Free Cisco Dump, Free Dumps
Free 300-415 ENSDWI Dump
Lưu ý: Free 300-415 ENSDWI Dump chỉ dành cho mục đích học tập và làm quen với bài thi. Nội dung của Free 300-415 ENSDWI Dump không được cập nhật mới nhất nên không đảm bảo Pass Exam. Liên hệ ITexamViet để Pass Exam Nhanh Nhất.
Mục lục
Multiple Choice
QUESTION 1
To configure file analysis for Advanced Malware Protection, which tasks are valid? (Choose three.)
A. Configure Threat Grid API key.
B. Configure file types list.
C. Enable file analysis.
D. Enable HTTPS inbound to the WAN Edge router.
E. Configure a security rule for Threat Grid.
Correct Answer: ABC
QUESTION 2
How many packets are in a single FEC block?
A. One data packet, one parity packet
B. One data packet, four parity packets
C. Two data packets, one parity packet
D. Four data packets, one parity packet
E. The value is configurable in the policy.
Correct Answer: E
QUESTION 3
How does the Cisco SD-WAN architecture differ from traditional WAN technologies? (Choose three.)
A. Single pane of glass
B. Increased scale with centralized control plane
C. Reduced uptime in branch locations
D. Topology dependence
E. Distributed architecture
Correct Answer: ABE
QUESTION 4
Cisco Cloud onRamp for Colocation supports which two types of service insertion?
A. Control policy
B. Local policy
C. Data policy
D. CLI policy
E. OMP policy
Correct Answer: AC
QUESTION 5
What is an attribute of TLOC?
A. tag
B. service
C. local preference
D. encryption
Correct Answer: A
QUESTION 6
What is the behavior of vBond orchestrator?
A. It builds permanent connections with vSmart controllers.
B. It builds permanent connections with WAN Edge routers.
C. It updates vSmart of WAN Edge routers behind NAT devices using OMP.
D. It maintains vSmart and WAN Edge routers secure connectivity state.
Correct Answer: A
QUESTION 7
Which routing protocol is used to exchange control plane information between vSmart controllers and WAN Edge routers in the Cisco SD-WAN secure extensible network?
A. BGP
B. OSPF
C. BFD
D. OMP
Correct Answer: D
QUESTION 8
What is a requirement for a WAN Edge to reach vManage, vBond, and vSmart controllers in a data center?
A. OMP
B. IGP
C. QoS
D. TLS
Correct Answer: D
QUESTION 9
Which set of elements are verified by the controller to confirm the identity of edge devices?
A. certificates, organization name, and serial number of the device
B. organization name, serial number, and system IP of the device
C. certificates, organization name, and vBond domain
D. certificates, system IP, and vBond domain
Correct Answer: A
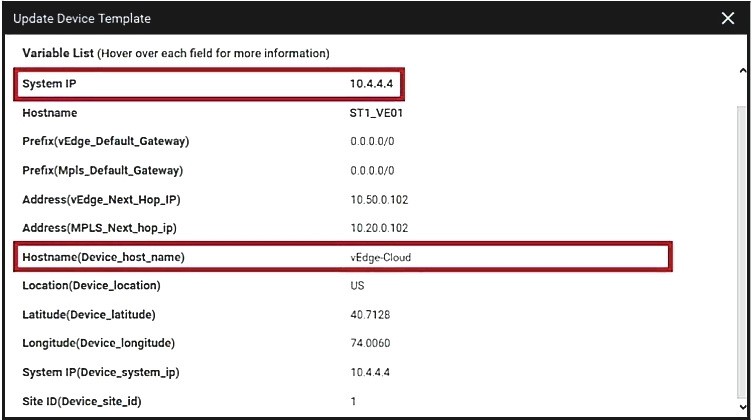
QUESTION 10
Refer to the exhibit. vManage and vBond have an issue establishing a connection with each other. Which action resolves the issue?
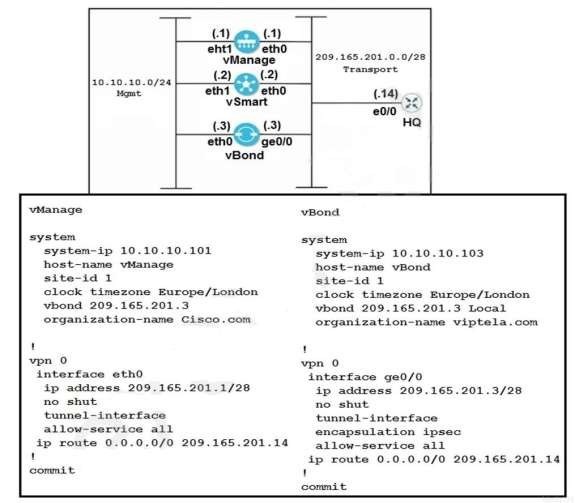
A. Change the organization name on both controllers to match viptela.com.
B. Configure the encapsulation ipsec command under the tunnel interface on vManage.
C. Reconfigure the system IPs to belong to the same subnet.
D. Remove the encapsulation ipsec command under the tunnel interface of vBond.
Correct Answer: A
QUESTION 11
Refer to the exhibit. An engineer is getting a CTORGNMMIS error on a controller connection. Which action resolves this issue?
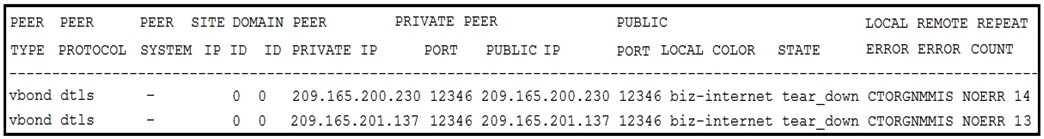
A. Configure a valid certificate on vSMART.
B. Configure a valid organization name.
C. Configure a valid serial number on the WAN Edge.
D. Configure a valid product ID.
Correct Answer: B
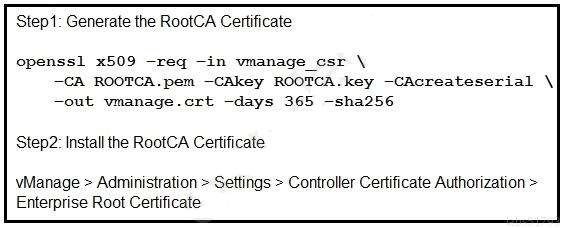
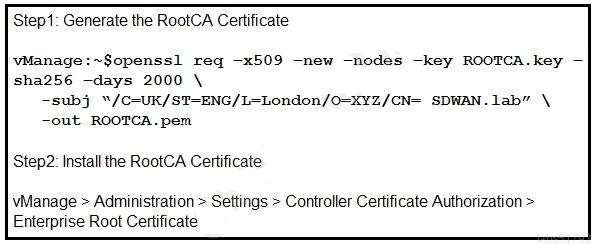
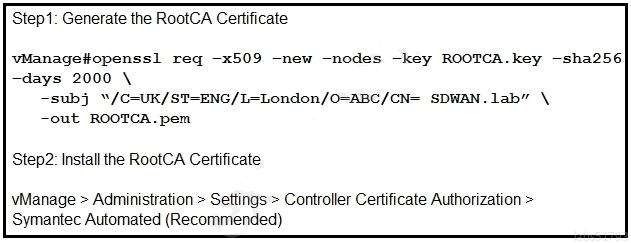
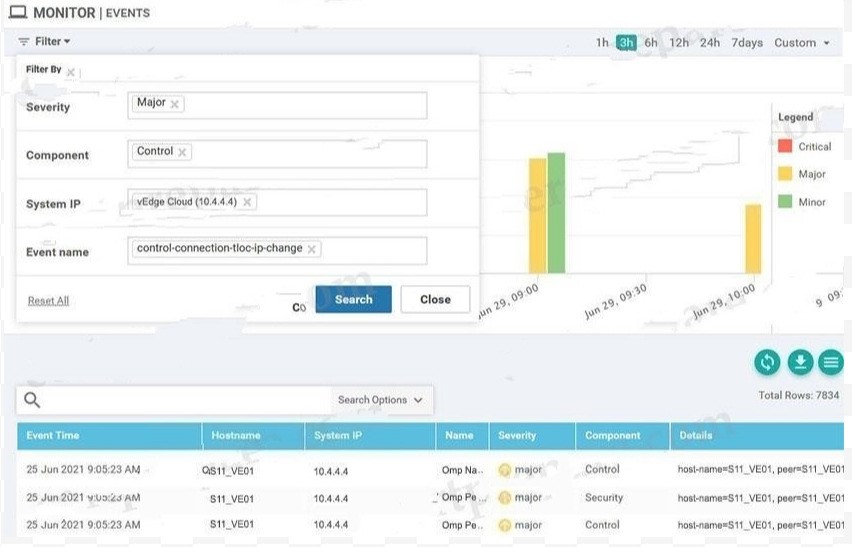
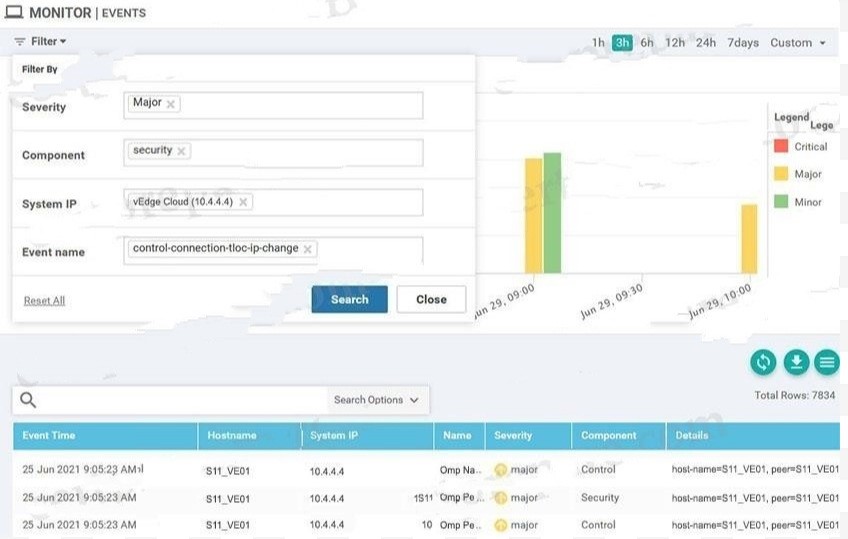
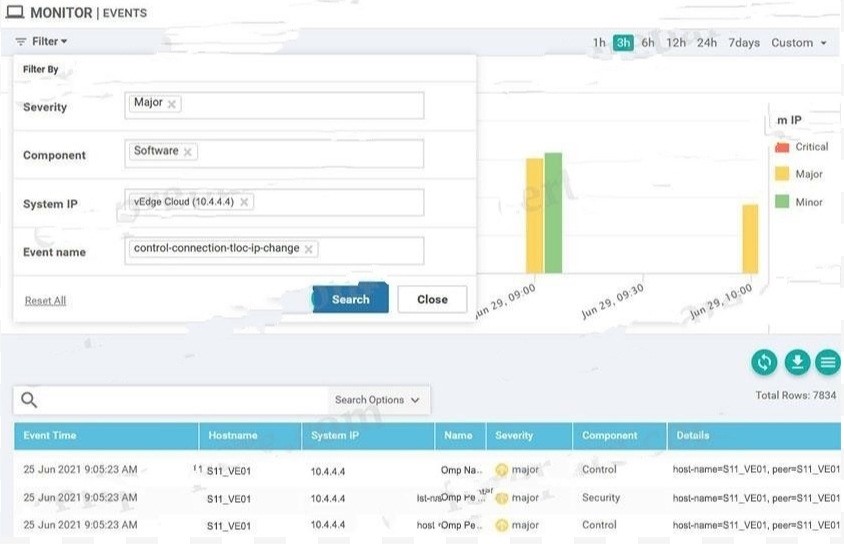
QUESTION 12
Refer to the exhibit. A small company was acquired by a large organization. As a result, the new organization decided to update information on their Enterprise RootCA and generated a new certificate using openssl. Which configuration updates the new certificate and issues an alert in vManage Monitor | Events Dashboard?
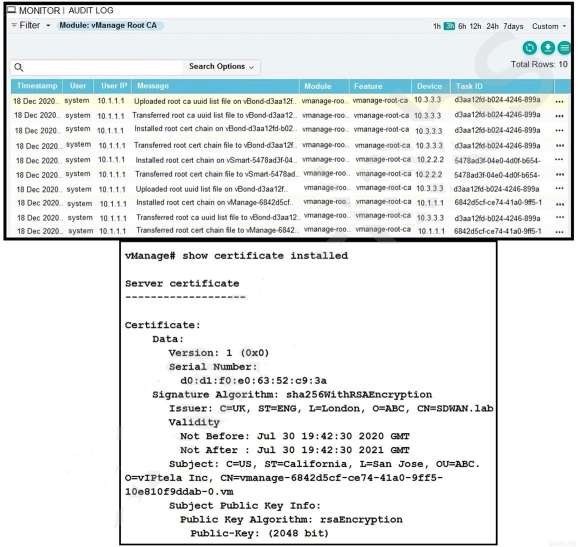
A.
B.
C.

