Free Cisco Dump, Free Dumps
Free 200-901 DEVASC Dump
Question #81
DRAG DROP –
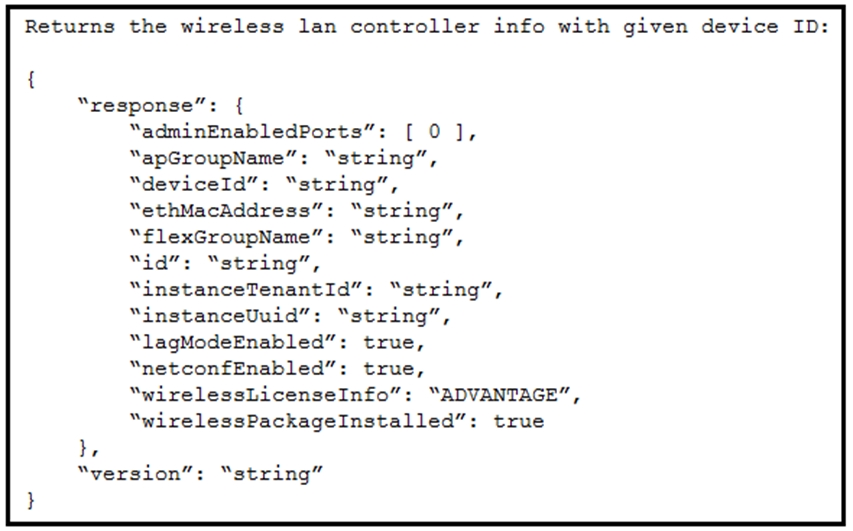
Refer to the exhibit. Drag and drop the code from the bottom onto the blanks in the code to construct a cURL command using the Cisco DNA Center API, which will provide the details of a WLAN controller with Id ab123456789. Not all options are used.
Select and Place:
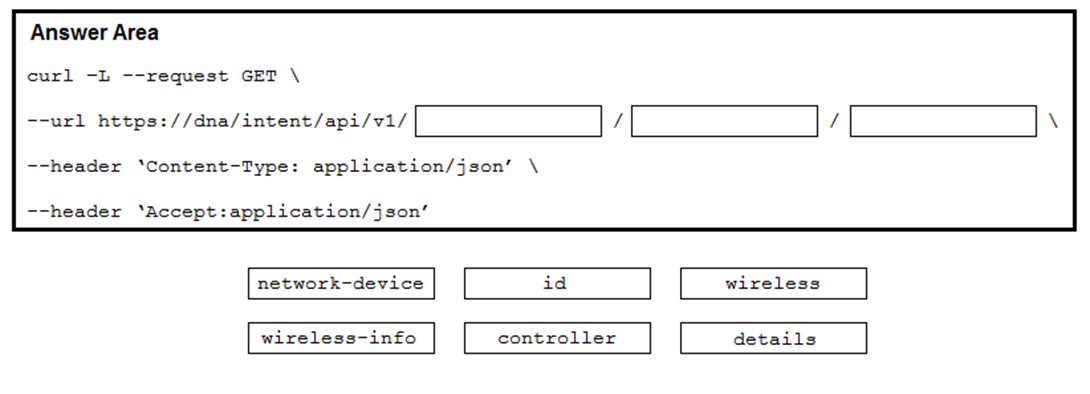
Correct Answer: 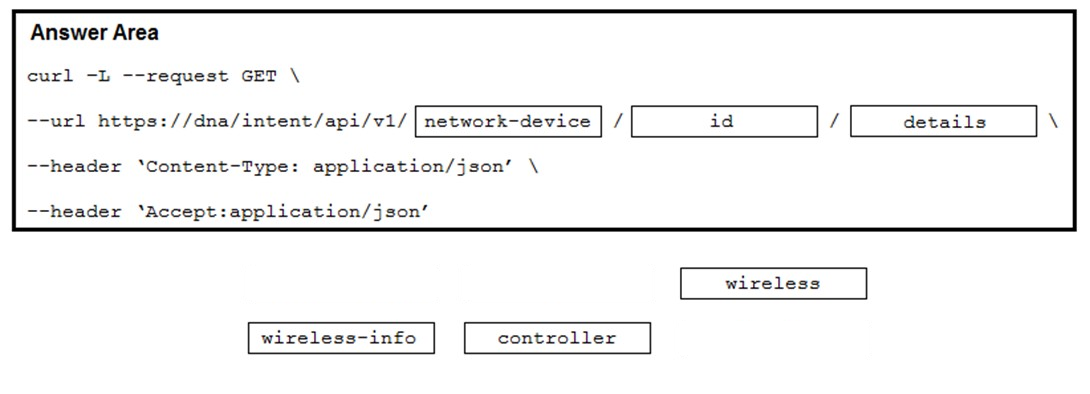
Question #82
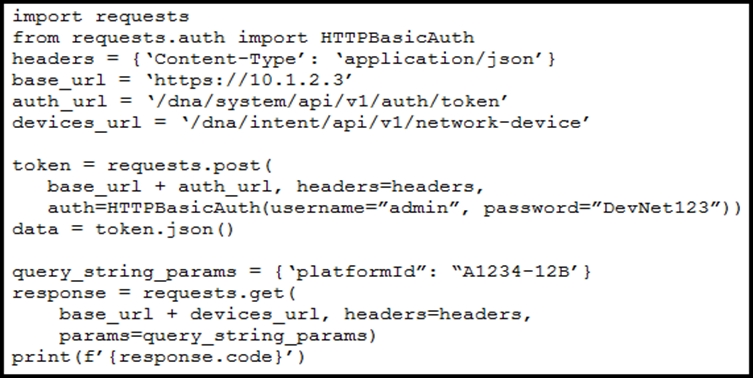
Refer to the exhibit. A network engineer must manage the network devices. The engineer prepares a Python script to authenticate to the Cisco DNA Center API and request a device list. The device request fails and returns error code 401. Which action solves the problem?
- A. Update the credentials that are already supplied and retry the request.
- B. Send the request to another network in case there are reachability issues.
- C. Send the Authentication header in the request with a valid configuration.
- D. Update the API URL, which matched the API endpoint for device list.
Correct Answer: C
Community vote distribution
C (83%)
A (17%)
Question #83
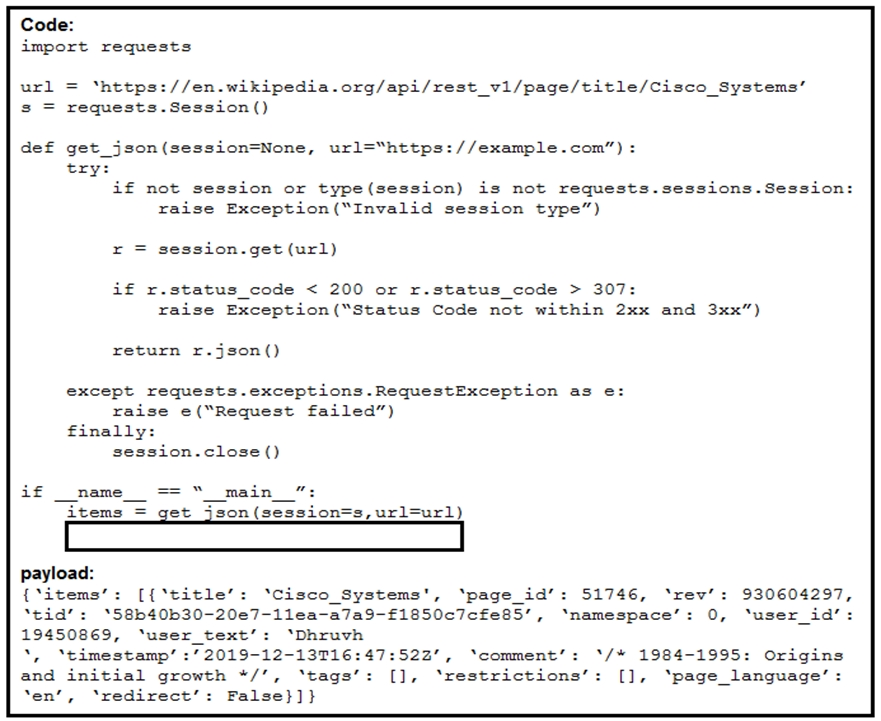
Refer to the exhibit. Which command needs to be placed on the box where the code is missing to output the value of page_id in the Python 3.7 script?
- A. print(items.get(‘items’)[0].get(‘page_id’))
- B. print(items.get(‘items’).get(‘page_id’))
- C. print(items[‘items’][‘page_id’].keys())
- D. print(items[‘items’][‘page_id’])
Correct Answer: B
Community vote distribution
A (94%)
Question #84
Refer to the exhibit.
