPN-C and receives traffic only from VPN-A. Which configuration is applied?
A. PE-2
vrf VPN-B address-family ipv4 unicast import route-target 100:1 export route-target 100:2
B. PE-3
vrf VPN-B address-family ipv4 unicast import route-target 100:1 export route-target 100:2 C.
D.
QUESTION 13
An engineer must create a new SSID on a Cisco 9800 wireless LAN controller. The client has asked to use a pre-shared key for authentication. Which profile must the engineer edit to achieve this requirement?
A. RF
B. Policy
C. WLAN
D. Flex
QUESTION 14
Refer to the exhibit.
R1#show run | b router ospf router ospf 1 network 192.168.10.0 0.0.0.255 area 0
R1#show run | b interface loopback0 interface loopback0 ip address 192.168.10.50 255.255.255.0
R2 is the neighboring router of R1. R2 receives an advertisement for network 192 168.10.50/32. Which configuration should be applied for the subnet to be advertised with the original /24 netmask?
A. R1(config)#interface loopback0
R1(config-if)#ip ospf network point-to-point
B. R1(config)#interface loopback0R1(config-if)#ip ospf 1 area 0
C. R1(config)#router ospf 1
R1(config-router)#network 192.168.10.0 255.255.255.0 area 0
D. R1(config)#interface loopback0
R1(config-if)#ip ospf network non-broadcast
QUESTION 15
A customer requests a design that includes GLBP as the FHRP. The network architect discovers that the members of the GLBP group have different throughput capabilities. Which GLBP load balancing method supports this environment?
A. host dependent
B. weighted
C. round robin
D. least connection
QUESTION 16
What is one primary REST security design principle?
A. password hash
B. fail-safe defaults
C. Adding a timestamp in requests
OAuth
QUESTION 17
An engineer must enable a login authentication method that allows a user to log in by using local authentication if all other defined authentication methods fail. Which configuration should be applied?
A. aaa authentication login CONSOLE group radius local-case enable aaa
B. authentication login CONSOLE group radius local enable none
C. aaa authentication login CONSOLE group radius local enable
D. aaa authentication login CONSOLE group tacacs+ local enable
QUESTION 18
Refer to the exhibit.
10.0.32.0/24 10.0.33.0/24 10.0.34.0/24 10.0.35.0/24 10.0.36.0/24 10.0.37.0/24 10.0.38.0/24
10.0.39.0/24
An engineer must permit traffic from these networks and block all other traffic. An informational log message should be triggered when traffic enters from these prefixes. Which access list must be used?
A. access-list acl_subnets permit ip 10.0.32.0 0 0.0.255 log
B. access-list acl_subnets permit ip 10.0.32.0 0.0.7.255 log C. access-list acl_subnets permit ip 10.0.32.0 0.0.7.255 access-list acl_subnets deny ip any log
D. access-list acl_subnets permit ip 10.0.32.0 255.255.248.0 log
QUESTION 19
A network engineer configures a WLAN controller with increased security for web access. There is IP connectivity with the WLAN controller, but the engineer cannot start a management session from a web browser. Which action resolves the issue?
A. Use a private or incognito session.
B. Disable Adobe Flash Player
C. Disable JavaScript on the web browser
D. Use a browser that supports 128-bit or larger ciphers.
QUESTION 20
Refer to the exhibit.

How does the router handle traffic after the CoPP policy is configured on the router?
A. Traffic coming to R1 that does not match access list SNMP is dropped.
B. Traffic generated by R1 that matches access list SNMP is policed.
C. Traffic passing through R1 that matches access list SNMP is policed.
D. Traffic coming to R1 that matches access list SNMP is policed.
QUESTION 21
Refer to the exhibit.
Which command set changes the neighbor state from Idle (Admin) to Active?
A. R1(config)#router bgp 65001
R1(config-router)#neighbor 192.168.50.2 activate
B. R1(config)#router bgp 65002
R1(config-router)#neighbor 192.168.50.2 activate
C. R1(config)#router bgp 65001
R1(config-router)#no neighbor 192.168.50.2 shutdown
D. R1(config)#router bgp 65001
R1(config-router)#neighbor 192.168.50.2 remote-as 65001
QUESTION 22
When firewall capabilities are considered, which feature is found only in Cisco next-generation firewalls?
A. malware protection
B. stateful inspection
C. traffic filtering
active/standby high availability
QUESTION 23
Refer to the exhibit.

An engineer configures the BGP adjacency between R1 and R2, however, it fails to establish. Which action resolves the issue?
A. Change the network statement on R1 to 172.16.10.0
B. Change the remote-as number for 192.168.100.11
C. Enable synchronization on R1 and R2
D. Change the remote-as number on R1 to 6500
QUESTION 24
Refer to the exhibit.
An engineer attempts to bundle interface Gi0/0 into the port channel, but it does not function as expected. Which action resolves the issue?
A. Set LACP max-bundle to 2 on interface Port-channel
B. Configure no shutdown on interface Gi0/0
C. Enable fast LACP PDUs on interface Gi0/0
D. Configure channel-group 1 mode active on interface Gi0/0
QUESTION 25
A network engineer is enabling HTTPS access to the core switch, which requires a certificate to be installed on the switch signed by the corporate certificate authority. Which configuration commands are required to issue a certificate signing request from the core switch?
A. Core-Switch(config)#crypto pki trustpoint Core-Switch Core-Switch(ca-trustpoint)#enrollment terminal
Core-Switch(config)#crypto pki enroll Core-Switch
B. Core-Switch(config)#crypto pki enroll Core-SwitchCore-Switch(config)#ip http secure-trustpoint Core-Switch
C. Core-Switch(config)#ip http secure-trustpoint Core-Switch Core-Switch(config)#crypto pki enroll Core-Switch
D. Core-Switch(config)#crypto pki trustpoint Core-Switch Core-Switch(ca-trustpoint)#enrollment terminal
Core-Switch(config)#ip http secure-trustpoint Core-Switch
QUESTION 26
Refer to the exhibit.
An engineer must prevent the R6 loopback from getting into Area 2 and Area 3 from Area 0. Which action must the engineer take?
A. Apply a fitter list inbound on R2 and R9
B. Apply a filter list outbound on R3 and R7
C. Apply a filter list outbound on R7 only
Apply a filter list inbound on R3 and R7
QUESTION 27
Which two parameters are examples of a QoS traffic descriptor? (Choose two)
A. MPLS EXP bits
B. bandwidth
C. DSCP
D. packet size
E. ToS
QUESTION 28
Refer to the exhibit.
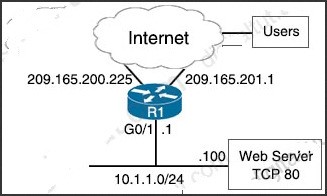
An engineer must configure static NAT on R1 to allow users HTTP access to the web server on TCP port 80. The web server must be reachable through ISP 1 and ISP 2. Which command set should be applied to R1 to fulfill these requirements?
A. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 extendable ip nat inside source static tcp 10.1.1.100 80 209.165.201.1 80 extendable B. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 ip nat inside source static tcp 10.1.1.100 80 209.165.201.1 80
C. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 ip nat inside source static tcp 10.1.1.100 8080 209.165.201.1 8080
D. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 no-alias ip nat inside source static tcp 10.1.1.100 80 209.165.201.1 80 no-alias
QUESTION 29
Based on the router’s API output in JSON format below, which Python code will display the value of the “hostname” key?
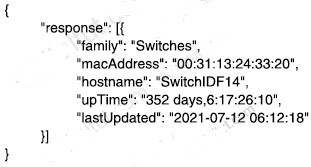
A. json_data = json.loads(response.text) print(json_data[‘response’][‘family’][‘hostname’]) B. json_data = response.json() print(json_data[‘response’][0][‘hostname’]) C. json_data = response.json() print(json_data[‘response’][family][hostname’]) D. json_data = json.loads(response.text) print(json_data[response][0][hostname])
QUESTION 30
Refer to the exhibit.
logging buffered discriminator Disc1 logging monitor discriminator Disc1 logging host 10.1.55.237 discriminator Disc1
A network engineer is enabling logging to a local buffer, to the terminal and to a syslog server for all debugging level logs filtered by facility code 7. Which command is needed to complete this configuration snippet?
A. logging buffered debugging
B. logging discriminator Disc1 severity includes 7
C. logging buffered discriminator Disc1 debugging
D. logging discriminator Disc1 severity includes 7 facility includes fac7
Correct Answer: D
QUESTION 31 Refer to the exhibit.

After configuring HSRP an engineer enters the show standby command. Which two facts are derived from the output? (Choose two)
A. The router with IP 10.10.1.3 is active because it has a higher IP address
B. R2 Fa1/0 regains the primary role when the link comes back up
C. If Fa0/0 is shut down, the HSRP priority on R2 becomes 80
D. R2 is using the default HSRP hello and hold timers
E. R2 becomes the active router after the hold time expires
QUESTION 32
Refer to the exhibit. enable secret cisco username cisco privilege 15 secret cisco
aaa new-model
aaa authentication login default group radius local aaa authorization network default group radius
The network administrator must be able to perform configuration changes when all the RADIUS servers are unreachable. Which configuration allows all commands to be authorized if the user has successfully authenticated?
A. aaa authorization exec default group radius none
B. aaa authentication login default group radius local none
C. aaa authorization exec default group radius
D. aaa authorization exec default group radius if-authenticated
QUESTION 33
Refer to the exhibit.
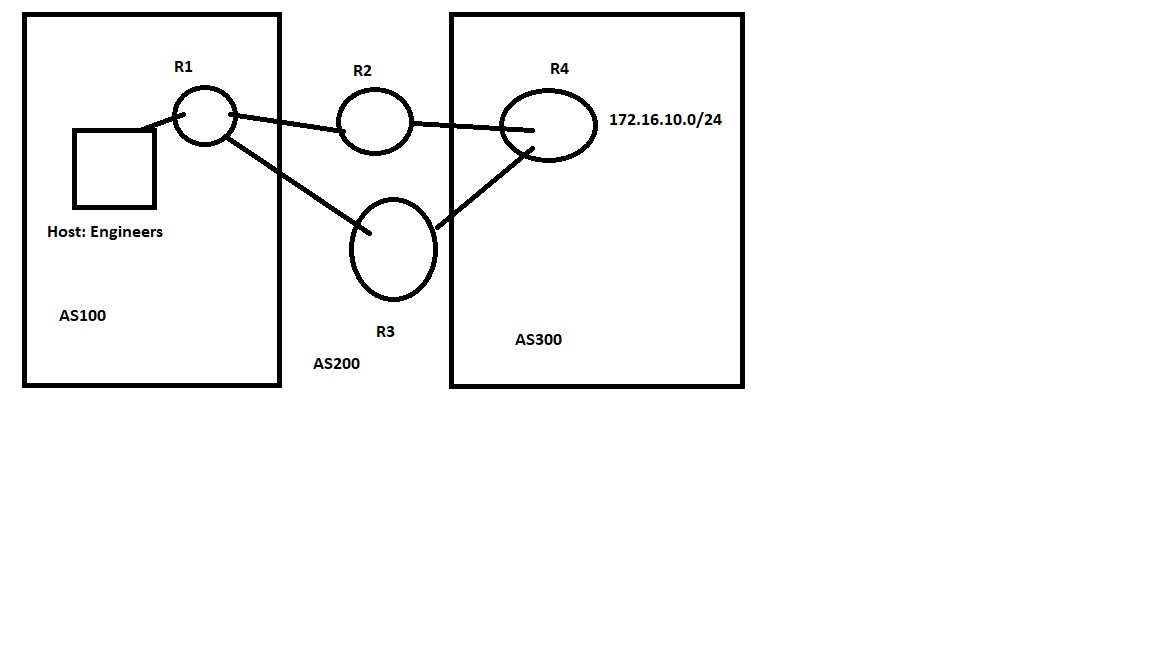
An engineers reaching network 172.16.10.0/24 via the R1-R2-R4 path. Which configuration forces the traffic to take a path of R1-R3-R4?
A. R1(config)#route-map RM_AS_PATH_PREPEND
R1(config-route-map)#set as-path prepend 200 200
R1(config-route-map)#exit
R1(config)#router bgp 100
R1(config-router)#neighbor 12.12.12.2 route-map RM_AS_PATH_PREPEND in
R1(config-router)#end
R1#clear ip bgp 12.12.12.2 soft in
B. R1(config)#router bgp 100
R1(config-router)#neighbor 13.13.13.3 weight 1
R1(config-router)#end
C. R2(config)#route-map RM_MED permit 10
R2(config-route-map)#set metric 1
R2(config-route-map)#exit
R2(config)#router bgp 200
R2(config-router)#neighbor 12.12.12.1 route-map RM_MED out
R2(config-router)#end
R2#clear ip bgp 12.12.12.1 soft out
D. R1(config)#route-map RM_LOCAL_PREF permit 10
R1(config-route-map)#set local-preference 101
R1(config-route-map)#exit
R1(config)#router bgp 100
R1(config-router)#neighbor 13.13.13.3 route-map RM_LOCAL_PREF in
R1(config-router)#end
R1#clear ip bgp 13.13.13.3 soft in
QUESTION 34
In a Cisco SD-Access solution, which protocol is used by an extended node to connect to a single edge node?
A. IS-IS
B. 802.1Q
C. VXLAN
D. CTS
QUESTION 35
What is a characteristic of Cisco StackWise technology?
A. It uses proprietary cabling
B. It supports devices that are geographically separated
C. It combines exactly two devices
D. It is supported on the Cisco 4500 series.
QUESTION 36
In a Cisco SD-WAN solution, which two functions are performed by OMP? (Choose two)
A. advertisement of network prefixes and their attributes
B. segmentation and differentiation of traffic
C. gathering of underlay infrastructure data
D. delivery of crypto keys
E. configuration of control and data policies
QUESTION 37
Refer to the exhibit. <exhibit missing>
An engineer must create a configuration that prevents R3 from receiving the LSA about 172.16.1.4/32. Which configuration set achieves this goal?
A. On R3
ip access-list standard R4_L0 deny host 172.16.1.4 permit any
router ospf 200 distribute-list R4_l0 in
B. On R3
ip prefix-list INTO-AREA1 seq 5 deny 172.16.1.4/32 ip prefix-list INTO-AREA1 seq 10 permit 0.0.0.0/0 le 32 router ospf 200
area 1 filter-list prefix INTO-AREA1 in
C. On R1
ip prefix-list INTO-AREA1 seq 5 deny 172.16.1.4/32 ip prefix-list INTO-AREA1 seq 10 permit 0.0.0.0/0 le 32
router ospf 200 area 1 filter-list prefix INTO-AREA1 in
D. On R1
ip prefix-list INTO-AREA1 seq 5 deny 172.16.1.4/32 ip prefix-list INTO-AREA1 seq 10 permit 0.0.0.0/0 le 32
router ospf 200 area 1 filter-list prefix INTO-AREA1 out
QUESTION 38
Why would an engineer use YANG?
A. To model data for NETCONF
B. To access data using SNMP
C. To transport data between a controller and a network device
D. To translate JSON into an equivalent XML syntax
QUESTION 39
By default, which virtual MAC address does HSRP group 16 use?
A. c0:41:43:64:13:10
B. 00:00:0c:07:ac:10C. 05:00:0c:07:ac:16
D. 00:05:5c:07:0c:16
QUESTION 40
How are map-register messages sent in a LISP deployment?
A. egress tunnel routers to map resolvers to determine the appropriate egress tunnel router
B. ingress tunnel routers to map servers to determine the appropriate egress tunnel router
C. egress tunnel routers to map servers to determine the appropriate egress tunnel router
D. ingress tunnel routers to map resolvers to determine the appropriate egress tunnel router
QUESTION 41
Which method is used by an AP to join HA controllers and is configured in NVRAM?
A. Primary/Secondary/Tertiary/Backup
B. DNS
C. IP Helper Addresses
D. stored WLC information
QUESTION 42
In a Cisco StackWise Virtual environment, which planes are virtually combined in the common logical switch?
A. control and management
B. management and data
C. control, and forwarding
D. control and data
QUESTION 43
Refer to the exhibit.
<exhibit missing>
… —config missing— Hello due in 00:00:07
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 1/2/2, flood queue length 0
Next 0x0(0)/0x0(0)/0x0(0)
Last flood scan length is 0, maximum is 0
Last flood scan time is 1 msec, maximum is 1 msec
Neighbor Count is 0, Adjacent neighbor count is 0 Suppress hello for 0 neighbor(s)
An engineer configures OSPF and wants to verify the configuration. Which configuration is applied to this device?
A. R1(config)#interface Gi0/1
R1(config-if)#ip ospf 1 area 0
R1(config-if)#no shutdown
B. R1(config)#router ospf 1
R1(config-router)#network 0.0.0.0.0 0.0.0.0 area 0
R1(config-router)#no passive-interface Gi0/1
C. R1(config)#interface Gi0/1R1(config-if)#ip ospf enable
R1(config-if)#ip ospf network broadcast
R1(config-if)#no shutdown
D. R1(config)#router ospf 1
R1(config-router)#network 192.168.50.0 0.0.0.255 area 0
QUESTION 44
When is the Design workflow used in Cisco DNA Center?
A. in a greenfield deployment, with no existing infrastructure
B. in a greenfield or brownfield deployment, to wipe out existing data
C. in a brownfield deployment, to modify configuration of existing devices in the network
D. in a brownfield deployment, to provision and onboard new network devices
QUESTION 45
A customer wants to use a single SSID to authenticate IoT devices using different passwords. Which Layer 2 security type must be configured in conjunction with Cisco ISE to achieve this requirement?
A. Fast Transition
B. Identity PSK
C. Cisco Centralized Key Management
D. Central Web Authentication
QUESTION 46
What does a northbound API accomplish?
A. programmatic control of abstracted network resources through a centralized controller
B. access to controlled network resources from a centralized node
C. communication between SDN controllers and physical switches
D. controlled access to switches from automated security applications
QUESTION 47
Refer to the exhibit.
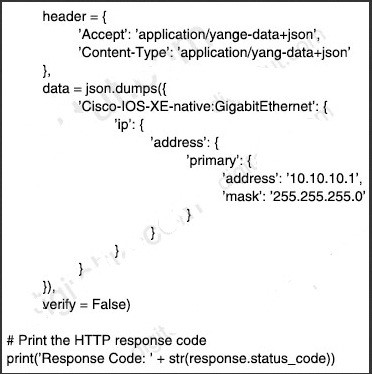
After the code is run on a Cisco IOS-XE router, the response code is 204. What is the result of the script?
A. The configuration fails because another interface is already configured with IP address 10.10.10.1/24
B. The configuration fails because interface GigabitEthernet2 is missing on the target device.
C. The configuration is successfully sent to the device in cleartext.
D. Interface GigabitEthernet2 is configured with IP address 10.10.10.1/24
Correct Answer: D
QUESTION 48
An engineer attempts to establish BGP peering between router CORP and two ISP routers. What is the root cause for the failure between CORP and ISP#2?
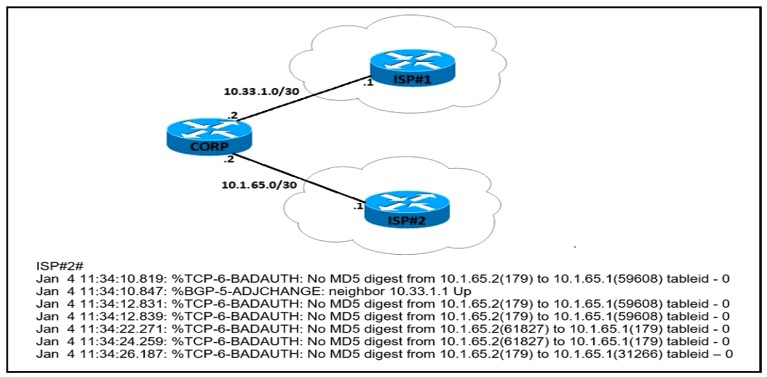
A. Router ISP#2 is configured to use SHA-1 authentication.
B. There is a password mismatch between router CORP and router ISP#2.
C. Router CORP is configured with an extended access control list.
D. MD5 authorization is configured incorrectly on router ISP#2.
QUESTION 49
An administrator must enable Telnet access to Router X using the router username and password database for authentication. Which configuration should be applied?
A. RouterX(config)#aaa new-model
RouterX(config)#aaa authentication login auth-list local
B. RouterX(config)#line vty 0 4
RouterX(config-line)#login
RouterX(config-line#end
C. RouterX(config)#line aux 0
RouterX(config-line)#password cisco
RouterX(config-line#login
D. RouterX(config)#line vty 0 4
RouterX(config-line)#login local
RouterX(config-line#end
QUESTION 50
Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
Select and Place:

QUESTION 51
Refer to the exhibit.
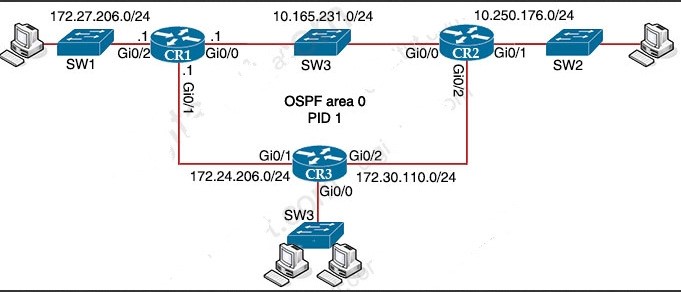
CR2 and CR3 are configured with OSPF. Which configuration, when applied to CR1, allows CR1 to exchange OSPF information with CR2 and CR3 but not with other network devices or on new interfaces that are added to CR1?
A. router ospf 1 network 0.0.0.0 255.255.255.255 area 0 passive-interface GigabitEthernet0/2 B. router ospf 1 network 10.0.0.0 0.255.255.255 area 0 network 172.16.0.0 0.15.255.255 area 0 passive-interface GigabitEthernet0/2 C. interface Gi0/2 ip ospf 1 area 0
!
router ospf 1 passive-interface GigabitEthernet0/2 D. router ospf 1 network 10.165.231.0 0.0.0.255 area 0 network 172.27.206.0 0.0.0.255 area 0 network 172.24.206.0 0.0.0.255 area 0
QUESTION 52
Drag and drop the characteristics from the left onto the infrastructure deployment models they describe on the right.
Select and Place:
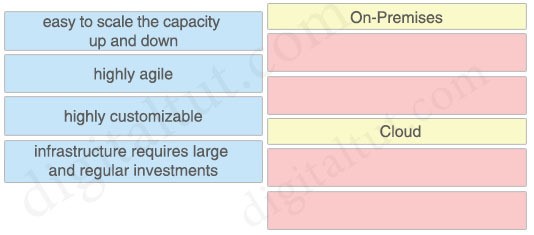
QUESTION 53
In which two ways does TCAM differ from CAM? (Choose two)
A. CAM is used to make Layer 2 forwarding decisions, and TCAM is used for Layer 3 address lookups.
B. The MAC address table is contained in TCAM, and ACL and QoS information is stored in CAM.
C. CAM is used for software switching mechanisms, and TCAM is used for hardware switching mechanisms D. CAM is used by routers for IP address lookups, and TCAM is used to make Layer 2 forwarding decisions.
E. The MAC address table is contained in CAM, and ACL and QoS information is stored in TCAM.
QUESTION 54
Refer to the exhibit.
SW2(config)#track 1000 interface gigabitEthernet0/0 line-protocol
SW2(config-track)#exit
SW2(config)#interface vlan 1000
SW2(config-if)#ip address 10.23.87.3 255.255.255.0
An engineer must configure HSRP for VLAN 1000 on SW2. The secondary switch must immediately take over the role of active router if the interlink with the primary switch fails. Which command set completes this task?
A. SW2(config-if)#standby version 2
SW2(config-if)#standby 1000 ip 10.23.87.1
SW2(config-if)#standby 1000 priority 95
SW2(config-if)#standby 1000 preempt
SW2(config-if)#standby 1000 track 1000
B. SW2(config-if)#standby version 2
SW2(config-if)#standby 1000 ip 10.23.87.1
SW2(config-if)#standby 1000 priority 95
SW2(config-if)#standby 1000 track 1000
C. SW2(config-if)#standby version 2
SW2(config-if)#standby 1000 ip 10.23.87.1
SW2(config-if)#standby 1000 priority 95
SW2(config-if)#standby 1000 preempt
SW2(config-if)#standby 1000 track gigabitethernet0/0
D. SW2(config-if)#standby 1000 ip 10.23.87.1
SW2(config-if)#standby 1000 priority 95
SW2(config-if)#standby 1000 preempt
SW2(config-if)#standby 1000 track 1000
QUESTION 55
Drag and drop the snippets onto the blanks within the code to construct a script that adds a prefix list to a route map and sets the local preference. Not all options are used.
Select and Place:
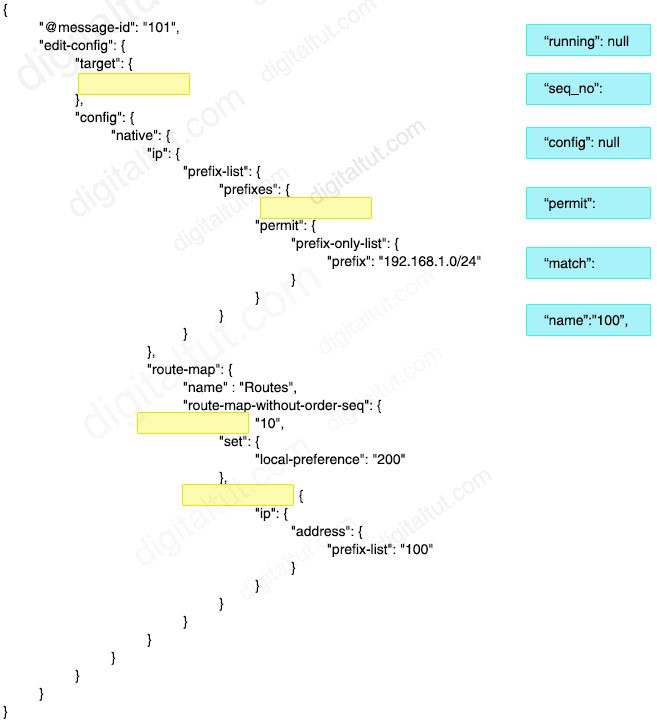
QUESTION 56
Drag and drop the tools from the left onto the agent types on the right.
Select and Place:
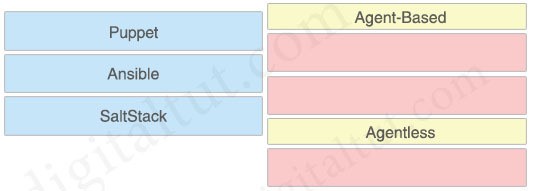
QUESTION 57
Drag and drop the characteristics from the left onto the infrastructure deployment models on the right.
Select and Place:
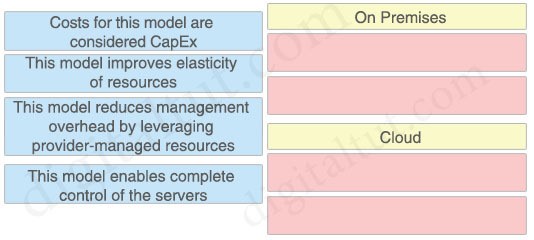
QUESTION 58
What occurs when a high bandwidth multicast stream is sent over an MVPN using Cisco hardware?
A. The traffic uses the default MDT to transmit the data only if it isa (S,G) multicast route entry
B. A data MDT is created to if it is a (*, G) multicast route entries
C. A data and default MDT are created to flood the multicast stream out of all PIM-SM neighbors.
D. A data MDT is created to allow for the best transmission through the core for (S, G) multicast route entries.
QUESTION 59
Which IPv4 packet field carries the QoS IP classification marking?
A. ID
B. TTL
C. FCS
D. ToS
QUESTION 60
Drag and drop the characteristics from the left onto the technology types on the right.
Select and Place:

QUESTION 61
Refer to the exhibit.

A network engineer must log in to the router via the console, but the RADIUS servers are not reachable. Which credentials allow console access?
A. the username “cisco” and the password “cisco123”
B. no username and only the password “test123”
C. no username and only the password “cisco123”
D. the username “cisco” and the password “cisco”
QUESTION 62
A customer transitions a wired environment to a Cisco SD-Access solution. The customer does not want to integrate the wireless network with the fabric. Which wireless deployment approach enables the two systems to coexist and meets the customer requirement?
A. Deploy a separate network for the wireless environment.
B. Implement a Cisco DNA Center to manage the two networks.
C. Deploy the wireless network over the top of the fabric.
D. Deploy the APs in autonomous mode.
QUESTION 63
Which two solutions are used for backing up a Cisco DNA Center Assurance database? (Choose two)
A. NFS share
B. local server
C. non-linux server
D. remote server
E. bare metal server
QUESTION 64
Refer to the exhibit.
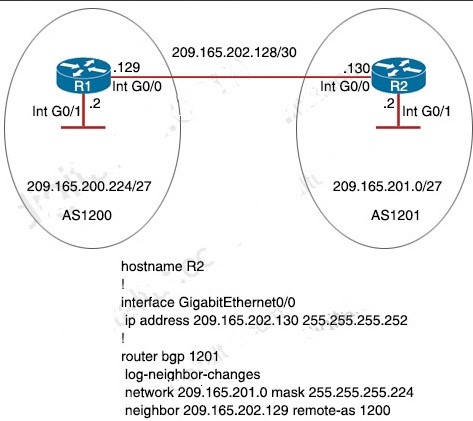
Which command set must be applied on R1 to establish a BGP neighborship with R2 and to allow communication from R1 to reach the networks?
A. router bgp 1200 network 209.165.200.224 mask 255.255.255.224 neighbor 209.165.202.130 remote-as 1201 B. router bgp 1200 network 209.165.201.0 mask 255.255.255.224 neighbor 209.165.202.130 remote-as 1201 C. router bgp 1200 network 209.165.200.224 mask 255.255.255.224 neighbor 209.165.202.130 remote-as 1200 D. router bgp 1200 network 209.165.200.224 mask 255.255.255.224 neighbor 209.165.201.2 remote-as 1200
QUESTION 65
A customer wants to provide wireless access to contractors using a guest portal on Cisco ISE. The portal is also used by employees. A solution is implemented, but contractors receive a certificate error when they attempt to access the portal. Employees can access the portal without any errors. Which change must be implemented to allow the contractors and employees to access the portal?
A. Install a trusted third-party certificate on the Cisco ISE
B. Install an internal CA signed certificate on the Cisco ISE.
C. Install a trusted third-party certificate on the contractor devices.
D. Install an internal CA signed certificate on the contractor devices.
QUESTION 66
What is the API keys option for REST API authentication?
A. a predetermined string that is passed from client to server
B. a one-time encrypted token
C. a username that is stored in the local router database
D. a credential that is transmitted unencrypted
QUESTION 67
Refer the exhibit.
Which configuration elects SW4 as the root bridge for VLAN 1 and puts G0/2 on SW2 into a blocking state?
A. SW4(config)#spanning-tree vlan 1 priority 32768
!
SW2(config)#interface G0/2
SW2(config-if)#spanning-tree vlan 1 port-priority 0
B. SW4(config)#spanning-tree vlan 1 priority 32768
!
SW2(config)#int G0/2
SW2(config-if)#spanning-tree cost 128
C. SW4(config)#spanning-tree vlan 1 priority 0
!
SW2(config)#int G0/2
SW2(config-if)#spanning-tree cost 128
D. SW4(config)#spanning-tree vlan 1 priority 0
!
SW2(config)#interface G0/2
SW2(config-if)#spanning-tree vlan 1 port-priority 64
Correct Answer: C
QUESTION 68
Which Python code snippet must be added to the script to save the returned configuration as a JSON-formatted file?
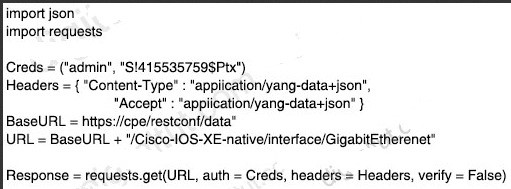
A. with open(“ifaces.json”, “w”) as OutFile: OutFile.write(Response.text)
B. with open(“ifaces.json”, “w”) as OutFile: OutFile.write(Response.json())
C. with open(“ifaces.json”, “w”) as OutFile:
JSONResponse = json.loads(Response.text)
OutFile.write(JSONResponse)
D. with open(“ifaces.json”, “w”) as OutFile: OutFile.write(Response)
QUESTION 69
Refer to the exhibit.
An engineer must configure an ERSPAN session with the remote end of the session 10.10.0.1. Which commands must be added to complete the configuration?
A. Device(config)# monitor session 1 type erspan-source
Device(config-mon-erspan-src)# destination
Device(config-mon-erspan-src-dst)#no origin ip address 10.10.0.1
Device(config-mon-erspan-src-dst)#ip address 10.10.0.1
B. Device(config)# monitor session 1 type erspan-destination
Device(config-mon-erspan-src)# source
Device(config-mon-erspan-src-dst)#origin ip address 10.1.0.1
C. Device(config)# monitor session 1 type erspan-source
Device(config-mon-erspan-src)# destination
Device(config-mon-erspan-src-dst)#no origin ip address 10.10.0.1
Device(config-mon-erspan-src-dst)#ip destination address 10.10.0.1
D. Device(config)# monitor session 1 type erspan-source
Device(config-mon-erspan-src)# destination
Device(config-mon-erspan-src-dst)#no vrf 1
QUESTION 70
Refer to the exhibit.
Reachability between servers in a network deployed with DHCPv6 is unstable. Which command must be removed from the configuration to make DHCPv6 function?
A. ipv6 address 2001:0:1:4::1/64
B. ipv6 dhcp server DHCPPOOL
C. ipv6 nd ra suppress
D. address prefix 2001:0:1:4::/64 lifetime infinite infinite
QUESTION 71
Which configuration feature should be used to block rogue router advertisements instead of using the IPv6 Router Advertisement Guard feature?
A. VACL blocking broadcast frames from nonauthorized hosts
B. IPv4 ACL blocking route advertisements from nonauthorized hosts
C. PVLANs with promiscuous ports associated to route advertisements and isolated ports for nodes
D. PVLANs with community ports associated to route advertisements and isolated ports for nodes
QUESTION 72
Refer to the exhibit.
R6 should reach R1 via R5>R2>R1. Which action resolves the issue?
A. Decrease the cost to 2 between R6-R5-R2.
B. Decrease the cost to 41 between R2 and R1.
C. Increase the cost to 61 between R2 and R3.
D. Increase the cost to 61 between R2-R3-R1.
QUESTION 73
Refer to the exhibit.

Router R2 should be learning the route for 10.123.187.0/24 via EIGRP. Which action resolves the issue without introducing more issues?
A. Remove route redistribution in R2 for this route in OSPF.
B. Use distribute-list to modify the route as an internal EIGRP route.
C. Redistribute the route in EIGRP with metric, delay, and reliability.
D. Use distribute-list to filter the external routes in OSPF.
QUESTION 74
Refer to the exhibit.
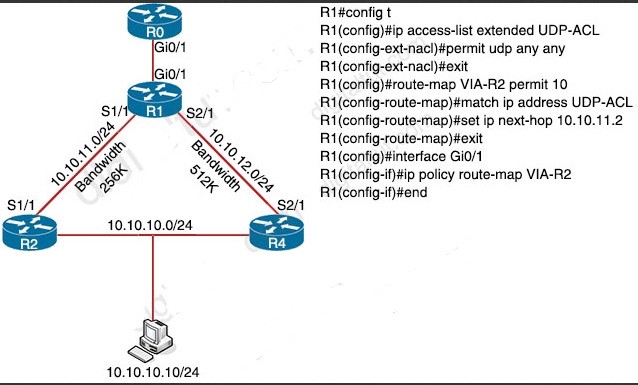
TCP traffic should be reaching host 10.10.10.10/24 via R2. Which action resolves the issue?
A. Allow TCP in the access list with no changes to the route map.
B. Set IP next-hop to 10.10.12.2 under the route-map permit 10 to allow TCP traffic.
C. Add a permit 20 statement in the route map to allow TCP traffic.
D. TCP traffic will reach the destination via R2 without any changes.
QUESTION 75
A customer requested a GRE tunnel through the provider network between two customer sites using loopback to hide internal networks. Which configuration on R2 establishes the tunnel with R1?
A. R2(config)#interface Tunnel1
R2(config-if)#ip address 172.20.1.2 255.255.255.0
R2(config-if)#ip mtu 1500
R2(config-if}#ip tcp adjust-mss 1360
R2(config-if)#tunnel source 192.168.20.1
R2(config-if)#tunnel destination 10.10.1.1
B. R2(config)#interface Tunnel1
R2(config-if)#ip address 172.20.1.2 255.255.255.0
R2(config-if)#ip mtu 1400
R2(config-if)#ip tcp adjust-mss 1360
R2(config-if)#tunnel source 192.168.20.1
R2(config-if)#tunnel destination 192.168.10.1
C. R2(config)#interface Tunnel1
R2(config-if)#ip address 172.20.1.2 255.255.255.0
R2(config-if)#ip mtu 1400
R2(config-if)#ip tcp adjust-mss 1360
R2(config-if)#tunnel source 10.10.2.2
R2(config-if)#tunnel destination 10.10.1.1
D. R2(config)#interface Tunnel1
R2(config-if)#ip address 172.20.1.2 255.255.255.0
R2(config-if)#ip mtu 1500
R2(config-if)#ip tcp adjust-mss 1360
R2(config-if)#tunnel source 10.10.2.2
R2(config-if)#tunnel destination 10.10.1.1
QUESTION 76
An engineer failed to run diagnostic commands on devices using Cisco DNA center, which action in Cisco DNA center resolves the issue?
A. Enable Secure Shell.
B. Enable Command Runner.
C. Enable APIsD. Enable CDP.
QUESTION 77
Refer to the exhibit.

A network administrator notices these console messages from host 10.11.110.12 originating from interface E1/0. The administrator considers this an unauthorized attempt to access SNMP on R1. Which action prevents the attempts to reach R1 E1/0?
A. Configure IOS management plane protection using ACL 90 on interface E1/0.
B. Configure IOS control plane protection using ACL 90 on interface E1/0.
C. Add a permit statement including the host 10.11.110.12 into ACL 90.
D. Create an inbound ACL on interface E1/0 to deny SNMP from host 10.11.110.12.
QUESTION 78
A network administrator added a new spoke site with dynamic IP on the DMVPN network. Which configuration command passes traffic on the DMVPN tunnel from the spoke router?
A. ip nhrp registration dynamic
B. ip nhrp registration ignore
C. ip nhrp registration no-registration
D. ip nhrp registration no-unique
QUESTION 79
Refer to the exhibit.
R4 is experiencing packet drop when trying to reach 172.16.2.7 behind R2. Which action resolves the issue?
A. Insert a /24 floating static route on R2 toward R3 with metric 254.
B. Disable auto summarization on R2.
C. Insert a /16 floating static route on R2 toward R3 with metric 254.
D. Enable auto summarization on all three routers R1, R2, and R3.
QUESTION 80
Which two components are required for MPLS Layer 3 VPN configuration? (Choose two)
A. Use MP-BGP for customer routes.
B. Use LDP for customer routes.
C. Use a unique RD per customer VRF.
D. Use pseudowire for Layer 2 routes
E. Use OSPF between PE and CE
QUESTION 81
Refer to the exhibit.
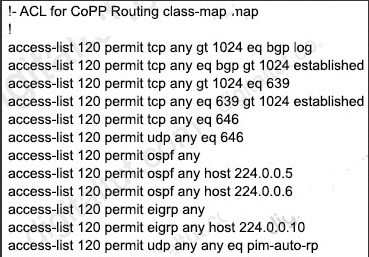
The control plane is heavily impacted after the CoPP configuration is applied to the router. Which command removal lessens the impact on the control plane?
A. access-list 120 permit eigrp any host 224.0.0.10
B. access-list 120 permit ospf any
C. access-list 120 permit udp any any eq pim-auto-rp
D. access-list 120 permit tcp any gt 1024 eq bgp log
QUESTION 82
Refer to the exhibit.
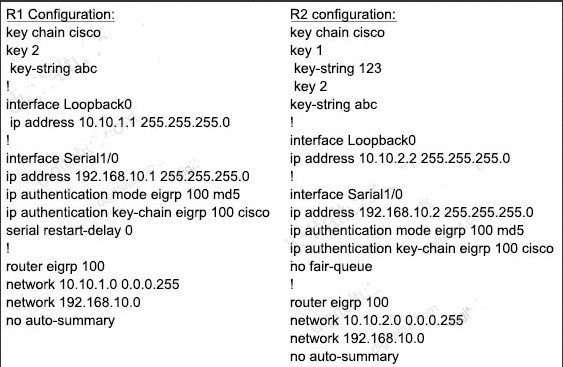
R1 and R2 are configured for EIGRP peering using authentication and the neighbors failed to come up. Which action resolves the issue?
A. Configure a matching key-id number on both routers.
B. Configure a matching lowest key-id on both routers.
C. Configure a matching key-chain name on both routers.
D. Configure a matching authentication type on both routers.
QUESTION 83
Which method provides failure detection in BFD?
A. short duration, high overhead
B. short duration, low overhead
C. long duration, high overhead
D. long duration, low overhead
QUESTION 84
Refer to the exhibit.
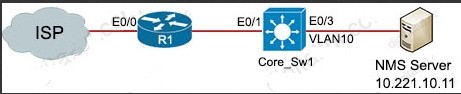
During ISP router maintenance, the network produced many alerts because of the flapping interface. Which configuration on R1 resolves the issue?
A. snmp trap ip verify drop-rate
B. no snmp trap link-status
C. ip verify drop-rate notify hold-down 60
D. snmp trap link-status down
QUESTION 85
Refer to the exhibit.
A loop occurs between R1, R2, and R3 while EIGRP is run with poison reverse enabled. Which action prevents the loop between R1, R2, and R3?
A. Configure route tagging.
B. Enable split horizon.
C. Configure R3 as stub receive-only.
D. Configure route filtering.
QUESTION 86
A customer reports that traffic is not passing on an EIGRP enabled multipoint interface on a router configured as below:
interface Serial0/0/0
no ip address
interface Serial0/0/0.9 multipoint
ip address 10.1.1.1 255.255.255.248
ip split-horizon eigrp 1
Which action resolves the issue?
A. Enable split horizon.
B. Disable poison reverse.
C. Disable split horizon.
D. Enable poison reverse.
QUESTION 87
Refer to the exhibit.
R2#sh ipv6 route ospf O 2002:ABCD::/64 [110/1]
via FastEthernet0/1, directly connected O 2004:BBAB::/64 [110/1]
via FastEthernet0/0, directly connected
O 2004:BBAC::/64 [110/1]
via FastEthernet1/0, directly connected O 3010:2:4:0:15::/128 [110/1] via FE80::C804:1DFF:FB20:8, FastEthernet0/0
A network engineer applied a filter for LSA traffic on OSPFv3 interarea routes on the area 5 ABR to protect advertising the internal routes of area 5 to the business partner network. All other areas should receive the area 5 internal routes. After the respective route filtering configuration is applied on the ABR, area 5 routes are not visible on any of the areas. How must the filter list be applied on the ABR to resolve this issue?
A. in the “out” direction for area 20 on router R2
B. in the “in” direction for area 5 on router R1
C. in the “out” direction for area 5 on router R1
D. in the “in” direction for area 20 on router R2
QUESTION 88
Refer to the exhibit.
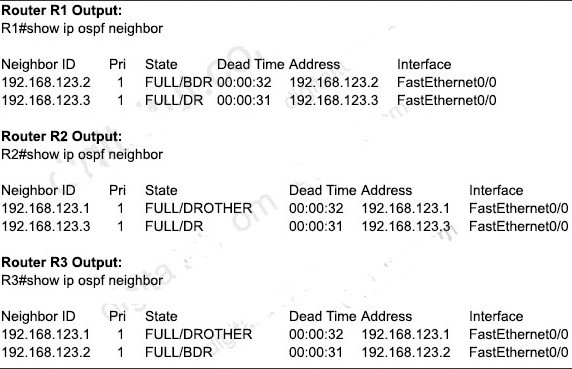
An administrator wanted to make R1 always elected as DR, R2 as BDR, and R3 as DROTHER but could not achieve the desired results. Which two configurations resolve the issue? (Choose two)
A. On the R2 F0/0 interface, configure OSPF priority to 200 B. On the R1 F0/0 interface, configure OSPF priority to 202
C. On the R2 F0/0 interface, configure OSPF priority to 201
D. On the R1 F0/0 interface, configure OSPF priority to 255
E. On the R3 F0/0 interface, configure OSPF priority to 201
QUESTION 89
Refer to the exhibit.

Which configuration enables OSPF for area 0 interfaces to establish adjacency with a neighboring router with the same VRF?
A. router ospf 1 vrf CCNP network 10.1.1.1 0.0.0.0 area 0 network 10.2.2.2 0.0.0.0 area 0
B. router ospf 1 interface Ethernet1 ip ospf 1 area 0.0.0.0 interface Ethernet2 ip ospf 1 area 0.0.0.0
C. router ospf 1 vrf CCNPinterface Ethernet1 ip ospf 1 area 0.0.0.0 interface Ethernet2 ip ospf 1 area 0.0.0.0
D. router ospf 1 vrf CCNPnetwork 10.0.0.0 0.0.255.255 area 0
QUESTION 90
Refer to the exhibit.

An engineer must advertise routes into IPv6 MP-BGP and failed. Which configuration resolves the issue on R1?
A. router bgp 65000
no bgp default ipv4-unicast
address-family ipv6 multicast
network 2001:DB8::/64
B. router bgp 65000
no bgp default ipv4-unicast
address-family ipv6 unicast
network 2001:DB8::/64
C. router bgp 64900
no bgp default ipv4-unicast
address-family ipv6 multicast
neighbor 2001:DB8:7000::2 translate-update ipv6 multicast
D. router bgp 64900
no bgp default ipv4-unicast
address-family ipv6 unicast
redistribute ospf
network 2001:DB9::/64
QUESTION 91
Refer to the exhibit.
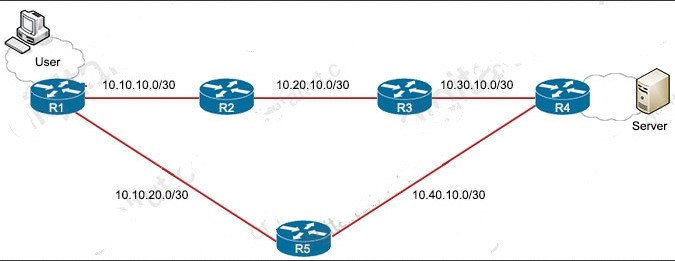
R1#show ip route
1.0.0.0/32 is subnetted, 1 subnets
C 1.1.1.1/32 is directly connected, Loopback0
2.0.0.0/32 is subnetted, 1 subnets
O 2.2.2.2/32 [110/2] via 10.10.10.2, 00:09:30, GigabitEthernet0/0/0
10.0.0.0/8 is variably subnetted, 7 subnets, 2 masks
C 10.10.10.0/30 is directly connected, GigabitEthernet0/0/0 L 10.10.10.1/32 is directly connected, GigabitEthernet0/0/0
C 10.10.20.0/30 is directly connected, GigabitEthernet0/0/1
L 10.10.20.1/32 is directly connected, GigabitEthernet0/0/1
D 10.20.10.0/30 [90/3072] via 10.10.10.2, 00:09:30, GigabitEthernet0/0/0
O 10.30.10.0/30 [90/3328] via 10.10.10.2, 00:05:48, GigabitEthernet0/0/0
S 10.40.10.0/30 [1/0] via 10.10.20.2
Routers R1, R2, R3, and R4 use EIGRP. However, traffic always prefers R1 to R5 backup links in non failure scenarios. Which configuration resolves the issue?
A. R1(config)#no ip route 10.40.10.0 255.255.255.252 10.10.20.2
R1(config)#ip route 10.40.10.0 255.255.255.252 10.10.20.2 115
B. R1(config)#int gigabitEthernet 0/0/0
R1 (config-if)#bandwidth 10000000
C. R1(config-if)#int gigabitEthernet 0/0/0
R1(config-if)#bandwidth 10000
D. R1(config)#no ip route 10.40.10.0 255.255.255.252 10.10.20.2
R1(config)#ip route 0.0.0.0 0.0.0.0 10.10.10.2
QUESTION 92
A newly installed spoke router is configured for DMVPN with the ip mtu 1400 command. Which configuration allows the spoke to use fragmentation with the maximum negotiated TCP MTU over GRE?
A. ip tcp adjust-mss 1360 crypto ipsec fragmentation after-encryption
B. ip tcp adjust-mss 1360 crypto ipsec fragmentation mtu-discovery
C. ip tcp payload-mtu 1360 crypto ipsec fragmentation mtu-discovery
D. ip tcp payload-mtu 1360 crypto ipsec fragmentation after-encryption
QUESTION 93
Refer to the exhibit.

An engineer is trying to add an encrypted user password that should not be visible in the router configuration. Which two configuration commands resolve the issue? (Choose two)
A. service password-encryption
B. username Admin password 5 Cisco@123
C. no service password-encryption
D. username Admin password Cisco@123
E. password encryption aes
F. username Admin secret Cisco@123
QUESTION 94
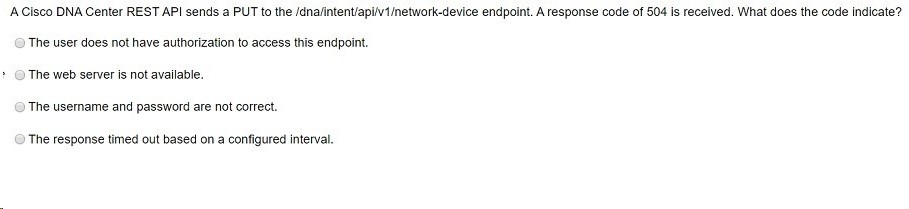
QUESTION 95

QUESTION 96

New Questions 2
QUESTION 1
Refer to the exhibit.
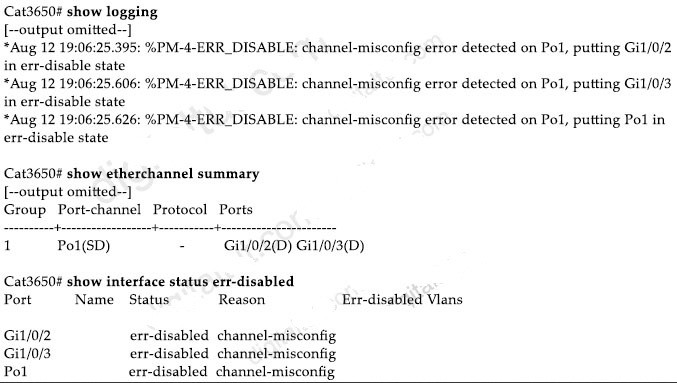
The administrator troubleshoots an Etherchannel that keeps moving to err-disabled. Which two actions must be taken to resolve the issue? (Choose two)
A. Reload the switch to force EtherChannel renegotiation
B. Ensure that interfaces Gi1/0/2 and Gi1/0/3 connect to the same neighboring switch
C. Ensure that the neighbor interfaces of Gi1/0/2 and Gi1/0/3 are configured as members of the same EtherChannel
D. Ensure that the corresponding port channel interface on the neighbor switch is named Port-channel1
E. Ensure that the switchport parameters of Port-channel 1 match the parameters of the port channel on the neighbor switch
QUESTION 2
Drag and drop the snippets onto the blanks within the code to construct a script that shows all logging that occurred on the appliance from Sunday until 9:00 p.m Thursday. Not all options are used.
Select and Place:
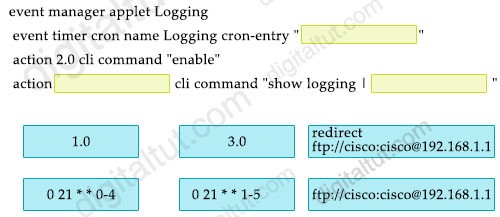
QUESTION 3
Drag and drop the characteristics from the left onto the infrastructure deployment models on the right.
Select and Place:
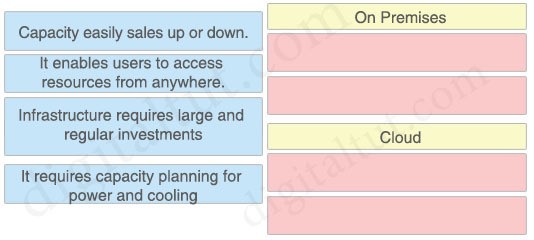
QUESTION 4
Which definition describes JWT in regard to REST API security?
A. an encrypted JSON token that is used for authentication
B. an encrypted JSON token that is used for authorization
C. an encoded JSON token that is used to securely exchange information
D. an encoded JSON token that is used for authentication
QUESTION 5
Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
Select and Place:
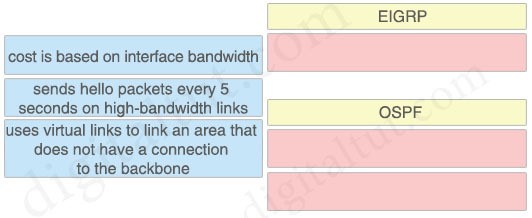
QUESTION 6
What happens when a FlexConnect AP changes to standalone mode?
A. All controller dependent activities stops working except DFS
B. Only clients on central switching WLANs stay connected
C. All clients roaming continues to work
D. All clients on all WLANs are disconnected
QUESTION 7
Which two Cisco SD-Access components provide communication between traditional network elements and controller layer? (Choose two)
A. network data platform
B. network underlay
C. fabric overlay
D. network control platform
E. partner ecosystem
QUESTION 8
What is one difference between EIGRP and OSPF?
A. OSPF is a Cisco proprietary protocol, and EIGRP is an IETF open standard protocol.
B. EIGRP uses the DUAL distance vector algorithm, and OSPF uses the Dijkstra link-state algorithm
C. EIGRP uses the variance command lot unequal cost load balancing, and OSPF supports unequal cost balancing by default
D. OSPF uses the DUAL distance vector algorithm, and EIGRP uses the Dijkstra link-state algorithm
QUESTION 9
Which function does a fabric wireless LAN controller perform in a Cisco SD-Access deployment?
A. performs the assurance engine role for both wired and wireless clients
B. coordinates configuration of autonomous nonfabric access points within the fabric
C. manages fabric-enabled APs and forwards client registration and roaming information to the Control Plane Node
D. is dedicated to onboard clients in fabric-enabled and nonfabric-enabled APs within the fabric
QUESTION 10
Drag and drop the characteristics from the left onto the orchestration tools that they describe on the right.
Select and Place:
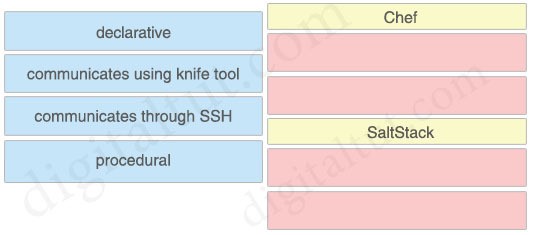
QUESTION 11
Refer to the exhibit.

An engineer must set up connectivity between a campus aggregation layer and a branch office access layer. The engineer uses dynamic trunking protocol to establish this connection, however, management traffic on VLAN1 is not passing. Which action resolves the issue and allow communication for all configured VLANs?
A. Allow all VLANs on the trunk links
B. Disable Spanning Tree for the native VLAN
C. Change both interfaces to access ports
D. Configure the correct native VLAN on the remote interface
QUESTION 12
How must network management traffic be treated when defining QoS policies?
A. as delay-sensitive traffic in a low latency queue
B. using minimal bandwidth guarantee
C. using the same marking as IP routing
D. as best effort
QUESTION 13
Refer to the exhibit.

Which command set is needed to configure and verify router R3 to measure the response time from router R3 to the file server located in the data center?
A. ip sla 6 icmp-echo 172.29.139.134 source-ip 172.29.139.132 frequency 300
ip sla schedule 6 start-time now
show ip protocol
B. ip sla 6 icmp-echo 172.29.139.134 source-ip 172.29.139.132 frequency 300
ip sla schedule 6 start-time now
C. ip sla 6 icmp-echo 10.0.1.3 source-ip 10.0.0.3 frequency 300
ip sla schedule 6 life forever start-time now
show ip sla statistics 6
D. ip sla 6 icmp-echo 10.0.1.3 source-ip 10.0.0.3 frequency 300
ip sla schedule 6 life forever start-time now
show ip protocol
QUESTION 14
What are the main components of Cisco TrustSec?
A. Cisco ISE and Enterprise Directory Services
B. Cisco ISE, network switches, firewalls, and routers
C. Cisco ISE and TACACS+
D. Cisco ASA and Cisco Firepower Threat Defense
QUESTION 15
Refer to the exhibit.

What is the result of the API request?
A. The information for all interfaces is read from the network appliance
B. The native interface information is read from the network appliance
C. The “params” variable sends data fields to the network appliance
D. The “params” variable reads data fields from the network appliance
QUESTION 16
What is a TLOC in a Cisco SD-WAN deployment?
A. value that identifies a specific tunnel within the Cisco SD-WAN overlay
B. identifier that represents a specific service offered by nodes within the Cisco SD-WAN overlay
C. attribute that acts as a next hop for network prefixes
D. component set by the administrator to differentiate similar nodes that offer a common service
QUESTION 17
Which Cisco FlexConnect state allows wireless users that are connected to the network to continue working after the connection to the WLC has been lost?
A. Authentication Down/Switching Down
B. Authentication-Central/Switch-Local
C. Authentication-Down/Switch-Local
D. Authentication-Central/Switch-Central
QUESTION 18
Refer to the exhibit.
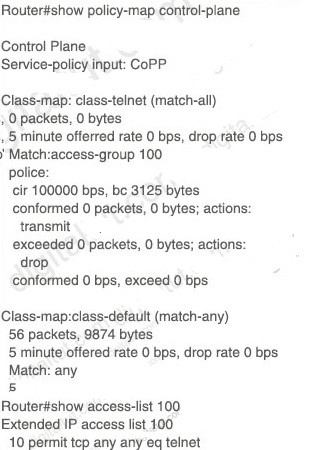
Which commands are required to allow SSH connection to the router?
A. Router(config)#access-list 10 permit tcp any eq 22 any
Router(config)#class-map class-ssh
Router(config-cmap)#match access-group 10
Router(config)#policy-map CoPP
Router(config-pmap)#class class-ssh
Router(config-pmap-c)#police 100000 conform-action transmit
B. Router(config)#access-list 100 permit udp any any eq 22
Router(config)#access-list 101 permit tcp any any eq 22
Router(config)#class-map class-ssh
Router(config-cmap)#match access-group 101
Router(config)#policy-map CoPP
Router(config-pmap)#police 100000 conform-action transmit
C. Router(config)#access-list 100 permit tcp any eq 22 any
Router(config)#class-map class-ssh
Router(config-cmap)#match access-group 10
Router(config)#policy-map CoPP
Router(config-pmap)#class class-ssh
Router(config-pmap-c)#police 100000 conform-action transmit
D. Router(config)#access-list 100 permit tcp any any eq 22 Router(config)#access-list 101 permit tcp any any eq 22 Router(config)#class-map class-ssh
Router(config-cmap)#match access-group 101
Router(config)#policy-map CoPP
Router(config-pmap)#class class-ssh
Router(config-pmap-c)#police 100000 conform-action transmit
QUESTION 19
Refer to the exhibit.
An engineer must configure and validate a CoPP policy that allows the network management server to monitor router R1 via SNMP while protecting the control plane. Which two commands or command sets must be used? (Choose two)
A. show quality-of-service-profile
B. show ip interface brief
C. access-list 150 permit udp 10.0.1.4 0.0.0.0 host 10.0.1.2 eq snmp
class-map match-all CoPP-management
match access-group 150
policy-map CoPP-policy
class CoPP-management
police 8000 conform-action transmit exceed-action transmit violate-action transmit
control-plane
service-policy input CoPP-policy
D. show policy-map control-plane
QUESTION 20
How do EIGRP metrics compare to OSPF metrics?
A. The EIGRP administrative distance for external routes is 170, and the OSPF administrative distance for external routes is 110
B. EIGRP uses the Dijkstra algorithm, and OSPF uses The DUAL algorithm
C. The EIGRP administrative distance for external routes is 170, and the OSPF administrative distance for external routes is undefined
D. EIGRP metrics are based on a combination of bandwidth and packet loss, and OSPF metrics are based on interface bandwidth
QUESTION 21
A network engineer is configuring OSPF on a router. The engineer wants to prevent having a route to 177.16.0.0/16 learned via OSPF. In the routing table and configures a prefix list using the command ip prefix-list OFFICE seq 5 deny
172.16.0.0/16. Which two identical configuration commands must be applied to accomplish the goal? (Choose two)
A. distribute-list prefix OFFICE in under the OSPF process
B. ip prefix-list OFFICE seq 10 permit 0.0.0.0/0 le 32
C. ip prefix-list OFFICE seq 10 permit 0.0.0.0/0 ge 32
D. distribute-list OFFICE out under the OSPF process
E. distribute-list OFFICE in under the OSPF process
QUESTION 22
Which two features does the Cisco SD-Access architecture add to a traditional campus network? (Choose two)
A. private VLANs
B. software-defined segmentation
C. SD-WAN
D. identity services
E. modular QoS
QUESTION 23
Which feature is used to propagate ARP broadcast, and link-local frames across a Cisco SD-Access fabric to address connectivity needs for silent hosts that require reception of traffic to start communicating?
A. Native Fabric Multicast
B. Layer 2 Flooding
C. SOA Transit
D. Multisite Fabric
QUESTION 24
An engineer must configure a new loopback interface on a router and advertise the interface as a /24 in OSPF. Which command set accomplishes this task?
A. R2(config)#interface Loopback0
R2(config-if)#ip address 172.22.2.1 255.255.255.0
R2(config-if)#ip ospf 100 area 0
B. R2(config)#interface Loopback0
R2(config-if)#ip address 172.22.2.1 255.255.255.0
R2(config-if)#ip ospf network broadcast
R2(config-if)#ip ospf 100 area 0
C. R2(config)#interface Loopback0
R2(config-if)#ip address 172.22.2.1 255.255.255.0
R2(config-if)#ip ospf network point-to-multipoint
R2(config-if)#router ospf 100
R2(config-router)#network 172.22.2.0 0.0.0.255 area 0
D. R2(config)#interface Loopback0
R2(config-if)#ip address 172.22.2.1 255.255.255.0
R2(config-if)#ip ospf network point-to-point
R2(config-if)#ip ospf 100 area 0
QUESTION 25
What is one characteristic of the Cisco SD-Access control plane?
A. It stores remote routes in a centralized database server
B. Each router processes every possible destination and route
C. It allows host mobility only in the wireless network
D. It is based on VXLAN technology
QUESTION 26
An engineer must configure a router to leak routes between two VRFs. Which configuration must the engineer apply?
A.
B.
C.
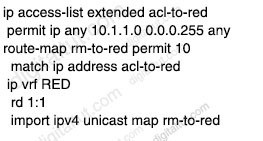
D.
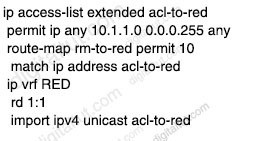
QUESTION 27
Refer to the exhibit.
restconf
!
ip http server ip http authentication local ip http secure-server
!
Which command must be configured for RESTCONF to operate on port 8888?
A. ip http port 8888
B. restconf port 8888
C. ip http restconf port 8888
D. restconf http port 8888
QUESTION 28
If the maximum power level assignment for global TPC 802.11a/n/ac is configured to 10 dBm, which power level effectively doubles the transmit power?
A. 13dBm
B. 14dBm
C. 17dBm
D. 20dBm
QUESTION 29
Which benefit is realized by implementing SSO?
A. IP first-hop redundancy
B. communication between different nodes for cluster setup
C. physical link redundancy
D. minimal network downtime following an RP switchover