D.
Correct Answer: B
QUESTION 13
Which third-party Enterprise CA server must be used for a cloud-based vSmart controller?
A. RootCert
B. VeriSign
C. Microsoft
D. RADIUS
Correct Answer: A
QUESTION 14
Refer to the exhibit. Which configuration value is used to change the administrative distance of iBGP routes to 20?

A. Configure Internal Routes Distance to 10.
B. Configure Propagate AS Path to off.
C. Configure Local Routes Distance to 20.
D. Configure External Routes Distance to 20.
Correct Answer: C
QUESTION 15
How is multicast routing enabled on devices in the Cisco SD-WAN overlay network?
A. The WAN Edge routers originate multicast service routes to the vSmart controller via OMP, which then forwards joins for requested multicast groups based on IGMP v2 or v3 toward the source or PIM-RP as specified in the original PIM join message.
B. The WAN Edge routers originate multicast service routes to the vSmart controller via OMP, which then forwards joins for requested multicast groups based on IGMP v1 or v2 toward the source or PIM-RP as specified in the original PIM join message.
C. The vSmart controller originates multicast service routes to the WAN Edge routers via OMP, which then forwards joins for requested multicast groups based on IGMP v1 or v2 toward the source or PIM-RP as specified in the original PIM join message.
D. The vSmart controller originates multicast service routes to the WAN Edge routers via OMP, which then forwards joins for requested multicast groups based on IGMP v2 or v3 toward the source or PIM-RP as specified in the original PIM join message.
Correct Answer: B
QUESTION 16
An engineer must configure a centralized policy on a site in which all HTTP traffic should use the Public Internet circuit if the loss on this circuit is below 10%, otherwise MPLS should be used. Which configuration wizard fulfills this requirement?
A. Create Applications or Groups of Interest > Configure Traffic Data > Apply Policies to Sites and VPNs.
B. Configure VPN Membership > Apply Policies to Sites and VPNs.
C. Create Applications or Groups of Interest > Configure Traffic Rules > Apply Policies to Sites and VPNs.
D. Configure Topology > Apply Policies to Sites and VPNs.
Correct Answer: C
QUESTION 17
An engineer must use data prefixes to configure centralized data policies using the vManage policy configuration wizard. What is the first step to accomplish this task?
A. Configure network topology.
B. Apply policies to sites and VPNs.
C. Configure traffic rules.
D. Create groups of interest.
Correct Answer: D
QUESTION 18
Refer to the exhibit. The Cisco SD-WAN network is configured with a default full-mesh topology. Islamabad HQ and Islamabad WAN Edges must be used as the hub sites. Hub sites MPLS TLOC must be preferred when forwarding FTP traffic based on a configured SLA class list. Which policy configuration does the network engineer use to call the SLA class and set the preferred color to MPLS?
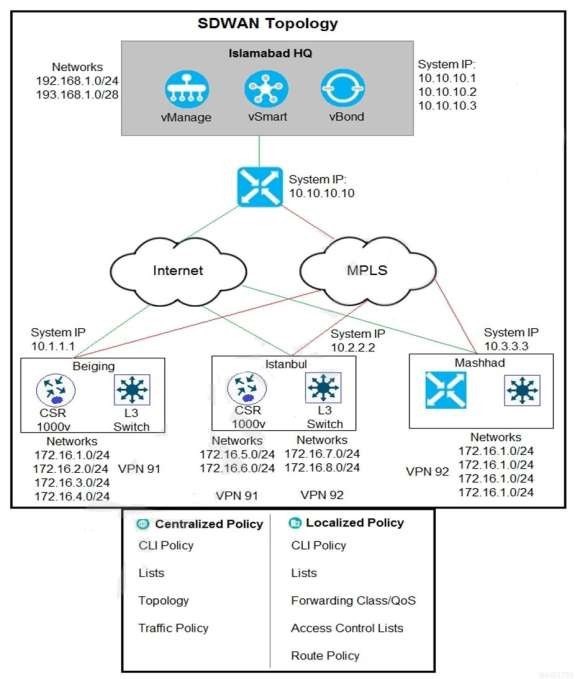
A. Centralized Policy, Traffic Policy
B. Centralized Policy, Topology
C. Localized Policy, Forwarding Class
D. Localized Policy, Route Policy
Correct Answer: A
QUESTION 19
Refer to the exhibit. Which command allows traffic through the IPsec tunnel configured in VPN 0?

A. service netsvc1 vpn1
B. service netsvc1 address 1.1.1.1
C. service FW address 1.1.1.1
D. service local
Correct Answer: B
QUESTION 20
Refer to the exhibit. Which configuration sets up direct Internet access for VPN 1?
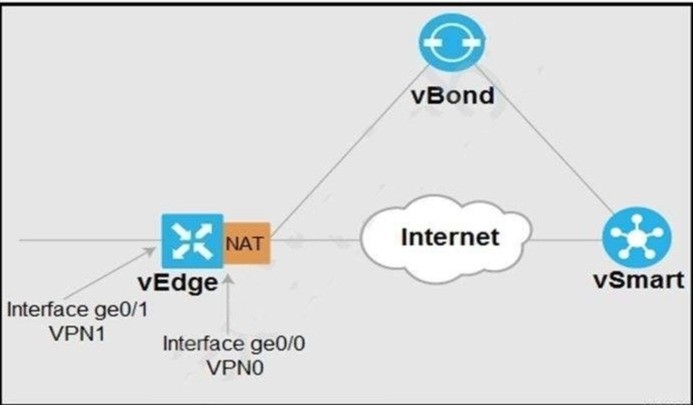
A.

B.

C.

D.

Correct Answer: B
QUESTION 21
An enterprise has several sites with multiple VPNs that are isolated from each other. A new requirement came where users in VPN 73 must be able to talk to users in VPN 50. Which configuration meets this requirement?
A.
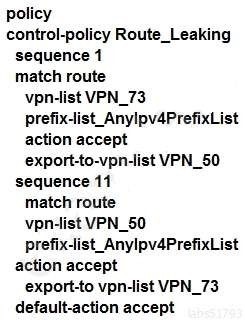
B.
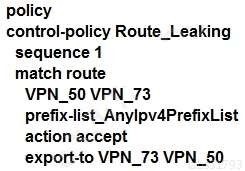
C.
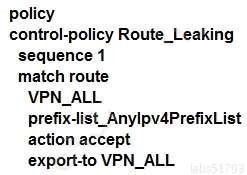
D.
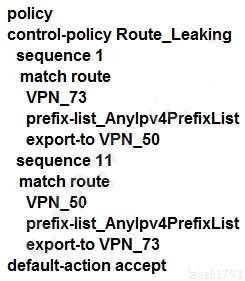
Correct Answer: A
QUESTION 22
The network administrator is configuring a QoS scheduling policy on traffic received from transport side tunnels on WAN Edge 5000 routers at location:405608122. Which command must be configured on these devices?
A. mls qos
B. cloud-qos
C. service qos
D. cloud-mls qos
Correct Answer: B
QUESTION 23
Which component of the Cisco SD-WAN secure extensible network provides a single pane of glass approach to network monitoring and configuration?
A. APIC-EM
B. vSmart
C. vManage
D. vBond
Correct Answer: C
QUESTION 24
Refer to the exhibit. A network administrator is setting the queueing value for voice traffic for one of the WAN Edge routers using vManagerGUI. Which queue value must be set to accomplish this task?

A. 0
B. 1
C. 2
D. 3
Correct Answer: A
QUESTION 25
An engineer is configuring a shaping rate of 1 Mbps on the WAN Edge router. Which configuration accomplishes this task? A.

B.

C.

D.