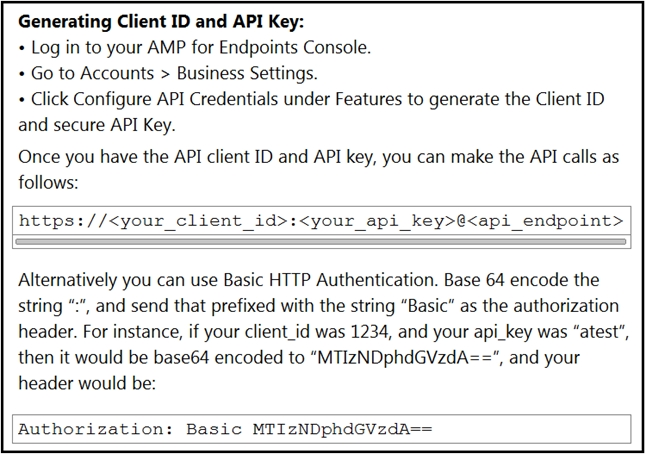
The documentation outlines how to use credentials for the AMP API. Which script successfully performs an API call using basic authentication?
A.

B.
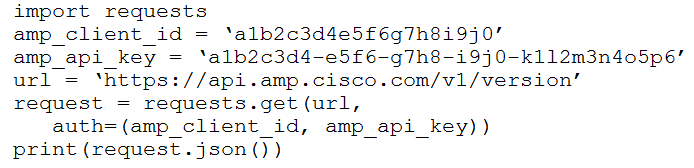
C.
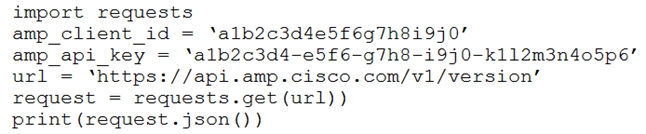
D.
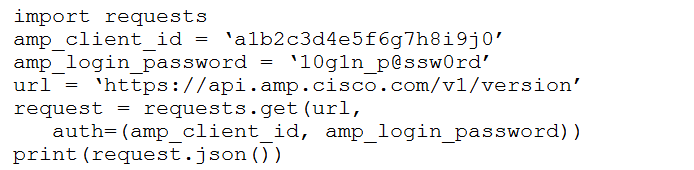
Correct Answer: B
Question #85
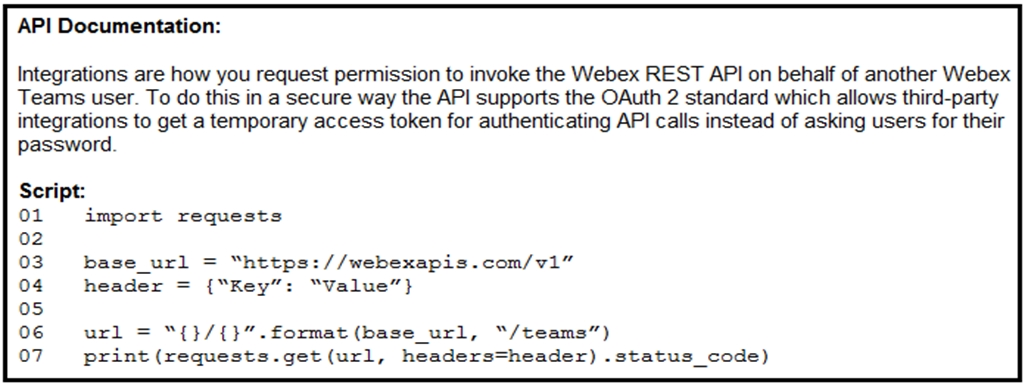
Refer to the exhibit. A developer creates a Python script that queries Cisco Webex. When the script is executed, a 401 code is returned. After troubleshooting, the developer discovers that the service is missing privileges. Which change to the header in line 4 of the script results in the code 200?
- A. header = {ג€Authenticationג€: ג€Bearer YOUR_TOKENג€}
- B. header = {ג€Authentication Bearerג€ : ג€YOUR_TOKENג€
- C. header = {ג€Authorization Bearerג€ : ג€YOUR_TOKENג€}
- D. header = {ג€Authorizationג€ : ג€Bearer YOUR_TOKENג€}
Correct Answer: D
Community vote distribution
D (100%)
Question #86
DRAG DROP –
Drag and drop the HTTP methods from the left onto their generally accepted corresponding create, read, update, and delete operations on the right.
Select and Place:
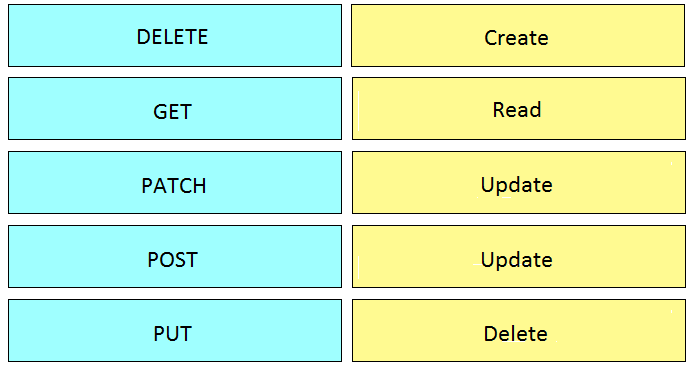
Correct Answer: 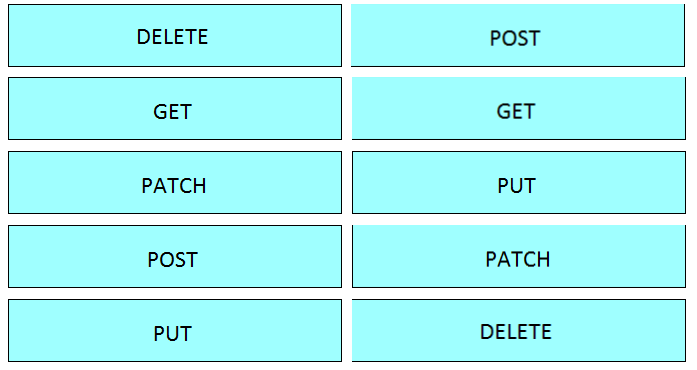
Reference:
https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/application-policy-infrastructure-controller-enterprise-module/1-2-x/config-guide/ b_apic-em_config_guide_v_1-2-x/b_apic-em_config_guide_v_1-2-x_chapter_01001.pdf
Question #87
DRAG DROP –
Refer to the exhibit.
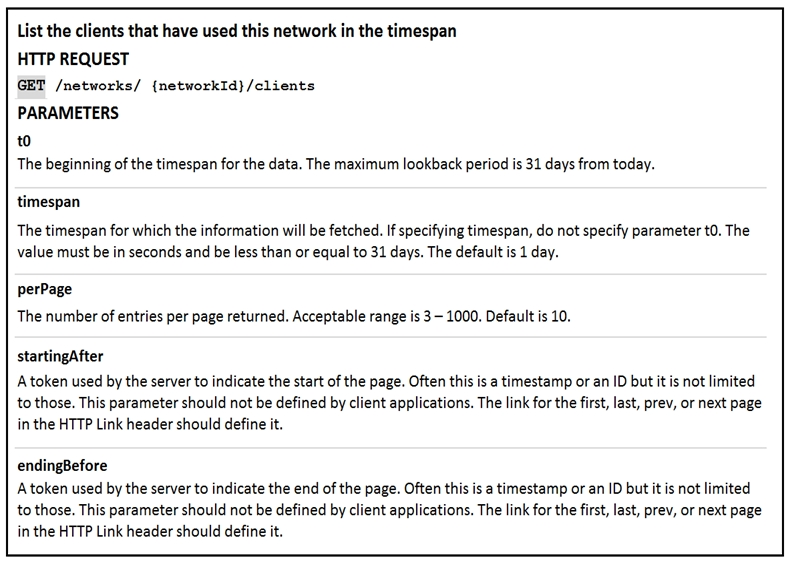
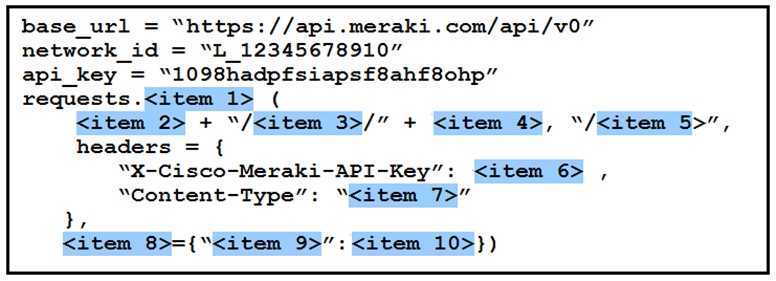
Drag and drop the code from the left onto the item numbers on the right to complete the Meraki code to obtain a list of clients which have used this network.
