Free Cisco Dump, Free Dumps
Free 200-901 DEVASC Dump
Question #160
Which two elements are foundational principles of DevOps? (Choose two.)
- A. organizing cross-functional teams over organizational silos
- B. designing applications as microservices
- C. encouraging containers for the deployment of applications
- D. automating over documenting
- E. optimizing the cost of infrastructures
Correct Answer: AD
Community vote distribution
AD (100%)
Question #161
Which platform is run directly on top of a hypervisor?
- A. bare metal systems
- B. virtual machines
- C. containers
- D. applications
Correct Answer: B
Community vote distribution
B (100%)
Question #162
What are two characteristics of Bare Metal environments that are related to application deployment? (Choose two.)
- A. specifically designed for container-based workloads
- B. suitable for legacy applications that do not support virtualization
- C. provides workloads with access to hardware features
- D. not compatible with other cloud services such as PaaS or SaaS offerings
- E. provides the hypervisor to host virtual servers
Correct Answer: CE
Community vote distribution
BC (100%)
Question #163
A new application is being developed that must be hardware independent. The application includes an administrative component which is accessed using a
Windows desktop GUI. Installation and management of the environment must be fully automated. Which application deployment type meets the requirements?
- A. virtual machine
- B. virtual Python environment
- C. container
- D. bare metal
Correct Answer: C
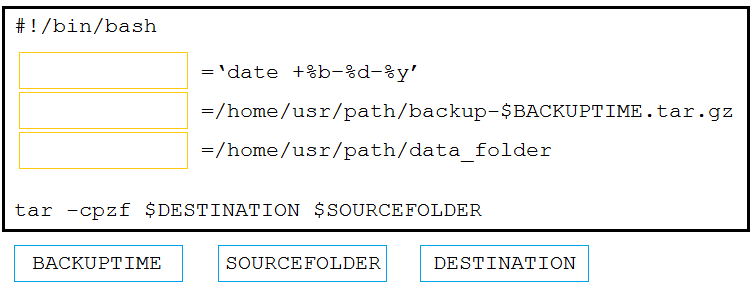
Question #164
DRAG DROP –
Drag and drop the code from the bottom onto the box where the code is missing in the Bash script to complete the missing assignments.
Select and Place:
Correct Answer: 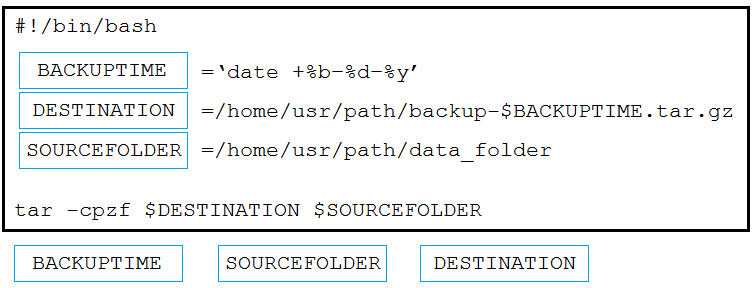
Question #165
Refer to the exhibit.
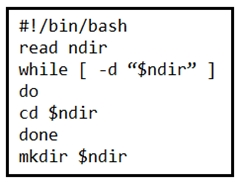
What is the action of the Bash script that is shown?
- A. For all directories in the current folder, the script goes into the directory and makes a new directory.
- B. The script waits until input is entered. If the directory exists, the script goes into it until there is no directory with the same name, then it creates a new directory.
- C. The script waits until input is entered, then it goes into the directory entered and creates a new directory with the same name.
- D. The script goes into the directory called ג€$ndirג€ and makes a new directory called ג€$ndirג€.
Correct Answer: B
Community vote distribution
B (100%)
Question #166
When using the Bash shell, how is the output of the devnet command saved to a file named `output.txt`?