Correct Answer: D
QUESTION 26
An engineer must improve video quality by limiting HTTP traffic to the Internet without any failover. Which configuration in Manage achieves this goal?
A.
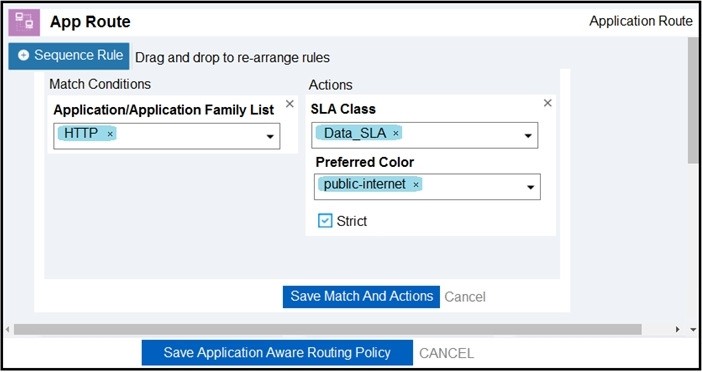
B.
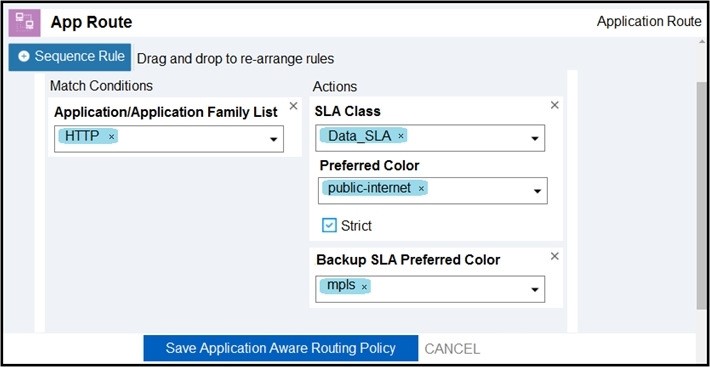
C.
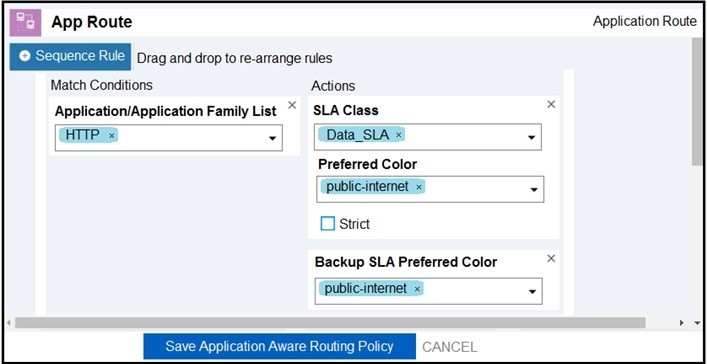
D.
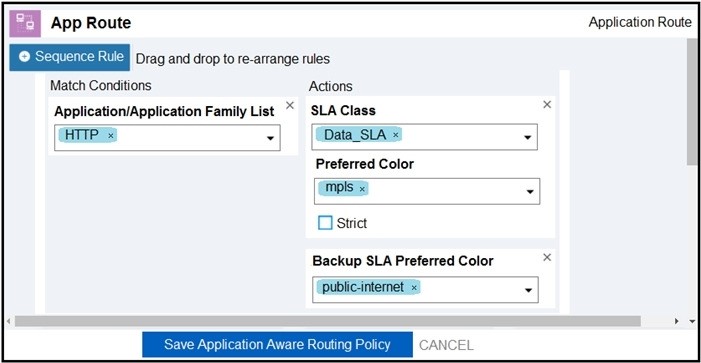
Correct Answer: A
QUESTION 27
An administrator must deploy the controllers using the On-Prem method while vManage can access the PnP portal from inside. How are the two WAN Edge authorized allowed lists to be made available to vManage? (Choose two)
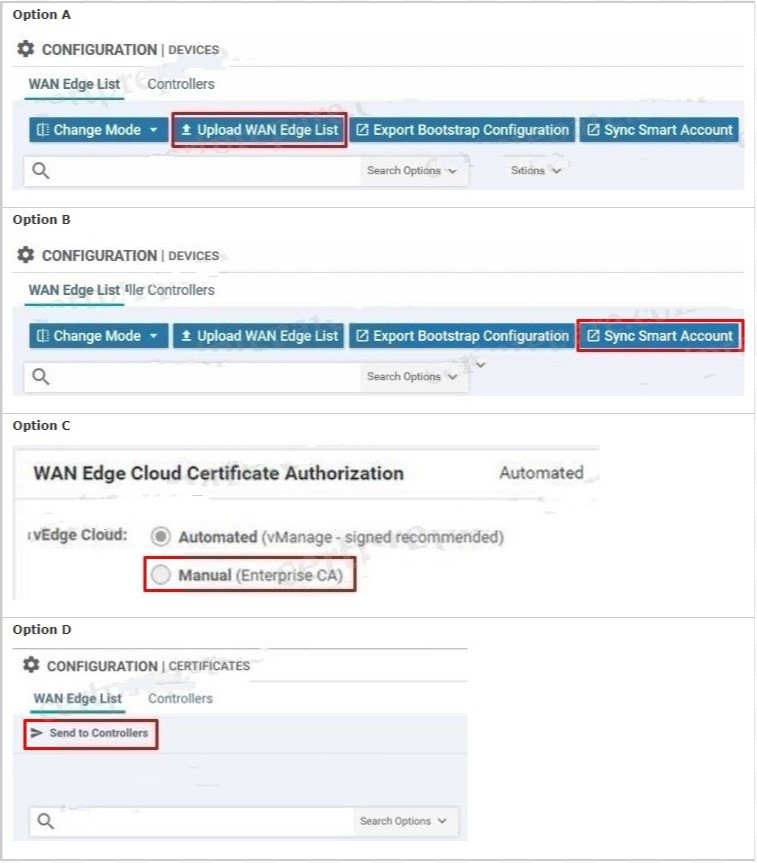
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: AB
QUESTION 28
What is a benefit of the application aware firewall feature in the Cisco SD-WAN solution?
A. application monitoring
B. application malware protection
C. application visibility
D. control policy enforcement
Correct Answer: C
QUESTION 29
A network administrator is configuring QoS on a Vedge 5000 router and needs to enable it on the transport side interface. Which policy setting must be selected to accomplish this goal?
A. Cloud QoS Service side
B. Cloud QoS
C. Netflow
D. Application
Correct Answer: B
QUESTION 30
A policy is created to influence routing path in the network using a group of prefixes. What policy application will achieve this goal when applied to a site list?
A. control-policy
B. vpn-membership policy
C. app-route policy
D. cflowd-template
Correct Answer: A
QUESTION 31
An engineer wants to track tunnel characteristics within a SLA-based policy for convergence. Which policy configuration will achieve this goal?
A. Data policy
B. Control policy
C. App-route policy
D. VPN membership policy
Correct Answer: C
QUESTION 32
Refer to the exhibit.
vEdge-2(config-vpn-0)#interface ge0/2.101 vEdge-2(config-interface)#ip address 10.1.100.0/24 vEdge-2(config-interface)#tloc-extension ge0/0 vEdge-2(config-interface)#mtu 1496 vEdge-2(config-interface)#no shutdown
What binding is created using the tloc-extension command?
A. between ge0/2.101 of port-type transport and ge0/0 of port-type service
B. between ge0/2.101 of port-type service and ge0/0 of port-type service
C. between ge0/2.101 of port-type service and ge0/0 of port-type transport
D. between ge0/2.101 of port-type transport and ge0/0 of port-type transport
Correct Answer: D
QUESTION 33
Which two algorithms authenticate a user when configuring SNMPv3 monitoring on a WAN Edge router? (Choose two)
A. AES-256 B. SHA-1
C. AES-128
D. MD5
E. SHA-2
Correct Answer: DE
QUESTION 34
A network administrator is configuring an application-aware firewall between inside zones to an outside zone on a WAN edge router using vManage GUI. What kind of inspection is performed when the “inspect” action is used?
A. Layer 7 inspection for TCP and Layer 4 inspection for UDP
B. IPS inspection for TCP and-Layer 4 inspection for UDP
C. stateful inspection for TCP and stateless inspection of UDP
D. stateful inspection for TCP and UDP
Correct Answer: D
QUESTION 35
What is the purpose of “vpn 0” in the configuration template when onboarding a WAN edge node?
A. It carries control traffic over secure IPsec connections between vSmart controllers and vEdge routers, and between vEdge and vManager
B. It carries control out-of-band network management traffic among the Viptela devices in the overlay network.
C. It carries control traffic over secure DTLS or TLS connections between vSmart controllers and vEdge routers, and between vSmart and vBond
D. It carries control traffic over secure IPsec connections between vSmart controllers and vEdge routers, and between vSmart and vBond
Correct Answer: C
QUESTION 36
In Cisco SD-WAN, what protocol is used for control connections between SD-WAN devices?
A. BGP
B. OSPF
C. DTLS
D. OMP
Correct Answer: C
QUESTION 37
In an AWS cloud, which feature provision WAN Edge routers automatically in Cisco SD-WAN?
A. Cloud OnRamp
B. vAnalytics
C. Cloud app
D. Network Designer
Correct Answer: A
QUESTION 38
When a WAN Edge device joins the SD-WAN overlay, which Cisco SD-WAN components orchestrates the connection between the WAN Edge device and a vSmart controller?
A. OMP
B. vBond
C. vManage
D. APIC-EM
Correct Answer: B
QUESTION 39
A network administrator is bringing up one WAN Edge for branch connectivity. Which types of tunnels form when the WAN edge router connects to the SD-WAN fabric?
A. DTLS or TLS tunnel with vBond controller and IPsec tunnel with vManage controller
B. DTLS or TLS tunnel with vBond controller and IPsec tunnel with other WAN Edge routers
C. DTLS or TLS tunnel with vSmart controller and IPsec tunnel with other Edge routers
D. DTLS or TLS tunnel with vSmart controller and IPsec tunnel with vBond controller
Correct Answer: C
QUESTION 40
In the Cisco SD-WAN solution, vSmart controller is responsible for which two actions? (Choose two)
A. Authenticate and authorize vEdge routers.
B. Distribute the IP address from DHCP server to vEdge routers.
C. Distribute crypto key information among vEdge routers
D. Configure and monitor vEdge routers.
E. Distribute route and policy information via OMP.
Correct Answer: CE
QUESTION 41
Which device in the SD-WAN solution receives and categorizes event reports, and generates alarms?
A. vSmart controllers
B. WAN Edge routers
C. vBond controllers
D. vManage NMS
Correct Answer: D
QUESTION 42
An administrator needs to configure SD-WAN to divert traffic from the company’s private network to an ISP network. What action should be taken to accomplish this goal?
A. configure the data security policy
B. configure the application aware policy
C. configure the control policy
D. configure the data policy
Correct Answer: D
QUESTION 43
Which software security feature is supported by the Cisco ISR 4451 router?
A. IPsec/GRE cloud proxy
B. reverse proxy
C. Enterprise Firewall with Application Awareness
D. Cloud Express service
Correct Answer: C
QUESTION 44
Which feature builds transport redundancy by using the cross link between two redundant WAN Edge routers?
A. OMP
B. TLOC extension
C. quality of service
D. zero-touch provisioning
Correct Answer: B
QUESTION 45
An engineer is configuring a centralized policy to influence network route advertisement. Which controller delivers this policy to the fabric?
A. vSmart
B. vBond
C. WAN Edge
D. vManage
Correct Answer: A
QUESTION 46
Which two WAN Edge devices should be deployed in a cloud? (Choose two)
A. vEdge 100wm
B. ASR 1000v
C. CSR 1000v
D. vEdge 5000v
E. vEdge cloud
Correct Answer: CE
QUESTION 47
Which two products that perform lifecycle management for virtual instances are supported by WAN Edge cloud routers? (Choose two)
A. OpenStack
B. VMware vCenter
C. AWS
D. IBM Cloud
E. Azure
Correct Answer: AB
QUESTION 48
Which secure connection should be used to access the REST APIs through the Cisco vManage web server?
A. HTTP inspector interface
B. authenticated HTTPS
C. authenticated DTLS
D. JSON Inspector interface
Correct Answer: B
QUESTION 49
What is a description of vManage NMS?
A. A cluster requires device templates to be created on and attached to the same server
B. It is accessible only from VPN 512 (the management VPN)
C. It is a software process on a dedicated WAN Edge router in the network
D. A cluster consists of a minimum of two vManage NMSs
Correct Answer: A
QUESTION 50
In which device state does the WAN edge router create control connections, but data tunnels are not created?
A. valid
B. backup
C. active
D. staging
Correct Answer: D
QUESTION 51
Refer to the exhibit.
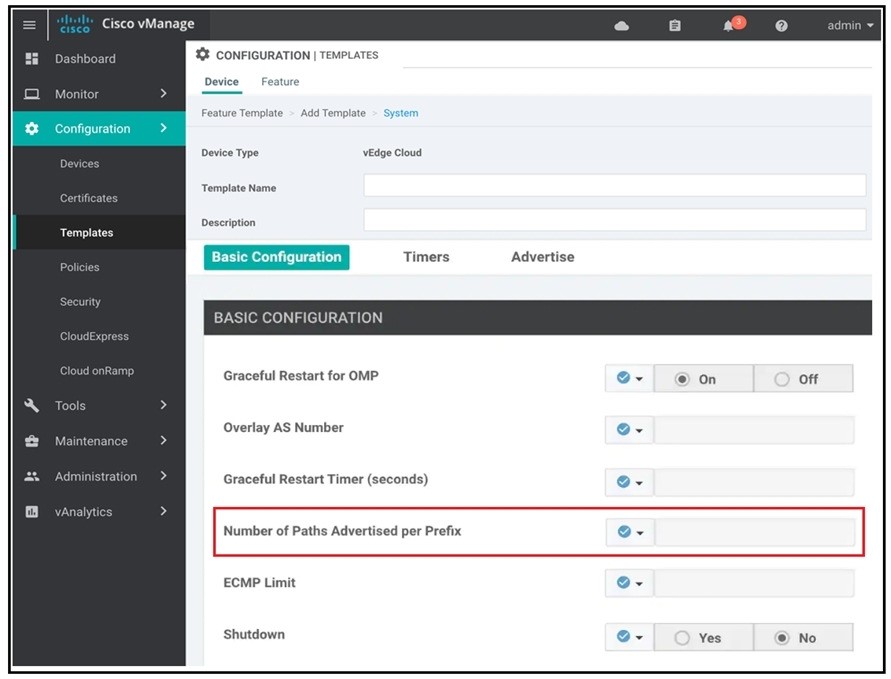
A network administrator is configuring OMP in vManage to advertise all the paths for the same prefix from a site that has two WAN Edge devices. Each WAN Edge device is connected to three ISPs and two private MPLS transports. What is the minimum value for `Number of Paths advertised per Prefix” that should be configured?
A. 2
B. 3
C. 5
D. 10
Correct Answer: D
QUESTION 52
A network administrator is configuring a tunnel interface on a branch Cisco IOS XE router to run TLOC extensions. Which configuration will extend a TLOC over a GRE tunnel to another router in the branch?
A.

B.

C.
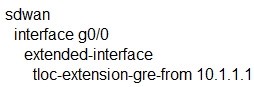
D.
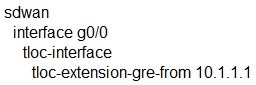
Correct Answer: B
QUESTION 53
If Smart Account Sync is not used, which Cisco SD-WAN component is used to upload an authorized serial number file?
A. vSmart
B. WAN Edge
C. vManage
D. vBond
Correct Answer: C
QUESTION 54
A network administrator is creating an OMP feature template from the vManage GUI to be applied to WAN edge routers. Which configuration attribute will avoid the redistribution of the routes back into the OMP from the LAN side?
A. configure “Number of Paths Advertised per Prefix”
B. configure “ECMP limit”
C. configure “Send Backup Paths”
D. configure “Overlay AS Number”
Correct Answer: D
QUESTION 55
An engineer is tasked to improve throughput for connection-oriented traffic by decreasing round- trip latency. Which configuration will achieve this goal?
A. turn on “Enable TCP Optimization”
B. turn off “Enable TCP Optimization”
C. turn off “Enhance ECMP Keying”
D. turn on “Enhance ECMP Keying”
Correct Answer: A
QUESTION 56
Which VPN connects the transport-side WAN Edge interface to the underlay/WAN network?
A. VPN 0
B. VPN 1
C. VPN 511
D. VPN 512
Correct Answer: A
QUESTION 57
Which port is used for vBond under controller certificates if no alternate port is configured?
A. 12345
B. 12347
C. 12346
D. 12344
Correct Answer: C
QUESTION 58
A network administrator is tasked to make sure that an OMP peer session is closed after missing three consecutive keepalive messages in 3 minutes. Additionally, route updates must be sent every minute. If a WAN Edge router becomes unavailable, the peer must use last known information to forward packets for 12 hours. Which set of configuration commands accomplishes this task?
A.

B.

C.

D.