Select and Place:
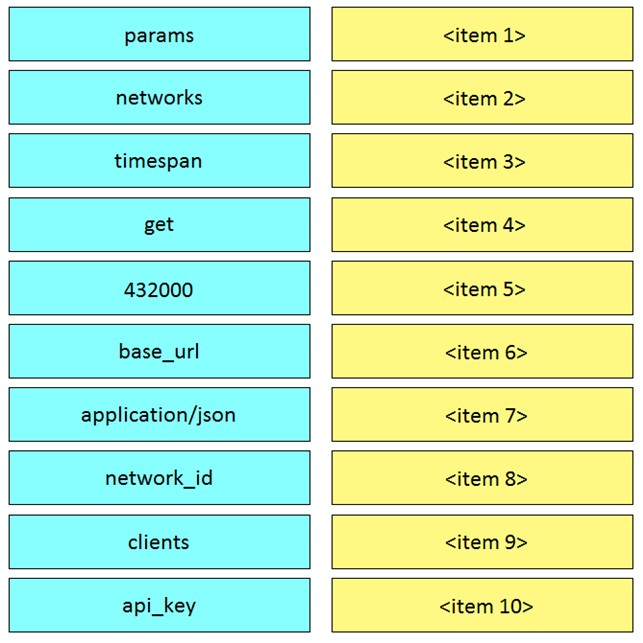
Correct Answer: 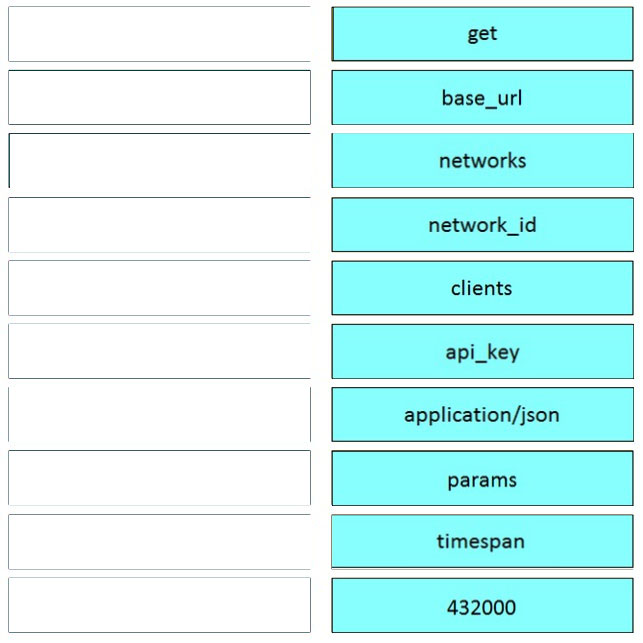
Question #88
In Python, which expression checks whether the script returns a success status code when the Requests library is used?
- A. response.status_code == requests.codes.ok
- B. response.code == requests.codes.ok
- C. response.status_code == requests.ok
- D. response.status_code != requests.codes.ok
Correct Answer: A
Reference:
https://realpython.com/python-requests/
Community vote distribution
A (100%)
Question #89
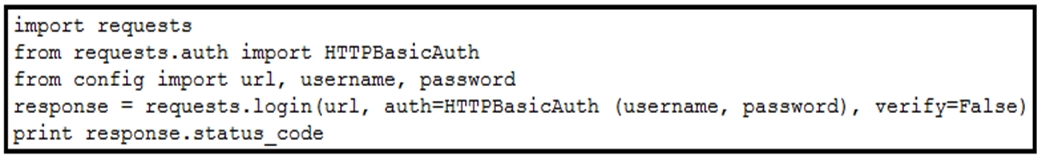
Refer to the exhibit. The script returns an output of 401. To use the supplied URL, an HTTP GET request must be sent with an Authorization header. The header value is a base64 encoded concatenation of the username and password. Which action must be taken to return an output of 200?
- A. Change the verify=False setting in the request to verify=True to enable HTTP Basic authentication.
- B. Verify that the username and password values imported from the configuration file are still valid.
- C. Insert an Authorization header with the values username:password from the supplied configuration file.
- D. Modify the method from LOGIN to GET and supply the username:password value as JSON payload.
Correct Answer: D
Community vote distribution
D (100%)
Question #90
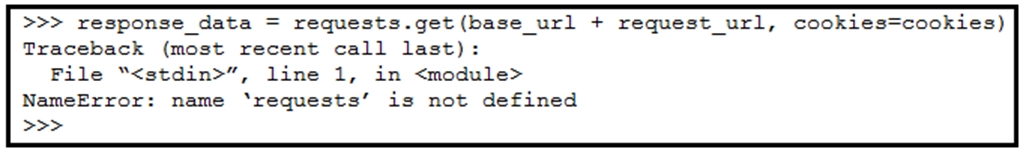
Refer to the exhibit. A Python code has been written to query a device. The executed code results in the error shown. Which action resolves the problem?
- A. import json
- B. requests(ג€GETג€, base_url + request_url, cookies=cookies)
- C. pip install requests
- D. import requests
Correct Answer: D
Community vote distribution
D (100%)
Question #91
Which REST architectural constraint indicates that no client context should be stored on the server between requests?
- A. cacheable
- B. stateless
- C. uniform interface
- D. client-server
Correct Answer: B
Reference:
https://developer.cisco.com/docs/nx-os/#!representational-state-transfer-rest
Community vote distribution
B (100%)
Question #92
Which HTTP code group is issued when a request is received successfully, understood, and processed?
- A. 2xx
- B. 3xx
- C. 4xx
- D. 5xx
Correct Answer: A
Community vote distribution
A (100%)
Question #93
A developer creates a web application that receives a username and password and uses them to sync the credentials to other services through HTTPS. API keys to services are part of the configuration files of the application, but the credentials to the database that stores the synchronization logs are obtained through an external vault service. What is the security issue in this scenario?
- A. Communication between the application and the services is not encrypted.
- B. The database credentials should be stored in the configuration files so that they are secured on the same server.
- C. The API keys are stored in the configuration files but should be stored in the vault service.
- D. The synchronization logs should be encrypted and not stored in a relational database.
Correct Answer: A
Community vote distribution
C (78%)
A (22%)
Question #94
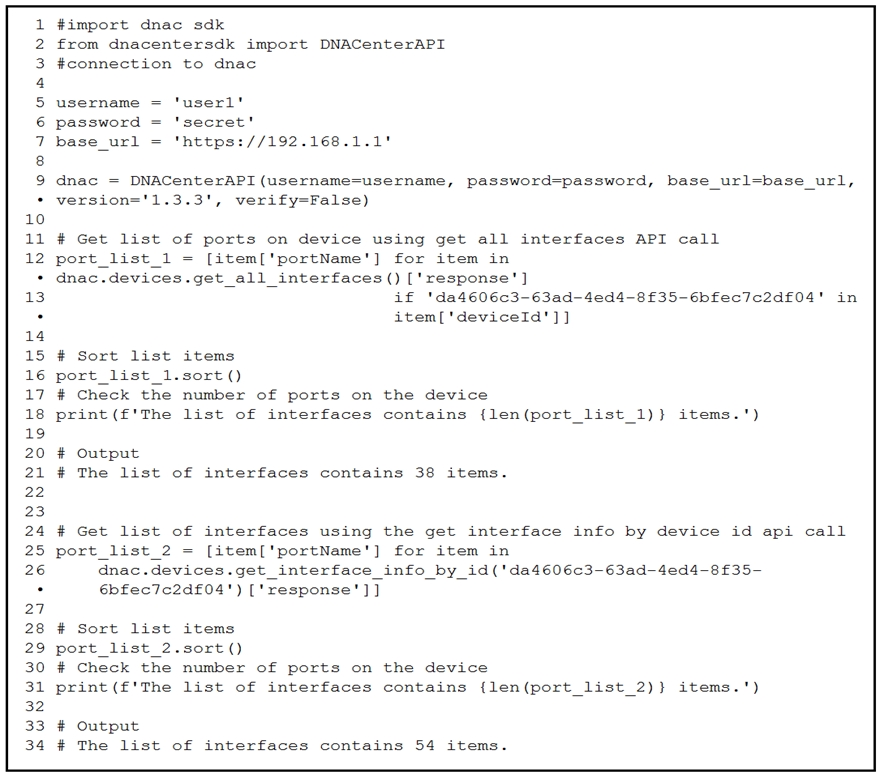
Refer to the exhibit. An engineer writes a Python script that uses two different API calls to query Cisco DNA Center for the number of interfaces on a device. The engineer notices that the two API calls produce different results. Why are fewer interfaces returned for the same device when the ‘get_all_interfaces’ API call is used?