- A. devnet > output.txt
- B. devnet | output.txt
- C. devnet < output.txt
- D. devnet & output.txt
Correct Answer: A
Reference:
https://askubuntu.com/questions/420981/how-do-i-save-terminal-output-to-a-file
Community vote distribution
A (100%)
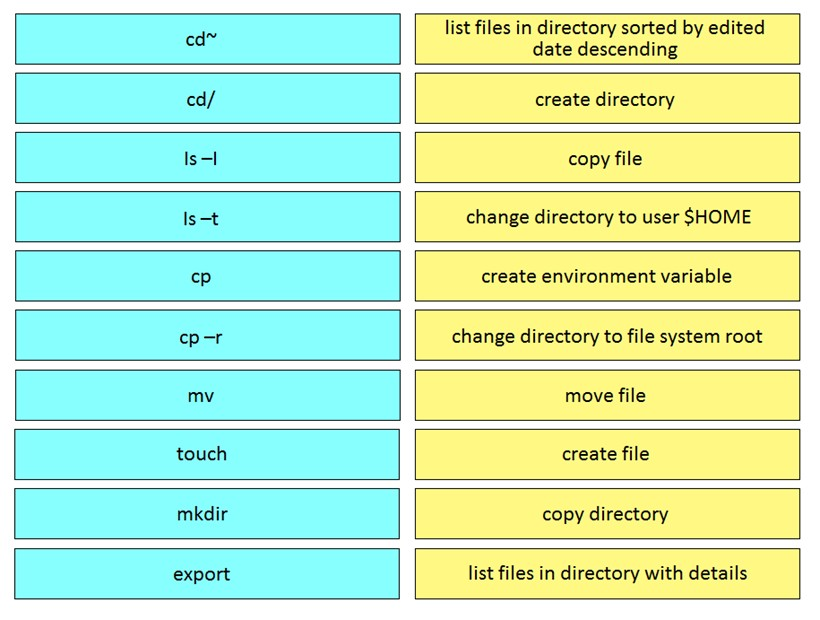
Question #167
DRAG DROP –
Drag and drop the Bash commands from the left onto the related actions on the right.
Select and Place:
Correct Answer: 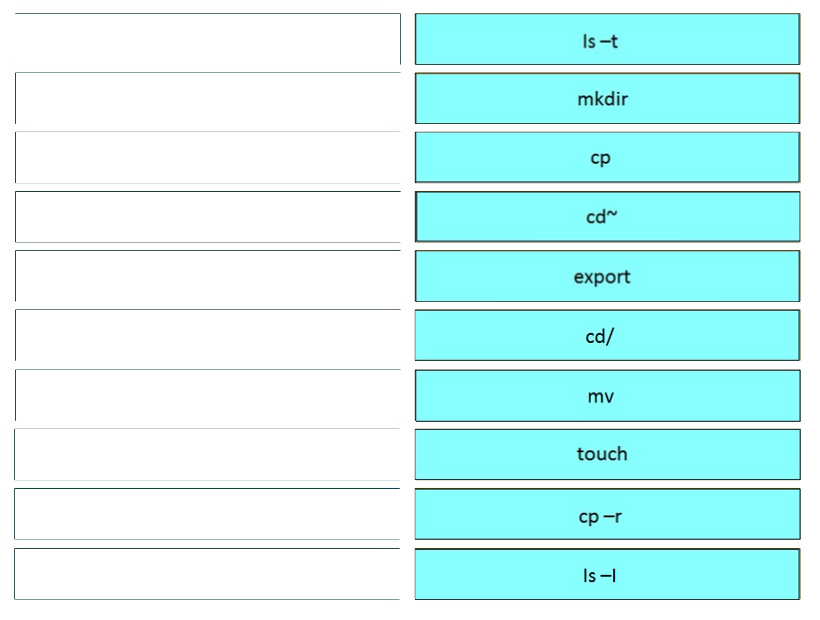
Question #168
FILL BLANK –
Fill in the blanks to complete the Bash script in which each file in a directory is renamed to its SHA256 hash?
TARGET_DIR=/usr/local/certs –
for f in ‘__________ __________’; do
__________ $f’ openssl sha -sha256 -r < $f | cut -f1 -cl’ ”
Correct Answer: See explanation below.
TARGET_DIR=/usr/local/certs –
for f in ‘/usr/local/certs’; do
echo $f’ openssl sha -sha256 -r < $f | cut -f1 -cl’ ”
Question #169
After a project is migrated to a new codebase, the `old_project` directory must be deleted. This directory has multiple read-only flies, and it must be deleted recursively without prompting for confirmation. Which Bash command must be used?
- A. rmdir -p old_project
- B. rm -rf old_project
- C. rm -r old_project
- D. rmdir old_project
Correct Answer: B
Community vote distribution
B (100%)
Question #170
What is a benefit of using edge computing in an IoT implementation?
- A. high speed in data processing
- B. low network design complexity
- C. low cost in network design
- D. high availability for network components
Correct Answer: A
Community vote distribution
A (100%)
Question #171
What is the benefit of edge computing?
- A. It reduces network latency by moving processing closer to the data source.
- B. It reduces data velocity from devices or other data sources.
- C. It simplifies security as devices and processing are brought closer together.
- D. It removes the need for centralized data processing.
Correct Answer: A
Reference:
https://blogs.cisco.com/networking/time-to-get-serious-about-edge-computing
Community vote distribution
A (100%)
Question #172
DRAG DROP –
Refer to the exhibit.
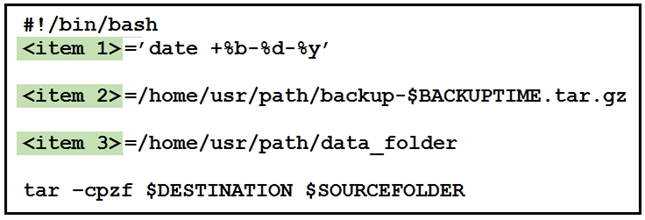
Drag and drop the variables from the left onto the item numbers on the right that match the missing assignments in the exhibit.
Select and Place:
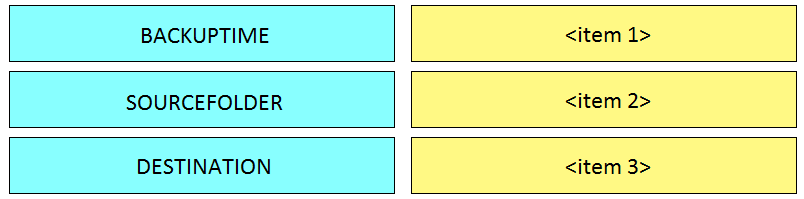
Correct Answer: 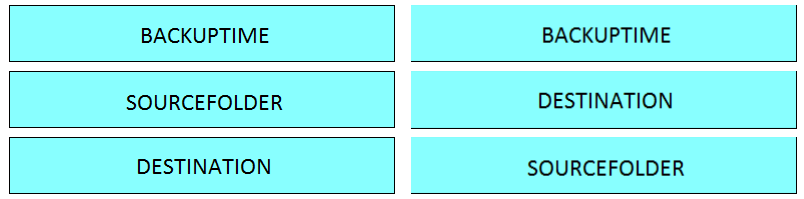
Reference:
https://medium.com/@fotios.floros/linux-backup-script-1722cc9c2bf6
(use tar in order to create your backup file)
Question #173
DRAG DROP –
Drag and drop the descriptions from the left onto the correct application deployment models on the right.
Select and Place:
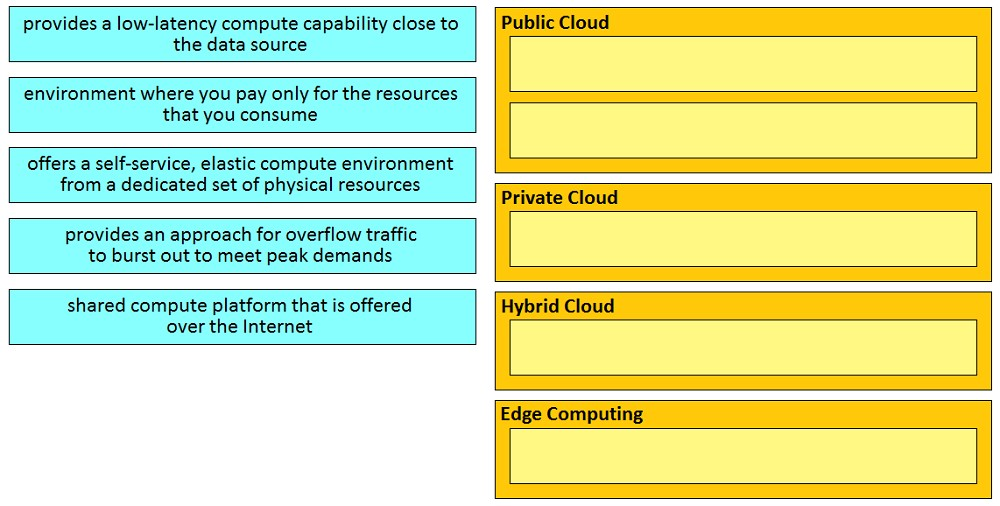
Correct Answer: 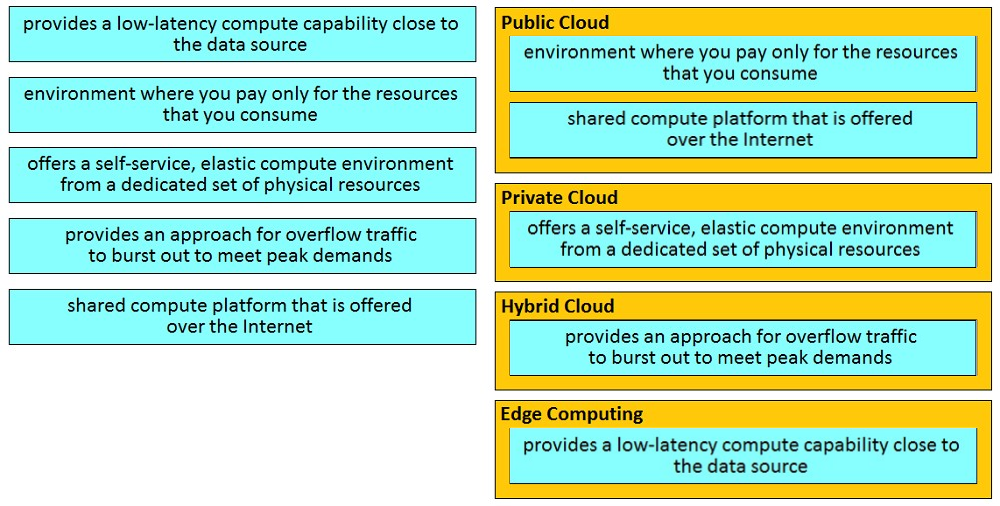
Question #174
Which type of threat occurs when an attacker can send hostile data to an interpreter within an application?
- A. sensitive data exposure
- B. broken authentication
- C. cross-site scripting
- D. injection
Correct Answer: D
Reference:
https://owasp.org/www-project-top-ten/OWASP_Top_Ten_2017/Top_10-2017_A1-Injection
Community vote distribution
D (100%)
Question #175
A company is looking for a cloud deployment which will only use the on-premise infrastructure, is user self-service, and is easy to scale. Which cloud solution should be selected for these requirements?
- A. multi
- B. private
- C. hybrid
- D. public
Correct Answer: B
Community vote distribution
B (100%)
Question #176
Refer to the exhibit.
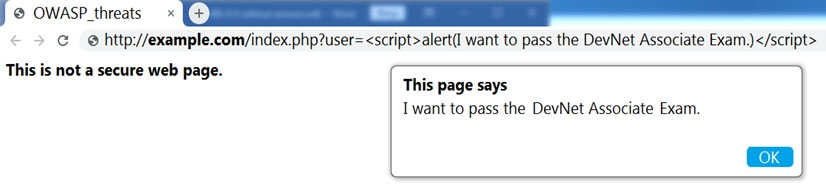
Which OWASP threat does this example demonstrate?
- A. broken access control
- B. cross-site scripting
- C. SQL injection
- D. man-in-the-middle
Correct Answer: B
Reference:
https://owasp.org/www-chapter-coimbatore/assets/files/Web%20Application%20Security%20Adithyan%20AK.pdf
Question #177
What should a CI/CD pipeline aim to achieve?
- A. to require minimal manual interaction
- B. to allow manual testing before deployment
- C. to support new deployments on a fixed monthly schedule
- D. to provide a documented process for feedback
Correct Answer: A
Community vote distribution
A (100%)
Question #178
A function my_func() returns True when it executes normally. Which Python snippet tests my_func()?
A.
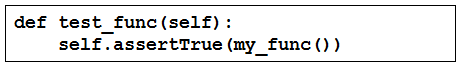
B.

C.

D.
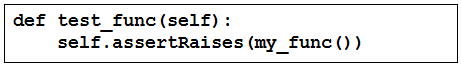
Correct Answer: C
Reference:
https://github.com/django/django/blob/master/tests/auth_tests/test_mixins.py
Question #179
What are two roles of an artifact repository in a CI/CD pipeline? (Choose two.)
- A. stores files needed and generated during the build process
- B. provides traceable, searchable, and manageable binary files
- C. is required for CI/CD pipelines executed on a public cloud infrastructure
- D. allows for comparing and merging changes in the source code
- E. is required for managing open source software
Correct Answer: AB
Community vote distribution
AB (100%)
Question #180
A company is adopting DevOps as part of an internal transformation, and is reviewing the success of the first deployments. Developers and engineers are working together to resolve any resulting issues. However, this new way of working has increased overhead, and the team is finding it difficult to complete releases in time.
Which area of the CALMS framework must the company target for improvement?
- A. Collaboration
- B. Lean
- C. Sharing
- D. Measurement
Correct Answer: B
Reference:
https://blog.sonatype.com/principle-based-devops-frameworks-calms
Community vote distribution
B (67%)
C (33%)
Question #181
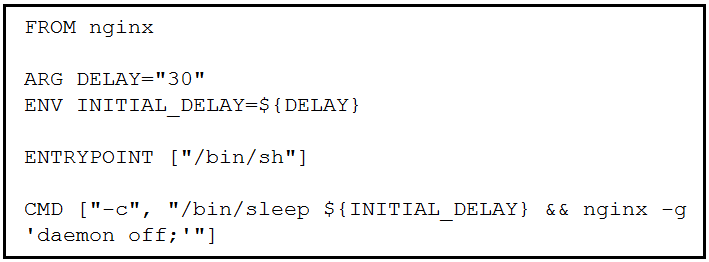
Refer to the exhibit. Which command, including arguments, is executed when the container starts?
- A. /bin/sh -c “/bin/sleep 30 && nginx -g ‘daemon off;'”
- B. /bin/sh -c “/bin/sleep 10 && nginx -g ‘daemon off;'”
- C. /bin/bash -c “/bin/sleep 30 && nginx -g ‘daemon off;'”
- D. /bin/sh -c “/bin/sleep 30” && nginx -g ‘daemon off;’
Correct Answer: A
Community vote distribution
A (100%)
Question #182
A developer created a new secure API and is testing the functionality locally. The API was added to a container for further testing, and other team members and applications need to connect to the API. Which command exposes the API in the container as port 8443 and allows connections external to the host?
- A. docker run -p 127.0.0.1:80:8443/tcp myapiservice
- B. docker run -p 0.0.0.0:443:8443/tcp myapiservice
- C. docker run -p 0.0.0.0:8443:443/tcp myapiservice
- D. docker run -p 127.0.0.1:443:8443/tcp myapiservice
Correct Answer: C
Community vote distribution
B (57%)
C (43%)
Question #183
A developer has created a new image to use in a Docker build and has added a tag for the image by using the command:
$ docker tag 84fe411926287 local/app:0.4
Which command must be executed next to build the Docker image using the tag?
- A. $ docker build -p local/app:0.4
- B. $ docker run -t local/app:0.4
- C. $ docker run -p local/app:0.4
- D. $ docker build -t local/app:0.4
Correct Answer: D
Community vote distribution
D (100%)
Question #184
Access to the management interface of devices must be restricted by using SSH and HTTPS. Which two ports must be included in the ACLs for the protocols to work? (Choose two.)
- A. 22
- B. 23
- C. 80
- D. 443
- E. 880
Correct Answer: AD
Community vote distribution
AD (100%)
Question #185
What is a benefit of using a code review process in application development?
- A. accelerates the deployment of new features in an existing application
- B. provides version control during code development
- C. enables the quick deployment of new code
- D. eliminates common mistakes during development
Correct Answer: D
Community vote distribution
D (100%)
Question #186
Which OWASP threat takes advantage of a web application that the user has already authenticated to execute an attack?
- A. phishing
- B. DoS
- C. brute force attack
- D. CSRF
Correct Answer: D
Community vote distribution
D (100%)
Question #187
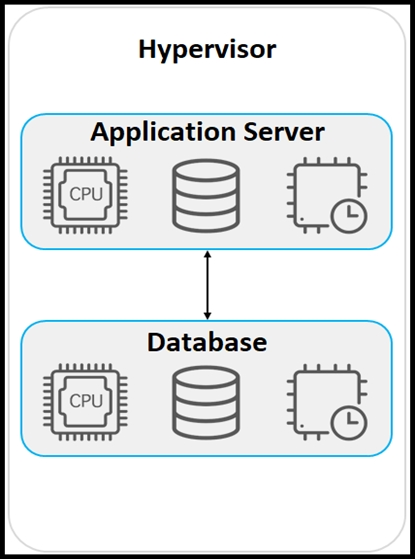
Refer to the exhibit. An application must be deployed on a server that has other applications installed. The server resources are to be allocated based on the deployment requirements. The OS for each application must be independent. Which type of deployment is used?
- A. hybrid
- B. virtual machines
- C. containers
- D. bare metal
Correct Answer: B
Community vote distribution
B (100%)
Question #188
What is a benefit of a distributed version control system?
- A. encourages users to commit small places of work to the system more frequently
- B. ensures that all code meets minimum standards before being committed to the system
- C. allows users to work on the codebase even when not connected to the Internet
- D. ensures that all code is tested before being committed to the system
Correct Answer: C
Reference:
https://about.gitlab.com/topics/version-control/benefits-distributed-version-control-system/
Community vote distribution
C (57%)
A (43%)
Question #189
A company requires a new platform to store large volumes of log data that is generated in their assembly plant. The platform must be scalable, so the underlying technology must provide a path for fast deployment of new nodes for data and indexing? The data contains sensitive information, so specialist encryption tools must be used to secure the data. Which application deployment model meets the requirements?
- A. edge
- B. private cloud
- C. public cloud
- D. hybrid cloud
Correct Answer: B
Reference:
https://www.simform.com/blog/cloud-deployment-models/
Community vote distribution
D (50%)
B (50%)
Question #190
What is a procedural component of CI/CD pipelines?
- A. Bundled artifacts must be generated.
- B. Every test must pass for the pipeline to continue its execution.
- C. Some tests fall without stopping the pipeline execution.
- D. The release label that identifies the build is optional.
Correct Answer: A
Community vote distribution
B (77%)
A (23%)
Question #191
Which OWASP threat occurs when untrusted data is supplied as input to an interpreter as part of a command or query?
- A. broken authentication
- B. data exposure
- C. injection
- D. cross-site scripting
Correct Answer: C
Reference:
https://owasp.org/www-community/Injection_Theory
Community vote distribution
C (100%)
Question #192
Which product provides network controller-level management features?
- A. Cisco ISE
- B. Cisco DNA Center
- C. Cisco UCS Manager
- D. Cisco NX-OS
Correct Answer: B
Reference:
https://www.cisco.com/c/en/us/products/cloud-systems-management/index.html
Question #193
What is the purpose of the Cisco VIRL software tool?
- A. to verify configurations against compliance standards
- B. to automate API workflows
- C. to simulate and model networks
- D. to test performance of an application
Correct Answer: C
Reference:
Community vote distribution
C (100%)
Question #194
What are two advantages of the Model-View-Controller software design pattern? (Choose two.)
- A. allows for multiple views of the same model
- B. separates responsibilities of the code, which makes future modifications easier
- C. simplifies network automation
- D. makes code easier to deploy using CI/CD pipelines
- E. reduces the need for error handling
Correct Answer: AB
Community vote distribution
AB (100%)
Question #195
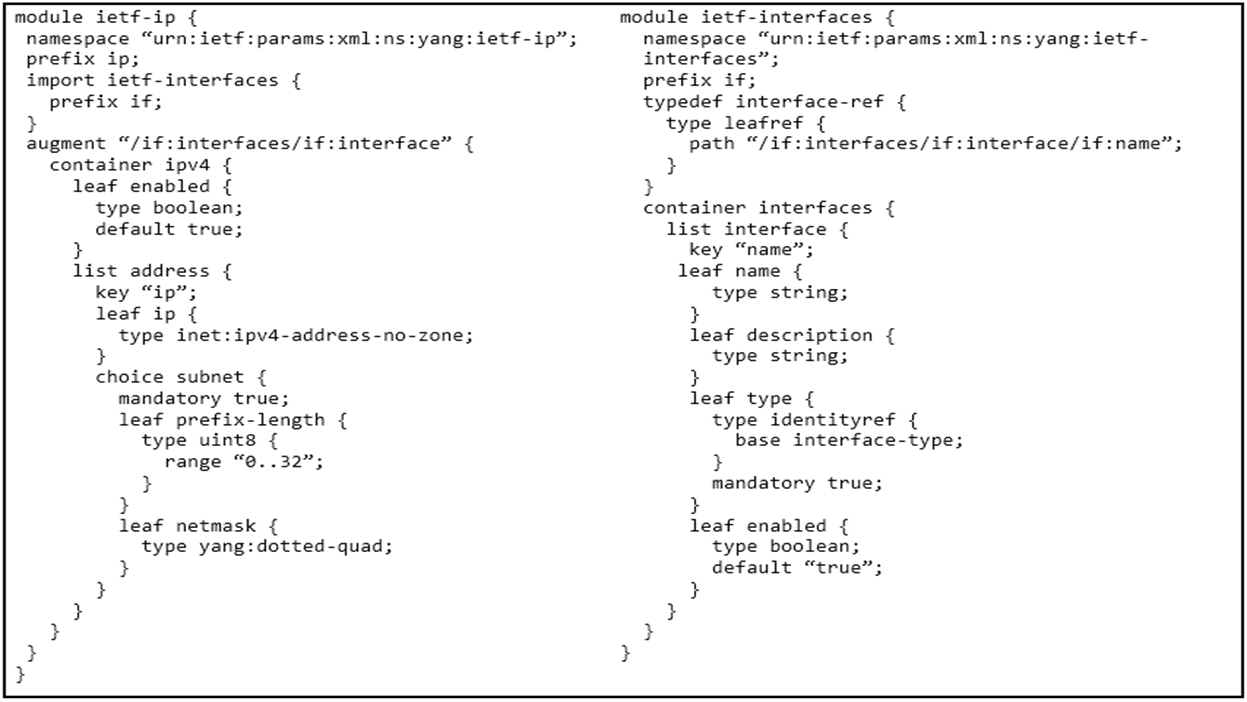
Refer to the exhibit. Which JSON snippet configures a new interface according to YANG model?
A.
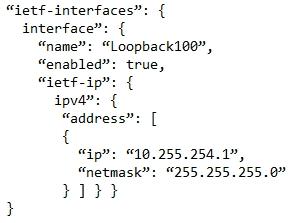
B.
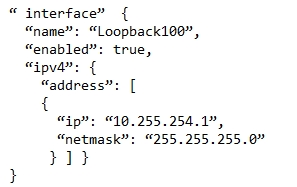
C.
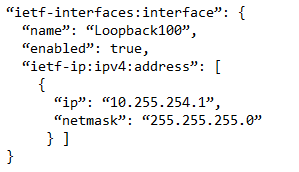
D.
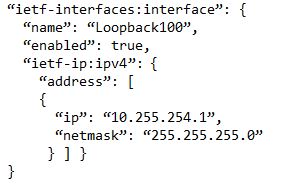
Correct Answer: D
Question #196
Refer to the exhibit.
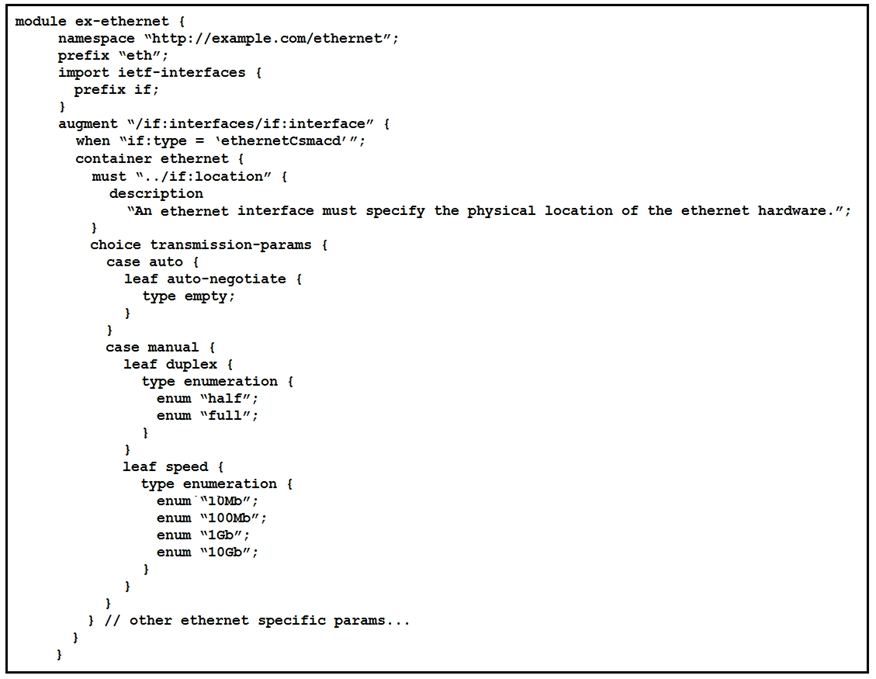
What is represented in this YANG module?
- A. interface management
- B. BGP
- C. OpenFlow
- D. topology
Correct Answer: A
Reference:
https://github.com/CiscoDevNet/dnav3-code/blob/master/intro-mdp/yang/models/Cisco-IOS-XE-interfaces-oper.yang
Community vote distribution
A (100%)
Question #197
Which CI/CD tool is an automation tool used to build, test, and deploy software?
- A. Git
- B. Gradle
- C. Nagios
- D. Jenkins
Correct Answer: D
Reference:
https://www.infoworld.com/article/3271126/what-is-cicd-continuous-integration-and-continuous-delivery-explained.html
Community vote distribution
D (100%)
Question #198
An automation script fails to connect to an internal server exactly 1 out of 2 times it is executed. This behavior is seen from different clients. Which networking device must be at fault?
- A. load balancer
- B. laptop on which the script is running
- C. switch
- D. router
Correct Answer: A
Community vote distribution
A (100%)
Question #199
What are two advantages of YANG-based approaches for infrastructure automation? (Choose two.)
- A. multi-platform vendor abstraction
- B. compiles to executables that run on network devices
- C. designed to reflect networking concepts
- D. directly maps to JavaScript
- E. command line driven interface
Correct Answer: AC
Community vote distribution
AC (100%)