Correct Answer: D
QUESTION 59
Refer to the exhibit.
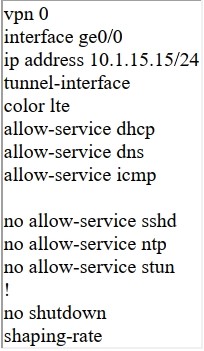
Which shaping-rate does the engineer use to shape traffic at 9 Mbps?
A. 9
B. 9000
C. 90000
D. 9000000
Correct Answer: B
QUESTION 60
Refer to the exhibit.
An engineer is configuring service chaining. Which set of configurations is required for all traffic from Site ID 1 going toward Site ID 2 to get filtered through the firewall on the hub site?
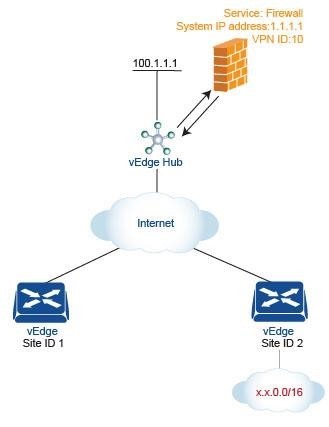
A.
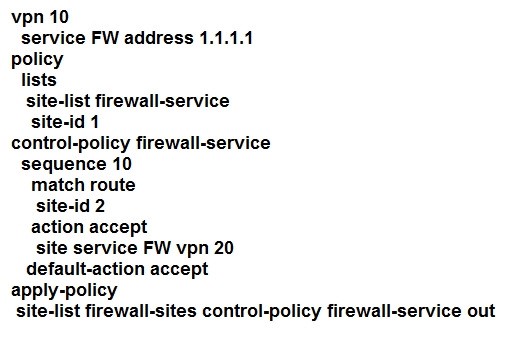
B.
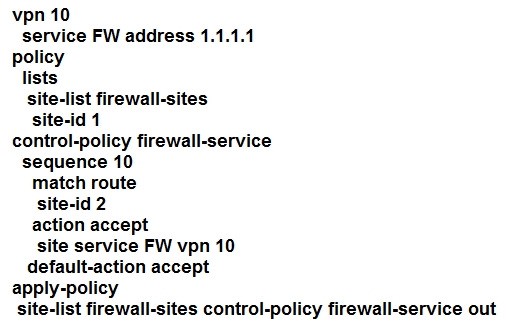
C.

D.
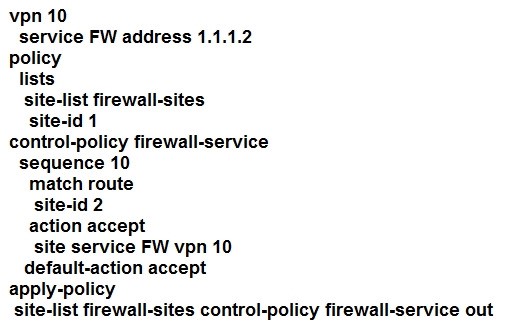
Correct Answer: B
QUESTION 61
In a Cisco SD-WAN architecture, what is the role of the WAN Edge?
A. It provides orchestration to assist in automatic provisioning of WAN Edge routers and overlay
B. It is the management plane responsible for centralized configuration and monitoring
C. It is the control plane that builds and maintains network topology
D. It is the data plane that is responsible for forwarding traffic
Correct Answer: D
QUESTION 62
Which two products are used to deploy Cisco WAN Edge Router virtual platforms? (Choose two)
A. HP ProLiant DL360 Generatton10 running HP-UX
B. Cisco ENCS 5000 Series
C. Sun SPARC Node running AIX
D. Cisco UCS
E. Sun Enterprise M4000 Server running Sun Solaris
Correct Answer: BD
QUESTION 63
A bank is looking for improved customer experience for applications and reduce overhead related to compliance and security. Which key feature or features of the Cisco SD-WAN solution will help the bank to achieve their goals?
A. integration with PaaS providers to offer the best possible application experience
B. QoS including application prioritization and meeting critical applications SLA for selecting optimal path
C. implementation of a modem age core banking system
D. implementation of BGP across the enterprise routing for selecting optimal path
Correct Answer: B
QUESTION 64
A large retail organization decided to move some of the branch applications to the AWS cloud. How does the network architect extend the in-house Cisco SD-WAN branch to cloud network into AWS? A. Create virtual WAN Edge devices Cloud through the AWS online software store
B. Create virtual instances of vSmart Cloud through the AWS online software store
C. Create GRE tunnels to AWS from each branch over the Internet
D. Install the AWS Cloud Router in the main data center and provide the connectivity from each branch
Correct Answer: A
QUESTION 65
An engineer is configuring a data policy for packets that must be captured through the policy. Which command accomplishes this task?
A. policy > data-policy > vpn-list > sequence > default-action > drop
B. policy > data-policy > vpn-list > sequence > match
C. policy > data-policy > vpn-list > sequence > default-action > accept
D. policy > data-policy > vpn-list > sequence > action
Correct Answer: D
QUESTION 66
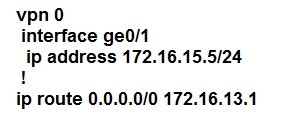
Refer to the exhibit.

The tunnel interface configuration on both WAN Edge routers is:

Which configuration for WAN Edge routers will connect to the Internet?
A.
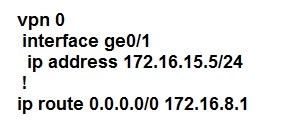
B.
C.
D.

Correct Answer: C
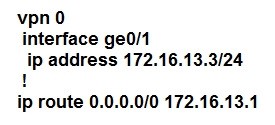
QUESTION 67
Refer to exhibit.
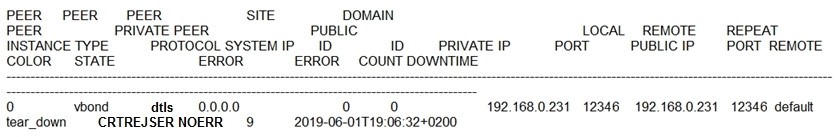
An engineer is troubleshooting tear down of control connections even though a valid CertificateSerialNumber is entered. Which two actions resolve the issue? (Choose two)
A. Enter a valid serial number on the controllers for a given device
B. Enter a valid product ID (model) on the PNP portal
C. Remove the duplicate IP in the network
D. Match the serial number file between the controllers
E. Restore network reachability for the controller
Correct Answer: AB
QUESTION 68
An engineer is configuring a list that matches all IP prefixes with lengths from /1 to /16 in a centralized control policy. Which list accomplishes this task?
A. 0.0.0.0/16 ge 1
B. 0.0.0.0/0 ge 1
C. 0.0.0.0/0 le l6
D. 0.0.0.0/1 le 16
Correct Answer: C
QUESTION 69
Where on vManage does an engineer find the details of control node failure?
A. Alarms
B. Events
C. Audit log
D. Network
Correct Answer: D
QUESTION 70
A network administrator is configuring VRRP to avoid a traffic black hole when the transport side of the network is down on the master device. What must be configured to get the fastest failover to standby?
A. lower timer interval
B. higher group ID number
C. OMP tracking
D. prefix-list tracking
Correct Answer: D
QUESTION 71
Which TCP Optimization feature is used by WAN Edge to prevent unnecessary retransmissions and large initial TCP window sizes to maximize throughput and achieve a better quality?
A. RTT
B. SYN
C. SEQ
D. SACK
Correct Answer: D
QUESTION 72 Refer to the exhibit.
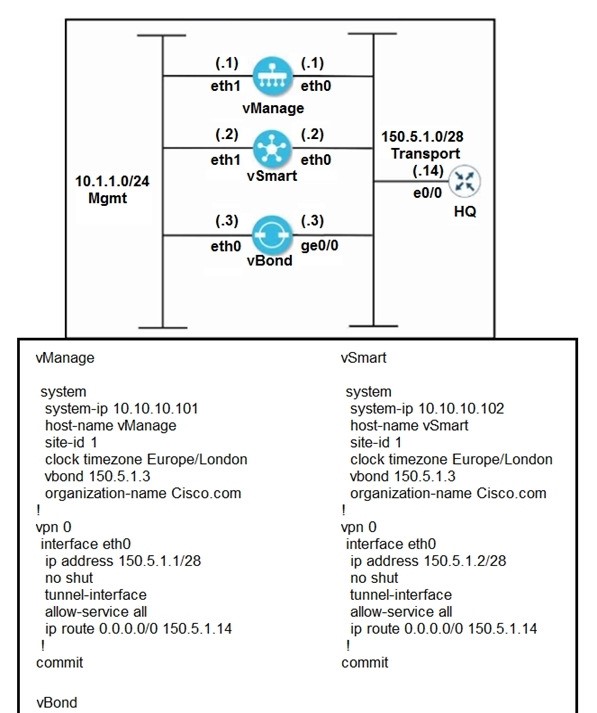
vBond
system
system-ip 10.10.10.103
host-name Bond
site-id 1
clock timezone Europe/London
bond 150.5.1.3
organization-name Cisco.com
!
vpn 0
interface ge0/0
ip address 150.5.1.3/28
no shut tunnel-interface
encapsultion ipsec
allow-service all
ip route 0.0.0.0/0 150.5.1.14
!
commit
An engineer is troubleshooting an issue where vManage and vSmart have a problem establishing a connection to vBond. Which action fixes the issue?
A. Remove the encapsulation ipsec command under the tunnel interface of vBond.
B. Configure the tunnel interface on all three controllers with a color of transport
C. Reconfigure the vbond command on the vBond as vbond 150.5.1.3 local
D. Configure encapsulation as IPsec under the tunnel interface of vManage and vSmart
Correct Answer: C
QUESTION 73
Company ABC has decided to deploy the controllers using the On-Prem method. How does the administrator upload the WAN Edge list to the vManage?
A.
B.

C.
D.
Correct Answer: D
QUESTION 74 Refer to the exhibit.
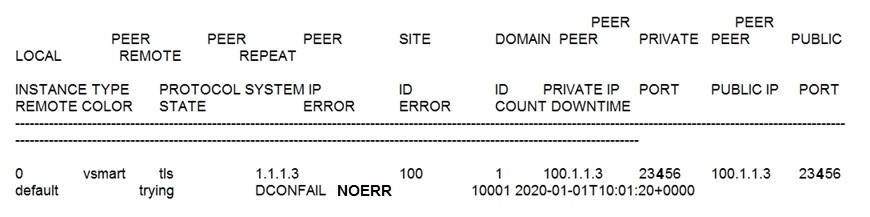
The control connection is failing. Which action resolves the issue?
A. import vSmart in vManager
B. Upload the WAN Edge list on vManage
C. Restore the reachability to the vSmart
D. Validate the certificates authenticity on vSmart
Correct Answer: C
QUESTION 75
Refer to the exhibit.
Which two configurations are needed to get the WAN Edges registered with the controllers when certificates are used? (Choose two)
A. Request a certificate manually from the Enterprise CA server
B. Generate a CSR manually on the WAN Edge
C. Generate a CSR manually within vManage server
D. Install the certificate received from the CA server manually on the WAN Edge
E. Install the certificate received from the CA server manually on the vManage
Correct Answer: CE
QUESTION 76
An administrator must configure an ACL for traffic coming in from the service-side VPN on a specific WAN Edge device with circuit ID 392318933. Which policy must be used to configure this ACL?
A. central control policy
B. central data policy
C. app-aware policy
D. local data policy
Correct Answer: D
QUESTION 77
Refer to the exhibit.
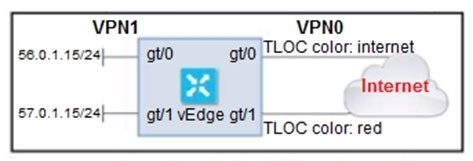
The ge0/0 interface connects to a 30-MB link A network administrator wants to always have 10 MB available for high priority traffic. When lower-priority traffic bursts exceed 20 MB, traffic should be redirected to the second WAN interface ge0/1.
Which set of configurations accomplishes this task?
A.
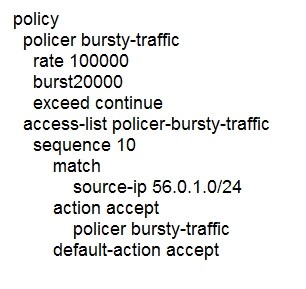
B.
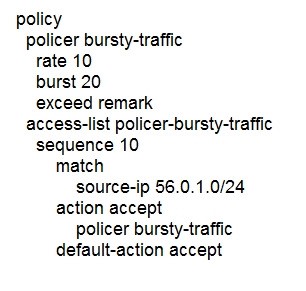
C.
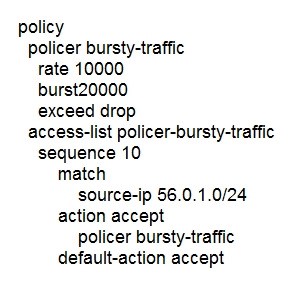
D.
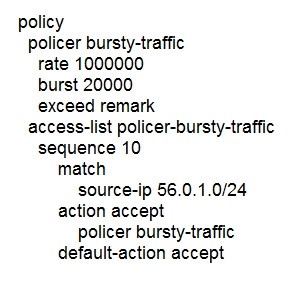
Correct Answer: D
QUESTION 78
An engineer is configuring a WAN Edge router for DIA based on matching QoS parameters. Which two actions accomplish this task? (Choose two)
A. Apply a QoS map policy.
B. Configure a control policy.
C. Configure a centralized data policy.
D. Configure NAT on the transport interface.
E. Apply a data policy on WAN interface.
Correct Answer: AC
QUESTION 79
An engineer is adding a tenant with location JD 306432373 in vManage. What is the maximum number of alphanumeric characters that are accepted in the tenant name field?
A. 8
B. 64
C. 256
D. 128
Correct Answer: D
QUESTION 80
Refer to the exhibit. Which configuration routes Site 2 through the firewall in Site 1?
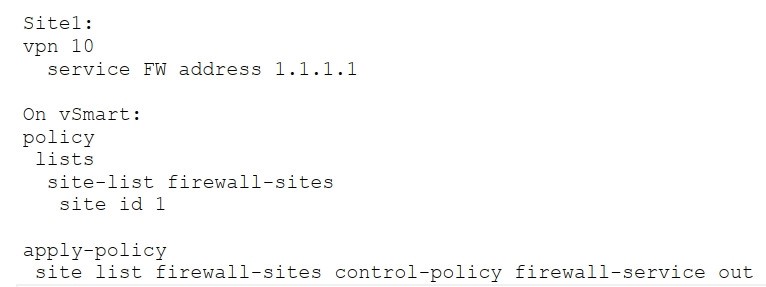
A.