- A. times out
- B. rate limit
- C. pagination
- D. invalid password
Correct Answer: C
Community vote distribution
C (100%)
Question #95
DRAG DROP –
Drag and drop the code snippets from the bottom into the Python script to write API output to a csv file. Not all options are used.
Select and Place:
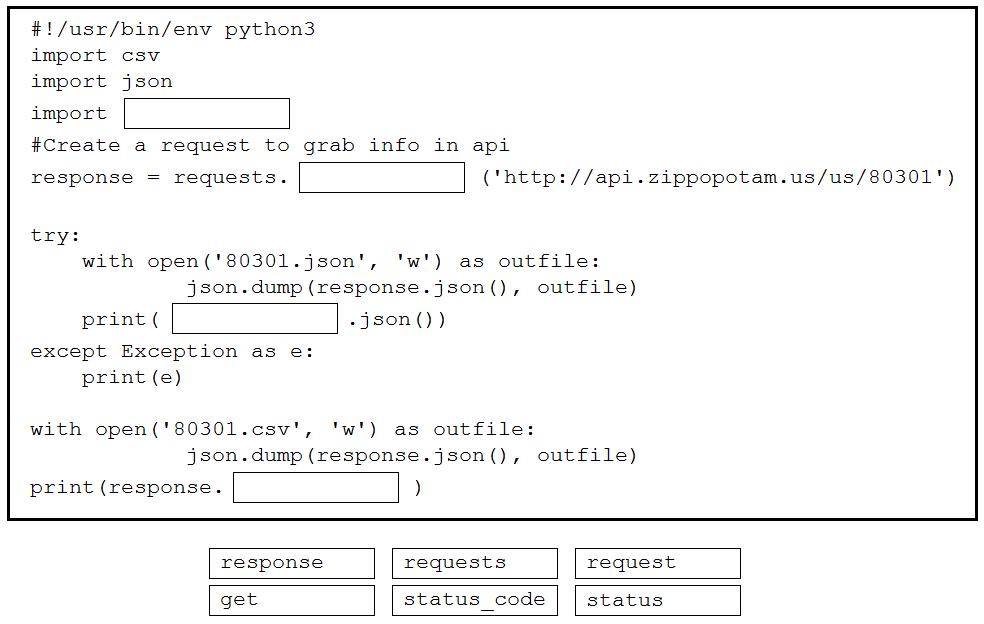
Correct Answer: 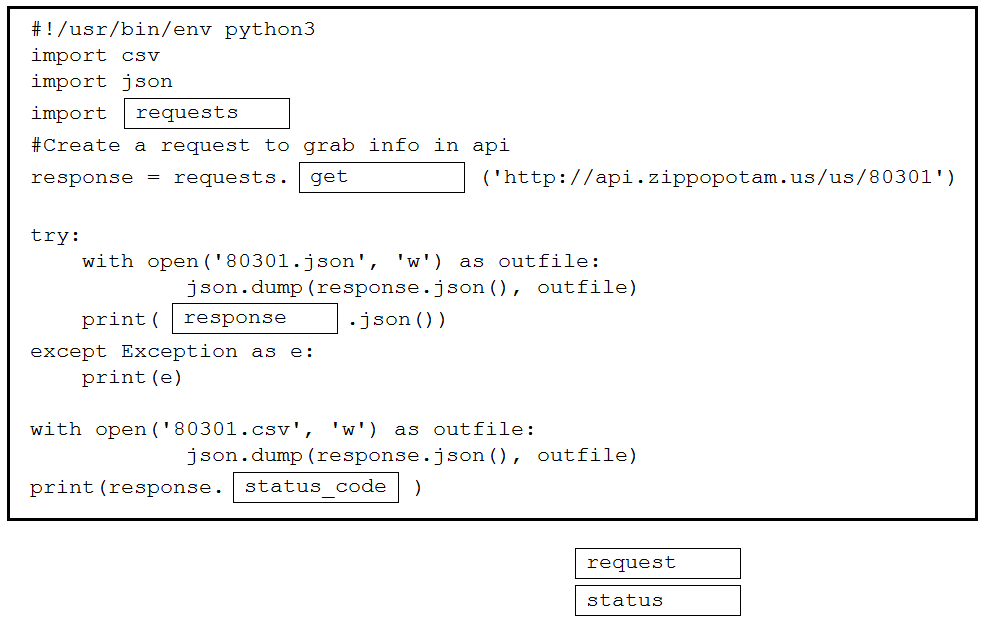
Question #96
DRAG DROP –
Drag and drop the code snippets from the bottom to the blanks in the code to test the API response through the Python unittest library. Not all options are used.
Select and Place:
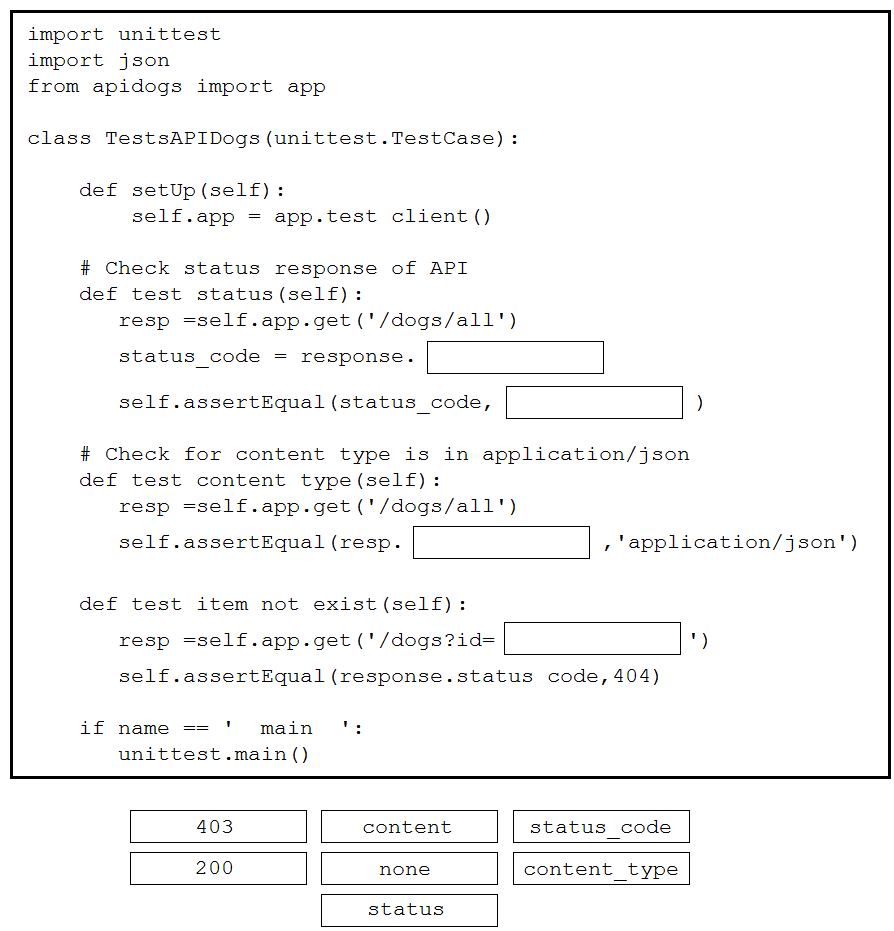
Correct Answer: 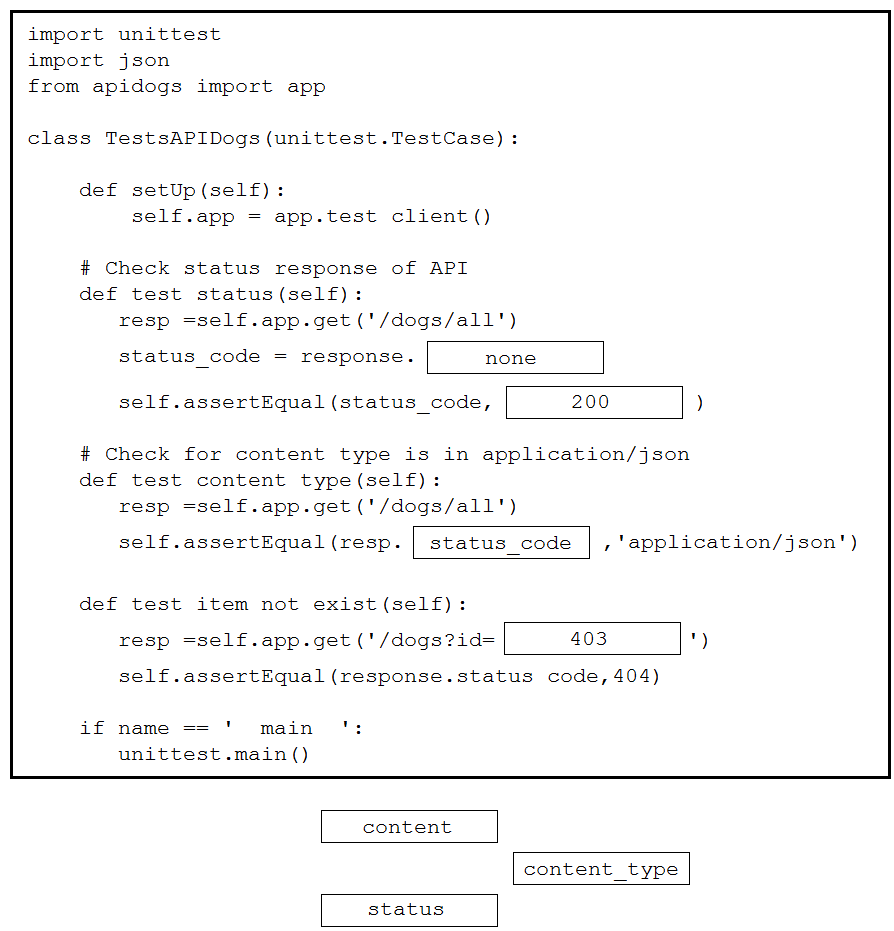
Question #97
DRAG DROP –
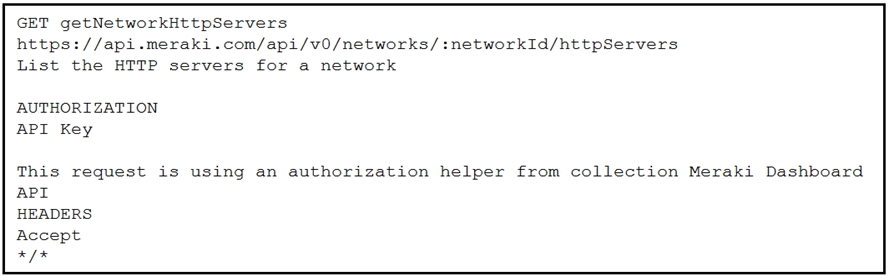
Refer to the exhibit. A developer is creating a Python script to obtain a list of HTTP servers on a network named office_east by using the Cisco Meraki API. The request has these requirements:
* Must time out if the response is not received within 2 seconds.
* Must utilize client certificates and SSL certificate verification.
* Must utilize basic authentication that uses a username of admin and a password of cisco.
* Must save the response to an object named response.
Drag and drop the code snippets from the bottom onto the blanks in the code to meet the requirements. Not all options are used.
Select and Place:
Correct Answer: 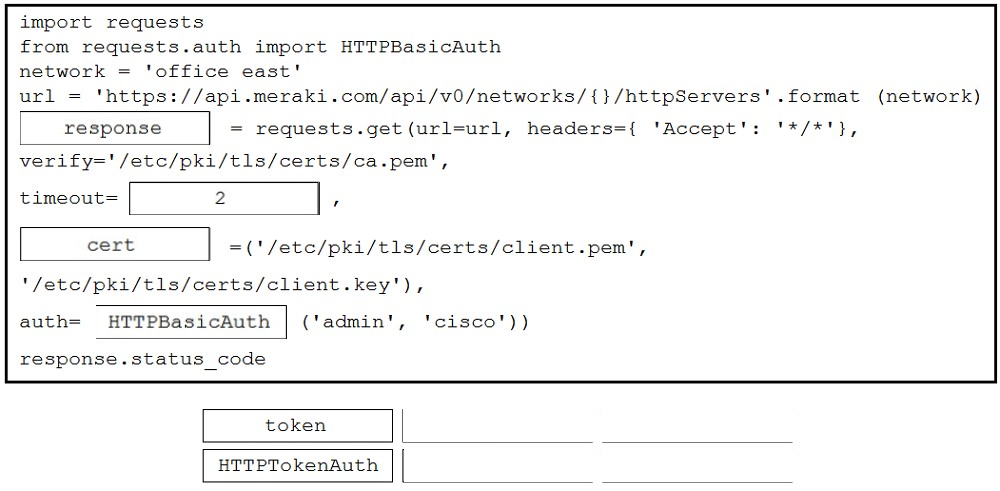
Reference:
https://community.cisco.com/t5/networking-blogs/authenticating-rest-api-calls-to-dnac-getting-started/ba-p/3658058
Question #98
DRAG DROP –
Drag and drop the code snippets from the bottom to the blanks in the code to complete the HTTP response. Not all options are used.
Select and Place:
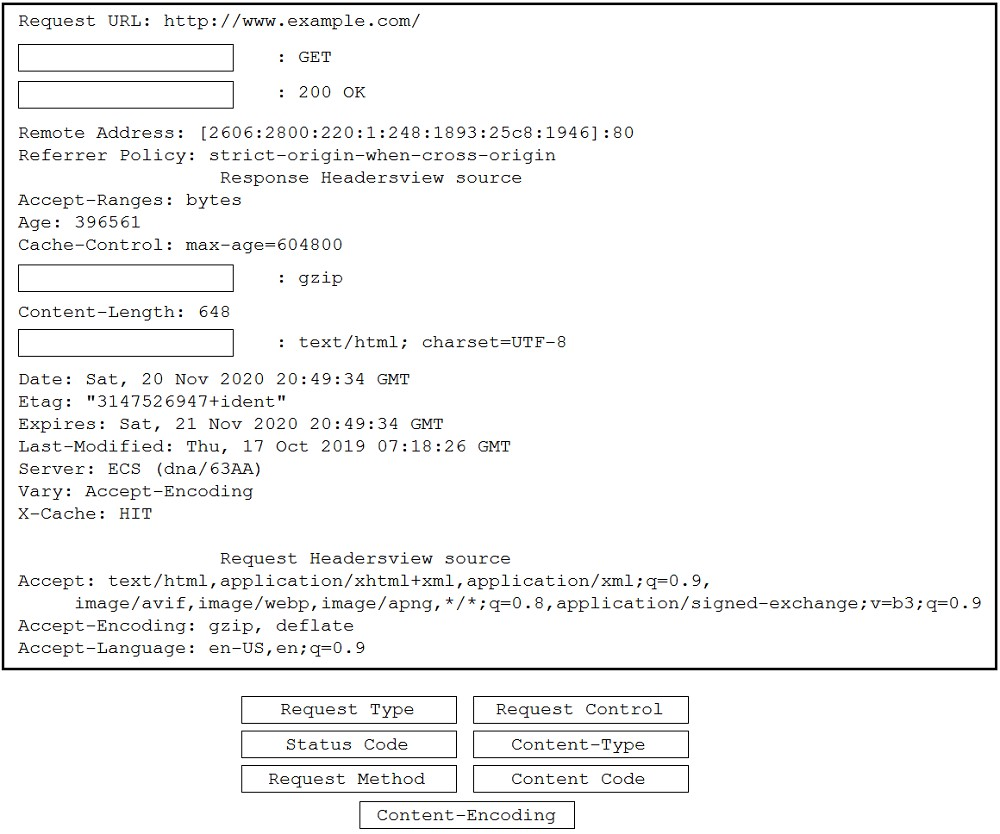
Correct Answer: 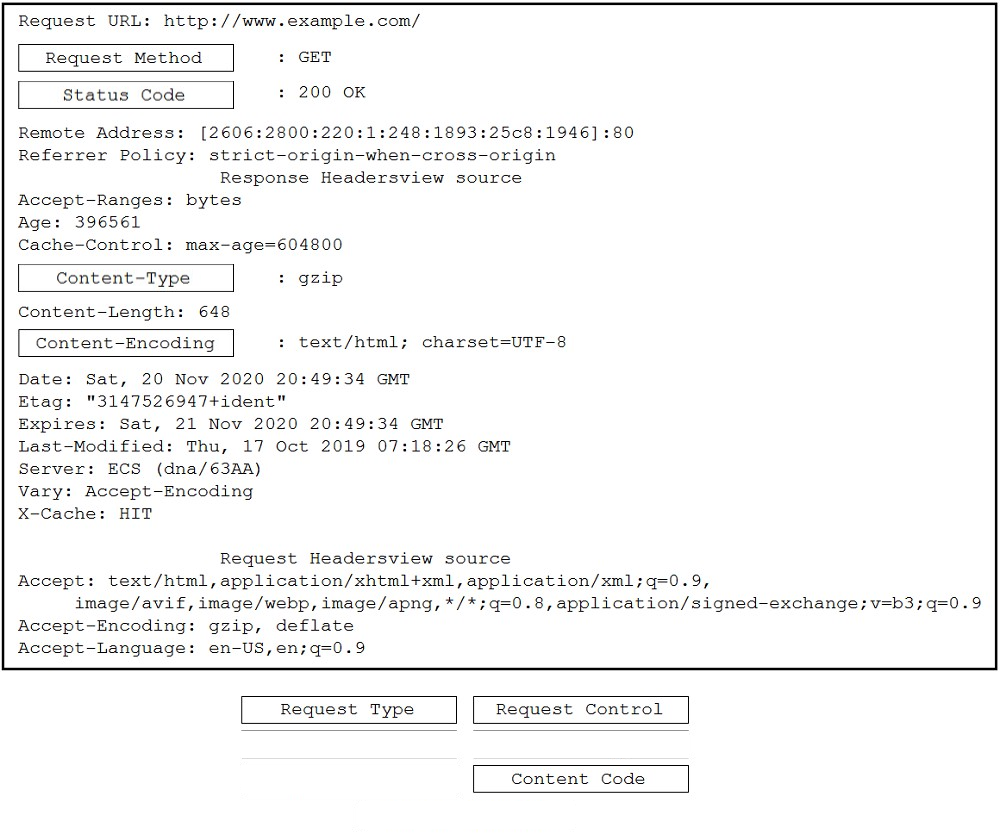
Question #99
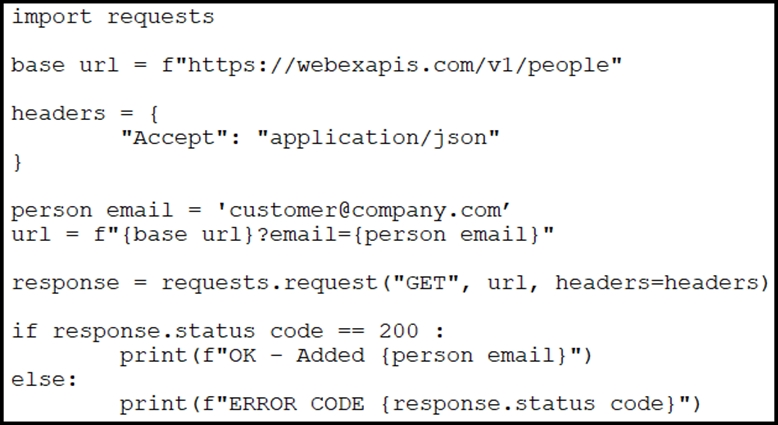
Refer to the exhibit. A collaboration engineer has developed a script to automate the gathering of information by providing the email address of the individual.
When the engineer tests the script, a 401 error is received. Which command fixes the script?
- A. Add ג€Authorizationג€: ג€Bearer <WEBEX_TOKEN>ג€ to the headers.
- B. Add ג€Authenticationג€: ג€Basic <WEBEX_TOKEN>ג€ in the base_url after ג€https://ג€.
- C. Add ג€<Authorization>:<password>@ג€ in the base_url after ג€https://ג€.
- D. Add ג€Authenticationג€: ג€Bearer <WEBEX_TOKEN>ג€ to the headers.
Correct Answer: A
Community vote distribution
A (100%)
Question #100
A developer is attempting to retrieve all the messages from a Cisco Webex space. The server responds by sending the first 1,000 messages. The developer must make additional requests to retrieve the rest of the messages. Which API constraint is described in this scenario?
- A. payload limiting
- B. throttling
- C. pagination
- D. rate limiting
Correct Answer: C
Community vote distribution
C (100%)
Question #101
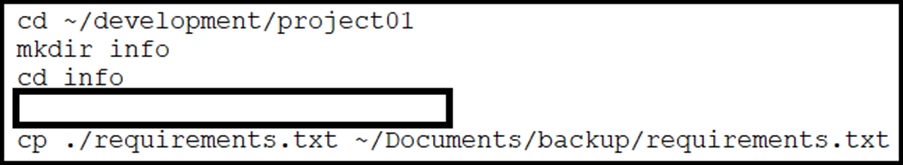
Refer to the exhibit. A developer just finished testing a Python script and wants to save the list of packages and versions installed on the current machine. The developer must make sure that it will not cause any issues if tested on another device due to different library versions. Which line of code needs to be placed on the snippet where the code is missing?
- A. pip freeze 2> requirements.txt
- B. pip freeze > requirements.txt
- C. pip freeze => requirements.txt
- D. pip freeze | requirements.txt
Correct Answer: B
Community vote distribution
B (100%)
Question #102
A developer pushes an application to production. The application receives a webhook over HTTPS without a secret. The webhook information contains credentials to service in cleartext. When the information is received, it is stored in the database with an SHA-256 hash. Credentials to the database are accessed at runtime through the use of a vault service. While troubleshooting, the developer sets the logging to debug to view the message from the webhook. What is the security issue in this scenario?
- A. Database credentials should be accessed by using environment variables defined at runtime.
- B. During the transport of webhook messages, the credentials could be unencrypted and leaked.
- C. During logging, debugging should be disabled for the webhook message.
- D. Hashing the credentials in the database is not secure enough; the credentials should be encrypted.
Correct Answer: B
Community vote distribution
B (64%)
A (18%)
C (18%)
Question #103
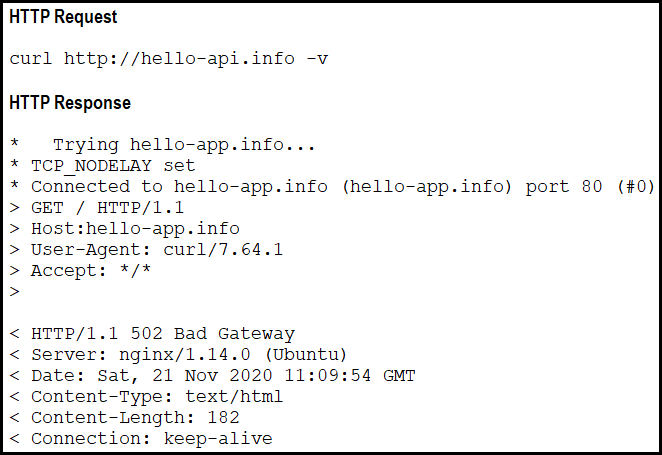
Refer to the exhibit. A developer cannot reach the web application behind an NGINX load balancer. The developer sends a request to an application FQDN with cURL but gets an HTTP 502 response. Which action solves the problem?
- A. Fix errors in the server configuration, which is behind the load balancer.
- B. Bring up the load balancer to the active state.
- C. Fix errors in the cURL request sent by the client.
- D. Change the default gateway on the load balancer to an active one.
Correct Answer: D
Community vote distribution
A (71%)
D (29%)
Question #104
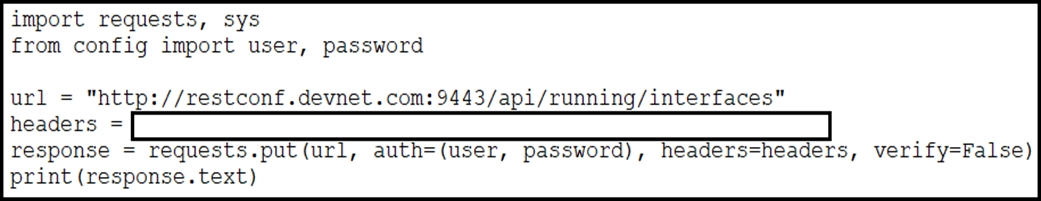
Refer to the exhibit. A network engineer wants use API update information about device interfaces. The network devices are deployed in a Cisco DevNet Sandbox and have running interfaces. Which value is suitable as the headers variable?
- A. {‘Content-Type’: ‘application/yang.data+yaml’, ‘Accept’: ‘application/yang.data+yaml’}
- B. {‘Content-Type’: ‘application/yang.data+json’, ‘Accept’: ‘application/yang.data+json’}
- C. {‘Content-Type’: ‘application/yang.data+utf8l’, ‘Accept’: ‘application/yang.data+utf8’}
- D. {‘Content-Type’: ‘application/restconf.data+txt’, ‘Accept’: ‘application/restconf.data+txt’}
Correct Answer: B
Community vote distribution
B (100%)
Question #105
Which action do webhooks enable an application to perform?
- A. Increase the request rate limit.
- B. Populate the application with restricted data.
- C. Receive real-time data.
- D. Implement a push model.
Correct Answer: D
Community vote distribution
D (50%)
C (38%)
Question #106
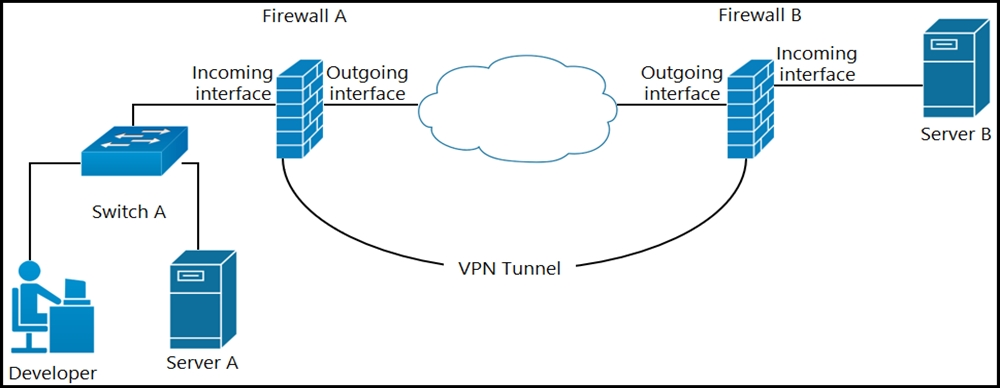
Refer to the exhibit. A developer can access the TLS REST API on server A, but cannot access the API on server B. The developer can ping server B. When the developer performs a packet capture on the TLS REST API port on server B, the capture shows that the packet arrived and the server responded. What causes the issue?
- A. Port 80 is blocked on the outgoing interface of firewall B.
- B. Port 443 is blocked on the outgoing interface of firewall A.
- C. Port 443 is blocked on the incoming interface of firewall B.
- D. Port 80 is blocked on the incoming interface of firewall A.
Correct Answer: C
Community vote distribution
C (100%)
Question #107
DRAG DROP –
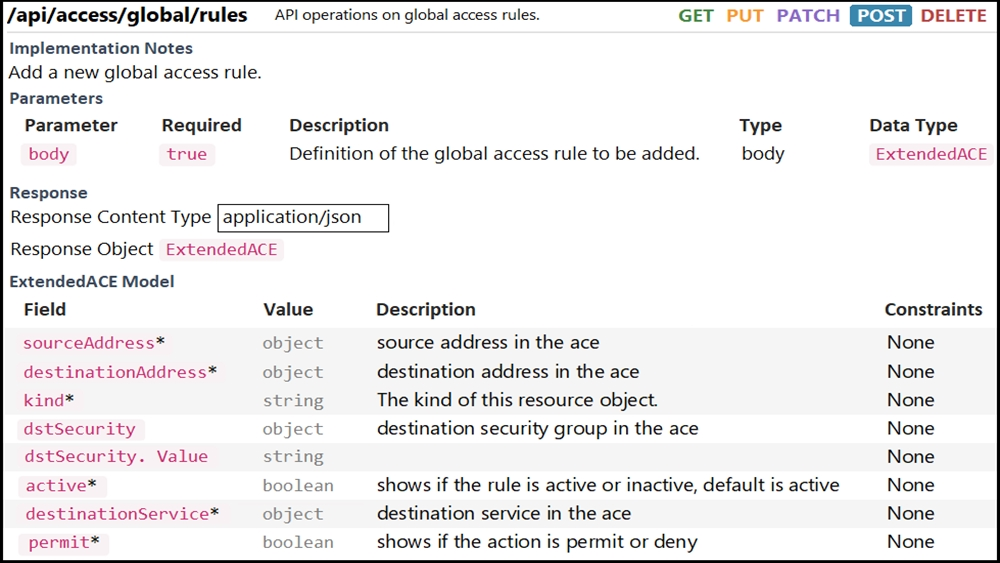
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to complete the function that adds a new global access rule that denies traffic using the Cisco ASA REST API. Not all options are used.
Select and Place:
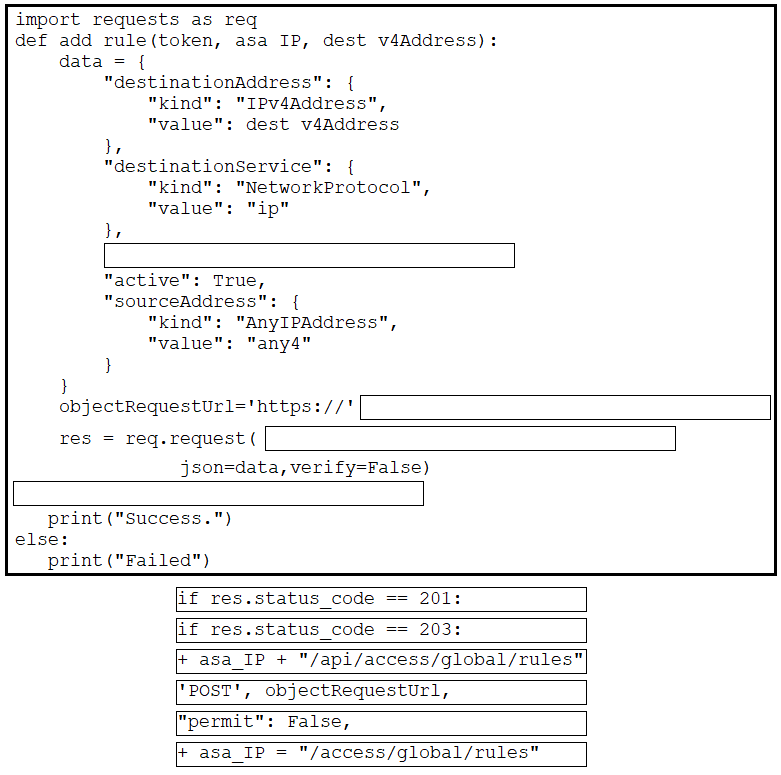
Correct Answer: 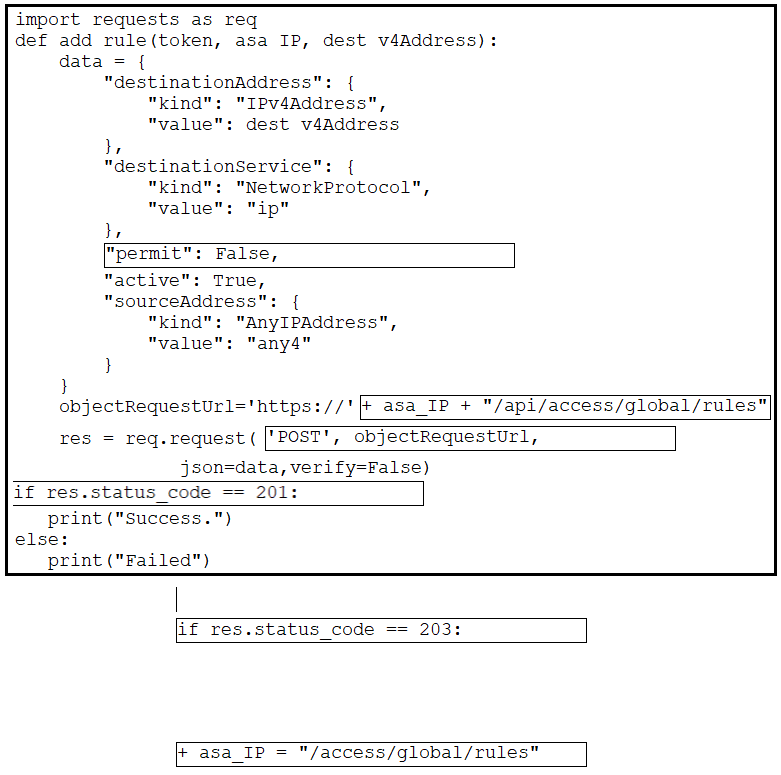
Question #108
DRAG DROP –
Drag and drop the API characteristics from the left onto the categories on the right.
Select and Place:
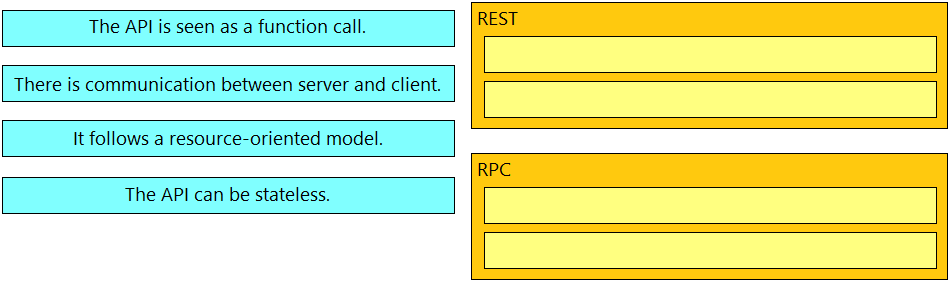
Correct Answer: 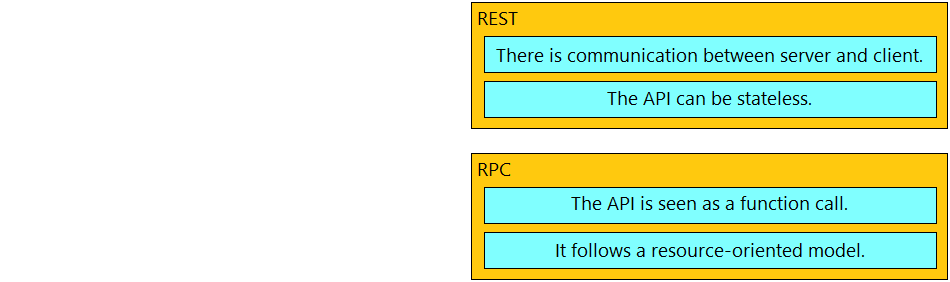
Question #109
How are operations on REST APIs performed as compared to RPC APIs?
- A. In a REST API, operations are performed on an object (node) that is identified by a URL, but RPC APIs are operation-oriented.
- B. In a REST API, operations are performed on an external resource that is defined on the API, but the RCP APIs are resource-oriented.
- C. In a REST API, operations are performed on a platform that is identified by the URL, but RPC APIs are platform-oriented.
- D. In a REST API, operations are performed on an internal resource that is defined on the API, but RPC APIs are resource-oriented.
Correct Answer: A
Community vote distribution
A (75%)
D (25%)
Question #110
Which HTTP error code series relates to redirection?
- A. 400
- B. 500
- C. 200
- D. 300
Correct Answer: D
Reference:
https://moz.com/learn/seo/http-status-codes
Community vote distribution
D (100%)
Question #111
Which platform has an API that can be used to obtain a list of vulnerable software on user devices?
- A. Cisco Umbrella
- B. Cisco Firepower
- C. Cisco Identity Services Engine
- D. Cisco Advanced Malware Protection
Correct Answer: D
Community vote distribution
D (100%)
Question #112
Which two items are Cisco DevNet resources? (Choose two.)
- A. TAC Support
- B. Software Research
- C. API Documentation
- D. Bitbucket
- E. Sandbox
Correct Answer: CE
Reference:
https://developer.cisco.com/
Community vote distribution
CE (100%)
Question #113
FILL BLANK –
Fill in the blanks to complete the Python script to update the Webex Teams membership of a room using the Python requests library. import requests url = `https://api.ciscospark.com/v1/memberships/
Y2lzY29zcGFyazov379971079INISVAvOTJiM2RkOWEtNjc1ZC00YTQxLThjNDEtMmFiZGY4OWY0NGY0OjExNzJkNmYwLTJIYzMtMTFIOS1iOWI3LWNmMjg3M
TJhYTkzNw`
my_token = `AbCdEf123456`
payload = `{\n \`isModerator\`: true\n}`
headers = {
‘Authorization’: ‘Bearer’ + my_token,
‘Content-Type’: ‘application/json’
}
response = requests. ___________ (`PATCH`, url, headers= ___________, data = ____________ ) print(response.text.encode(‘utf8’))
Correct Answer: See explanation below.
response = requests.request(ג€PATCHג€, url, headers= headers, data = payload ) print(response.text.encode(‘utf8’))
Question #114
While developing a real-time VoIP application on a Cisco Webex platform, users report that their voice gets chopped or parts of the conversation drop out. Which network constraint is impacting the application?
- A. jitter
- B. capacity
- C. delay
- D. latency
Correct Answer: A
Community vote distribution
A (67%)
B (33%)
Question #115
FILL BLANK –
Refer to the exhibit.
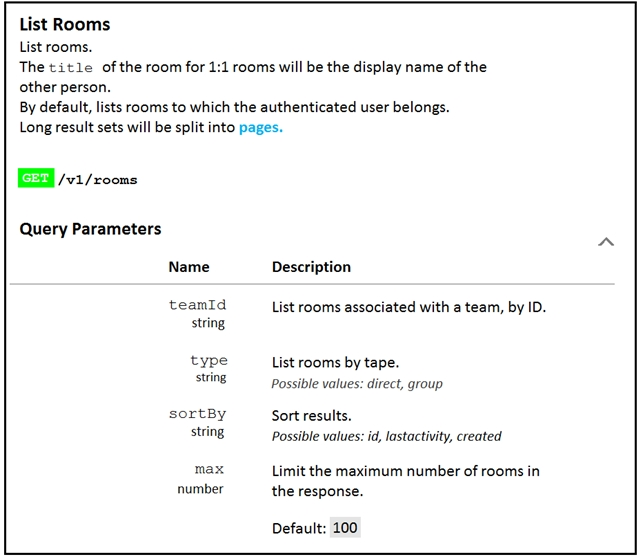
Fill in the blank to complete the query parameter and value so that the result set is returned in reverse chronological order (most recent first) based on when messages were posted to those rooms.
HTTP GET /v1/rooms ________________
Correct Answer: See explanation below.
GET/v1/rooms{?teamId,type,sortBy,max}
Reference:
https://developer.webex.com/docs/api/v1/rooms/list-rooms
Question #116
A company has written a script that creates a log bundle from the Cisco DNA Center every day. The script runs without error and the log bundles are produced.
However, when the script is run during business hours, people report poor voice quality of phone calls. What explains this behavior?
- A. The script is written in a low-level programming language where there is no memory safety. This causes a buffer overflow and disruption on the network.
- B. The speed and duplex settings in Cisco DNA Center are set incorrectly, which causes the transfer to be too slow.
- C. The script is running in the Voice VLAN and causes delays and jitter in the subnet.
- D. Generating the logs causes the CPU on the network controller to spike, which causes delays in forwarding the voice IP packets.
Correct Answer: C
Community vote distribution
C (50%)
D (43%)
Question #117
FILL BLANK –
Fill in the blanks to complete the statement.
Cisco DNA Center provides the capability to send an HTTP _______________ request to the API endpoint https://DNA-C_API_ADDRESS/api/v1/ network-device/and receive a list of network _______________ in _______________ format.
Correct Answer: See explanation below.
get
device
json
Question #118
FILL BLANK –
Fill in the blanks to complete the Python script to retrieve a list of network devices using the Cisco DNA Center API. my_token=
‘eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzl1NiJ9.ey.JzdWliOil1ZDE0OWZkMjhlZTY2
MmQ3NGM5YzE5ZTliLmYzMClslmV4cCI6MTU3MjM3ODE5MCwidXNlcm5hbWUiOiJraX
N370940885.zhK5LPQd501ZUpZI0IH_qrgOXttlNbxSFFF7JOEtRls’
import requests
url = `https://myDNAserver/dna/intent/api/v1/network-device`
payload = {}
headers = {‘x-auth-token’: my_token}
response = requests.request( _______________________ , url,
headers = _________________________, data = _______________________ ) print(response.text.encode(‘utf8’))
Correct Answer: See explanation below.
response = requests.request( method , url,
headers = headers, data = request.get_data )
print(response.text.encode(‘utf8’))
Reference:
https://www.programcreek.com/python/example/64946/flask.request.get_data
Question #119
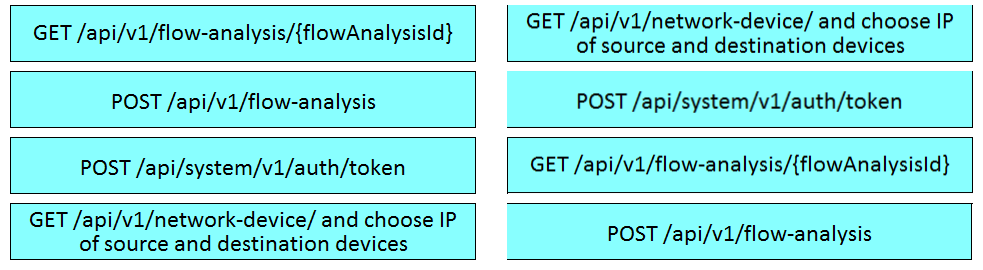
DRAG DROP –
Drag and drop the requests from the left into the order on the right to create and check the path trace between two devices using Cisco DNA center API.
Select and Place:
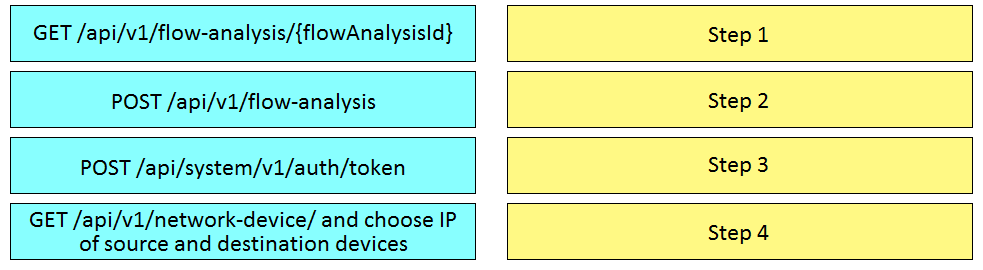
Correct Answer: