Free Cisco Dump, Free Dumps
Free 200-901 DEVASC Dump
Question #280
Which protocol is used for clock synchronization between network devices?
- A. FTP
- B. NNTP
- C. BGP
- D. NTP
Correct Answer: D
Question #281
What is the meaning of the HTTP status code 204?
- A. request completed; new resource created
- B. server successfully processed request; no content returned
- C. standard response for successful requests
- D. invalid query parameters
Correct Answer: B
Question #282
Which two commands download and execute an Apache web server container in Docker with a port binding 8080 in the container to 80 on the host? (Choose two.)
- A. docker pull apache
- B. docker run –p 8080:80 httpd
- C. docker run –p 80:8080 httpd
- D. docker pull httpd
- E. docker pull https
Correct Answer: DC
Question #283
A group of software developers wants to improve its collaboration with the operations team. The group wants to deliver release-ready code that merges code changes back to the main branch and runs the automated testing as often as possible. Which DevOps concept does this scenario represent?
- A. continuous delivery
- B. version control
- C. continuous integration
- D. continuous deployment
Correct Answer: C
Question #284
A developer is running an application that connects to the Cisco website and collects data. The application will be hosted in a local data center and the data will need to be collected on a frequent basis. The application client requires certain environmental variables to be set before the run. Which Bash command sets the environmental variables for a Linux system?
- A.

- B.
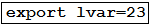
- C.
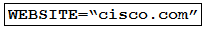
- D.
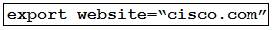
Correct Answer: D
Question #285
DRAG DROP
–
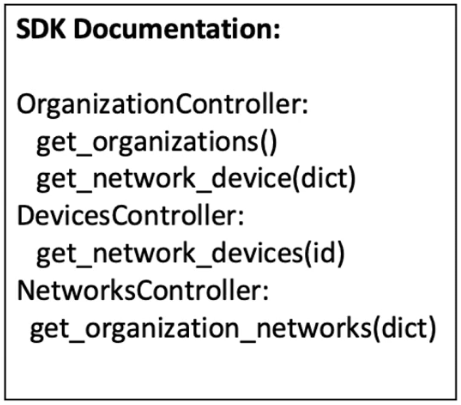
Refer to the exhibit. A script must output details of all the Cisco Meraki MS220-BP switches across all organizations and networks. Drag and drop the code snippets from the bottom onto the boxes in the code to complete the script. Not all options are used.
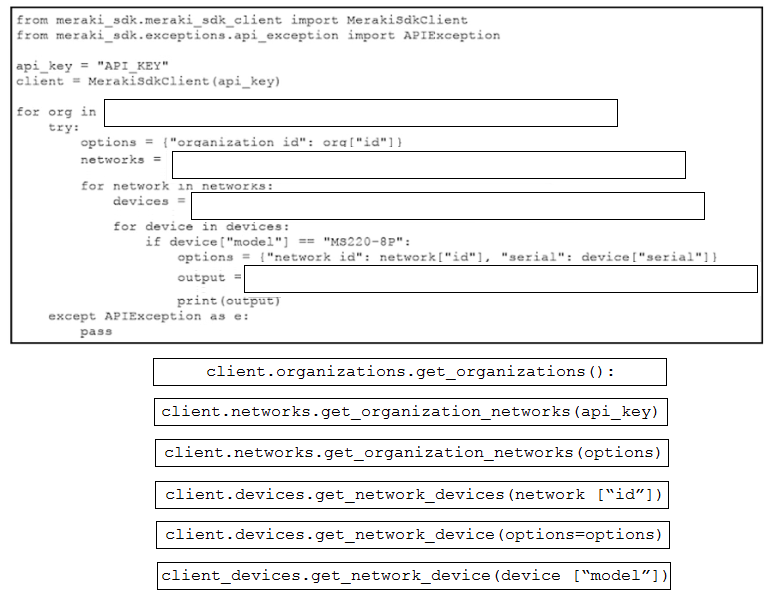
Correct Answer: 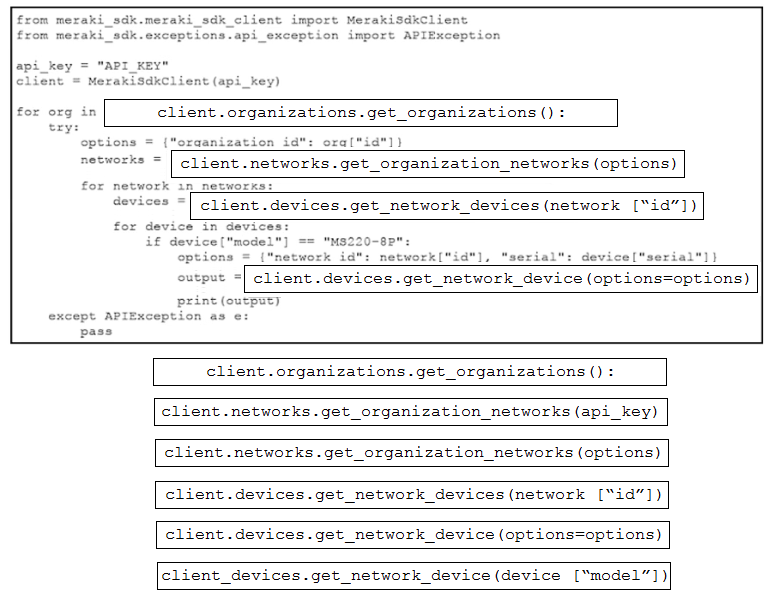
Question #286
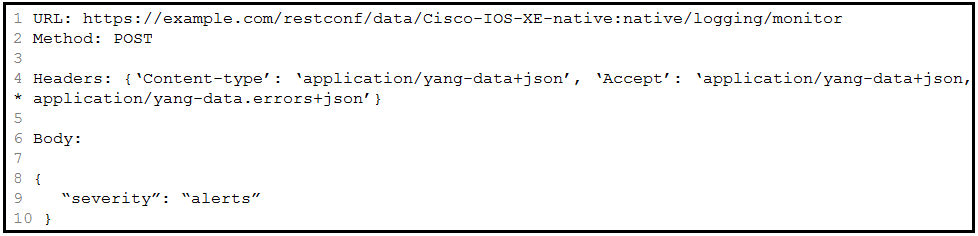
Refer to the exhibit. Which HTTP code is returned after the RESTCONF query is executed?
- A. 201
- B. 204
- C. 302
- D. 304
Correct Answer: A
Question #287
DRAG DROP
–
Drag and drop the code snippets from the bottom onto the blanks in the code to complete the happy path scenario. Not all options are used.
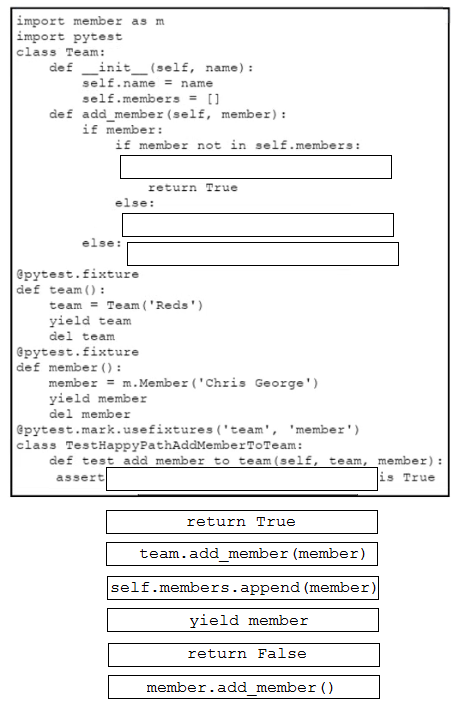
Correct Answer: 
Question #288
Which traffic is handled on the control plane?
- A. BGP
- B. SMB
- C. NTP
- D. NETCONF
Correct Answer: A
Question #289
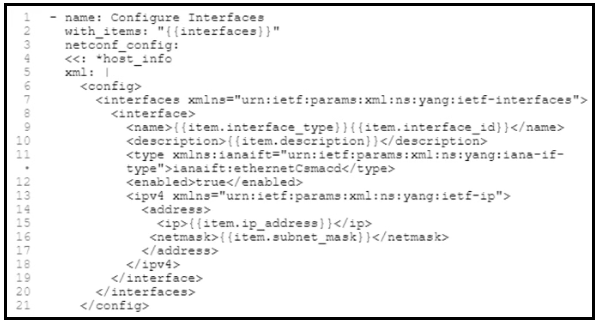
Refer to the exhibit. A network engineer must configure new interfaces on a set of devices and is planning to use an Ansible playbook for the task. All devices support SSH and NETCONF protocol, and the interface variables are unique per device. In which directory are the YAML files including variables hosted to automate the task with the netconf_config module?
- A. current working directory
- B. host_vars directory
- C. group_vars directory
- D. home directory
Correct Answer: A
Question #290
Which standard supported by Cisco IOS XE and Cisco NX-OS is used for automating the configuration of multiple devices across a network?
- A. SNMP – YANG
- B. SYSLOG – YANG
- C. CLI – YANG
- D. NETCONF – YANG
Correct Answer: D
Question #291
A developer has addressed a bug that was found in the production code of an application. A separate file named ‘bug427896191v_fix” has been created with the changes to the code. Which Git command must be used to incorporate the bug fix into the production code?
- A. git rebase
- B. git cat-file
- C. git merge-file
- D. git bisert
Correct Answer: C
Question #292
What is a principle of a code review process?
- A. Changes are made after the code is submitted to source control.
- B. It must not prevent code from getting into production as quickly as possible.
- C. Naming standards must be consistent.
- D. A technical lead must sign off on the review.
Correct Answer: D
Question #293
Why would a developer compare a current version of code to a previous version?
- A. to provide the single source of truth
- B. to troubleshoot code failures
- C. to track who made a change
- D. to aid in collaboration
Correct Answer: B
Question #294
Which Cisco platform is used to manage data center infrastructure through third-party tools and system integrations?
- A. Cisco DNA Center
- B. Cisco UCS Manager
- C. Cisco Intersight
- D. Cisco UCS Director
Correct Answer: D
Question #295
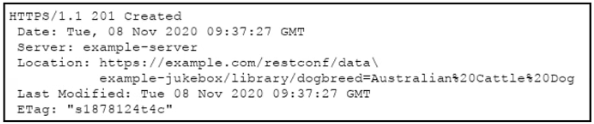
Refer to the exhibit. Which RESTCONF request results in this response?
- A.
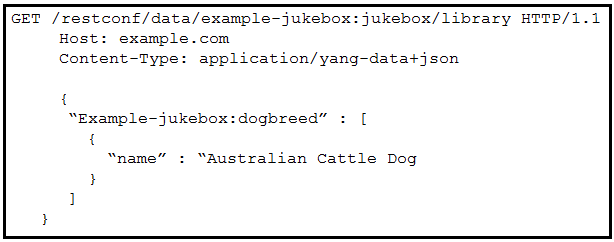
- B.
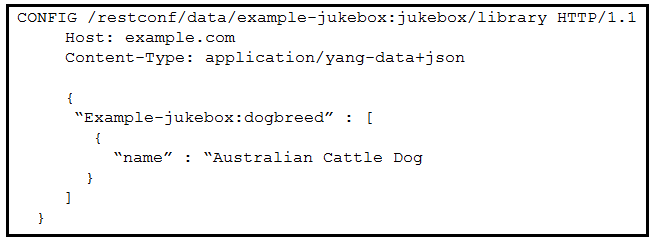
- C.

- D.

Correct Answer: D
Question #296
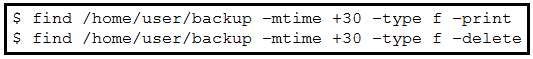
Refer to the exhibit. An engineer is managing the network of an enterprise. The network is using a distributed deployment model. The enterprise uses database to store logs. The current policy requires logs to be stored if changes are made to the infrastructure in any of the devices on the data centers. Which workflow is being automated by the Bash script?
- A. returning backup files that are older than 30 days
- B. deleting backup files that are older than 30 days
- C. configuring the directory to delete files automatically
- D. automating deletion of all backup files every 30 days
Correct Answer: B
Question #297
DRAG DROP
–
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a list of network devices from Cisco DNA Center. Not all options are used.
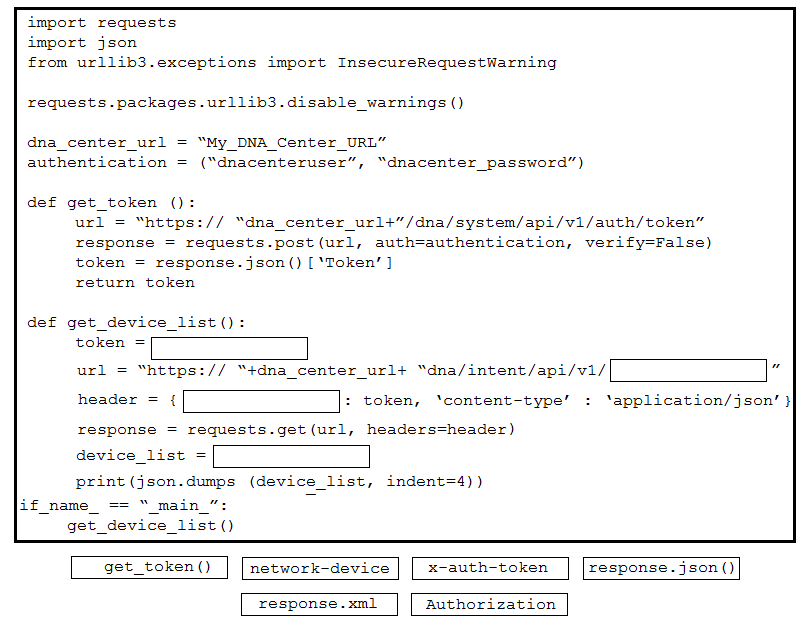
Correct Answer: 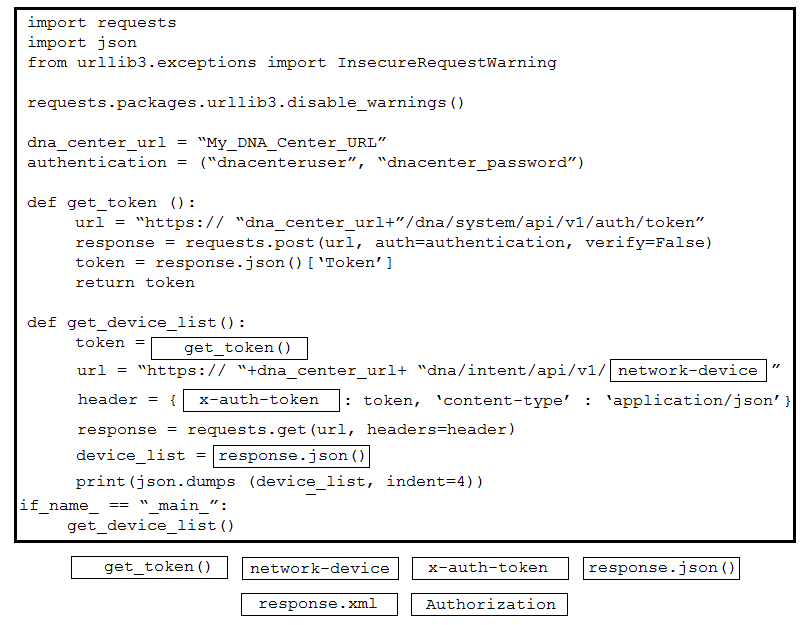
Question #298
What is a characteristic of RPC APIs compared to REST APIs?
- A. Authentication is done over provisions for the service caller and vice versa for RPC API, and REST API uses HTTP headers for authentication.
- B. All communications between the client and server must be stateless for RPC API, and REST API is stateful.
- C. The architecture model for RPC API is resource-focused, and REST API is procedure-focused.
- D. The data payload must be in JSON format for RPC API, and REST API allows JSON and XML formats.
Correct Answer: A
Question #299
Which two situations align with infrastructure as code principles? (Choose two.)
- A. nonreplicable snowflake servers
- B. release versions to specific hardware
- C. maximized configuration drift
- D. easily reproducible systems
- E. repeatable processes
Correct Answer: BD
Question #300
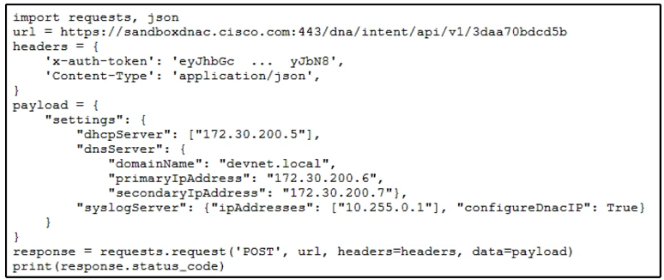
Refer to the exhibit. A developer writes a script to create a new network by using the Cisco DNA Center API. After running the script for the first time, the developer observes that HTTP code 404 is printed to the console. Which action resolves the problem?
- A. The x-auth-token value must be changed to a valid token.
- B. The API URL must be changed with a valid URL.
- C. The requested payload must be fixed to include missing parts.
- D. Internal errors on the code of API server must be fixed.
Correct Answer: B
Question #301
A developer plans to deploy a new application that will use an API to implement automated data collection from Webex with these requirements:
• The application was created by using the request library.
• Requires HTTP basic authentication.
• Provides data in JSON or XML formats.
Which Cisco DevNet resource helps the developer with how to use the API?
- A. DevNet sandbox
- B. API documentation
- C. forums
- D. DevNet code exchange
Correct Answer: B
Question #302
An engineer deploys a Cisco CSR 1000 V instance to a virtual machine. The engineer must output the device configuration in JSON format. Which protocol is used for this task?
- A. YANG
- B. NETCONF
- C. SNMP
- D. RESTCONF
Correct Answer: D
Question #303
What are two benefits of implementing common data structures when working with APIs in remote systems? (Choose two.)
- A. ensures that developers are limited to using one data schema type
- B. prevents multivendor interoperability
- C. improves security in RESTful web services
- D. enforces standardized data structures
- E. leverages code that is easily managed and reused
Correct Answer: BE
Question #304
A development team is creating an application used for contactless payments. The application must:
• Be web-based
• Capture and process the credit card information for a purchase.
Which security action must the web application use to gather and process the private customer data?
- A. Enable RATs to monitor the web application remotely.
- B. Disable botnets to eliminate risks.
- C. Disable TLS to increase the connection speed.
- D. Enable the encryption of network traffic.
Correct Answer: D
Question #305
An engineer needs to collect information about 20,000 Bluetooth clients using the Cisco Meraki API. The API returns only 1,000 results. One of the HTTP response headers has the data:
Link: https://api.meraki.com.info/api/v0/networks/ABC/bluetoothClients?perPage=1000&startingAfter=1000>;rel=“next”
Which RFC is implemented by the API to apply the restriction?
- A. RFC 5988 – Web Linking
- B. RFC 5890 – Response Constraints
- C. RFC 5005 – Feed Paging and Archiving
- D. RFC 5446 – Content Limits
Correct Answer: C
Question #306
What are two benefits of using classes over functions when writing applications? (Choose two.)
- A. improved readability
- B. increased compatibility
- C. variable reusability
- D. increased performance
- E. code organization
Correct Answer: AC
Question #307
DRAG DROP
–
Drag and drop the steps from the left into order on the right to create a common CI/CD pipeline process. Not all options are used.
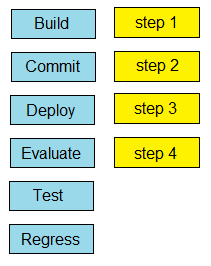
Correct Answer: 
Question #308
DRAG DROP
–
Drag and drop the code from the bottom onto the box where the code is missing to obtain a list of network devices by using the Cisco Meraki API. Not all options are used.
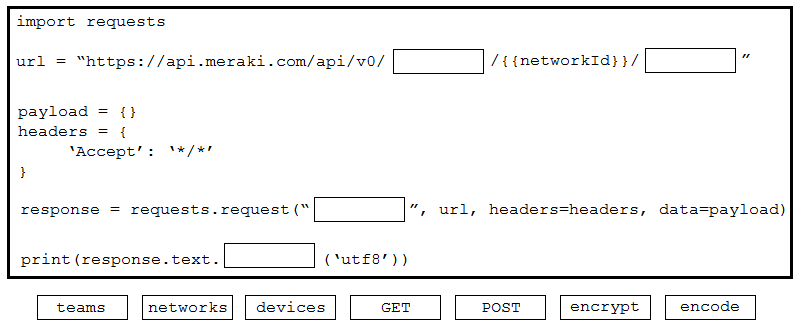
Correct Answer: 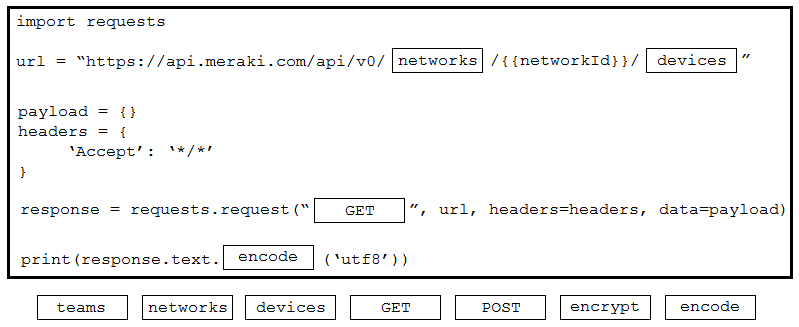
Question #309
A developer creates a new application, but the application must be tested before being released to a customer. When a mobile phone that uses 4G is used to access the application, the request fails. Why does the connection to the application fail?
- A. The application is hosted on premises and VPN connectivity is required
- B. The application must be added to the production server before testing.
- C. The application must be moved to the cloud before testing is possible.
- D. The application connectivity is limited to HTTPS protocol.
Correct Answer: A
Question #310
Which platform has an API that has the capability to obtain a list of vulnerable software on user devices?
- A. Cisco Advanced Malware Protection
- B. Cisco Umbrella
- C. Cisco Identity Services Engine
- D. Cisco Firepower
Correct Answer: A
Question #311
A developer creates an application that must provide an encrypted connection or API keys. The keys will be used to communicate with a REST API. Which command must be used for the secure connection?
- A. curl –X PUSH ‘http://username.app.com/endpoint/?api_key=12345abcdef’
- B. curl –v ‘ftp://username.app.com/endpoint/?api_key=12345abcdef’
- C. curl –X GET ‘https://username.app.com/endpoint/?api_key=12345abcdef’
- D. curl –X GET ‘http://username.app.com/endpoint/?api_key=12345abcdef’
Correct Answer: C
Question #312
A developer is developing a web application that uses username and password to authenticate to the next service. The user credentials must be available at any time in the application. The developer must choose and implement a secure method of storing the authentication credentials that are used in the automation code. Which password handling method must be used to minimize the security risk?
- A. Store the username and password in a separate configuration file.
- B. Store the username and password in a vault.
- C. Store the passwords in a dictionary.
- D. Store the username and password in code.
Correct Answer: B
Question #313
What is a capability of the AXL API?
- A. It signs a user in to a phone that is configured for extension mobility.
- B. It pulls logs for the Cisco Tomcat service.
- C. It authenticates users who exist in Cisco Unified Communications Manager.
- D. It provides support for HTTP and HTTPS communications.
Correct Answer: C
Question #314
A developer creates a program in which an object maintains a list of classes based on the observer pattern. The classes are dependent on the object. Whenever the state of the object changes, it notifies the dependent classes directly through callbacks. Which advantage of the observer pattern offers minimum dependencies and maximum flexibility between dependent objects or classes?
- A. tight coupling
- B. cohesion
- C. mediation
- D. loose coupling
Correct Answer: D
Question #315
What is a feature of XML compared to other data formats?
- A. It uses tags to define the structure.
- B. It uses parenthesis for key-value pairs.
- C. It uses indentation to define the structure.
- D. It uses namespaces for list representation.
Correct Answer: A
Question #316
DRAG DROP
–

Refer to the exhibit. Drag and drop the actions from the left that the contents of this Dockerfile accomplish onto the right. Not all options are used.
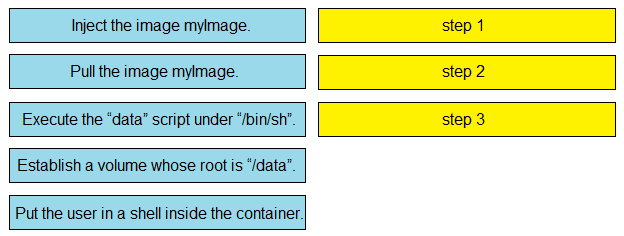
Correct Answer: 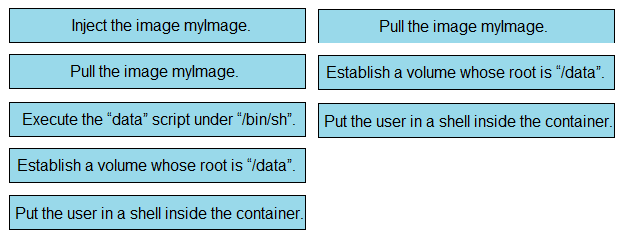
Question #317
What is a capability of Ansible playbooks?
- A. They execute scheduled tasks regularly.
- B. They define the state for a device configuration.
- C. They collect SNMP logs from networking devices.
- D. They utilize the target device agent to execute.
Correct Answer: A
Question #318
DRAG DROP –
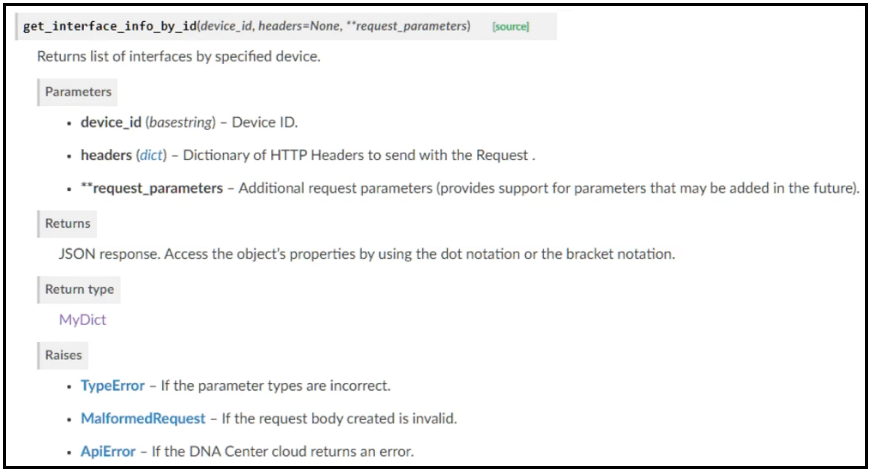
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to return the number of interfaces on a network device by using the Cisco DNA Center SDK. Not all options are used.
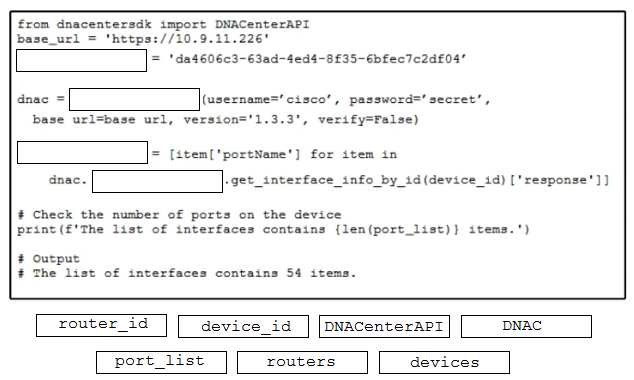
Correct Answer: 1: Device_id
2: DNACenterApi
3: port_list
4: devices
Question #319
What is the purpose of running tests before writing code in test-driven development?
- A. to find unexpected failures in the tests
- B. to demonstrate that the tests fail for expected reasons
- C. to ensure that the tests pass
- D. to provide proof of the work carried out
Correct Answer: D