B.
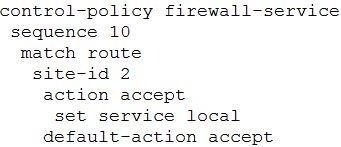
C.
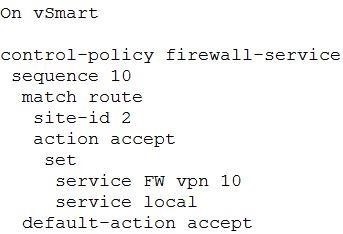
D.

Correct Answer: D
QUESTION 81
Refer to the exhibit. Which configuration stops Netconf CLI logging on WAN Edge devices during migration?

A.
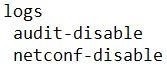
B.
![]()
C.
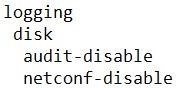
D.
![]()
Correct Answer: A
QUESTION 82
A network administrator is configuring a centralized control policy based on match action pairs for multiple conditions. Which order must be configured to prefer Prefix List over TLOC and TLOC over Origin?
A. highest to lowest sequence number
B. nonsequential order
C. deterministic order
D. lowest to highest sequence number
Correct Answer: D
QUESTION 83
A customer is receiving routes via OMP from vSmart controller for a specific VPN. The customer must provide access to the W2 loopback received via OMP to the OSPF neighbour on the service- side VPN. Which configuration fulfills these requirements?
A.
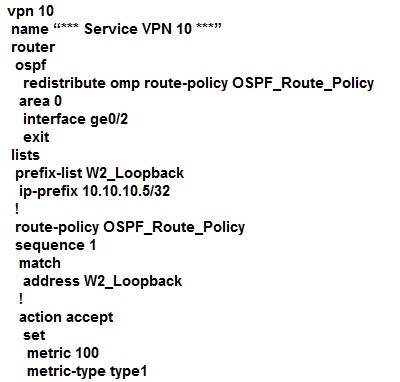
B.
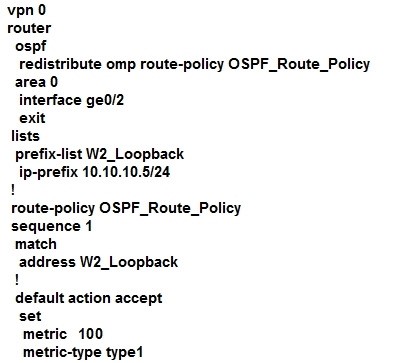
C.
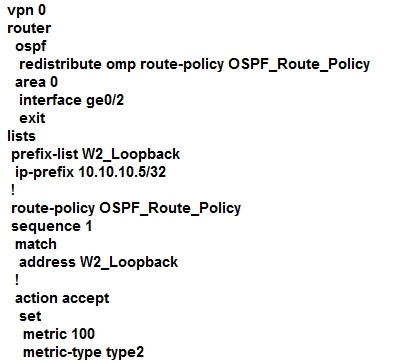
D.
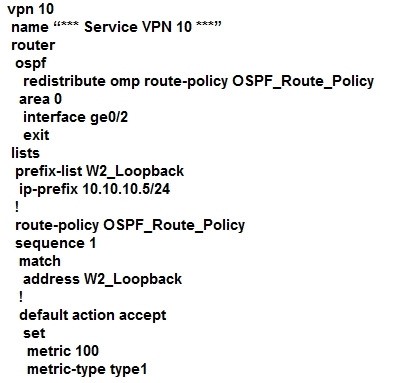
Correct Answer: D
QUESTION 84
Which plane assists in the automatic onboarding of the SD-WAN routers into the SD-WAN overlay?
A. Orchestration
B. Data
C. Management
D. Control
Correct Answer: A
QUESTION 85
Refer to the exhibit. Which configuration configures IPsec tunnels in active and standby?

A.
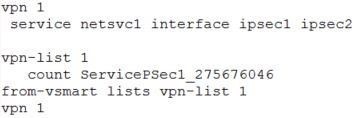
B.
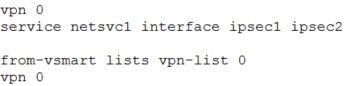
C.
D.

Correct Answer: C
QUESTION 86
An engineer wants to automate the onboarding process for a WAN Edge router with vManage. Which command will accomplish this?
A. request vedge-cloud activate chassis-number <chassis-number> serial <serial>
B. request vedge-cloud activate chassis-number <chassis-number> token <token-number>
C. request vedge-cloud activate serial <serial> token <token-number>
D. request vedge-cloud activate chassis-number <chassis-number> organization <organization>
Correct Answer: B
QUESTION 87
Refer to the exhibit.
An administrator is configuring a policy in addition to an existing hub-and-spoke policy for two sites that should directly communicate with each other. How is this policy configured?
A. hub-and-spoke
B. import existing topology
C. mesh
D. custom control (route and TLOC)
Correct Answer: B
QUESTION 88
An administrator is configuring the severity level on the vManage NMS for events that indicate that an action must be taken immediately. Which severity level must be configured?
A. warning
B. critical
C. error
D. alert
Correct Answer: B
QUESTION 89
Which two features does the application firewall provide? (Choose two)
A. classification of 1400+ layer 7 applications
B. classification of 1000+ layer 4 applications
C. numbered sequences of match-action pairs
D. blocks traffic by application or application-family
E. application match parameters
Correct Answer: AD
QUESTION 90 Refer to the exhibit.

The network administrator has configured a centralized topology policy that results in the displayed routing table at a branch office. Which two configurations are verified by the output? (Choose two)
A. The default route is learned via OMP.
B. The routing table is for the transport VPN.
C. This routing table is from a cEdge router.
D. The default route is configured locally.
E. The configured policy is adding a route tag of 300 to learned routes.
Correct Answer: AC
QUESTION 91
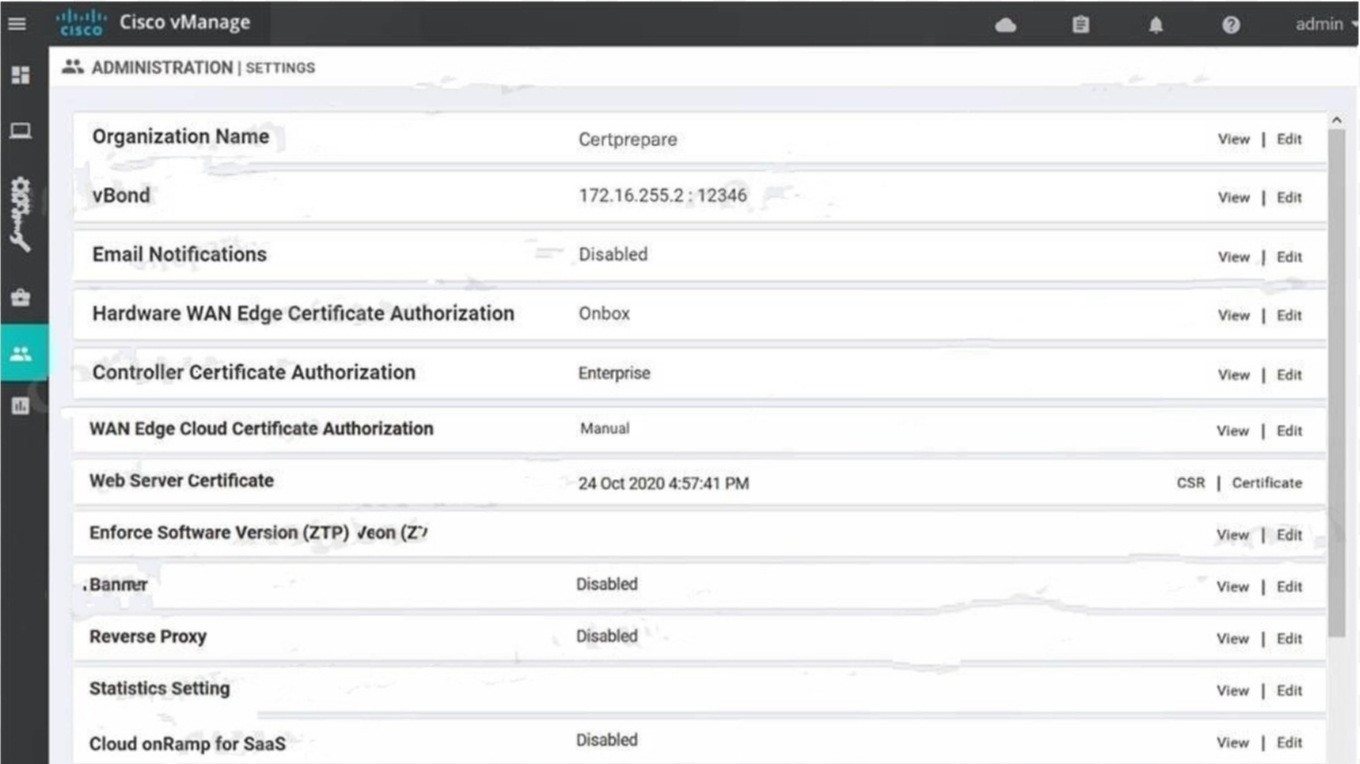
An engineer wants to change the configuration of the certificate authorization mode from manual to automated. Which GUI selection will accomplish this?
A. Configuration > Certificates
B. Tools > Operational Commands
C. Maintenance > Security
D. Administration > Settings
Correct Answer: D
QUESTION 92
Which policy blocks TLOCs from remotes and allows TLOCs from the data center to form hub- and-spoke peering?
A. localized data policy
B. localized control policy
C. centralized data policy
D. centralized control policy
Correct Answer: D
QUESTION 93
Which component is responsible for routing protocols such as BGP and OSPF in a Cisco SD-WAN solution?
A. vManage
B. vBond Orchestrator
C. vSmart Controller
D. WAN Edge Router
Correct Answer: D
QUESTION 94
In a Cisco SD-WAN network, which component is responsible for distributing route and policy information via the OMP?
A. vSmart Controler
B. vManage
C. vBond Orchestrator
D. WAN Edge Router
Correct Answer: A
QUESTION 95
For data plane resiliency, what does the Cisco SD-WAN software implement?
A. OMP
B. BFD
C. multiple vBond orchestrators
D. establishing affinity between vSmart controllers and WAN Edge routers
Correct Answer: B
QUESTION 96
Which Cisco SD-WAN component the initial communication between WAN Edge devices to join the fabric?
A. WAN Edge Router
B. vSmart Controller
C. vManage
D. vBond Orchestrator
Correct Answer: D
QUESTION 97
Which protocol is used for the vManage to connect to the vSmart Controller hosted in Cloud?
A. NETCONF
B. ZTP
C. HTTP
D. PnP Server
Correct Answer: A
QUESTION 98
Refer to the exhibit.
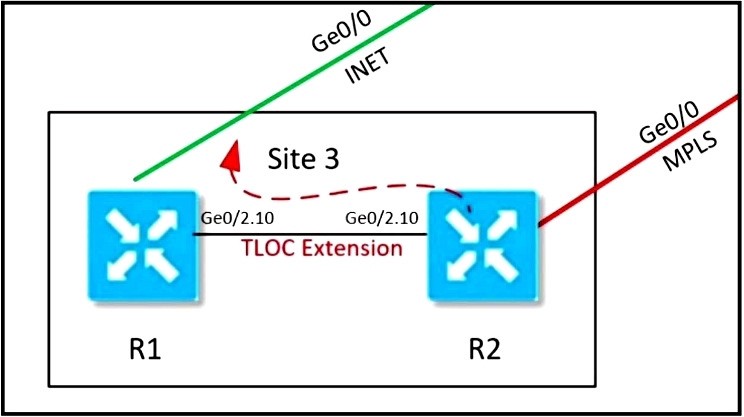
Which configuration extends the INET interface on R1 to be used by R2 for control and data connections?
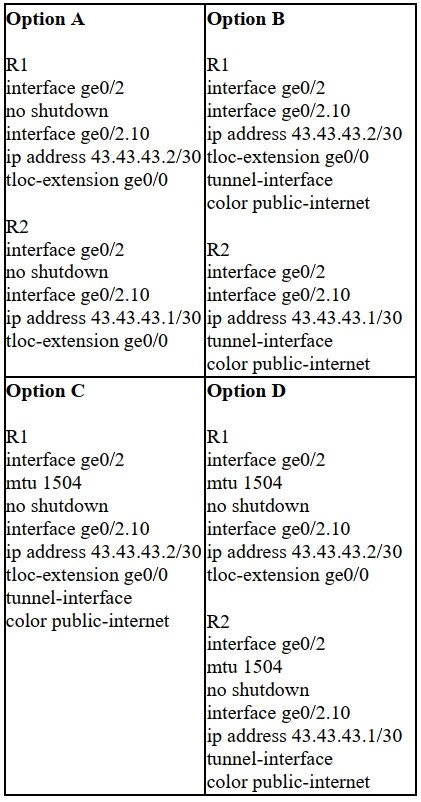
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: D
QUESTION 99
A customer must upgrade the Cisco SD-WAN devices and controllers from version 19.2 to version 20.3. The devices include WAN Edge cloud, vManage, vSmart, and vBond. Which types of image types of image files are needed for this upgrade?
A. one file for vManage, one for vSmart and one for vBond + WAN Edge Cloud with extension.bin
B. one file for vManage and one file for all other devices with extension tar.gz
C. one file for vManage, one for vSmart and one for vBond + WAN Edge Cloud with extension tar.gz
D. one file for vManage, and one file for all other devices with extension .bin
Correct Answer: B
QUESTION 100
Refer to the exhibit.
vManage logs are available for the past few months. A device name change deployed mistakenly at a critical site. How is the device name change tracked by operation and design teams?
Option A
Option B
Option C
Option D
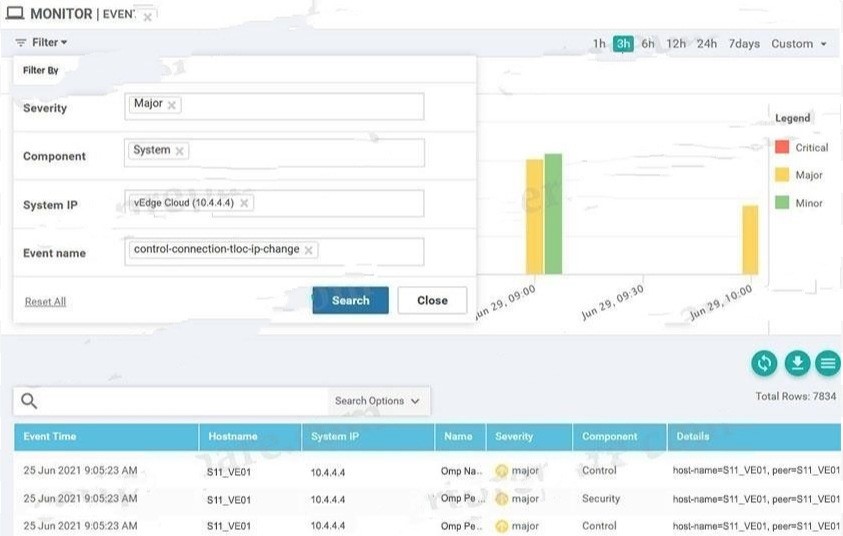
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: D
QUESTION 101
Which two prerequisites must be met before the Cloud onRamp for IaaS is initiated on vManage to expand to the AWS cloud? (Choose two)
A. Attach the “AmazonCreateVPC” and “Amazon Provision EC2” permission policy to the IAM account
B. Subscribe to the SD-WAN Edge router AMI in the AWS account
C. Attach an OSPF feature template to the AWS cloud Edge router template
D. Attach a device template to the cloud WAN Edge router to be deployed in the AWS
E. Preprovision the transit VPC in the AWS region
Correct Answer: BD
QUESTION 102
Which feature allows reachability to an organization’s internally hosted application for an active DNS security policy on a device?
A. local domain bypass
B. DHCP option 6
C. DNSCrypt configurator
D. data pokey with redirect
Correct Answer: A
QUESTION 103
Which two requirements must be met for DNS inspection when integrating with Cisco Umbrella? (Choose two)
A. Upload the WAN Edge serial allow list to the Umbrella portal.
B. Attach security policy to the device template.
C. Register and configure the vManage public IP and serial number in the Umbrella portal.
D. Create and attach a System feature template with the Umbrella registration credentials.
E. Configure the Umbrella token on the vManage.
Correct Answer: BE
QUESTION 104
An organization wants to use the Cisco SD-WAN regionalized service-chaining feature to optimize cost and user experience with application in the network, which allows branch routers to analyze and steer traffic toward the required network function. Which feature meets this requirement?
A. Cloud onRamp for CoLocation
B. VNF Service Chaning
C. Cloud Services Platform
D. Cloud onRamp for IaaS
Correct Answer: A
QUESTION 105
What are the two protocols redistributed into OMP? (Choose two)
A. OSPF
B. RIP
C. EIGRP
D. RSVP
E. LDP
Correct Answer: AC
QUESTION 106
How does the replicator role function in Cisco SD-WAN?
A. vSmart Controllers advertise the rendezvous point to all the receivers through the overlay network.
B. WAN Edge devices advertise the rendezvous point to all the receivers through the underlay network.
C. WAN Edge devices advertise the rendezvous point to all receivers through the overlay network.
D. vSmart Controllers advertise the rendezvous point to all the receivers through the underlay network.
Correct Answer: A
QUESTION 107
Which type of route advertisement of OMP can be verified?
A. Origin, TLOC, and VPN
B. Origin, TLOC, and service
C. OMP, VPN, and origin
D. OMP, TLOC, and service
Correct Answer: D
QUESTION 108
Which two hardware platforms support Cisco IOS XE SD-WAN images? (Choose two)
A. ISR4000 series
B. ISR9300 series
C. vEdge-1000 series
D. ASR9000 series
E. ASR1000 series
Correct Answer: AE
QUESTION 109
Which Cisco SD-WAN WAN Edge platform supports LTE and Wi-Fi?
A. ISR 1101
B. ASR 1001
C. CSR 1000v
D. vEdge 2000
Correct Answer: A
QUESTION 110
Which component of the Cisco SD-WAN control plane architecture facilitates the storage of certificates and configurations for network components?
A. vSmart
B. WAN Edge
C. vManage
D. vBond
Correct Answer: C
QUESTION 111
What is a default protocol for control plane connection?
A. HTTPS
B. TLS
C. IPsec
D. DTLS
Correct Answer: D
QUESTION 112
Which component of the Cisco SD-WAN control plane architecture should be located in a public Internet address space and facilitates NAT-traversal?
A. WAN Edge
B. vSmart
C. vBond
D. vManage
Correct Answer: C
QUESTION 113
Which component of the Cisco SD-WAN architecture oversees the control plane of overlay network to establish, adjust, and maintain the connections that form the Cisco SD-WAN fabric?
A. APIC-EM
B. vSmart
C. vManage
D. vBond
Correct Answer: B
QUESTION 114
Which two options are SD-WAN solution capabilities? (Choose two)
A. Ability to provide and integrate security with complementary products and applications
B. The separation of management plane, control plane and data plane to enable horizontal scaling
C. Truck roll branch turn up for easy provisioning and new installations
D. Cloud hosted or on-premise fully redundant management and control plane functions
Correct Answer: BD
QUESTION 115
Which Cisco SD-WAN component provides a secure data plane with remote vEdge routers?
A. vManage
B. vSmart
C. vBond
D. vEdge
Correct Answer: D
QUESTION 116
Which two mechanisms are used to guarantee the integrity of data packets in the Cisco SD-WAN architecture data plane? (Choose two)
A. certificates
B. transport locations
C. authentication headers
D. encapsulation security payload
E. TPM chip
Correct Answer: CD
QUESTION 117
How is the scalability of the vManage increased in Cisco SD-WAN Fabric?
A. Increase the bandwidth of the WAN link connected to the vManage
B. Increase licensing on the vManage
C. Deploy more than one vManage controllers on different physical server
D. Deploy multiple vManage controllers in a cluster
Correct Answer: D
QUESTION 118
Which configuration step is taken on vManage after WAN Edge list is uploaded to support the on- boarding process before the device comes online?
A. Verify the device certificate
B. Enable the ZTP process
C. Set the device as valid
D. Send the list to controllers
Correct Answer: C
QUESTION 119
Which API call retrieves a list of all devices in the network?
A. https://vmanage_IP_address/dataservice/system/device/{{model}}
B. http://vmanage_IP_address/dataservice/system/device/{{model}}
C. http://vmanage_IP_address/api-call/system/device/{{model}}
D. https://vmanage_IP_address/api-call/system/device/{{model}}
Correct Answer: A
QUESTION 120
Which combination of platforms are managed by vManage?
A. ISR4351, ASR1002HX, vEdge2000, vEdge Cloud
B. ISR4321, ASR1001, Nexus, ENCS
C. ISR4321, ASR1001, ENCS, ISRv
D. ISR4351, ASR1009, vEdge2000, CSR1000v
Correct Answer: A
QUESTION 121
Two sites have one WAN Edge each. Each WAN Edge has two public TLOCs with no restrict configured. There is full reachability between the TLOCs. How many data tunnels are formed on each Edge router?
A. 6
B. 2
C. 4
D. 8
Correct Answer: C
QUESTION 122
On which device is a service FW address configured to insert firewall service at the hub?
A. vSmart at the branch
B. vEdge at the branch
C. vEdge at the hub
D. vSmart at the hub
Correct Answer: C
QUESTION 123
Which command verifies a policy that has been pushed to the vEdge router?
A. vSmart# show running-config policy
B. vEdge# show running-config data policy
C. vSmart# show running-config apply policy
D. vEdge# show policy from-vsmart
Correct Answer: D
QUESTION 124
Refer to the exhibit. An engineer is troubleshooting a control connection issue. What does “connect” mean in this show control connections output?
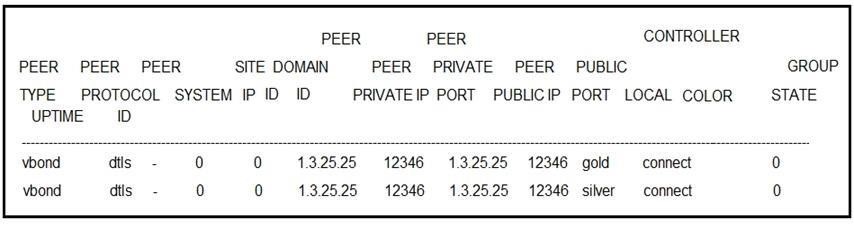
A. Control connection is down
B. Control connection is up
C. Control connection attempt is in progress
D. Control connection is connected
Correct Answer: C
QUESTION 125
Which attributes are configured to uniquely identify and represent a TLOC route?
A. system IP address, link color, and encapsulation
B. origin, originator, and preference
C. site ID, tag, and VPN
D. firewall, IPS, and application optimization
Correct Answer: A
QUESTION 126
An engineer is troubleshooting a certificate issue on vEdge. Which command is used to verify the validity of the certificates?
A. show control local-properties
B. show control summary
C. show certificate installed
D. show certificate status
Correct Answer: A
QUESTION 127
Which OSPF command makes the WAN Edge router a less preferred exit from a site with a dual WAN Edge design?
A.

B.
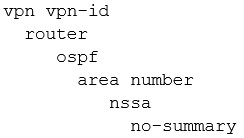
C.

D.

Correct Answer: A
QUESTION 128
A vEdge platform is sending VRRP advertisement messages every 10 seconds. Which value configures the router back to the default timer?
A. 2 seconds
B. 5 seconds
C. 1 second
D. 3 seconds
Correct Answer: C
QUESTION 129
An engineer is troubleshooting a vEdge router and identifies a “DCONFAIL DTLS connection ” message. What is the problem?
failure
A. memory issue
B. certificate mismatch
C. organization mismatch
D. connectivity issue
Correct Answer: D
QUESTION 130
At which layer does the application-aware firewall block applications on a WAN Edge?
A. 3
B. 5
C. 2
D. 7
Correct Answer: D
QUESTION 131 What is the default interval for BFD packets?
A. 1 second
B. 15 seconds
C. 10 seconds
D. 5 seconds
Correct Answer: A
QUESTION 132
Refer to the exhibit. What does the BFD value of 8 represent?

A. dead timer of BFD session
B. poll-interval of BFD session
C. hello timer of BFD session
D. number of BFD sessions
Correct Answer: D
QUESTION 133
When software is upgraded on a vManage NMS, which two image-adding options store images in a local vManage software repository? (Choose two)
A. To be downloaded over an ICMP connection
B. To be downloaded over a SNMP connection
C. To be downloaded over a control plane connection
D. To be downloaded over an out-of-band connection
E. To be downloaded over a SMTP connection
Correct Answer: CD
QUESTION 134
Which two platforms for the Cisco SD-WAN architecture are deployable in a hypervisor on- premises or in IAAS Cloud? (Choose two)
A. CSR 1000v
B. ISR 4431
C. vEdge 100c
D. vEdge 2000
E. vEdge Cloud
Correct Answer: AE
QUESTION 135
Which two image formats are supported for controller codes? (Choose two)
A. .nxos
B. .qcow2
C. .iso
D. .ova
E. .tgz
Correct Answer: BD
QUESTION 136
What are the two advantages of deploying cloud-based Cisco SD-WAN controllers? (Choose two)
A. centralized control and data plane
B. infrastructure as a service
C. management of SLA
D. centralized raid storage of data
E. distributed authentication policies
Correct Answer: BC
QUESTION 137
Which two platforms can host a vEdge Cloud Router? (Choose two)
A. Microsoft Azure
B. Dream host
C. AWS
D. DigitalCloud
E. Google
Correct Answer: AC
QUESTION 138
Which two services are critical for zero touch provisioning onboarding? (Choose two)
A. EMAIL
B. SNMPC. AAA
D. DHCP
E. DNS
Correct Answer: DE
QUESTION 139
When redistribution is configured between OMP and BGP at two Data Center sites that have Direct Connection Interlink, which step avoids learning the same routes on WAN Edge routers of the DCs from LAN?
A. Set down-bit on Edge routers on DC1
B. Define different VRFs on both DCs
C. Set OMP admin distance lower than BGP admin distance
D. Set same overlay AS on both DC WAN Edge routers
Correct Answer: D
QUESTION 140
Which device information is required on PNP/ZTP to support the zero touch onboarding process?
A. serial and chassis numbers
B. interface IP address
C. public DNS entry
D. system IP address
Correct Answer: A
QUESTION 141
Which command displays BFD session summary information per TLOC on vEdge routers?
A. show bfd tloc-summary-list
show bfd history
C. show bfd summary
D. show bfd sessions
Correct Answer: A
QUESTION 142
Which configuration allows users to reach YouTube from a local Internet breakout?
A.

B.
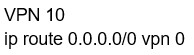
C.
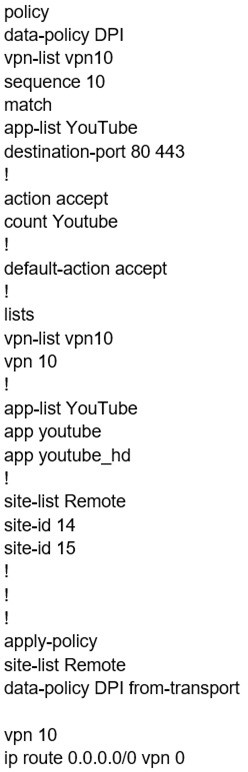
D.
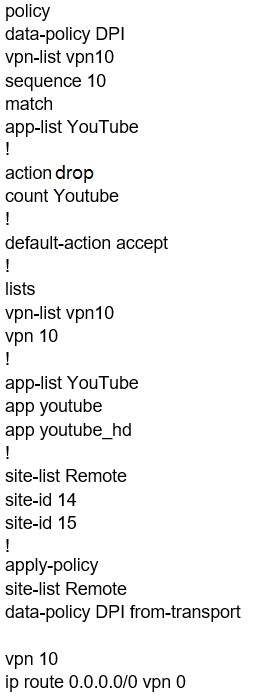
Correct Answer: A
QUESTION 143
Which feature template configures OMP?
A.

B.
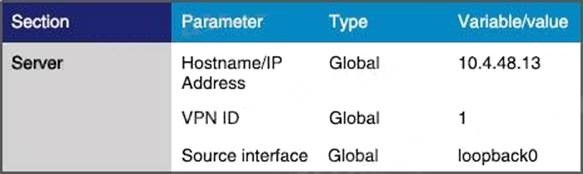
C.

D.
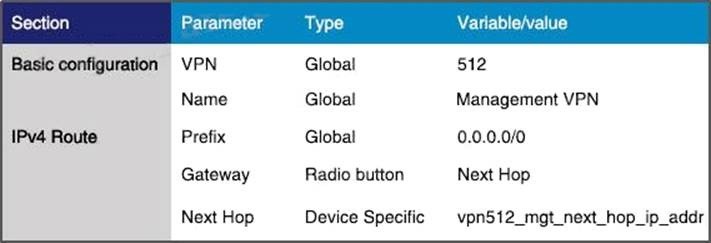
Correct Answer: A
QUESTION 144
Refer to the exhibit. Which configuration change is needed to configure the tloc-extention on Branch1-Edge1?
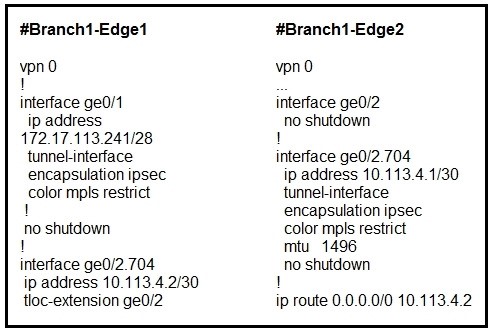
A.

B.
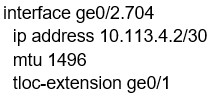
C.
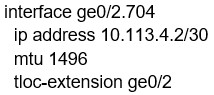
D.

Correct Answer: B
QUESTION 145 Which command on a WAN Edge device displays the information about the colors present in the fabric that are learned from vSmart via OMP?
A. show omp peers
B. show omp route
C. show omp sessions
D. show omp tlocs
Correct Answer: D
QUESTION 146
Which statement about VRRP is true?
A. It supports load balancing
B. It can be configured with HSRP on a switch or switch stack
C. It supports IPv4 and IPv6
D. It supports encrypted authentication
Correct Answer: B
QUESTION 147
Refer to the exhibit. Which QoS treatment results from this configuration after the access list acl-guest is applied inbound on the vpn1 interface?
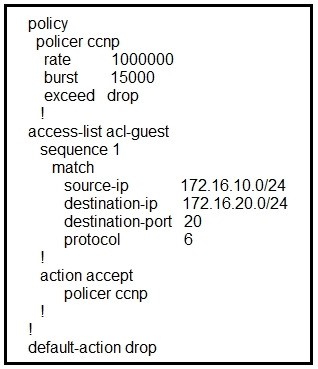
A. A TCP packet sourcing from 172.16.10.1 and destined to 172.16.20.1 is dropped
B. A UDP packet sourcing from 172.16.20.1 and destined to 172.16.10.1 is accepted
C. A UDP packet sourcing from 172.16.10.1 and destined to 172.16.20.1 is dropped
D. A TCP packet sourcing from 172.16.20.1 and destined to 172.16.10.1 is accepted
Correct Answer: C
QUESTION 148
Which SD-WAN component is configured to enforce a policy to redirect branch-to-branch traffic toward a network service such as a firewall or IPS?
A. vBond
B. vSmart
C. WAN Edge
D. Firewall
Correct Answer: B
QUESTION 149
Which configuration changes the packet loss priority from low to high?
A.

B.

C.

D.

Correct Answer: D
QUESTION 150
Which policy configures an application-aware routing policy under Configuration > Policies?
A. Data policy
B. Centralized policy
C. Localized policy
D. Control policy
Correct Answer: B
QUESTION 151
Where does the Cisco V-Edge Router perform QoS traffic classification?
A. Per VPN
B. Per vEdge
C. Egress interface
D. Ingress interface
Correct Answer: D
QUESTION 152
Which scheduling method is configured by default for the eight queues in the cloud vEdge router?
A. weighted round robin
B. priority queue
C. low latency queue
D. weighted random early detection
Correct Answer: A
QUESTION 153
A voice packet requires a latency of 50 msec. Which policy is configured to ensure that a voice packet is always sent on the link with less than a 50 msec delay?
A. localized data
B. centralized control
C. localized control
D. centralized data
Correct Answer: D
QUESTION 154
In which VPN is the NAT operation on an outgoing interface configured for direct Internet access?
A. 0
B. 512
C. 10
D. 1
Correct Answer: A
QUESTION 155
When the VPN membership policy is being controlled at the vSmart controller, which policy disallows VPN 1 at sites 20 and 30?
A.
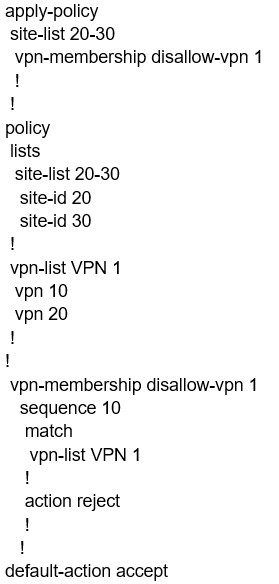
B.
C.
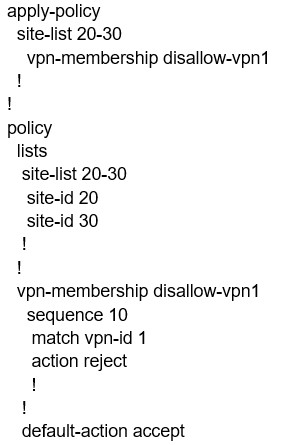
D.

Correct Answer: C
QUESTION 156
When VPNs are grouped to create destination zone in Zone-Based Firewall, how many zones can a single VPN be part of?
A. two
B. four
C. one
D. three
Correct Answer: C
QUESTION 157
Which template configures the out-of band management VPN?
A.
B.
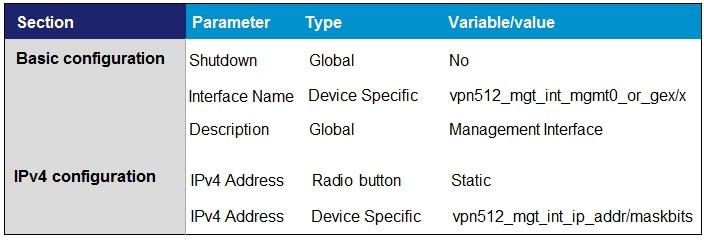
C.
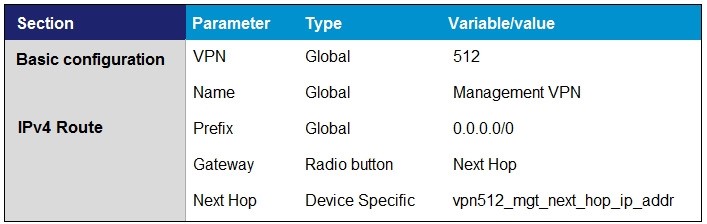
D.

Correct Answer: C
QUESTION 158
Which on-the-box security feature is supported by the Cisco ISR 4451 SD-WAN device and not on vEdge?
A. Cloud Express service
B. Enterprise Firewall with Application Awareness
C. reverse proxy
D. IPsec/GRE cloud proxy
Correct Answer: B
QUESTION 159
What is a benefit of the application-aware firewall?
A. It blocks traffic by MTU of the packet
B. It blocks encrypted traffic
C. It blocks traffic by application
D. It blocks traffic by MAC address
Correct Answer: C
QUESTION 160
Which value is verified in the certificates to confirm the identity of the device?
A. Serial Number
B. OTP
C. System-IP
D. Chassis-ID
Correct Answer: A
QUESTION 161
Which hardware component is involved in the Cisco SD-WAN authentication process for ISR platforms?
A. ZTP
B. OTPC
C. SUDI
D. TPMD
Correct Answer: C
QUESTION 162
Which alarm setting is configured to monitor serious events that affect, but do not shut down, the operation of a network function?
A. Critical
B. Medium
C. MajorD. Minor
Correct Answer: C
QUESTION 163
Which command disables the logging of syslog messages to the local disk?
A. no system logging disk local
B. system logging server remote
C. no system logging disk enable
D. system logging disk disable
Correct Answer: C
QUESTION 164
Which logs verify when a device was upgraded?
A. ACL
B. Email
C. SNMP
D. Audit
Correct Answer: D
QUESTION 165
Which protocol is used to measure loss, latency, jitter, and liveliness of the tunnel between WAN Edge router peers?
A. OMP
B. NetFlow
C. BFD
D. IP SLA
Correct Answer: C
QUESTION 166
Which pathway under Monitor > Network > Select Device is used to verify service insertion configuration?
A. System Status
B. ACL Logs
C. Real Time
D. Events
Correct Answer: C
Drag and drop
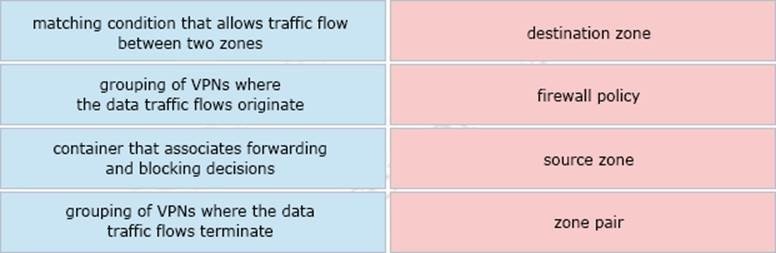
QUESTION 1
Drag and drop the definitions from the left to the configuration on the right.
Select and Place:
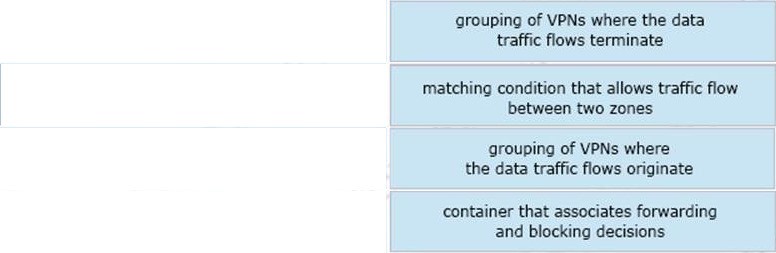
Correct Answer:
QUESTION 2
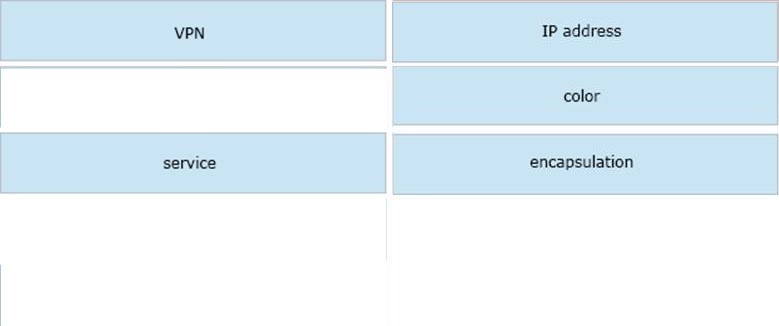
Drag and drop the attributes from the left that make each transport location unique onto the right. Not all options are used.
Select and Place:
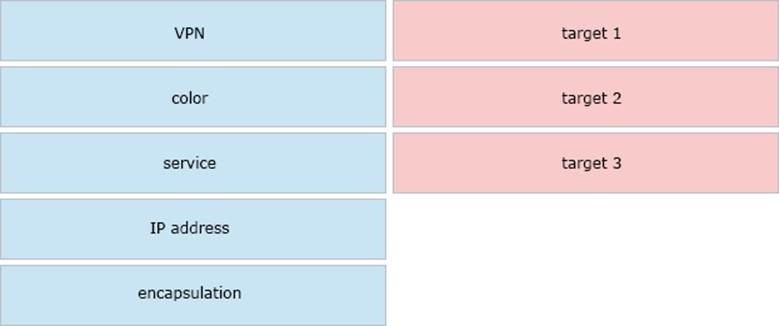
Correct Answer:
QUESTION 3
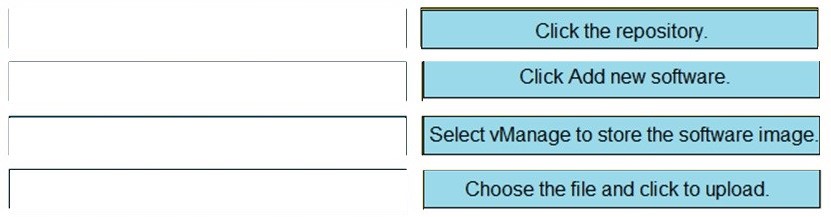
Drag and drop the steps from the left into the order on the right to upload software on vManage repository that is accessible from maintenance > Software Repository.
Select and Place:

Correct Answer:
QUESTION 4
Drag and drop the REST API calls from the left onto the functions on the right.
Select and Place:
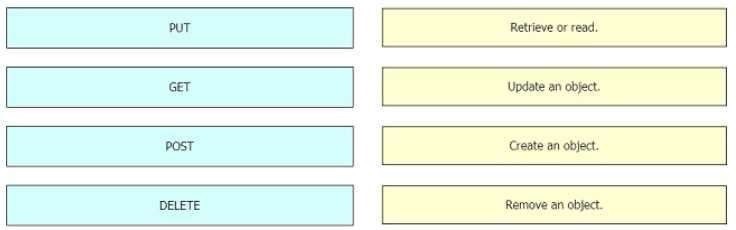
Correct Answer:

QUESTION 5
Drag and drop the Cisco SD-WAN components from the left onto their functions on the right.
Select and Place:
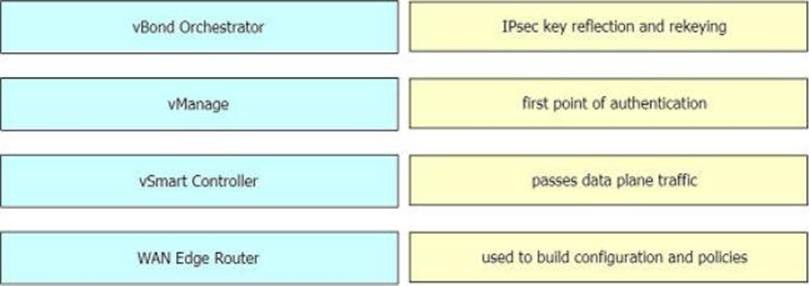
Correct Answer:

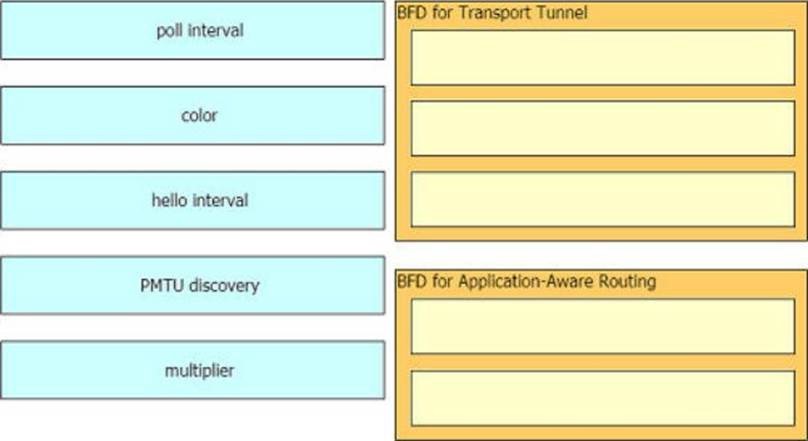
QUESTION 6
Drag and drop the BFD parameters from the left onto the BFD configurations on the right.
Select and Place:
Correct Answer:
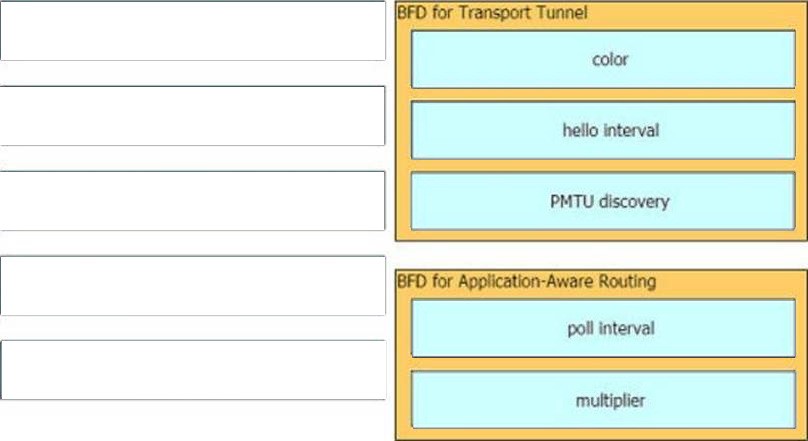
QUESTION 7
Drag and drop the devices from the left onto the correct functions on the right.
Select and Place:
Correct Answer:

QUESTION 8
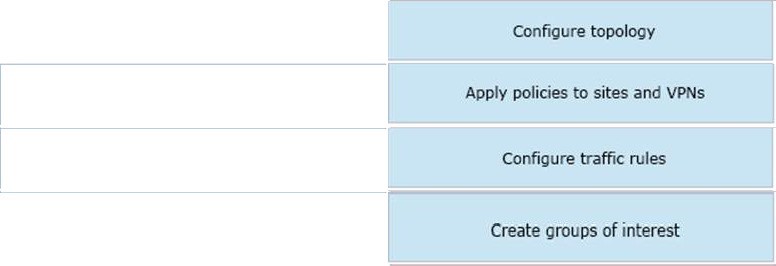
Drag and drop the vManage policy configuration procedures from the left onto the correct definitions on the right.
Select and Place:
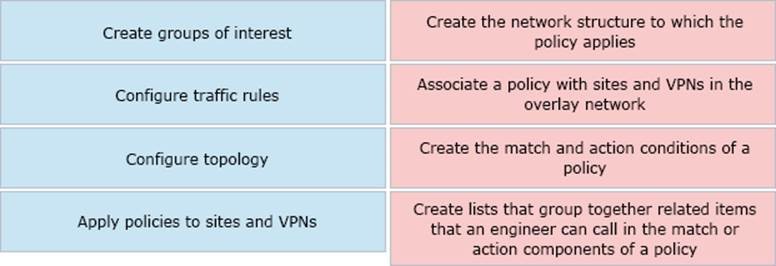
Correct Answer:
QUESTION 9
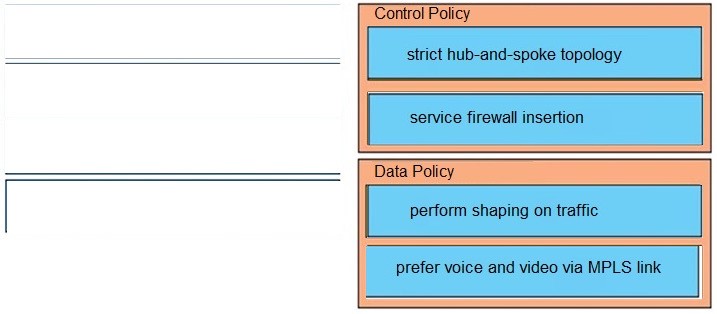
Drag and drop the policies from the left onto the correct policy types on the right.
Select and Place:
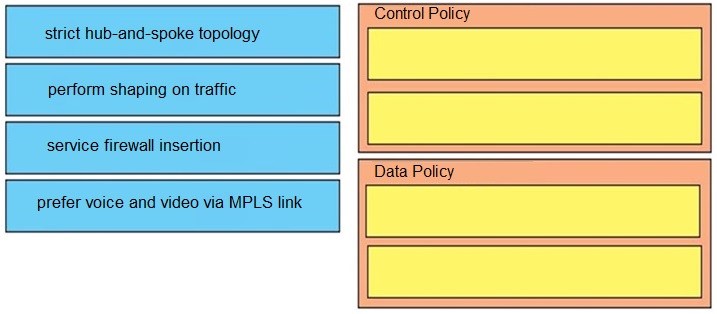
Correct Answer:
QUESTION 10
Drag and drop the route verification output from show omp tlocs from the left onto the correct explanations on the right.
Select and Place:
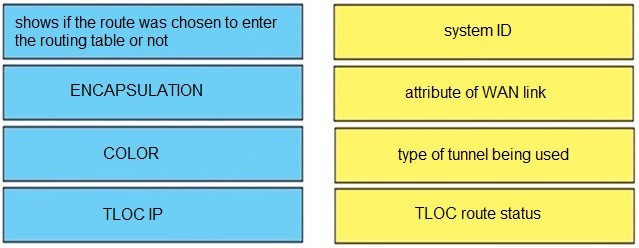
Correct Answer:
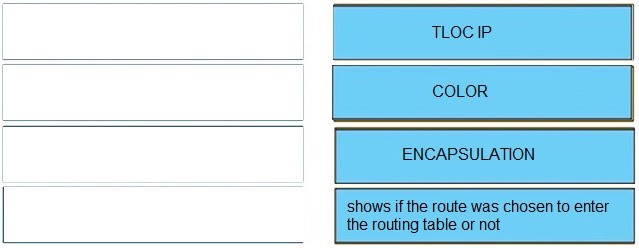
QUESTION 11
Drag and drop the actions from the left into the correct sequence on the right to create a data policy to direct traffic to the Internet exit Select and Place:

Correct Answer:
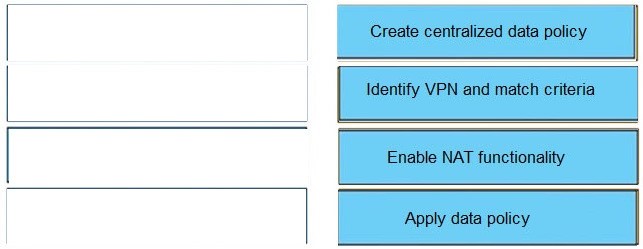
QUESTION 12
Drag and drop the functions from the left onto the correct templates on the right.
Select and Place:
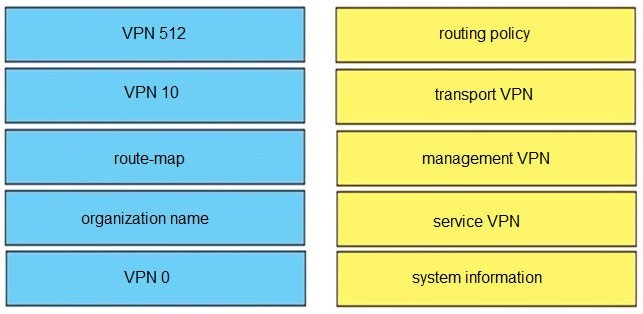
Correct Answer:

QUESTION 13
Drag and drop the components from the left onto the corresponding Cisco NFV infrastructure Building Blocks on the right. Not all options are used.
Select and Place:
Correct Answer: