Free Cisco Dump, Free Dumps
Free 200-901 DEVASC Dump
Question #240
DRAG DROP –
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right. Not all options are used.
Select and Place:

Correct Answer: 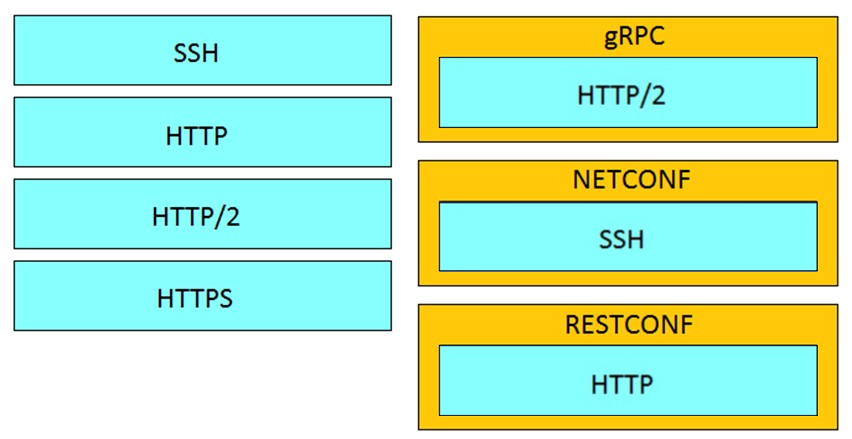
Reference:
https://www.ciscolive.com/c/dam/r/ciscolive/apjc/docs/2017/pdf/BRKSDN-2119.pdf slide 49
Question #241
Which detail is included in a routing table?
- A. broadcast address
- B. TCP or UDP port number
- C. IP protocol
- D. destination next hop or outgoing interface
Correct Answer: D
Reference:
https://geek-university.com/ccna/routing-table-explained/
Community vote distribution
D (100%)
Question #242
What is an example of a network interface hardware address?
- A. workstation name
- B. IP address
- C. domain name
- D. MAC address
Correct Answer: D
Community vote distribution
D (100%)
Question #243
DRAG DROP –
Drag and drop the functionalities from the left onto the correct networking devices on the right.
Select and Place:
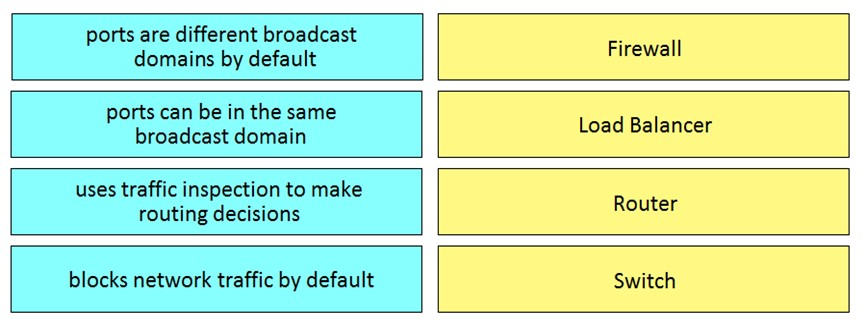
Correct Answer: 
Reference:
https://geek-university.com/ccna/broadcast-domain-explained/
Question #244
On which network plane is routing protocol traffic handled?
- A. management plane
- B. data plane
- C. authentication plane
- D. control plane
Correct Answer: D
Reference:
https://tools.cisco.com/security/center/resources/understanding_cppr
Community vote distribution
D (100%)
Question #245
Which device is used to transport traffic from one broadcast domain to another broadcast domain?
- A. layer 2 switch
- B. proxy server
- C. router
- D. load balancer
Correct Answer: C
Community vote distribution
C (100%)
Question #246
Which service provides a directory lookup for IP addresses and host names?
- A. DNS
- B. NAT
- C. SNMP
- D. DHCP
Correct Answer: A
Community vote distribution
A (100%)
Question #247
Users cannot access a webserver and after the traffic is captured, the capture tool shows an ICMP packet that reports “time exceeded in-transit”. What is the cause of this webserver access issue?
- A. A router along the path has the wrong time.
- B. A router along the path is misrouting the packets in a wrong direction.
- C. The server is too loaded and the connection could not be handled in time.
- D. The server is too far away and the packets require too much time to reach it.
Correct Answer: B
Community vote distribution
B (60%)
D (40%)
Question #248
What is used in Layer 2 switches to direct packet transmission to the intended recipient?
- A. MAC address
- B. IPv6 address
- C. spanning tree
- D. IPv4 address
Correct Answer: A
Community vote distribution
A (100%)
Question #249
What is the purpose of a firewall in application deployment?
- A. adds TLS support to an application that does not support it natively
- B. limits traffic to only ports required by the application
- C. provides translation for an application’s hostname to its IP address
- D. forwards traffic to a pool of instances of the application
Correct Answer: B
Community vote distribution
B (100%)
Question #250
A small company has 5 servers and 50 clients. What are two reasons an engineer should split this network into separate client and server subnets? (Choose two.)
- A. Subnets will split domains to limit failures.
- B. A router will limit the traffic types between the clients and servers.
- C. Subnets provide more IP address space for clients and servers.
- D. A router will bridge the traffic between clients and servers.
- E. Internet access to the servers will be denied on the router.
Correct Answer: AB
Community vote distribution
AC (50%)
AB (25%)
Question #251
What is the function of an IP address in networking?
- A. represents a network connection on specific devices
- B. specifies the type of traffic that is allowed to roam on a network
- C. specifies resource’s location and the mechanism to retrieve it
- D. represents the unique ID that is assigned to one host on a network
Correct Answer: D
Community vote distribution
D (100%)
Question #252
Where is an IP packet routed if the packet does not match any routes in the routing table?
- A. firewall
- B. load balancer
- C. central switch
- D. default gateway
Correct Answer: D
Community vote distribution
D (100%)
Question #253
Which two query types does a client make to a DNS server? (Choose two.)
- A. Inverse
- B. PTR
- C. AAAA
- D. ACK
- E. DISCOVER
Correct Answer: BC
Community vote distribution
BC (100%)
Question #254
What are two functions of a routing table on a network device? (Choose two.)
- A. It lists the routes to drop traffic.
- B. It lists the routes to a particular destination.
- C. It lists the static and dynamic entries.
- D. It lists hosts that are one hop away.
- E. It lists entries more than two hops away.
Correct Answer: BC
Community vote distribution
BC (75%)
B (25%)
Question #255
What does a load balancer distribute in a network environment?
- A. different TCP connections to the routers
- B. incoming traffic across multiple servers
- C. traffic in the network by leveraging the switch architecture
- D. outgoing connections to the network
Correct Answer: B
Community vote distribution
B (100%)
Question #256
Refer to the exhibit.
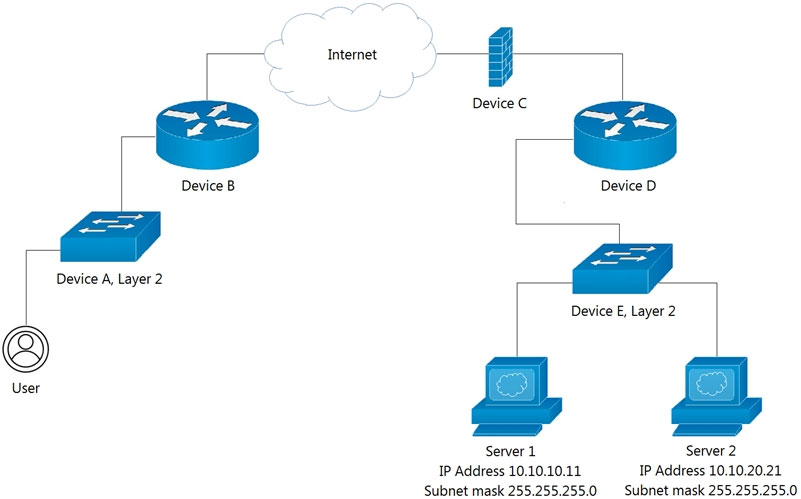
Which Device limits traffic between Server 1 and Server 2?
- A. Device B
- B. Device C
- C. Device D
- D. Device E
Correct Answer: C
Community vote distribution
C (57%)
D (43%)
Question #257
What is the purpose of a MAC address on a network device?
- A. unique network address that identifies the network interface of a device
- B. unique network interlace address that is provided by the DHCP server
- C. unique hardware address that identifies the network interface of a device
- D. unique hardware interface address that is provided by the central switch
Correct Answer: C
Community vote distribution
C (100%)
Question #258
How are load balancers used in modern application deployments?
- A. Turn off traffic and take down compute units, then update and bring the compute units back up.
- B. Allow traffic to continue as new compute units are brought up and old compute units are taken down.
- C. Allow HTTP and HTTPS traffic to continue as old compute units are discontinued before new units are brought up.
- D. Bring up new compute units, test the compute units, and switch the traffic from old units to new units.
Correct Answer: B
Question #259
Which protocol must be allowed on the firewall so that NTP services work properly?
- A. TCP
- B. ICMP
- C. BGP
- D. UDP
Correct Answer: D
Reference:
https://www.cisco.com/c/en/us/support/docs/ip/network-time-protocol-ntp/108076-ntp-troubleshoot.html
Community vote distribution
D (100%)
Question #260
Which protocol runs over TCP port 22?
- A. SSH
- B. NETCONF
- C. HTTP
- D. Telnet
Correct Answer: A
Community vote distribution
A (100%)
Question #261
What is the purpose of the first three pairs of digits in a MAC address?
- A. defines packet forwarding priority sent or received by the adapter
- B. defines a routing identifier for the client
- C. indicates vendor of the network card or adapter
- D. indicates the IP address of the client in Hex
Correct Answer: C
Community vote distribution
C (100%)
Question #262
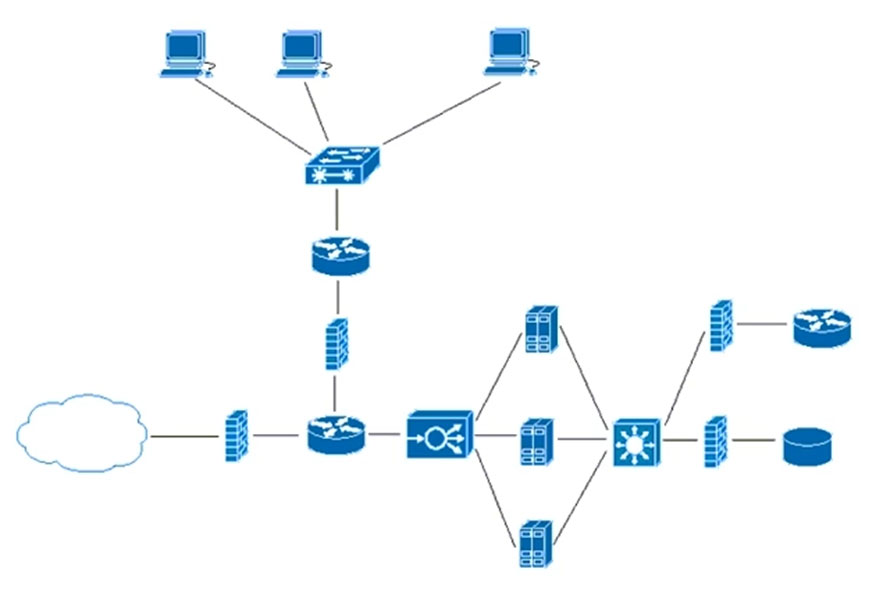
Refer to the exhibit. What does the load balancer enable in the network topology?
- A. hosted application to access Internet services
- B. external requests to be routed to the application servers
- C. application to access the database server
- D. workstations to access the Internet
Correct Answer: B
Community vote distribution
B (100%)
Question #263
What are two benefits of using VLANs? (Choose two.)
- A. limits the devices that can join the network
- B. enables the logical grouping of devices that belong to different Layer 2 devices
- C. segments the broadcast domain
- D. allows all network devices to be accessible from any host on the network
- E. extends the broadcast domain
Correct Answer: BC
Community vote distribution
BC (67%)
BE (33%)
Question #264
What are two considerations when selecting the `best route` for a network device to reach its destination? (Choose two.)
- A. MAC address
- B. IP address
- C. metrics
- D. administrative distance
- E. subnet mask
Correct Answer: CD
Community vote distribution
CD (63%)
DE (38%)
Question #265
DRAG DROP –
Drag and drop the function on the left onto the type of plane that handles the function on the right.
Select and Place:
Correct Answer: 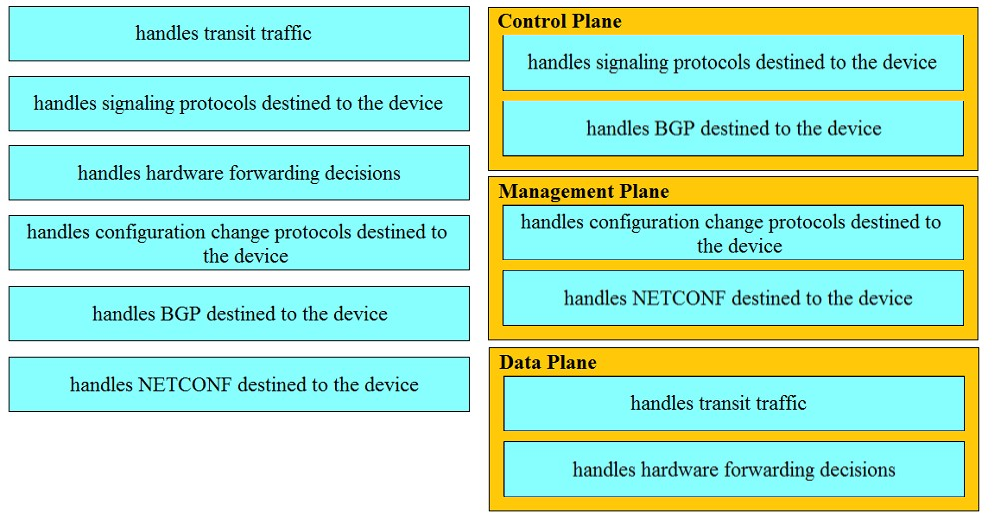
Question #266
Users cannot access a webserver and after the traffic is captured, the capture tool shows an ICMP packet that reports “communication administratively prohibited”. What is the cause of this webserver access issue?
- A. An access list along the path is blocking the traffic.
- B. Users must authenticate on the webserver to access it.
- C. A router along the path is overloaded and thus dropping traffic.
- D. The traffic is not allowed to be translated with NAT and dropped.
Correct Answer: A
Community vote distribution
A (100%)
Question #267
Which application should be used to externally access all applications deployed in the same host machine with a single public IP address and port, when each application listens on different local ports?
- A. reverse proxy
- B. load balancer
- C. DNS
- D. firewall
Correct Answer: B
Community vote distribution
A (59%)
D (29%)
12%
Question #268
Which implementation creates a group of devices on one or more LANs that are configured to communicate as if they were attached to the same wire?
- A. WLAN
- B. VLAN
- C. IPsec
- D. HSRP
Correct Answer: B
Community vote distribution
B (100%)
Question #269
What are two properties of private IP addresses? (Choose two.)
- A. They can be used to access the Internet directly.
- B. They are more secure than public IP addresses.
- C. They are not globally unique.
- D. They can be repeated within the same local network.
- E. They are controlled globally by an IP address registry.
Correct Answer: BC
Community vote distribution
BC (100%)
Question #270
Which protocol runs over TCP port 23?
- A. SSH
- B. NETCONF
- C. HTTP
- D. Telnet
Correct Answer: D
Community vote distribution
D (100%)
Question #271
Which two details are captured from the subnet mask? (Choose two.)
- A. portion of an IP address that refers to the subnet
- B. default gateway of the host
- C. unique number ID assigned to the host
- D. part of an IP address that refers to the host
- E. network connection of a host or interface
Correct Answer: AD
Community vote distribution
AD (100%)
Question #272
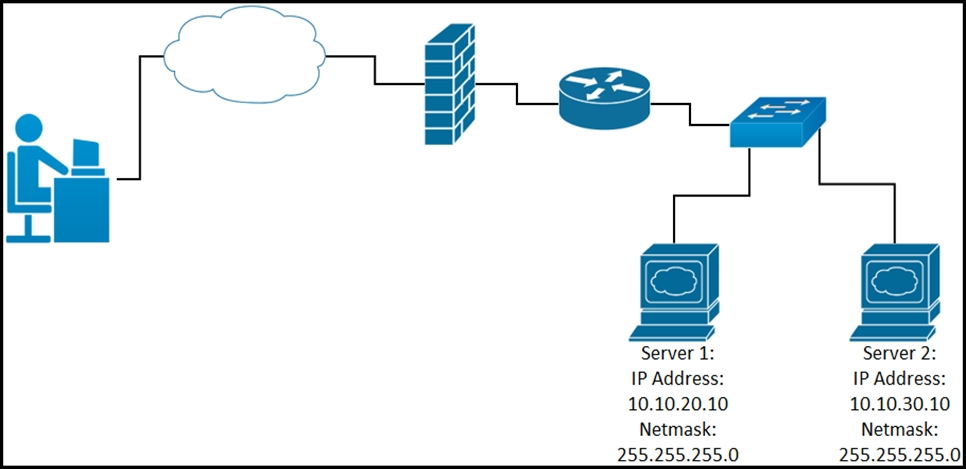
Refer to the exhibit. While developing a Cisco Webex bot, an application reaches the public IP address of the firewall, but traffic is forwarded to the IP address of server 1 instead of the IP address of server 2. What causes this issue?
- A. The proxy server that rewrites traffic is misconfigured.
- B. The router is sending the traffic to server 1 instead of server 2.
- C. The switch is forwarding IP traffic to the wrong VLAN.
- D. NAT is misconfigured on the firewall.
Correct Answer: D
Community vote distribution
D (100%)
Question #273
Developer is working on a new feature and made changes on a branch named ‘branch-413667549a-new’. When merging the branch to production, conflicts occurred. Which Git command must the developer use to recreate the pre-merge state?
- A. git merge ג€”no-edit
- B. git merge ג€”commit
- C. git merge ג€”revert
- D. git merge ג€”abort
Correct Answer: D
Community vote distribution
D (100%)
Question #274
A company wants to automate the orders processed on its website using API. The network device that supports the solution must:
• support XML encoding
• support distributed transactions
• support YANG data models
• be support software redundancy
Which requirement prevents the use of RESTCONF for the solution?
- A. software redundancy
- B. YANG data models
- C. distributed transactions
- D. XML encoding
Correct Answer: C
Community vote distribution
C (100%)
Question #275
DRAG DROP
–
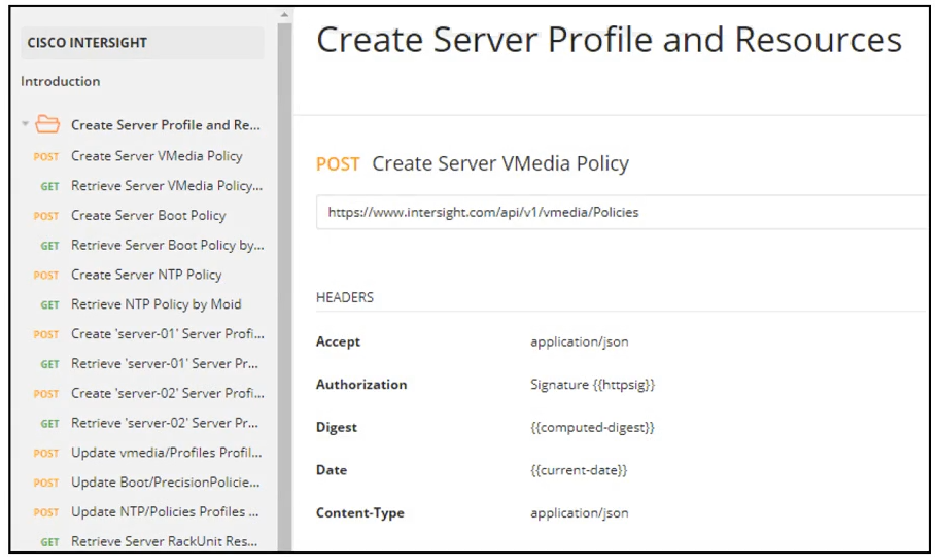
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script by using the Cisco SDK. Not all options are used.
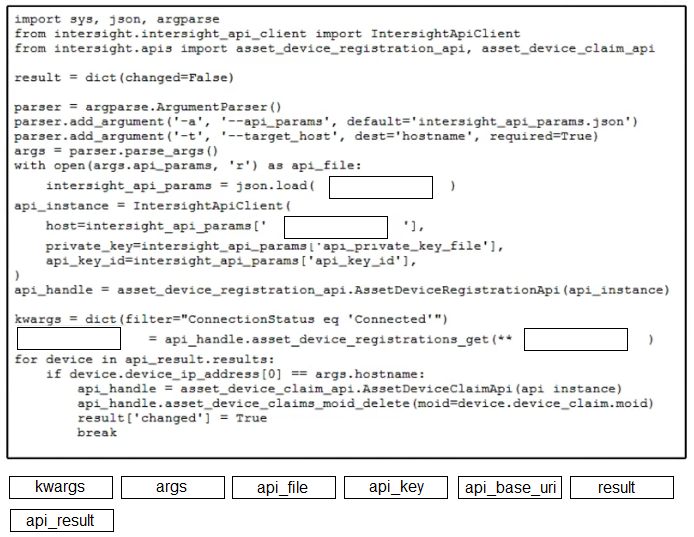
Correct Answer: 
Question #276
DRAG DROP
–
Drag and drop the functions from the left onto the networking devices on the right.
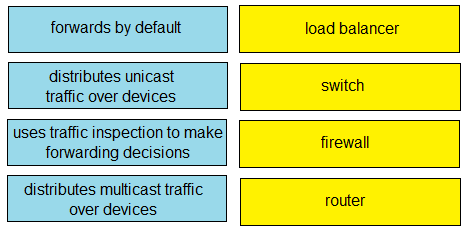
Correct Answer: 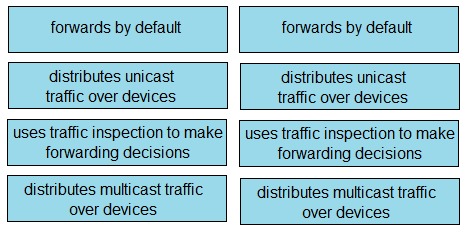
Question #277
Which technology is responsible for resolving a host name to an IP address?
- A. DNS
- B. SNMP
- C. DHCP
- D. NTP
Correct Answer: A
Question #278
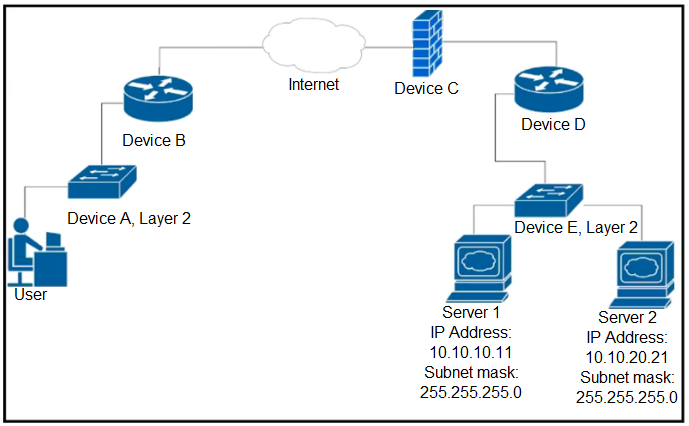
Refer to the exhibit. Up to which device does the communication server 1 and server 2 go?
- A. device B
- B. device C
- C. device D
- D. device E
Correct Answer: B
Question #279
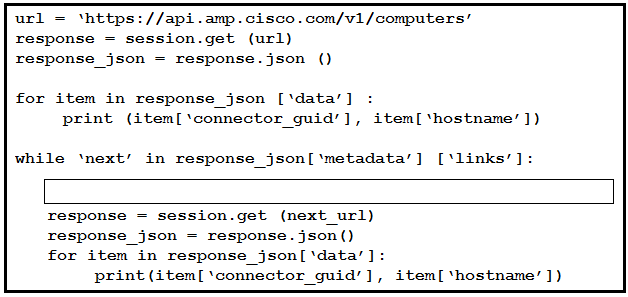
Refer to the exhibit. An engineer sends the request to collect data over Cisco AMP for Endpoints API. The Engineer must list guide and hostname data for all computers, but the first request returns only 500 items out of 2,000. Then, the engineer adds the loop to collect all the data. What must be added to the script where the code is missing to complete the requests?
- A.
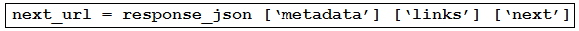
- B.

- C.
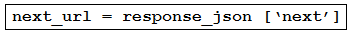
- D.
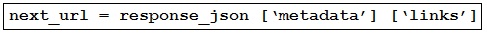
Correct Answer: C

